Adele
Information Technology Paper 1 Grade 12 Memorundum - NSC Past Papers And Memos September 2020 Preparatory Examinations
MEMORANDUM
NAME OF LEARNER: | |||||||
TOTAL QUESTION 1: | TOTAL QUESTION 2: | TOTAL QUESTION 3: | TOTAL QUESTION 4: | TOTAL | |||
/40 | /40 | /40 | /30 | /150 | |||
QUESTION 1: GENERAL PROGRAMMING SKILLS | MAX. MARKS | MARKS ACHIEVED | |||||
1.1 | Button [1.1 Display Club name]
| 6 | |||||
1.2 | Button [1.2 Process]
| 16 | |||||
| MAX. MARKS | MARKS ACHIEVED | ||
1.3 | Button [1.3 Test for leap year]
else
else
else
Alternative solution using a Boolean flag:
else
else
else
| 12 | |
1.4 | Button [1.4 Pattern]
| 6 | |
TOTAL QUESTION 1 | 40 | ||
QUESTION 2: OBJECT-ORIENTATED PROGRAMMING | MAX. MARKS | MARKS ACHIEVED | |
2.1.1 | Constructor Create:
| 5 | |
2.1.2 | Function calculatefunds : real
| 6 | |
2.1.3 | Procedure addnumber;
| 7 | |
2.1.4 | Function tostring: string;
| 8 | |
2.1 Subtotal: Object class | 26 | ||
2.2.1 | Button [Q2.2.1]
| 6 | |
2.2.2 |
| 8 | |
2.2 Subtotal: Form class | 14 | ||
TOTAL QUESTION 2 | 40 | ||
QUESTION 3: DATABASE PROGRAMMING | MAX. MARKS | MARKS ACHIEVED | |
3.1.1 | Button: [3.1.1] | 4 | |
SQL: select MaterialType from Material order by MaterialType DESC | |||
Concepts:
| |||
3.1.2 | Button: [3.1.2] | 5 | |
SQL: Select MaterialType from Material where MaterialType like ' + quotedstr('%' + SLINE + '%') | |||
Concepts:
| |||
3.1.3 | Button: [3.1.3] | 5 | |
SQL: Select Datedisposed, MaterialType from Material where Month(DateDisposed) = 10 | |||
Concepts:
| |||
3.1.4 | Button: [3.1.4] | 4 | |
SQL: update Disposal set Employees = Employees + Employees*10/100 | |||
Concepts:
| |||
3.1.5 | Button: [3.1.5] | 7 | |
SQL: Select sum(Quantity) As Total_Quantities, DisposalMethod from Material, Disposal where Material.Disposalcode = Disposal.Disposalcode group by DisposalMethod | |||
Concepts:
| |||
3.1 Subtotal: SQL | 25 | ||
3.2.1 | Button: [3.2.1]
| 7 | |
3.2.2 | Button: [3.2.2]
| 8 | |
3.2 Subtotal: Code constructs | 15 | ||
TOTAL QUESTION 3 | 40 | ||
QUESTION 4: PROBLEM SOLVING | MAX. MARKS | MARKS ACHIEVED | |
4.1 | Combobox option [Total weight of All waste]
| 4 | |
4.2 | Combobox option [Total weight of RECYCLED waste]
| 5 | |
4.3 | Combobox option [Percentage of RECYCLED waste]
| 3 | |
4.4 | Combobox option [TOTAL weight of EACH waste product]
| 18 | |
TOTAL QUESTION 4 | 30 | ||
SAMPLE SOLUTIONS
QUESTION 1
QUESTION 3

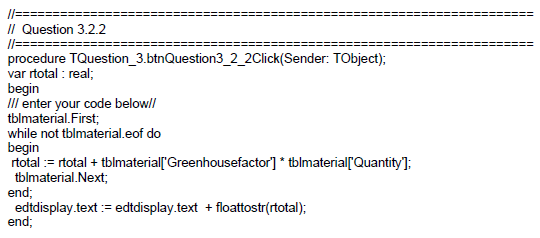
QUESTION 4
Information Technology Paper 2 Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
INSTRUCTIONS AND INFORMATION
- This paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (23)
SECTION C: Communication and Network Technologies (28)
SECTION D: Data and Information Management (24)
SECTION E: Solution Development (24)
SECTION F: Integrated Scenario (36) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give the correct computer term for each of the following descriptions. Write only the term next to the question number (1.1.1–1.1.10) in the ANSWER BOOK.
1.1.1 A method in object-oriented programming used to build an object in memory (1)
1.1.2 The combination of more than one field to uniquely identify a record (1)
1.1.3 A set of electrical paths etched on the motherboard, used to transfer data between different parts of a computer (1)
1.1.4 The gap between people that have access to computers and technology and people that do not (1)
1.1.5 Programs that are part of the system software and maintenance and administrative tasks (1)
1.1.6 Total amount of data that can be transferred from one point to another in a given period of time (1)
1.1.7 The type of crime when someone steals your details in order to pretend to be you (1)
1.1.8 A single complete working CPU circuit (1)
1.1.9 Contracting specialist businesses to run aspects of your own business that are essential for proper functioning, but do not fall within your own area of expertise (1)
1.1.10 A web application that is designed to deliver the functions and features of a traditional desktop application (1)
1.2 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.2.1–1.2.5) in the ANSWER BOOK, for example 1.2.6 D.
1.2.1 The conversion of hexadecimal number A13 to a decimal number is …
- 2579.
- 2560.
- 2563.
- 2576. (1)
1.2.2 What will the value of iNum be when the following statement is executed?
iNum := 7 + 5 * 9 div 3 – sqrt(49);
- -7
- 6
- 15
- 9 (1)
1.2.3 Software that translates programming instructions into machine code one line at a time is called …
- compilers.
- coding.
- interpreters.
- translator. (1)
1.2.4 … refer to businesses that use groups of low paid workers whose work is to repetitively click on links to fake high web traffic.
- Mediated searches
- Click farms
- Context-ware searches
- Customised searching (1)
1.2.5 A sequence of one or more characters used to specify the boundary between separate independent regions in plain text is called …
- separator.
- delimiter.
- limiter.
- grouping. (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
The reality is that there is no single specification that determines the speed or performance of a computing device. Instead, a whole lot of different components and specifications all play a role in determining the overall performance of the machine.
2.1 In today’s modern times, mobility and portability have become the norm in terms technology.
2.1.1 Mobile technology is driven by ease of access, user experience, the need, the desire to be always on and always connected.
- What does the always on concept mean in terms of technology? (1)
- List TWO devices that have the always on technology. (2)
- Why is the always on an advantage in mobile devices? (1)
2.1.2 If you had to carry around multiple devices, no matter how powerful they are, you would become irritated and frustrated because you would be overloaded with devices and forget to bring the device you need.
- Briefly explain the concept wearable technology. (1)
- List TWO examples of wearable devices. (2)
2.2 Things tend to decay and descend into chaos when you just leave them to themselves – this also applies to computing devices and data. The simple answer to this problem is that we need to manage our computing devices.
2.2.1 Briefly explain in simple terms the importance to manage our computers. (1)
2.2.2 List the THREE important factors that drive or influence computer management. (3)
2.2.3 Name THREE things you need to do, which will assist you quickly and economically to rebuild a system, if your hard drive crashes. (3)
2.2.4 It is essential to have a firewall when using the Internet. Explain what a firewall is and what function it performs. (2)
2.3 Study the following dialogue box and answer the questions below.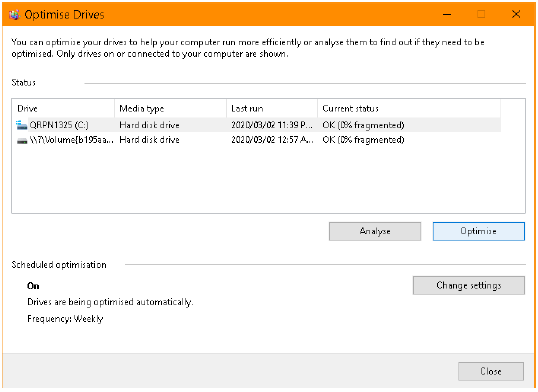
2.3.1 What do we mean when we say the disk is fragmented? (1)
2.3.2 Why does a fragmented disk slow down a computer? (1)
2.3.3 Explain the concept disk defragmentation. (1)
2.4 There are lots of campaigns done by banking industries and the government about a variety of methods to deal with scams and malware.
2.4.1 Give TWO general tips related to the use of anti-virus software. (2)
2.4.2 Mention TWO items or points that should be included in a good password policy besides changing passwords on a regular basis. (2)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
Connecting devices in a network brought a whole new dimension to the use of computers and technology.
3.1 Configuring a network covers a wide range of concepts – from choosing or buying hardware and software, to planning and implementing user rights and permissions.
3.1.1 List and briefly explain THREE different permissions that can be granted in a network. (3)
3.1.2 There are two main groups of users on a network. List and explain the TWO main groups of users on a network and the role played by each group. (4)
3.2 BitTorrent is a peer-to-peer protocol used to transfer and share large files across a network such as the Internet. To use a BitTorrent you need to install a client software.
3.2.1 List TWO examples of BitTorrent client software. (2)
3.2.2 Briefly explain the concept seeders and describe the role played by seeders in BitTorrent. (2)
3.3 Remote access technology is divided into TWO groups.
3.3.1 List and briefly explain TWO groups of remote access technologies. (4)
3.3.2 List TWO third-party software used by ONE of the groups. (2)
3.4 When the usage of the Internet expanded to include e-commerce, anonymity became a huge problem. Solutions had to be found that would allow users to trust businesses, banks etc. Digital certificates and digital signatures are the solutions currently in use.
3.4.1 Briefly explain what a digital signature is and the function it performs. (2)
3.4.2 Give TWO examples of Certificate Authorities (CAs) tasked with issuing digital certificates. (2)
3.5 A consequence of appification is that browsing and browser-based discovery of sites is decreasing and search engines are struggling to make money because of appification.
3.5.1 Explain what appification is. (1)
3.5.2 Give THREE reasons why the apps have become so popular on mobile devices. (3)
3.6 What is the term used to describe the concept that more and more devices, objects are being connected to the Internet, with the ability to communicate with other devices and objects and to take intelligent decisions based on the input received. (1)
3.7 Name the TWO web data storage models and briefly outline the main difference between these two models. (2)
TOTAL SECTION C: 28
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
Traditionally, data was organised in file formats. DBMS was a new concept then, and all the research was done to make it overcome the deficiencies in the traditional style of data management.
4.1 Briefly explain what a DBMS is (the meaning of the acronym is not required). (1)
4.2 Briefly explain the concept transaction. (1)
4.3 Distinguish between Commit/Post and Purge/Consolidate. (2)
4.4 Data redundancy covers two concepts. Briefly describe these two concepts. (2)
4.5 Parallel data set is a buzzword associated with databases.
4.5.1 Explain what a parallel data set is and what it is used for. (2)
4.5.2 Give the main disadvantage of implementing parallel data sets. (1)
4.5.3 Why should a parallel data set be kept in separate places? (1)
4.6 Differentiate between overflow and truncation. (2)
4.7 A database table has been setup containing details about all the movies and studios.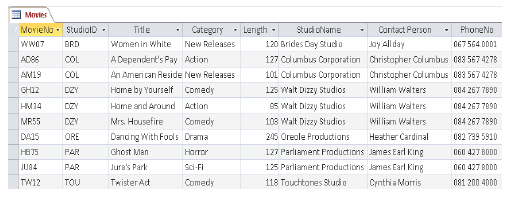
4.7.1 The table is not normalised. What is the general aim of normalisation in a database? (1)
4.7.2 Normalise the above table (Movies). Indicate the primary keys and foreign keys for each table. Create the relationship between tables. (7)
4.7.3 Use the tables in QUESTION 4.7.2 to design an ER diagram and show the relationship that exist between entities. (4)
TOTAL SECTION D: 24
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
| A common problem-solving method among programmers is to break a large problem into a series of smaller problems and then to solve each of the smaller problems. |
5.1 Computers, however, cannot make mistakes. Mistakes are made by humans. The user of the program either enter incorrect or invalid data or the programmer did not write programs with built-in measures to handle invalid operations or the correct logic was not applied when writing the programming code.
5.1.1 What is the programming tool called that allows the programmer to control how a program responds to abnormal or erroneous data and allows the program to continue running by building in a code to solve the error? (1)
5.1.2 What is another name of an error in programming called? (1)
5.1.3 Define the concept step-and-watch in programming. (2)
5.1.4 What is a tool called that is used to identify logical errors, by working through the program manually step by step and recording the results of each step in a table? (1)
5.2 All programming languages have structures available to store data.
5.2.1 Explain what a data structure is and give TWO examples of data structures. (3)
5.2.2 Which example of data structure in QUESTION 5.2.1 is classified as a temporal data structure? (1)
5.2.3 Write the output of the following program statements:
Var
Name, sLine : string;
Long, iPos : integer;
sLine := ‘I just LOVE Delphi’;
- Long := Length(sLine); (1)
- iPos := POS(‘O’, sLine); (1)
- Name := COPY(sLine, 1, iPos-1); (1)
- DELETE (sLine, 1, iPos); (1)
- INSERT(‘XTRA’, sLine, 2); (1)
5.3 UML is designed to help plan and design classes and objects. It is a powerful and complex modelling tool. A class diagram is one of the UML tools which is divided into three sections (class name section, attributes section and methods section).
5.3.1 Explain the purpose of a constructor in classes and objects. (2)
5.3.2 To remove the object from memory, we use the keyword:
ObjectName. .......................................... OR ObjectName. .................................................... (2)
5.4 Study the following code and answer the question that follows:
procedure TForm1.btnEnterValuesClick(Sender: TObject);
var
Value1, Value2, Value3, Value4, Value5 : integer; begin
- Value1 := 9;
- redOutput.Lines.Add('Solution');
- Value2 := StrToInt(InputBox('Enter Number','Enter an integer value.',''));
- Value3 := StrToInt(InputBox('Enter Number','Enter an integer value.',''));
- Value5 := Value1 - (Value2 - Value3) DIV 2;
- Value4 := 4 * Value2;
- Value2 := Value4 + Value5;
- Value3 := Value2 MOD 3;
- Value1 := (Value5 DIV 2) + (Value3 * Value3);
- redOutput.Lines.Add(IntToStr(Value1));
- redOutput.Lines.Add(IntToStr(Value2)); end;
Copy the trace table provided below into your ANSWER BOOK and complete to determine output. Assume that 12 and 6 are entered in an inputbox as Value2 and Value3 respectively.
Line No | Value1 | Value2 | Value3 | Value4 | Value5 | Screen Output |
1 | ||||||
2 | ||||||
3 | ||||||
(12 ÷ 2) (6)
TOTAL SECTION E: 24
SECTION F: INTEGRATED SCENARIO
QUESTION 6
| ICT has revolutionised the way in which people use media to communicate socially. ICT has changed the workplace in terms of employment practices and the physical nature of the space. |
6.1 Electronic devices become increasingly smart and versatile, security cameras that previously supplied raw video data are now also able to analyse data. This enables you to alter your product ranges.
6.1.1 It is fair to say that every human activity has some greater or lesser impact upon the environment. Reasonably this means that ICT also has an environmental impact.
- Explain the term e-waste. (1)
- Name THREE typical examples of e-waste. (3)
- Give TWO reasons why e-waste is dangerous to the environment. (2)
- Be responsible and recycle your used equipment. Briefly explain what happens in the recycling process. (1)
6.1.2 Preserving power is another form of encouraging green computing. Briefly explain the term green computing. (1)
6.2 Computer criminals always seem shrouded in mystery and cloaked with some sort of cyber-superpower. In movies and on television they are able to do amazing things with just a few lines of code or magical mouse clicks and they always seem to be able to keep one step ahead of the law.
6.2.1
- Explain what a spammer is. (1)
- Briefly explain why spam is a problem except that is regarded as annoying. (1)
- List TWO tips that can be applied to avoid spam. (2)
6.2.2 Cyber-crime is any crime committed by using ICT as a tool. Name THREE advantages to the criminals of using ICT as a tool to commit crime. (3)
6.2.3 What do criminals use to control computing devices to commit crime? (1)
6.2.4 What is the name of the computer that is compromised in a network used to commit crime? (1)
6.3 Computers are essential tools in managing projects of national and international importance for government, academic research and business enterprises.
6.3.1 Name TWO computer-based systems that can help us to make informed decisions. (2)
6.3.2 Name THREE general applications for distributed computing. (3)
6.3.3 Name a specific example of distributed computing in practice. (1)
6.4 Concentration is a valuable asset. You need the ability to focus if you are to work effectively, be productive and achieve your goals.
6.4.1 Explain TWO advices/tips that you can apply to manage social networking to improve your concentration and make you more productive. (2)
6.4.2 Almost all social networking tools, sites and apps encourage you to share information. The problem is that you are encouraged to share and you are told of the benefits of sharing but you are not made aware of the possible negative consequences. Name TWO things you need to be aware of before publishing or sharing information on the Internet. (2)
6.5 People keep discovering new ways to extract information from databases and new ways to store and process data. What does TPS stand for? (1)
6.6 Describe the concept Software as a Service. (1)
6.7 Automatic encryption is something that happens without you consciously choosing to use the software to encrypt data. Name TWO places where automatic encryption is used. (2)
6.8 Hackers may steal data either because they want to sell it or they want to use it themselves or to blackmail someone. Explain the concept backdoor in terms of theft of data. (1)
6.9 Criminals place a skimmer and a video camera on an ATM machine. Explain the purpose of the skimmer and a video camera in this context. (2)
6.10 The way we behave and the things we do change the way in which society operates. When crime changes our behaviour and habits, it has a set of consequences on how our society operates. Name TWO effects or societal consequences of cybercrime. (2)
TOTAL SECTION F: 36
GRAND TOTAL: 150
Information Technology Paper 1 Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
INSTRUCTIONS AND INFORMATION
- This question paper is divided into FOUR sections. Candidates must answer ALL the questions in ALL FOUR sections.
- The duration of this examination is three hours. Because of the nature of this examination it is important to note that you will not be permitted to leave the examination room before the end of the examination session.
- This question paper is set with programming terms that are specific to the Delphi programming language.
- Make sure that you answer the questions according to the specifications that are given in each question. Marks will be awarded according to the set requirements.
- Answer only what is asked in each question. For example, if the question does not ask for data validation, then no marks will be awarded for data validation.
- Your programs must be coded in such a way that they will work with any data and not just the sample data supplied or any data extracts that appear in the question paper.
- Routines, such as locate, search, sort and selection, must be developed from first principles. You may NOT use the built-in features of Delphi for any of these routines.
- All data structures must be declared by you, the programmer, unless the data structures are supplied.
- You must save your work regularly on the disk/CD/DVD/flash disk you have been given, or on the disk space allocated to you for this examination session.
- Make sure that your name and surname appear as a comment in every program that you code, as well as on every event indicated.
- If required, print the programming code of all the programs/classes that you completed. You will be given half an hour printing time after the examination session.
- At the end of this examination session you must hand in a disk/CD/DVD/flash disk with all your work saved on it OR you must make sure that all your work has been saved on the disk space allocated to you for this examination session. Make sure that all files can be read.
- The files that you need to complete this question paper have been given to you on the disk/CD/DVD/flash disk or on the disk space allocated to you. The files are provided in the form of password-protected executable files.
Do the following:- Double click on the password-protected executable file.
- Click on the extract button.
- Enter the following password: 20%tRiAL#gR12
Once extracted, the following list of files will be available in the folder DataSept2020:
Question 1:
Question1_u.pas
Question1_u.dfm
Question1_p.dpr
Question1_p.res
Question 2:
Trees.jpg
Question2ClassDefinition.pas
Question2_u.pas
Question2_u.dfm
Question2_p.dpr
Question2_p.res
Question 3:
dbConnection_u.pas
WasteDisposal.mdb
WasteDisposalBackup.mdb
Question3_u.pas
Question3_u.dfm
Question3_p.dpr
Question3_p.res
Question 4:
waste.txt
Question4_u.pas
Question4_u.dfm
Question4_p.dpr
Question4_p.res
QUESTIONS
QUESTION 1: GENERAL PROGRAMMING SKILLS
Do the following:
- Open the incomplete program in the Question 1 folder.
- Enter your full name as a comment in the first line of the Question1_u.pas file.
- Compile and execute the program. The program has no functionality currently.
- Follow the instructions below to complete the code for each section of QUESTION 1, as described in QUESTION 1.1, QUESTION 1.2, QUESTION 1.3 and QUESTION 1.4.
Your school has created a club to provide information and conduct research on various environmental issues. Complete the program for the club by using the instructions below.
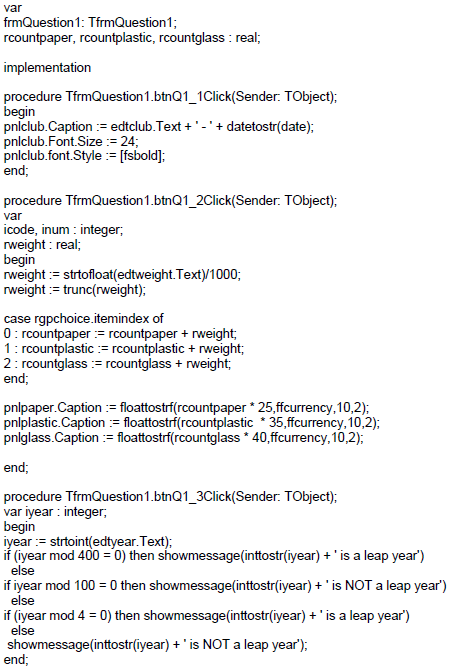
1.1 Button [1.1 Display Club name]
Write code in the Q1.1 event handler to do the following:
- Obtain the name of the club from the edit box named edtclub.
- The system date must be displayed at the end of the name of the club.
- The font of the panel must be set to size 24 and the style of the font must be bold.
- The name of the club and the system date must be displayed in the pane named pnlclub.
Example of output: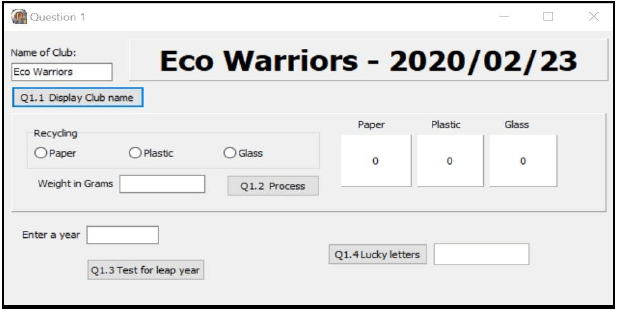
1.2 Button [1.2 Process]
Your school has collected paper, plastic and glass for recycling. The program in the Question 1 folder contains components to keep track of how much the monetary value is for each type of waste material that has been collected. A user will choose a waste material type and then enter the weight for that product. The refund value in Rands for each waste material type must be added up and displayed on the panels provided for paper, plastic and glass.
Write code to do the following:
- Obtain the input from the edit box named edtweight. This number is entered as grams.
- Use the choice selected from the radiogroup box named rgpchoice.
- The unit price paid for each type of waste material is listed below:
Paper = R25 per kilogram
Plastic = R35 per kilogram
Glass = R40 per kilogram
The total price paid for each waste material must be calculated as follows:
- Convert the weight in grams to kg by dividing by 1000.
- Only whole kilograms will be considered for payment and any amount less than 1 kg will not be included. Do NOT round the amount after dividing by 1000.
- Multiply the weight in kg by the correct unit price paid for a waste material type in order to obtain the amount to be paid.
- Add the amount to be paid to a total to be paid for that waste material type.
- Display the total paid for each waste material on the correct panels provided (pnlpaper, pnlplastic and pnlglass).
Use the following data to test your solution:
Material | Weight in g | Weight in kg | Monetary value |
Paper | 356 | 0 | R 0 |
Paper | 1785 | 1 | R 25 |
Paper | 2356 | 2 | R 50 |
Plastic | 3500 | 3 | R 105 |
Plastic | 7854 | 7 | R 245 |
Glass | 1000 | 1 | R 40 |
Glass | 3745 | 3 | R 120 |
Example of output after entering the data in the table above: (16)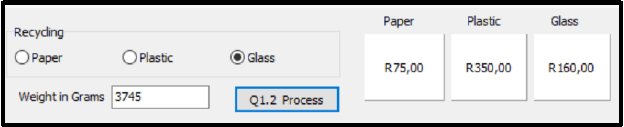
1.3 Button [1.3 Test for leap year]
A leap year has 366 days instead of 365 days. Write code in the onclick event of Q1.3 button to test if a year entered is a leap year.
To check whether a year is a leap year or not, you need to check the following 3 conditions:
- Any year that is divisible by 400 with no remainder is definitely a leap year.
- If it is not divisible by 400, then check if it is divisible by 100. If it is divisible by 100 with no remainder, then it is NOT a leap year (even if it is divisible by 4 with no remainder).
- If the above two conditions are not satisfied, then check for divisibility by
- If it is divisible by 4 with no remainder then it is a leap year.
Do the following:
- Obtain the input from the edit box named edtyear.
- Use the algorithm given above to determine if the year that is entered is a leap year or not.
- Display a suitable message in a message component.
Example of output:
Data to test your solution:
Leap years from 2004 to 2044:
2004
2008
2012
2016
2020
2024
2028
2032
2036
2040
2044
(12)
1.4 Button [1.4 Lucky letters]
Lucky prizes will be awarded to members of the club at a meeting.
Every third letter of the alphabet will be the first letter of the surnames of the winners, starting with the letter ‘A’.
Write code in the onclick event of Q1.4 button to display 9 letters of the alphabet, using the rule described above, in the richedit named reddisplay.
NOTE: String handling and iteration (loops) must be used.
Example of output: (6)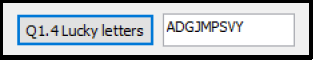
- Enter your name and surname as a comment in the first line of the program file.
- Save your program.
- A printout of the code may be required. [40]
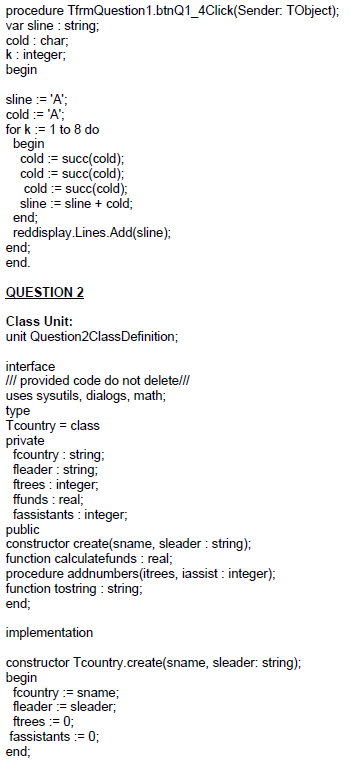
QUESTION 2: OBJECT-ORIENTED PROGRAMMING
| A global organisation named ‘The Tree Project’ has branches around the world. A program is supplied in the QUESTION 2 folder to document the number of trees and workers as well as to calculate the monetary funds required to run this project in a particular country. |
Do the following:
- Open the incomplete program in the Question 2 folder.
- Open the incomplete object class Question2ClassDefinition.pas.
- Enter your name as a comment in both Question2ClassDefinition.pas.and Question2_u.pas.
- Compile and execute the program. Currently the program has no functionality.
- Do NOT remove or change any provided code.
The following user interface is displayed: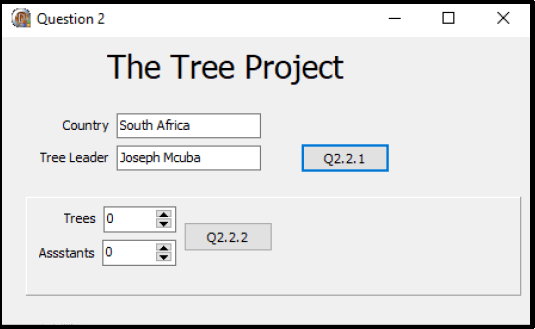
Complete the code for this program, as specified in QUESTION 2.1 and QUESTION 2.2.
2.1 The incomplete class (Tcountry) contains the declaration of five attributes that describe the objcountry object.
NAMES OF ATTRIBUTES | DESCRIPTION |
fcountry | The name of the country |
fleader | The name of the leader for the tree project in a country |
ftrees | The number of trees to be planted |
ffunds | The money required to run the project |
fassistants | The number of people working on the project |
Complete the code in the object class, as described in QUESTION 2.1.1 to QUESTION 2.1.4 below.
2.1.1 Write code for a constructor method named Create that will receive the name of a country and the name of a leader as parameters.
Assign these parameter values to the correct attributes and initialise the attributes for the number of trees and assistants to zero.(5)
2.1.2 Write code for a method named calculatefunds which must use the attributes named ftrees and fassistants to calculate and return the amount of funding needed for the tree project.
The funds are calculated as follows:
- The leader must receive R250
- The cost of planting one tree is R2
- Each assistant must receive R100
Example:
6 assistants and 100 trees: Cost of project = R250 + R600 + R200 = R1050 (6)
2.1.3 Write code for a method named addnumbers that will receive two integer parameters which will each represent the number of trees and the number of assistants with which you will increase the attributes of the class.
Set the value of the attributes as described below:
- Use the attributes named ftrees and fassistants.
- Increase these attributes with the values of the corresponding parameters
- Use the method written previously named calculatefunds to set the attribute named ffunds. (7)
2.1.4 Write code for a method named tostring which must return a string.
The string must contain the attributes of the class joined together in the following format:
<country name>
<leader name> and <number of assistants > assistants
<number of trees> trees
Funds: <amount of funds required in Rands>
Example of output: 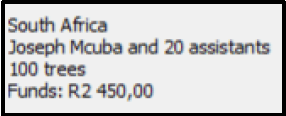
(8)
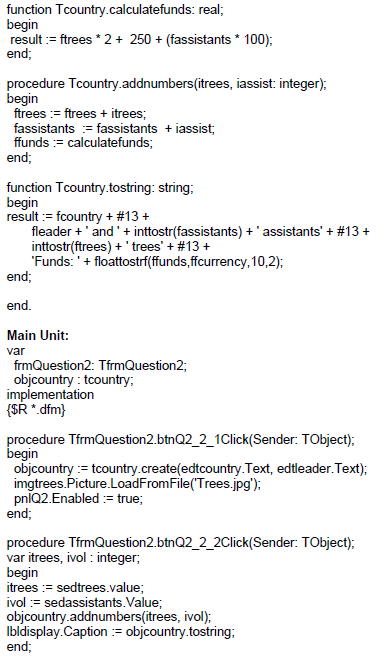
2.2 An incomplete unit Question2_u.pas has been provided.
It contains code for the object class to be accessible and has a global object variable, objcountry, already declared.
Do NOT delete or change any provided code.
Follow the instructions below to code the solution.
2.2.1 Button Q2.2.1
The user will enter a country name and a leader name in the provided edit boxes named edtcountry and edtleader.
Write code to do the following:
- Instantiate the object, objcountry, using the country name and leader name.
- Enable the panel named pnlQ2.
- Load the picture named Trees.jpg into the image component named imgtrees. (6)
2.2.2 Button Q2.2.2
Write code to receive the input from the spinedits named sedtrees and sedassistants.
Use the methods of the class to do the following:
- Increase the number of trees and the number of assistants using the values from the spinedits and calculate the amount of funds required.
- Display the country and leader, as well as the number of trees, assistants and the amount of funds required, in the label named lbldisplay.
Example of output:
Joseph Mcuba as leader in South Africa starting with 30 trees and 5 assistants: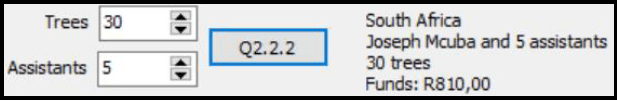
5 trees and 1 assistant added to the South African team with Joseph Mcuba as leader: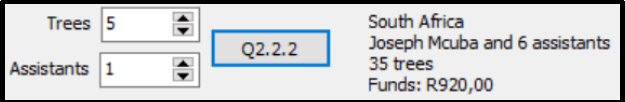
(8)
- Enter your name and surname as a comment in the first line of the program file. (In both the class and the main program that uses the class)
- Save your programs.
- A printout of the code of both units may be required. [40]
QUESTION 3: DATABASE PROGRAMMING
The database WasteDisposal.mdb contains the details of waste materials and disposal methods of a waste management company that manages the permanent removal of all waste for a city. The database contains two tables, namely Material and Disposal.
Table: Disposal
This table contains the methods of disposal of waste.
Field name | Data type | Description |
Disposalcode | Number – Long Integer | A unique number assigned to each profile |
DisposalMethod | Text (50) | The name of the method of waste disposal |
Employees | Number – Long Integer | The number of people required to carry out the disposal method |
Example of data in the Disposal table:
Disposal | ||
Disposalcode | DisposalMethod | Employees |
1 | Recycled | 120 |
2 | Reused | 320 |
3 | Landfill | 11 |
4 | Recoveredforenergy | 24 |
5 | Compostedonsite | 4 |
6 | Compostedoffsite | 10 |
Table: Material
This table contains information of all the waste materials that have been disposed of by the waste management company.
Field name | Data type | Description |
MaterialID | Autonumber | A unique number assigned to the material |
Materialtype | Text (50) | The different types of waste materials |
Datedisposed | Date/Time | Date that the last disposal took place |
Quantity | Number (long integer) | Weight in Tons that was last disposed on the date described in the Datedisposed field |
Greenhousefactor | Number (Double) | Carbon dioxide gas emissions factor for landfills. This number will be multiplied by the tonnage of the material, which results in the total carbon dioxide emission |
Disposalcode | Number (long integer) | Foreign key to connect to the Disposal table |
Example of data of the first ten records of the Material table.
Material | |||||
MaterialID | Materialtype | Datedisposed | Quantity | Greenhousefactor | Disposalcode |
1 | Plasticcontainers | 2019/10/02 | 85 | 0 | 1 |
2 | Plasticbags | 2019/09/28 | 26 | 0 | 1 |
3 | Polystyrene | 2019/07/31 | 45 | 1,8 | 3 |
4 | Glassbottlesbroken | 2019/09/18 | 74 | 0 | 1 |
5 | Glassbottlesnotbroken | 2019/07/10 | 25 | 0 | 2 |
6 | Aluminiumcanswhole | 2019/10/27 | 22 | 0 | 1 |
7 | Aluminiumcansflattened | 2019/08/13 | 14 | 0 | 1 |
8 | AluminiumcansBales | 2019/10/02 | 56 | 0 | 1 |
9 | Steelcanswhole | 2019/08/11 | 98 | 0 | 1 |
10 | Steelcansflattened | 2019/10/23 | 75 | 0 | 1 |
The following one-to-many relationship with referential integrity exists between the two tables in the database: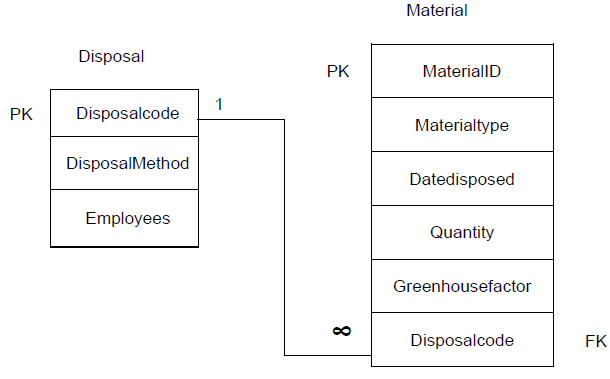
Do the following:
- Open the incomplete project file called Question3_p.dpr in the Question 3 folder.
- Enter your name and surname as a comment in the first line of the Question3_u.pas unit file.
- Compile and execute the program. The program has no functionality currently.
The user interface for all questions is displayed below: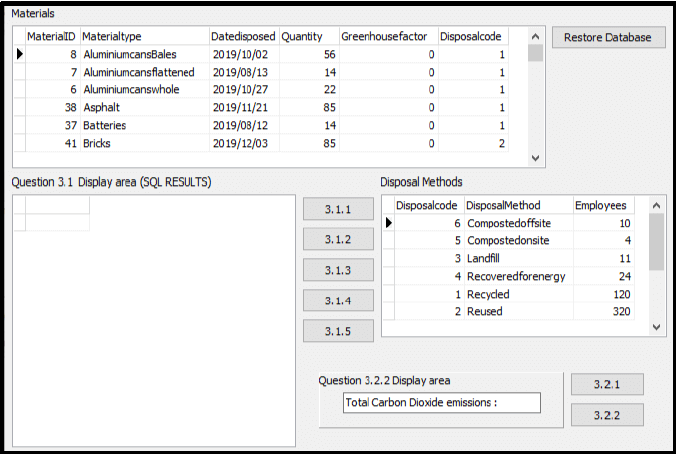
- Follow instructions to complete the code for each question, as described in QUESTION 3.1 and QUESTION 3.2.
- Use SQL statements to answer QUESTION 3.1 and Delphi code to answer QUESTION 3.2.
NOTE:
- The [Restore Database] button is provided to restore your data contained in the database to the original content. If you need to test your code on the original data, you may click this button to restore data.
- Do NOT change any of the code provided.
- Code is provided to link the GUI components to the database.
- TWO variables are declared as global variables, as described in the table below.
- Use tbldisposal and tblmaterial components in Question 3.2 only.
Variable | Data type | Description |
tbldisposal | TADOTable | Refers to the table named Disposal |
tblmaterial | TADOTable | Refers to the table named Material |
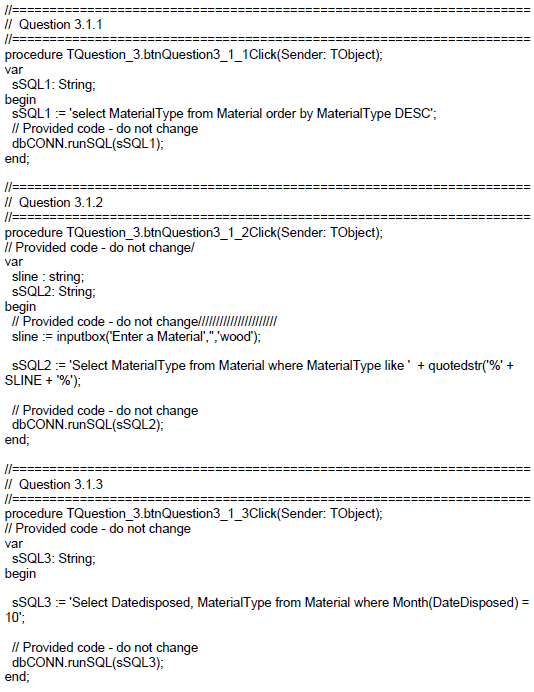
3.1 In this section you may ONLY use SQL statements to answer QUESTION 3.1.1 to QUESTION 3.1.5.
Code to execute the SQL statements and display of the results of the queries is provided. The SQL statements are incomplete.
Do the following to complete the incomplete SQL statements assigned to the variables sSQL1, sSQL2, sSQL3, sSQL4 and sSQL5 per question respectively.
3.1.1 Button [3.1.1]
Write SQL code to display the MaterialType of all materials sorted in reverse alphabetical order.
Example of output of the first 13 records: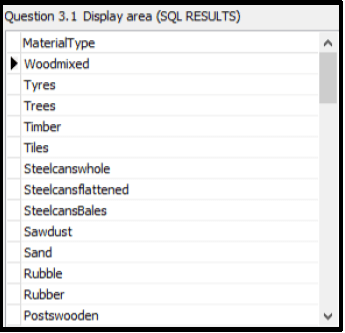 (4)
(4)
3.1.2 Button [3.1.2]
The user must enter the name of a material. Code has been provided for the material name “wood” to be entered in an input box and saved in a variable named sline.
Write SQL code to display the Materialtype of all materials that contain the word stored in the variable sline.
Example of output: 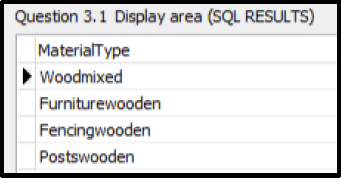 (5)
(5)
3.1.3 Button [3.1.3]
Write an SQL statement to display the Datedisposed and Ma materials disposed in October. (The year 2019 is the only the database.) terialtype of all year recorded in
Example of output: 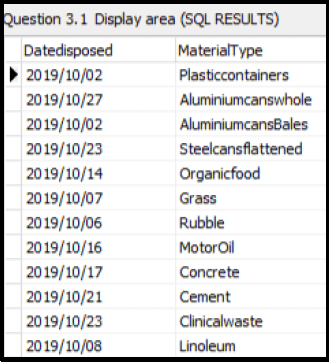 (5)
(5)
3.1.4 Button [3.1.4]
The waste management company is expecting an increase of 10% in the number of employees next year.
Write an SQL statement to add 10% to the number of Employees. Rounding of numbers is not required.
(Code has been written to display the successfully updated table after editing.)
Example of output: 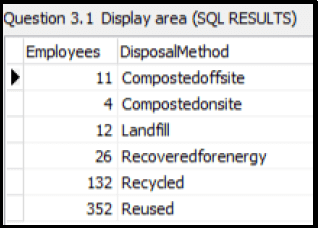 (4)
(4)
3.1.5 Button [3.1.5]
Display the total of all quantities of waste materials (Quantity) as Total_Quantities for each DisposalMethod.
Example of output: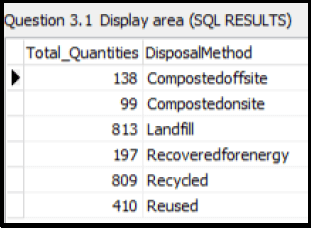 (7)
(7)
3.2 In this section, only Delphi code may be used to answer QUESTION 3.2.1 and QUESTION 3.2.2.
Use the global variables, tblmaterial and tbldisposal, provided.
NO marks will be awarded for SQL statements in QUESTION 3.2.
3.2.1 Button [3.2.1]
Write code to set the Greenhousefactor to 2 for all materials that have a
Disposalcode equal to 6.
Example of output of the last 6 records: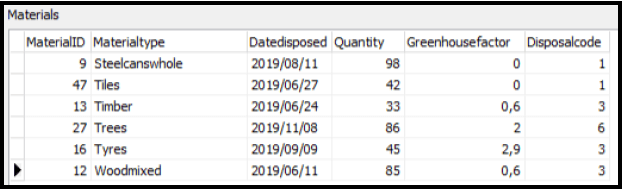 (7)
(7)
3.2.2 Button [3.2.2]
Write code to calculate the total of all carbon dioxide emissions.
CO2 emissions are calculated by multiplying the Greenhousefactor by the Quantity (number of tons) of material waste.
Display the total by adding it to the end of the string located in the edit box named edtdisplay.
Example of output: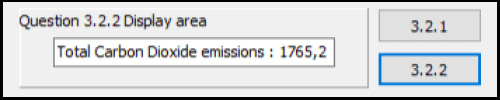 (8)
(8)
- Enter your name and surname as a comment in the first line of the program file.
- Save your program.
- A printout of the code may be required. [40]
QUESTION 4: PROBLEM-SOLVING PROGRAMMING
Do the following:
- Open the incomplete program in the Question 4 folder.
- Enter your name and surname as a comment in the first line of the Question4_u.pas file.
- Compile and execute the program. Currently the program has no functionality.
Supplied GUI:
The supplied GUI represents the interface of the program used by a waste management company to record and report on waste disposal data.
A text file named waste.txt is included which contains the waste materials, method of disposal (either recycled or used as landfill) and the weights measured in kilograms of each material that was disposed of recently by the waste management company.
The format of the text file is:
<Waste material><Disposal method><weight of waste material in kg>
Example of some of the lines in the text file named waste.txt:
Paper;Recycled#2543
Cardboard;Recycled#495
Trash;Landfill#1885
Cardboard;Recycled#398
Trash;Landfill#1657
Paper;Recycled#2754
Cardboard;Recycled#769
Trash;Landfill#2025
Timber;Landfill#2125
Pallets;Recycled#398
Rubber;Recycled#4321
Tyres;Landfill#1258
Metal;Recycled#541
Food;Landfill#774
Grass;Landfill#1142
Trees;Landfill#685
Soil;Landfill#5547
Rubble;Recycled#3984
Clay;Recycled#547
A constant array named arrtypes has been declared and filled with unique waste material types.
arrtypes: array[1..15] of string = ('Paper','Cardboard','Trash','Timber','Pallets','Rubber','Tyres','Metal','Food','Grass','Trees' ,'Soil','Rubble','Clay','Computers');
Code has been written to read the items from each line of the text file into 2 global, parallel arrays, named arrdata and arrweights.
arrdata : array[1..100] of string; arrweights: array[1..100] of integer; icount: integer;
Arrdata contains the name of each waste material joined to either the word Recycled or Landfill with a semicolon separating the two words.
Arrweights contains integers representing the weight of the corresponding waste material in kilograms.
The variable icount holds the total number of items for the two parallel arrays.
Code has been written in the OnActivate event of the form to read data from the text file into the two arrays and then display the array contents into the rich edit.
Complete the code for each question, QUESTION 4.1 and QUESTION 4.2.
NOTE:
- Good programming techniques and modular design must be applied in the design and coding of your solution.
- You may NOT change the code provided.
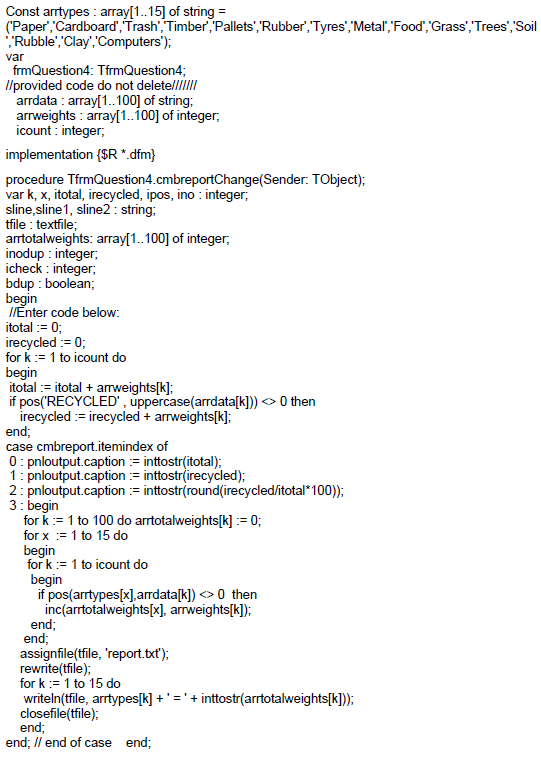
You must write code in the onchange event of the combobox named cmbreport.
Below is a diagram of the 4 options of the combobox.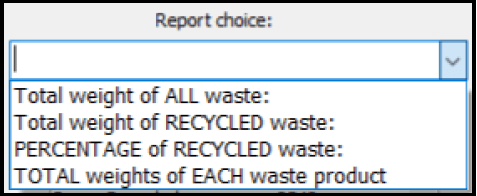
For QUESTIONS 4.1 to 4.4 you must write code for each of the combobox options.
4.1 Combobox option [Total weight of ALL waste]
Calculate and display the total weight of all waste materials collected. The total must be displayed on the panel named pnloutput.
Example of output: 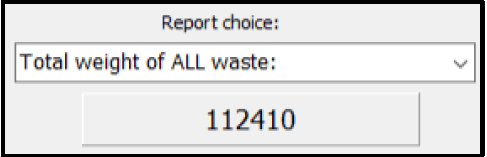 (4)
(4)
4.2 Combobox option [Total weight of RECYCLED waste]
Calculate and display the total weight of all recycled waste material. The total must be displayed on the panel named pnloutput.
Example of output: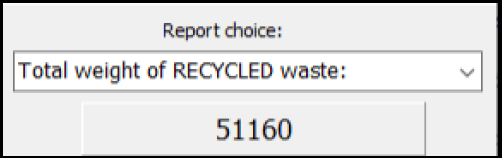 (5)
(5)
4.3 Combobox option [Percentage of RECYCLED waste]
The recycled weight must be divided by the total weight and then multiplied by 100 and rounded to a whole number, in order to calculate the percentage of waste that was recycled.
Display the result on the panel named pnloutput.
Example of output: 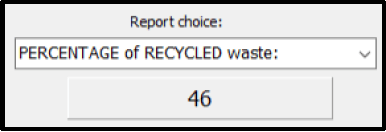 (3)
(3)
4.4 Combobox option [TOTAL weight of EACH waste product]
The array named arrdata has many waste types that are duplicated, eg ‘Cardboard;Recycled’ occurs many times in the array.
The global constant array named arrtypes contains all of the unique types of waste that have been disposed of by the waste management company.
Use this information to calculate the total weights collected for each unique waste type and write the results to a text file named report.txt.
(Note: The text file named report.txt must be created using Delphi code.)
Example of the output to the text file, report.txt:
| Paper = 13332 Cardboard = 6669 Trash = 22606 Timber = 5488 Pallets = 1194 Rubber = 5843 Tyres = 4643 Metal = 1624 Food = 4052 Grass = 5650 Trees = 11801 Soil = 7010 Rubble = 4872 Clay = 4986 Computers = 12640 |
(18)
- Enter your name and surname as a comment in the first line of the program file.
- Save your program.
- A printout of the code may be required.
[30]
TOTAL: 150
Hospitality Studies Grade 12 Memorandum - NSC Past Papers And Memos September 2020 Preparatory Examinations
MEMORANDUM
SECTION A
QUESTION 1
1.1 MULTIPLE-CHOICE ITEMS
1.1.1 B
1.1.2 C
1.1.3 A
1.1.4 A
1.1.5 D
1.1.6 C
1.1.7 B
1.1.8 D
1.1.9 C
1.1.10 A (10 x 1) (10)
1.2 MATCHING ITEMS
1.2.1 G
1.2.2 A
1.2.3 F
1.2.4 B
1.2.5 D (5 x 1) (5)
1.3 MATCHING ITEMS
1.3.1 D
1.3.2 F
1.3.3 E
1.3.4 A
1.3.5 B (5 x 1) (5)
1.4 ONE-WORD ITEMS
1.4.1 Canapé
1.4.2 Nett profit
1.4.3 Method Cap Classique
1.4.4 Demitasse
1.4.5 Chef Pâtissier
1.4.6 Baked Alaska
1.4.7 Chakalaka
1.4.8 Almonds
1.4.9 Bromelain
1.4.10 Mint (10 x 1) (10)
1.5 SELECTION
1.5.1
- A
- B
- C
- D
- G (Any order) (5 x 1) (5)
1.5.2
- A
- B
- D
- F
- G (Any order) (5 x 1) (5)
TOTAL SECTION A: 40
SECTION B: KITCHEN AND RESTAURANT OPERATIONS; HYGIENE, SAFETY AND SECURITY
QUESTION 2
2.1
2.1.1 Pest control:
- Effective measures must be taken to eliminate flies, other insects, rodents or vermin on the food premises.
2.1.2 Refuse bins:
- Refuse bins are cleaned and disinfected regularly / refuse is removed from the food premises or from the room where food is handled as often as necessary / refuse is stored or disposed of in such a manner that it does not create a problem.
2.1.3 Jewellery:
- No person handling food that is not pre-packed may wear any jewellery unless it is suitably covered. (3 x 2) (6)
2.2
- A guide dog accompanying a blind person in the sales or serving area.
- Fish, molluscs or crustaceans that need to be kept alive until prepared for consumption. (2)
2.3
- HIV/Aids weaken the body’s immune system.
- It leaves the body more vulnerable to TB.
- A weakened immune system allows TB to infect parts of the body other than the lungs.
- TB seems to increase the formation of HIV/Aids viruses, thereby weakening the immune system further. (Any 2) (2)
2.4
- There will be a workflow disruption.
- Less workers will lead to low productivity.
- There will be a need for retraining and hiring of workers.
- It will increase indirect costs related to care and treatment of employees.
- There will be vacant posts/ job opportunities for others.
- Less money will be available for investment.
- The worker does not earn money / no money to spend or pay tax.
- Economic growth of the business will be inhibited/ it has a negative impact on the economy / multiplier effect. (Any 4) (4)
2.5
DISEASE | CHOLERA | GASTRO-ENTERITIS |
Causes | Drinking contaminated water / eating food which has been in contact with contaminated water, flies or soiled hands / vibrio cholera (1) | Intake of contaminated foods, drinks or chemicals / Viral / Rota virus or bacterial infection / Salmonella / Staphylococcus / Clostridium / Escherichia(1) |
Symptoms |
|
|
NOTE: NOT diarrhoea / vomiting / abdominal pain / dehydration since it is similarities. | ||
(6)
TOTAL SECTION B: 20
SECTION C:
NUTRITION AND MENU PLANNING; FOOD COMMODITIES
QUESTION 3
3.1
3.1.1
- A – Paris Brest
- B – Croquembouche
- C – Beignets / Churros
- D – Eclairs (4 x 1) (4)
3.1.2
A
- Whipped cream
- Grilled almonds
B
- Spun sugar
C
- Dusted with icing sugar / Rolled in castor sugar
D
- Melted chocolate (Any 4) (4)
3.2
3.2.1 Cheese aigrettes / pommes dauphine (1)
3.2.2 Gougere (1)
3.3 SHORT PASTRY:
- Rub shortening into flour and add cold liquid to form a stiff dough
SWEET PASTRY
- Cream sugar and egg and add to flour mixture. No liquid (2)
3.4
- Work as quickly as possible
- Brush the pastry with melted butter or oil
- Cover the pastry with a wet cloth while working (3)
3.5
3.5.1 Puff pastry / Rough puff
3.5.2 Shortcrust pastry / pâté brisée
3.5.3 Phyllo / purr pastry / Strudel
3.5.4 Sweet pastry / pâté sucrée (4 x 1) (4)
3.6 3.6.1 Rack of Lamb (1)
3.6.2 Baking / frying
Reason:
- It is a soft cut / meat cut from the hind quarter / it is a tender cut and requires little cooking time. (2)
3.6.3 Rib (1)
3.6.4
- AAA – softest meat / young meat
- 222 – little / lean fat (2)
3.6.5
- During resting time meat juices redistribute themselves evenly
- Meat juices will be retained and the dish will be moist inside (2)
3.7
3.7.1 Fish(1)
3.7.2 Eggs (1)
3.7.3 Cheese (1)
3.7.4 Chicken (1)
3.8
3.8.1
- TVP are meat replacement products / High-protein meat substitute.
- They are made from soya beans, wheat, oats and other sources.
- They resemble mincemeat. (3)
3.8.2
- They have the same protein value as meat.
- It is cheaper than meat.
- They look and taste similar to mincemeat dishes.
- They have a long shelf life and can be kept for a year.
- They do not require a fridge / freezer when stored.
- They stretch meat dishes.
- They are convenient to use as they are easy to rehydrate and use in dishes.
- They are low in kilojoules and beneficial to health as they do not contain saturated fat or cholesterol. (Any 3) (3)
3.8.3
- Sausages
- Stews
- Pies
- Hamburgers (Any 3) (3)
[40]
QUESTION 4
4.1
4.1.1
- Net profit = selling price – total costs
Net profit = R100 000 + R45 000 + R50 000 = R195 000
= R450 000 – R195 000
Net profit = R255 00 (4)
4.1.2
- Gross profit / total sales x 100
Gross profit % = (R450 000 – R100 000) / R450 000 x 100
Gross profit % = 77,8% (4)
4.1.3
- R450 000/500
= R900 per person (2)
4.2
4.2.1
- Table d’hôte
Motivation:
- It has a fixed price / it does not have any choices (2)
4.2.2
-
- Change Prawn and Mussel Chowder to another soup/ starter without shellfish, for example Vegetable soup.
- Change Grilled chicken breast by omitting the bacon and feta cheese.
- Add a sauce for example orange sauce or brown sauce. (4)
-
- Remove the mashed potato and substitute it with cauliflower mash or any other vegetables that contains little carbohydrates
OR - Remove the chocolate mousse and replace it with fresh berries / any other suitable low carbohydrate dessert(Any 2) (2)
- Remove the mashed potato and substitute it with cauliflower mash or any other vegetables that contains little carbohydrates
-
- Remove the chocolate mousse and replace it with fresh berries/ any other suitable low carbohydrate dessert (2)
4.3
4.3.1
- The food products will be available all year round / the product will have an extended shelf-life / Food preservation increases the safe storage period of foodstuffs.
- The company will save money, for example instead of buying jam they can produce their own / excess products can be kept for later use.
- Chefs can be creative with new products that they develop that taste much better than store-bought items, for example pickles / jams / it increases the availability of various food stuffs.
- Enzyme action is reduced and the growth of micro-organisms is inhibited.
- Transportation of various foodstuffs is easier. (3)
4.3.2 Food item A
- Freezing
- Pickles
- Atjar (Any 2) (2)
Food item B
- Freezing
- Jam
- Tinned
- Dried
- Atjar
- Chutney (Any 2) (2)
4.4
CLASS | EXPLANATIONS |
French Meringue / Common meringue ü | Beat egg whites into a soft peak and gradually add sugar ü |
Swiss Meringue ü | Beat egg whites and sugar over a bain- marie until sugar is dissolved ü |
Italian Meringue ü | A hot syrup is poured onto egg whites while it is being whipped ü |
(6)
4.5
4.5.1 The mixture can lose its thickening ability and will not set. (1)
4.5.2
- Orange juice will increase the acid content.
- The mixture will melt more easily / will have a softer jelly. (2)
4.5.3
- Raw figs contain proteolytic enzymes / ficin that will break down the gelatine.
- The mixture will lose its setting ability / it will be a runny mixture instead of a firm jelly or mould/gel will not form/hydrolyse the gelatine. (2)
4.5.4 Freezing will cause water to ooze out of the gelatine dish / syneresis will occur. (1)
4.5.5 The egg custard will curdle. (1)
[40]
TOTAL SECTION C: 80
SECTION D: SECTORS AND CAREERS
FOOD AND BEVERAGE SERVICE QUESTION 5
5.1
5.1.1
- Training as a chef
- 20 years of experience in the hospitality industry
- He is used to working long hours
- He has lots of energy and enthusiasm
- Exceptional culinary creativity
- His products are of high quality and standard (Any 4) (4)
5.1.2 His exceptional culinary creativity / his signature dish of orange-and- prickly pear sauce. (1)
5.1.3 A signature dish is a recipe that is unique and associated with an individual chef or restaurant. (1)
5.1.4
- Goals and strategy
A broad overview of your core business / your target market and clear targets for what you want to achieve. (2) - Operational plans
It describes how the business will operate and the details and costs for manufacturing, delivering, stock control, merchandising and storing. (2) - Financial plans
A list of expenses and possible income / calculations of possible expenses and income to see whether the business have the potential to be profitable. (2)
5.1.5
- New entrants into the market – The more companies enter the market; the less profit can be generated and vice versa.
- The customer’s bargaining power – If customers have a lot of power, they can keep the prices relatively low, thereby reducing profit margins.
- Substitute products – Similar products that is more attractive or cheaper can result in lower profit margins.
- Bargaining power of suppliers of ingredients and packaging – If suppliers have a lot of power, they can determine the terms at which they supply the materials, thereby reducing the profit margin.(Any 3 x 2) (6)
5.1.6
- Chef
- Kitchen assistant
- Cleaner
- Marketing manager
- Delivery person/sales person
- Admin clerk (Any 2)(2)
5.1.7
- The font letter type is not easily readable.
- Font size of types of sauces and address is too small.
- Potential customers might be drawn to ‘best in town’.
- The pictures used is of the ingredients and not of the actual product.
- The price is not shown.
- The volume of containers is not shown.
- The type of packaging is not shown.
- Only website is shown; not any other contact details. (Any 5) (5)
5.2
Revenue-generating | Non-revenue-generating |
bar | housekeeping |
banquet room | finance |
maintenance |
(5) [30]
QUESTION 6
6.1
6.1.1 To adjust the cutlery that was originally laid to meet a guest’s specific order. (1)
6.1.2
- If there were choices in the same meal, the cover will have to be adjusted according to the selection of the guest.
- If a traditional place setting was used and a guest orders fish for main course, the joint knife and fork will be replaced with a fish knife and fork.
- Glassware that guests are not going to use must be removed.
- Covers are corrected after orders have been taken and placed with the kitchen.
- Covers may be corrected up to and including the main course.
- Place the required items in the sequence of use. (Any 3) (3)
6.2
- Deal with the situation calmly and professionally.
- Quickly diffuse the problem.
- Let the guest describe without interruption what went wrong. / Listen and pay attention.
- Apologies should sound sincere and convincing.
- Do not make excuses or blame anyone else.
- Be polite. / control your emotions.
- Never offer something you cannot deliver.
- Check back.
- Acknowledge the complaint and thank the guest for bringing the matter to your attention.
- If you cannot handle the complaint, call the Maître d’hôtel or your supervisor to assist. (Any 5) (5)
6.3
- Maintain high quality service standards / acknowledge guests within 30 seconds of entering the restaurant/ handing guests the menu within 2 minutes of their arrival /show that you are genuinely pleased to see customers and serve them properly.
- Answer guests’ enquiries about food and drinks available/ take an interest in their orders and make appropriate suggestions regarding menu choices/make an eye contact.
- Meet special needs of guests, for example dietary and religious requirements, child seats, wheelchair access, and a non-smoking area. / be aware of customers moods
- Provide adequate service levels, for example, how long guests have to wait for special dishes and the facilities and services the restaurant offers, such as toilets and safe parking areas /apologise if customers have been kept waiting.
- Remember what regular guests eat and drink and if they have special requests, for example a favourite table.
- Use guests’ names but always respect their privacy.
- Be professional and friendly at all times.
- Make sure that guests never have to wait for the bill and always accept gratuities with thanks.
- Show respect and courtesy to people and their cultural practices.
- All customers should e treated equally and with the necessary respect and dignity. (Any 5) (5)
6.4
6.4.1 Sauvignon Blanc / Chenin Blanc
6.4.2 Shiraz
6.4.3 Pinotage
6.4.4 Cabernet Sauvignon
6.4.5 Port (5)
6.5
- Make sure that the sparkling wine is well chilled.
- Serve it in a flute shaped glass.
- Pour from the right side.
- Use the correct way of opening the bottle.
- Lift the glass and bottle at a slight angle / 45°.
- Pour slowly along the side of the glass.
- Pour the glass ⅔ to ¾ full
- Put the glass down. (Any 4) (4)
6.6 On-consumption license
- The establishment is allowed to serve liquor with a meal, but not allowed to let guests remove open bottles of alcohol from the premises / liquor to be consumed where it is bought, but not taken off the premises.
- Example: hotels, restaurants, pubs, theatres, clubs, sports grounds, temporary venues.
Off-consumption license
- The establishment sell alcohol, but customers are not allowed to open bottles or drink alcohol on the premises / sells liquor that will be consumed elsewhere.
- Example: liquor stores, grocers, wine farms / wholesalers / liquor outlets. (4)
6.7
- Ideally it should be stored in an underground cellar that is free from vibrations.
- The cellar should be free from excessive dampness, draughts and unwanted odours.
- The cellar should be absolutely clean, well-ventilated, with only subdued lighting / wine must be kept in the dark to avoid damage from ultra violet light.
- The cellar should have a constant temperature of 10 °C–12 °C/ 14 °C–16 °C.
- A humidity level of 70% is ideal to prevent corks from drying out.
- Bottles with corks should lie on their sides to prevent the cork from drying out.
- Store wines upside down in a box.
- Red wine should be stored in a slightly raised position with the corks at the top.
- Rotate wine on regular basis.
- Store similar wines together.
- Pack and store wines bottles with the label to the top or to the front.
- When wine is stored in cardboard boxes, the arrows should face up. (Any 3) (3)
[30]
TOTAL SECTION D: 60
GRAND TOTAL: 200
Hospitality Studies Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
INSTRUCTIONS AND INFORMATION
- This question paper consists of FOUR sections.
SECTION A: Short questions (All topics) (40)
SECTION B: Kitchen and restaurant operations;
Hygiene, safety and security (20)
SECTION C: Nutrition and menu planning;
Food commodities (80)
SECTION D: Sectors and careers;
Food and beverage service (60) - Answer ALL the questions in your ANSWER BOOK.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: SHORT QUESTIONS
1.1 MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the correct answer and write only the letter (A–D) next to the question numbers (1.1.1–1.1.10) in the ANSWER BOOK, for example 1.1.11 C.
EXAMPLE:
1.1.11 A good source of proteins is …
- oranges.
- pumpkin.
- meat.
- cornflour.
ANSWER: 1.1.11 C
1.1.1 Dried beans should be ... before cooking.
- grated
- soaked
- roasted
- blanched (1)
1.1.2 A suitable cooking method for lamb neck:
- Grilling
- Frying
- Stewing
- Roasting (1)
1.1.3 In South Africa red sparkling wine is made from ... grapes.
- Pinotage
- Chardonnay
- Riesling
- Colombar (1)
1.1.4 A fruit jelly for vegetarians will be set with ...
- agar-agar.
- aspic.
- potato starch.
- gelatine. (1)
1.1.5 A suitable glaze for a cold strawberry tart:
- Blackberry sauce
- Aspic jelly
- Egg wash
- Apricot syrup (1)
1.1.6 Vegetarians can substitute meat with ... in their diet.
- spinach
- bone broth
- tofu
- egg plant (1)
1.1.7 Identify a dish that is NOT suitable for a Jewish person:
- Grilled snoek
- Beef lasagne
- Meat balls with tomato sauce
- Grilled chicken breast (1)
1.1.8 Sorbet, as a palate cleanser, is served ...
- before the canapés.
- after the main course.
- after the cheese and biscuits.
- before the main course. (1)
1.1.9 The service gear a waiter needs for silver service:
- Carving set
- Moveable trolley
- Spoon and fork
- Soup ladle (1)
1.1.10 Food service workers who suffer from Hepatitis A, should be excluded from work for ... weeks after contracting the illness.
- six
- three
- one
- five (1)
1.2 MATCHING ITEMS
Match the snack food in COLUMN B that best suits an event in COLUMN A. Write only the correct letter (A–G) next to the question numbers (1.2.1–1.2.5) in your ANSWER BOOK, for example 1.2.6 H.
COLUMN A | COLUMN B | ||
EVENT | SNACK FOOD | ||
1.2.1 | Ladies’ book club in summer | A | Chocolate truffles |
1.2.2 | High tea | B | Samoosas |
1.2.3 | Seafood buffet | C | Spaghetti Bolognese |
1.2.4 | Indian theme evening | D | Melon kebab |
1.2.5 | Picnic basket for a fruitarian | E | Tomato soup |
F | Sushi | ||
G | Crudités |
(5 x 1) (5)
1.3 MATCHING ITEMS
Choose an example from COLUMN B that matches a marketing mix in COLUMN A. Write only the correct letter (A–G) next to the question numbers (1.3.1–1.3.5) in your ANSWER BOOK, for example 1.3.6 H.
COLUMN A | COLUMN B | ||
MARKETING MIX | EXAMPLE | ||
1.3.1 | Packaging | A | Hamburgers made from organic meat |
1.3.2 | Place | B | Clients save 20% by buying seasonal tickets |
1.3.3 | People | C | Safety measures are adhered to |
1.3.4 | Product | D | Compostable burger box |
1.3.5 | Price | E | Factory workers who want to buy lunch |
F | Mobile food truck at the entrance of large car plant | ||
G | Special opening discount for the first 3 weeks |
(5 x 1) (5)
1.4 ONE-WORD ITEMS
Give ONE word/term for EACH of the following descriptions. Write ONLY the word/term next to the question numbers (1.4.1–1.4.10) in the ANSWER BOOK.
1.4.1 A type of bite-sized hors d’œuvre consisting of a small piece of bread, puff pastry, or a cracker topped with some savoury food
1.4.2 The income you get from selling a product, minus all the expenses
1.4.3 South African sparkling wines made in the traditional French method
1.4.4 A small cup used to serve espresso coffee
1.4.5 The French term for a chef who is trained in the making of pastries, desserts, bread and other baked goods
1.4.6 Ice cream on a sponge cake base which is covered with meringue and then caramelised
1.4.7 South African vegetable relish, usually spicy, that is traditionally served with bread, pap, samp, stews or curries
1.4.8 The nut that is the main ingredient in marzipan
1.4.9 The enzyme in fresh pineapple that prevents setting
1.4.10 A jelly that is served with the classic roast leg of lamb (10 x 1) (10)
1.5 SELECTION
1.5.1 Identify FIVE food items in the list below that can cause food allergies. Write only the letters (A–G) next to the question number (1.5.1) in the ANSWER BOOK.
- Crème Caramel
- Nuts
- Ciabatta
- Tartrazine
- Stewed apples
- Chocolate
- Avocado Ritz (5 x 1) (5)
1.5.2 Identify FIVE ways for large hotel kitchens to save water. Write only the letters (A–G) next to the question number (1.5.2) in the ANSWER BOOK.
- Invest in dishwashers
- Use a large bowl to rinse fruit and vegetables. Then use the leftover water for plants
- Install a high flow spout
- Turn off the faucet when not rinsing dishes
- Defrost food in water
- Use less water to boil food in
- Avoid running the spout needlessly (5 x 1) (5)
TOTAL SECTION A: 40
SECTION B:
KITCHEN AND RESTAURANT OPERATIONS; HYGIENE, SAFETY AND SECURITY
QUESTION 2
2.1 Elaborate on the government’s regulations regarding prevention of food contamination in Government Notice No. R918 of July 1999 regarding:
2.1.1 Pest control
2.1.2 Refuse bins
2.1.3 Jewellery (3 x 2) (6)
2.2 Animals are not permitted in areas where food is handled. Mention TWO exceptions. (2)
2.3 Explain the connection between HIV/Aids and tuberculosis. (2)
2.4 Chefs who are infected with tuberculosis will probably be absent from work quite frequently. Discuss the effect of this absence on our country’s economy. (4)
2.5 Some of the symptoms of cholera overlap with the symptoms of gastro- enteritis. Compare the differences between cholera and gastro-enteritis with regard to the causes and symptoms. Tabulate your answer as follows:
DISEASE | CHOLERA | GASTRO-ENTERITIS | |
Causes | (1) | (1) | |
Symptoms | (2) | (2) | |
(6)
TOTAL SECTION B: 20
SECTION C: NUTRITION AND MENU PLANNING; FOOD COMMODITIES
QUESTION 3
3.1 Study the pictures of choux pastry dishes below and answer the questions that follow.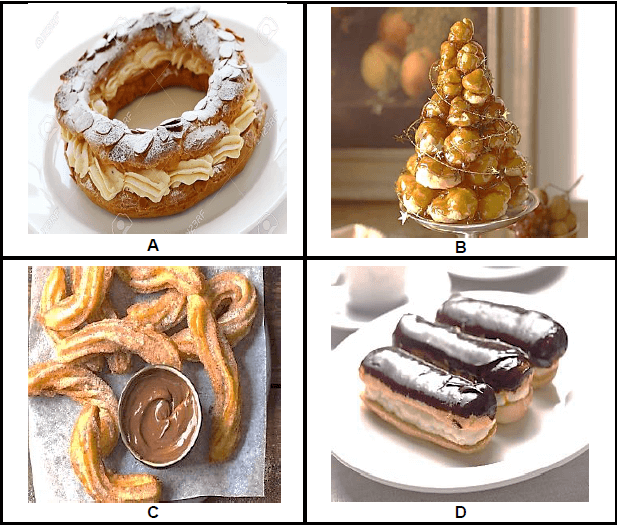
3.1.1 Identify each choux pastry dish above. (4)
3.1.2 Differentiate between FOUR different methods that were used to serve each dish attractively. (4)
3.2 Suggest a suitable savoury choux pastry dish that comply with the following criteria:
3.2.1 Deep fried, suitable for a lacto-ovo vegatarian (1)
3.2.2 Served as a light meal with a salad (1)
3.3 Briefly describe how the preparation of short pastry (pâté brisée) and sweet pastry (pâté sucrée) differ. (2)
3.4 Supply THREE possible solutions for the following: Phyllo pastry tend to dry out during preparation (3)
3.5 Recommend a suitable type of pastry for the following dishes:
3.5.1 Beef Wellington
3.5.2 Quiche Lorraine
3.5.3 Samoosas
3.5.4 Fruit tartlet (4 x 1) (4)
3.6 Study the picture of a lamb cut below and answer the questions that follow.
3.6.1 Identify the dish above. (1)
3.6.2 Suggest a suitable cooking method for the dish. Motivate your answer. (2)
3.6.3 Identify the meat cut used in the above dish. (1)
3.6.4 Explain the meaning of the roller mark AAA 222 on this particular meat cut. (2)
3.6.5 Motivate the chef’s instruction to ‘rest’ the roasted meat before serving. (2)
3.7 Choose from the list below ONE food item which is included in the diet of the following types of vegetarians:
| cheese; beef; fish; eggs; chicken |
3.7.1 Pesco (1)
3.7.2 Ovo (1)
3.7.3 Lacto (1)
3.7.4 Pollo (1)
3.8
3.8.1 Explain what Textured Vegetable Proteins (TVP) are. (3)
3.8.2 Analyse the advantages of using Textured Vegetable Proteins (TVP) as replacement for meat. (3)
3.8.3 Compose a list of THREE possible ways to incorporate Textured Vegetable Proteins (TVP) in mincemeat dishes. (3)
[40]
QUESTION 4
4.1 Study the spreadsheet of the costing of a large exclusive banquet given below and answer the questions that follow.
Banquet: 500 people | |
COSTS | AMOUNT |
Ingredients | R100 000 |
Labour | R45 000 |
Overheads | R50 000 |
Net profit | |
Net profit % | |
Sales/ Income | R450 000 |
Gross profit | |
Gross profit % | |
4.1.1 Calculate the net profit. Show ALL formulas and calculations. (4)
4.1.2 Calculate the gross profit percentage. Show ALL formulas and calculations. (4)
4.1.3 Calculate the cost of the event for each guest. (2)
4.2 Study the menu below and answer the questions that follow. 
4.2.1 Identify the type of menu above. Motivate your answer. (2)
4.2.2 Adapt the menu to suit the following special needs:
- Jewish religion (4)
- Low carbohydrates diet (2)
- Diabetic (2)
4.3 Study the pictures below and answer the questions that follow.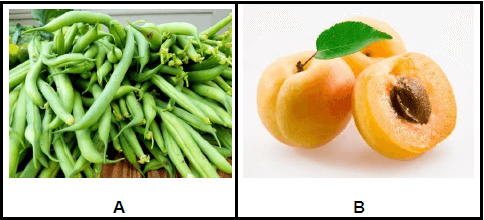
4.3.1 A hotel kitchen’s garden produced more of the above fruits and vegetables that they were able to consume. Convince the chef to preserve these food items by stating THREE advantages of preserving food. (3)
4.3.2 Suggest TWO ways how each of the above food items can be preserved.
- Food item A (2)
- Food item B (2)
4.4 Classify meringues in THREE groups and explain how the preparation of each differs. Tabulate your answer as follows.
CLASS | EXPLANATION |
(3 x 2) (6)
4.5 Predict the effect of each of the following steps on the texture of a gelatine dessert:
4.5.1 The gelatine mixture boiled (1)
4.5.2 Water was substituted with orange juice (2)
4.5.3 Raw fig puree was used (2)
4.5.4 The dish was left in the freezer overnight (1)
4.5.5 Gelatine was added to hot egg custard (1) [40]
TOTAL SECTION C: 80
SECTION D:
SECTORS AND CAREERS; FOOD AND BEVERAGE SERVICE
QUESTION 5
5.1 Read the extract below and answer the questions that follow.
Pedro is a trained chef and has worked in the hospitality industry for 20 years. After many months of planning and research he decided to start his own business from home. He is used to working long hours and wants to put his energy and enthusiasm into his own pocket. He will prepare and bottle a large variety of salad dressings and sweet dessert sauces. His culinary creativity is exceptional and his products are of high quality and standard. His signature dish is his Orange-and-Prickly Pear Sauce. |
5.1.1 Identify FOUR strengths that Pedro has that can contribute to his success as an entrepreneur. (4)
5.1.2 Point out Pedro’s competitive advantage of his business. (1)
5.1.3 Explain the term signature dish. (1)
5.1.4 Give a brief summary of each of the following aspects that must be included in Pedro’s business plan:
- Goal and strategy (2)
- Operations plan (2)
- Financial plan (2)
5.1.5 Investigate THREE possible marketing forces that Pedro will have to reckon with. (3 x 2)(6)
5.1.6 Predict TWO work opportunities that can be developed from Pedro’s business.(2)
5.1.7 Criticise Pedro’s digital poster for his Facebook page as an effective marketing tool.
(5)
5.2 Classify each of the following into revenue-generating and non-revenue- generating areas of a hotel:
| housekeeping; bar; finance; banquet room; maintenance |
Tabulate your answer as follows:
REVENUE-GENERATING | NON-REVENUE-GENERATING |
(5)
[30]
QUESTION 6
6.1
6.1.1 Explain what the term to correct a cover means. (1)
6.1.2 List THREE different scenarios where a waiter needs to correct a cover. (3)
6.2 Compile a list of FIVE guidelines on how to successfully respond to difficult guests during food service. (5)
6.3 Maintaining a regular client base depends on good guest relationships. Formulate FIVE guidelines for restaurant staff to follow in order to build excellent guest relations. (5)
6.4 Select from the list below a suitable wine cultivar to be served with the following dishes:
| Sauvignon Blanc; Port; Cabernet Sauvignon; Pinotage; Shiraz; Chenin Blanc |
6.4.1 Fried hake and chips
6.4.2 Lamb curry stew
6.4.3 Grilled Kudu steak
6.4.4 Mature cheddar
6.4.5 Baked chocolate pudding (5)
6.5 Outline FOUR guidelines to follow when serving sparkling wine to guests. (4)
6.6 Distinguish between an on-consumption liquor licence and an off-consumption liquor licence with examples. (4)
6.7 Discuss THREE points to consider when storing wine. (3)
[30]
TOTAL SECTION D: 60
GRAND TOTAL: 200
History Paper 2 Grade 12 Memorandum - NSC Past Papers And Memos September 2020 Preparatory Examinations
MEMORANDUM
SECTION A: SOURCE-BASED QUESTIONS
QUESTION 1: HOW DID THE PHILOSOPHY OF BLACK CONSCIOUSNESS INFLUENCE THE SOUTH AFRICAN YOUTH IN THE 1970s?
1.1
1.1.1 [Definition of historical concepts from Source 1A – L1]
- Accepting oneself as black/self-value/self-esteem/self-worth
- To be proud of what you are/black pride
- Black South Africans should be proud of themselves and should strive for self-reliance
- Black South Africans should become independent
- Any other relevant response (Any 1 x 2)(2)
1.1.2 [Interpretation of evidence from Source 1A – L2]
- Motivated blacks to unite and fight against apartheid
- Black South Africans should stand up and fight for their rights
- Black South Africans should change their mindset
- Blacks should stop feeling inferior
- Any other relevant response (Any 2 x 2)(4)
1.1.3 [Extraction of evidence from Source 1A – L1]
- It mobilised the people when all the major political opposition was banned, their leaders in exile or in jail (1 x 2)(2)
1.1.4 [Evaluate the usefulness of the evidence from Source 1C – L3]
This source is useful because:
- It became the mouth piece/voice of the oppressed people in South Africa
- It filled the political vacuum that existed at that stage
- It made black South Africans aware not to accept their oppression by the apartheid government
- Any other relevant response (Any 2 x 2)(4)
1.1.5 [Extraction of evidence from Source 1A – L1]
- Independent thinking
- Self-reliance
- Fearlessness
- Dignity (4 x 1)(4)
1.2
1.2.1 [Extraction of evidence from Source 1B – L1]
- Self-concept
- Self-esteem (2 x 1)(2)
1.2.2 [Interpretation of evidence from Source 1B – L2]
- The apartheid government saw the BCM as a threat
- Many leaders were imprisoned/banned
- Any other relevant response (Any 1 x 2)(2)
1.2.3 [Extraction of evidence from Source 1B – L1]
- There were forces that threatened to deal with them
- Denied employment if we didn’t abandon our political beliefs (2 x 1) (2)
1.3
1.3.1 [Extraction of evidence from Source 1C – L1]
- Because they spread the ideas of Black Consciousness (1 x 2) (2)
1.3.2 [Interpretation of evidence from Source 1C – L2]
- Major anti-apartheid organisations were banned at this stage
- Influenced by the BCM, they learned to resist apartheid
- They became aware of their social, political and economic oppression they endured
- Any other relevant response (Any 2 x 2) (4)
1.3.3 [Interpretation of evidence from Source 1C – L2]
- He was banned
- Detained
- Could not leave King William’s Town
- He could not attend meetings
- The police often searched his home to check on him
- Could not write for newspapers or magazines
- He was refused a passport and could not leave the country
- Any other relevant response (Any 1 x 2) (2)
1.3.4 [Interpretation of evidence from Source 1C – L2]
- Wanted to maintain white minority rule
- Saw the Black Consciousness Movement as a threat
- Perceived the Black Consciousness Movement as agitators that wanted to overthrow the government
- Any other relevant response (Any 1 x 2) (2)
1.4 1.4.1 [Interpretation of evidence from Source 1D – L2]
- Fearless
- Independent
- Prepared to die for his beliefs
- He lived according to his beliefs
- Any other relevant response (Any 2 x 2) (4)
1.4.2 [Interpretation of evidence from Source 1D – L2]
- Power to the people (1 x 2) (2)
1.5 [Comparison of evidence from Sources 1A and 1D – L3]
- Both sources reveal that the BCM influenced the youth
- Both sources show that the youth were taught to become fearless
- Any other relevant response (2 x 2) (4)
1.6 [Interpretation, comprehension and synthesis of evidence from relevant sources – L3]
Candidates can include the following aspects in their responses:
- BCM mobilised the people (Source 1A)
- BCM instilled independent thinking, self-reliance, fearlessness and dignity (Source1A)
- Broke the silence of the time (Source 1A)
- It conscientised black South Africans to stand up against oppression (Own knowledge)
- Young blacks refused to be held in an inferior position (Own knowledge)
- Students were at the forefront of the struggle (Source 1B)
- Black people to be proud of their colour (Source 1B)
- Made black South Africans realise their self-worth (Source 1B)
- Conscientised black students to reject apartheid (Source 1B)
- Led to the formation of community organisations (Own knowledge)
- Students influenced through the writings of Biko (Source 1C)
- Influenced by the BCM, students became fearless (Source 1A and 1D)
- Transformed into disciplined young black men (Source 1C)
- Any other relevant response
Use the following rubric to allocate a mark:
LEVEL 1 |
| Marks: 0–2 |
LEVEL 2 |
| Marks: 3–5 |
LEVEL 3 |
| Marks: 6–8 |
(8)
[50]
QUESTION 2:
HOW SUCCESSFUL WAS THE TRUTH AND RECONCILIATION COMMISSION (TRC) IN DEALING WITH THE MURDER OF AMY BIEHL?
2.1
2.1.1 [Extraction of evidence from Source 2A – L1]
- Establish the causes, nature and extent of the gross violation of human rights
- Conducting investigations and holding hearings
- To facilitate the granting of amnesty to persons who made full disclosure of all the relevant facts, related to acts associated with a political objective
- Restore the human and civil dignity of victims
- Recommend reparation measures
- To compile a report of its findings and activities and recommend measures to prevent future violations of human rights (Any 2 x 1)(2)
2.1.2 [Interpretation of evidence from Source 2A – L2]
- Apartheid violated the rights of most South Africans
- Apartheid discriminated against South Africans based on the colour of their skin
- Any other relevant response (Any 1 x 2)(2)
2.1.3 [Definition of historical concepts from Source 2A – L2]
- Is the granting of official pardon for people that committed politically related offences
- Any other relevant response (1 x 2) (2)
2.1.4 [Evaluate the usefulness of the evidence from Source 2B – L3]
This source is useful because:
- It explains the reasons for the establishment of the TRC
- It gives an overview of the period being investigated
- It gives the reasons for the need of a TRC
- It gives information on the committees that will perform the duties of the TRC
- Any other relevant response (Any 2 x 2) (4)
2.1.5 [Extraction of evidence from Source 2A – L1]
- Human Rights Violation Committee
- Amnesty Committee
- Reparation and Rehabilitation Committee (3 x 1) (3)
2.2
2.2.1 [Extraction of evidence from Source 2B – L1]
- She was a victim of racial violence
- She was white (2 x 1) (2)
2.2.2 . [Extraction of evidence from Source 2B – L1]
- Beaten
- Stabbed (2 x 1) (2)
2.2.3 [Interpretation of evidence from Source 2B – L2]
- She was an anti-apartheid activist
- She did legal research for the ANC
- Assisted with voter registration/education
- Worked with underprivileged communities
- Any other relevant response (Any 2 x 2) (4)
2.2.4 [Interpretation of evidence from Source 2B – L2]
- To kill white people
- By killing the white people, they would get their land back
- Wanted to end apartheid
- Wanted whites to feel what blacks had to endure
- Any other relevant response (Any 2 x 2) (4)
2.3
2.3.1 [Extraction of evidence from Source 2C – L1]
- Mzikhona Nofemela
- Ntobeka Peni
- Vusumzi Ntamo
- Mongezi Manqina (Any 3 x 1) (3)
2.3.2 [Interpretation of evidence from Source 2C – L2]
- Wanted their forgiveness
- Wanted amnesty
- Showed remorse for their senseless deeds
- Any other relevant response (Any 2 x 2) (4)
2.3.3 [Extraction of evidence from Source 2C – L1]
- “I feel sorry and very down-hearted, especially today, realising the contribution Amy Biehl played in the struggle” (1 x 2) (2)
2.4
2.4.1 [Interpretation of evidence from Source 2D – L2]
- It provided a platform for perpetrators to tell their stories
- It provided a platform for victims to find closure
- Any other relevant response (Any 1 x 2) (2)
2.4.2 Interpretation of evidence Source 2D – L2]
- To tell the truth
- To prove that their actions were politically motivated
- To be released from jail
- Any other relevant response (Any 1 x 2) (2)
2.5 [Comparison of evidence from Sources 2C and 2D – L3]
- Source 2C indicates that the killers of Amy Biehl applied for amnesty and Source 2D shows them appearing before the Amnesty Commission
- Both sources reveal that it provided a platform for the killers to reveal the truth of their atrocities
- Both sources show they showed remorse for their actions
- Any other relevant response (Any 2 x 2) (4)
2.6 [Interpretation, comprehension and synthesis of evidence from sources – L3]
Candidates could include some of the following:
- The reason for the establishment of the TRC was to deal with the past (Source 2A)
- The TRC offered full amnesty to those who came forward and confessed their crimes (Source 2A)
- TRC provided a platform for the killers of Amy to reveal the truth about the reasons for their actions (Source 2C)
- Peni revealed the truth of their actions and claimed that it was politically motivated at his amnesty hearing (Source 2C)
- Victims had the opportunity to confront those who hurt their loved ones (Own knowledge)
- Perpetrators had the chance to show remorse (Source 2C and 2D)
- The TRC provided a platform for the parents of Amy to give their opinions on the amnesty process (Source 2C)
- Victims found out for the first time what happened to their loved ones and how they had died (Own knowledge)
- Parents forgave the perpetrators (Source 2C)
- Perpetrators were released from jail (Source 2C)
- Perpetrators received amnesty (Source 2C and 2D)
- The Amy Biehl Foundation was set up by her parents to commemorate Amy (Own knowledge)
- Perpetrators are working at the foundation level, doing community work and help to prevent violence (Own knowledge)
- Any other relevant response
Use the following rubric to assess this paragraph.
LEVEL 1 |
| Marks: 0–2 |
LEVEL 2 |
| Marks: 3–5 |
LEVEL 3 |
| Marks: 6–8 |
(8)
[50]
QUESTION 3:
WHAT MPACT DID MULTI-NATIONAL CORPORATIONS (MNC’S) HAVE ON GLOBAL CULTURES IN THE 1990s?
3.1
3.1.1 [Definition of historical concepts from Source 3A – L1]
- Refers to the technological, political and economic changes which have resulted in the world functioning in a different way from what it did 20 years ago
- Any other relevant explanation (1 x 2)(2)
3.1.2 [Extraction of evidence from Source 3A – L1]
- International trade
- Investment (2 x 1)(2)
3.1.3 [Extraction of evidence from Source 3A – L1]
- ‘For thousands of years, people – and later, corporations – have been buying from and selling to each other in lands at great distances’ (1 x 2)(2)
3.1.4 [Interpretation of evidence from Source 3A – L2]
- Less trade barriers between countries
- Mass production by MNC’s led to cheaper products
- Technological advances enable goods to move faster between countries
- Many countries have adopted a free-market economic system
- Any other relevant response (Any 2 x 2)(4)
3.2
3.2.1 [Extraction of evidence from Source 3B – L1]
- American countries
- European countries (2 x 1)(2)
3.2.2 [Extraction of evidence from Source 3B – L2]
- Television
- Radio
- Satellite
- Internet (Any 2 x 1)(2)
3.2.3 [Interpretation of evidence from Source 3B – L2]
- Consumers have access to a variety of goods and services
- Inter-connectedness of the world through information technology
- People can learn about other people’s cultures and traditions
- Any other relevant response (Any 2 x 2)(4)
3.2.4 Evaluate the reliability of the evidence from Source 3B – L3]
This source is reliable because:
- The source shows both the positive and negative effects that globalisation had on the cultures of people around the world
- It is not biased
- People wearing name brands from overseas corporations has become a daily feature
- Many people around the world have acquired some knowledge of the English language
- Any other relevant response (Any 2 x 2)(4)
3.3
3.3.1 [Extraction of evidence from Source 3C – L1]
- Sweatshops
- Child labour (2 x 1) (2)
3.3.2 [Extraction of evidence from Source 3C – L1]
- Boston
- Washington D.C.
- Bangalore
- San Pedro Sula (Any 2 x 1) (2)
3.3.3 [Interpretation of evidence from Source 3C – L2]
- People worked under harsh conditions
- People were paid low wages
- It did not respect workers’ rights
- The commitment to change the company’s practices were not implemented
- Any other relevant response (Any 2 x 2) (4)
3.4
3.4.1 [Interpretation of evidence Source 3D – L2]
- It shows opposition against the corporations
- It accuses the big corporations of enslaving the people
- Any other relevant response (2 x 2) (4)
3.4.2 [Interpretation of evidence from Source 3D – L2]
JUSTIFIED
- TNC’s only motive was profit-making
- People had to work in harsh conditions for low wages
- TNC’s used contractors and sub-contractors thus saving on operation costs and allowing them to leave whenever they desire
- Any other relevant response
OR
NOT JUSTIFIED
- TNC’s provide jobs
- They stimulate economic growth of countries
- It promotes access to technology and skills
- Any other relevant response (Any 2 x 2) (4)
3.5 [Comparison of evidence from Sources 3C and 3D – L3]
- Source 3C shows that a demonstration was held against the Nike sweatshop and Source 3D shows opposition against sweatshops
- Source 3C indicates that people worked in harsh conditions and Source 3D indicates that corporates were enslaving people in sweatshops
- Both sources indicate that MNC’s being accused of exploiting people
- Any other relevant response (Any 2 x 2) (4)
3.6 [Interpretation, comprehension and synthesis of evidence from sources – L3]
Candidates could include some of the following:
- Cultures have been changed due to globalisation (Source 3B)
- People’s culture changed through television, radio, satellite and internet (Source 3B)
- Globalisation made people to learn about other people’s cultures (own knowledge)
- Name brand goods produced by MNC’s has become a popular phenomenon worldwide (Own knowledge)
- It has led to the destruction of local cultures and identities (own knowledge)
- It has impoverished many nations as many people do not buy locally produced products (Own knowledge)
- It caused poverty in many countries as the profits made from production is taken out of the countries (own knowledge)
- People work in harsh conditions in sweatshops (Source 3C)
- TNC’s only care about making profit (own knowledge)
- Led to opposition against MNC’s (Source 3D)
- Any other relevant response
Use the following rubric to assess this paragraph.
LEVEL 1 |
| Marks: 0–2 |
LEVEL 2 |
| Marks: 3–5 |
LEVEL 3 |
| Marks: 6–8 |
(8)
[50]
SECTION B: ESSAY QUESTIONS
QUESTION 4: CIVIL RESISTANCE, 1970s TO 1980s: SOUTH AFRICA: THE CRISIS OF APARTHEID IN THE 1980s
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates need to indicate to what extent demonstrations, boycotts, sanctions and disinvestments by the international anti-apartheid organisations contributed to the eventual demise of the apartheid regime in the 1980’s.
MAIN ASPECTS
Candidates should include the following aspects in their response:
- Introduction: Candidates need to take a stance and demonstrate how different actions taken by the international anti-apartheid organisations eventually led to the demise of apartheid.
ELABORATION
- Formation and role of the Anti-Apartheid Movement (AAM) in the United Kingdom/Irish Anti-Apartheid
- The role of the International Defence Aid Fund (IDAF) made funds available for anti-apartheid activities
- P. W. Botha’s attempt at reforming apartheid/cosmetic reforms
- P.W. Botha’s Rubicon speech in 1985 forced the international community into action which embarked on various forms of boycotts, sanctions and disinvestments against the apartheid regime
- Sport boycotts: SANROC, HART and SACOS
- Cultural boycotts: In 1985 US artists protested against apartheid and refused to perform in South Africa and raised money for liberation movements (In 1986 the Freedom Festival in London); Musicians displayed their solidarity with the people in SA
- Academic boycotts: International scholars refused to travel to South Africa / International publishers refused to publish South African manuscripts and grant access to information/International conferences barred South Africa scholars/ Institutions abroad denied South Africa academic access and refused to recognise South African degrees
- Consumer boycotts: OPEC placed an embargo on oil sales to South Africa (South Africa experienced a recession in the 1980s)/Irish workers refused to handle fruits from SA/Imports of raw materials from South Africa – coal, iron, steel – were banned
- Disinvestment: In 1980s foreign investments dropped by 30%; by 1980 Britain already disinvested from Simon’s Town naval dockyard; General Motors and Barclays Bank pulled out of SA/ In the 1980s South Africa’s economy struggled as investors left the country/The effects of AAM protests had a negative effect on the South African government
- Between 1985 and 1990 over 200 US companies pulled out of South Africa/ The University of California withdrew investments of three million dollars from South Africa
- Sanctions: In 1985 the US Bank Chase Manhattan cut ties with South Africa/the Johannesburg Stock Exchange closed for 4 days/The value of the rand dropped by 35% from 54 cents to 34 cents against the dollar/In 1986 the US Congress passed a law that banned all new investments and loans in South Africa
- Big corporations such as General Electric, Pepsi Cola, General Motors, Mobil and IBM stopped their activities in South Africa/The USA threatened to stop weapon sales to countries which provided weapons to South Africa/In 1986 the Anti-Apartheid Law of the USA caused Europe and Japan to introduce sanctions against South Africa/International banks lost confidence in South Africa’s economy
- In 1982 the United Nations condemned apartheid and called for total sanctions against South Africa
- In 1985 the European Economic Community banned new investments in South Africa
- In 1988 one fifth of British companies withdrew their businesses from South Africa because of pressure from shareholders/Barclays Bank sold their shares due to pressure of the British public/The South African economy kept stagnating and produced growth of only 1,1%
- Release Mandela Campaign: Wembley Stadium/United Nations/UN Security Council and UN General Assembly called for the release of Nelson Mandela
- The role of international trade unions: The AAM in Europe and Australia/Liverpool dockworkers/Finland’s Transport Workers Union imposed a ban on trade with South Africa
- This resulted in South Africa experiencing great economic difficulties and they were forced to begin negotiations with liberation organisations in South Africa
- The role of the frontline states
- Any other relevant response
Conclusion: Candidates should tie up their argument with a relevant conclusion.[50]
QUESTION 5: THE COMING OF DEMOCRACY IN SOUTH AFRICA AND COMING TO TERMS WITH THE PAST: NEGOTIATED SETTLEMENT AND THE GNU
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates need to critically discuss how South Africa’s road to democracy was beset with various challenges, dilemmas and obstacles, but it was the spirit of intense negotiations, resolute leadership and commitment that eventually led to the birth of a democratic dispensation in 1994.
MAIN ASPECTS
Candidates should include the following aspects in their response:
- Introduction: Candidates need to take a stance and indicate how the spirit of intense negotiations, resolute leadership, and commitment paved the way for the birth of a democratic South Africa in 1994.
ELABORATION
- De Klerk comes to power in 1989 – brief background
- De Klerk’s speech in parliament on 2 February 1990 (Political leadership)
- The unbanning of political and civic organisations, such as the ANC and SACP
- The removal of restrictions on COSATU, AZAPO, etc. (Political leadership and commitment)
- Groote Schuur Minute, 2 May 1990 (ANC and NP met, ANC delegation led by Nelson Mandela, NP delegation led by FW de Klerk) (Political leadership and commitment)
- Apartheid legislation revoked, such as the Reservation of Separate (Amenities Act (Political leadership and commitment)
- Pretoria Minute, 6 August 1990 (Suspension the armed struggle by the ANC)
- CODESA 1 (19 political parties, excluding AZAPO, CP and PAC/300 delegates met) (Political leadership and commitment)
- Violence erupts in some parts of the country, such as the Witwatersrand and Natal Whites-only referendum and its impact (March 1992) (Political leadership)
- CODESA 2 (2 May 1992 collapsed); parties failed to agree on a new constitution making body and interim government (Political leadership and commitment)
- NP wanted minority veto while the ANC wanted an interim government for no longer than 18 months and simple majority rule
- Boipatong massacre and its consequences (17 June 1992)
- Bhisho massacre derailed the process of negotiations (7 September 1992)
- Record of Understanding signed on 26 September 1992 between Roelf Meyer (NP) and Cyril Ramaphosa (ANC) (Political leadership and commitment)
- Assassination of Chris Hani (10 April 1993) and its impact on South Africa (Political leadership)
- Multiparty Negotiating Forum (Political leadership and commitment)
- Right-wing (AWB) attack on World Trade Centre and its consequences
- Increasing violence – rolling mass action (i.e. Boipatong, Bisho, etc.)
- Sunset Clause introduced by Joe Slovo broke the negotiations deadlock (Political leadership and commitment)
- Election date announced, 27 April 1994 (Political leadership)
- ANC won elections and Mandela became the first black South African President
- Any other relevant response
Conclusion: Candidates should tie up their argument with a relevant conclusion. [50]
QUESTION 6:
THE END OF THE COLD WAR AND A NEW WORLD ORDER: 1989 TO THE PRESENT
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates need to indicate whether they agree or disagree with the statement and indicate if it was the collapse of the Soviet Union in 1989 that significantly contributed to the political transformation that occurred in South Africa.
MAIN ASPECTS
Candidates should include the following aspects in their response:
- Introduction: Candidates need to take a stance and indicate if it was the collapse of the Soviet Union that contributed to the political transformation in South Africa.
ELABORATION
- Gorbachev’s reform policies of Glasnost and Perestroika
- By the end of 1989 the Soviet Union disintegrated and its impact
- The communist regimes in Eastern Europa collapsed
- Political changes in the rest of the world put pressure on the apartheid regime to embark on changes
- The collapse of communism affected both the National Party and the ANC
- The National Party was now prepared to negotiate with the ANC
- The National Party’s fear of a communist-controlled ANC now seemed unfounded
- After the demise of communism in the Soviet Union; the ANC did not receive further support from the Soviet Union
- The ANC could no longer rely on the Soviet Union for economic and military support
- The fall of the USSR deprived the ANC of its main source of support (financial, military, morally and the consequences thereof)
- The National Party’s claim that it acted as protector to a communist onslaught in Southern Africa became unrealistic
- Countries in the western world supported the move that South Africa should resolve its problems peacefully and democratically
- There was no doubt that continued repression of black South Africans by the apartheid regime was not sustainable and would result in political instability
- The government started to believe that reform was needed to include the development of a strong middle class which would act as a ‘bulwark against the revolution’
- Influential members of the National Party realised that apartheid was not the answer to the needs of white capitalist development
- The Battle of Cuito Cuanavale and the consequences thereof
- The security forces and state of emergency did not stop township protests
- By the late 1980s South Africa was in a state of economic depression
- The role of business leaders in South Africa’s political transformation
- PW Botha suffered a stroke and was succeeded by FW de Klerk
- FW de Klerk realised South Africa’s political predicament and began to accept that the black South African struggle against apartheid was not a conspiracy directed from Moscow
- This enabled De Klerk to engage in discussions with the liberation organisations
- On 2 February 1990 De Klerk announced ‘a new and just constitutional dispensation’
- De Klerk unbanned all anti-apartheid organisations including the ANC, PAC and South African Communist Party
- This signalled the end of apartheid and the beginning of the process of negotiations
- Any other relevant response
Conclusion: Candidates should tie up their argument with a relevant conclusion. [50]
TOTAL: 150
History Paper 2 Grade 12 Addendum - NSC Past Papers And Memos September 2020 Preparatory Examinations
ADDENDUM
QUESTION 1:
HOW DID THE PHILOSOPHY OF BLACK CONSCIOUSNESS (BC) INFLUENCE THE SOUTH AFRICAN YOUTH IN THE 1970s?
SOURCE 1A
This extract focuses on the meaning of the philosophy of Black Consciousness by Steve Biko in 1968.
Biko had a clear insight into the psychological aspect of the oppression of his time which resulted in momentary (brief) political impotence (weakness). As politics was racialised by apartheid, the movement was called Black Consciousness. His message was simple and clear: Do not be a part of your oppression. It was a crucial intervention, a fresh, youthful and distinctive voice that mobilised people when all the major political opposition was banned and their leaders were in exile or in jail. It provided a new, vital, unifying element to the ANC, as Wally Serote said, ‘oxygen and new life, which the movement desperately needed’. Black Consciousness worked with consensus decision-making. It instilled independent thinking, self-reliance, fearlessness and dignity. Biko and his contemporaries (colleagues) broke the stunned (shocked) silence of their time. The refusal of a new generation of young blacks to be subservient (obedient) or humiliated, even in the face of death, changed the nature of the struggle. Biko himself lived and died by this truth. A key catalyst (promoter) of transformation, Biko’s generation inspired a culture of fearlessness. |
[From Steve Biko by L. Wilson]
SOURCE 1B
The source below describes the influence of the Black Consciousness Movement on Veli Mbele who resided in Soweto in 1976.
I grew up in an environment in which many of my peers did not value their own lives and I consider myself fortunate to have encountered Black Consciousness at an early stage. Black Consciousness helped to transform my self-concept and self-esteem in a remarkable way. When I joined the Black Consciousness Movement, I was only 16. At the time the environment was not entirely friendly towards the BCM. Our belief in Black Consciousness was so strong we were not prepared to go into hiding purely because other forces had threatened to ‘deal’ with us or deny us employment if we didn’t abandon our political beliefs. This kind of reaction fortified (encouraged) us even more and we decided to spread the gospel of Black Consciousness even more vigorously (stronger). Thanks to Black Consciousness, many in my generation were transformed into young disciplined black men who through their community activism, earned the respect and admiration of their peers, families and the community. Ever since I came into contact with Black Consciousness, I have felt complete, content with who I am and most importantly, that I’m worthy of respect and dignity. |
[From We Write What We Like by C. Van Wyk]
SOURCE 1C
This extract focuses on the influence of the Black Consciousness Movement (BCM) on students in the 1970s.
In 1976 the Black Consciousness Movement (BCM) was very strong and black students were at the forefront of the struggle. Police arrested many student leaders and put them on trial. Through these political trials, the government wanted to show that the students were dangerous because they spread the ideas of Black Consciousness. The police said black consciousness made black people hate whites. In May, Steve got the chance to show that this was not true. He was called as a defence witness in the trial of nine young South African Student Organisation (SASO) students. A witness in a court of law can say things that are heard by everyone and reported all over the country. It was the first time Steve had spoken in public for three years. The whole world heard him talk about Black Consciousness. He showed that the movement was not trying to make black people hate whites. Black Consciousness wanted black people to be proud of their colour, not ashamed. The world listened carefully to what Steve said, but the South African government refused to listen. Anger in the township grew. On 16 June 1976 thousands of Sowetan students protested in the streets against the apartheid laws. The security forces opened fire and students were killed. |
[From Steve Biko by L. Price]
SOURCE 1D
This is a cartoon by Zapiro on commemorating Steve Biko and was published in the Daily Maverick on 19 September 2017.
[From Zapiro, Daily Maverick]
(Martyred – meaning tortured and killed)
QUESTION 2:
HOW SUCCESSFUL WAS THE TRUTH AND RECONCILIATION COMMISSION (TRC) IN DEALING WITH THE MURDER OF AMY BIEHL?
SOURCE 2A
This extract explains the reasons for the establishment of the TRC by the first democratically elected parliament in 1995.
In the year after the elections, Parliament’s Justice Portfolio Committee drafted legislation to establish a Truth and Reconciliation Commission (TRC). The seventeen- member Commission was given the task of establishing as complete a picture as possible of the causes, nature and extent of the gross violation of human rights violations committed in the period between 1 March 1960 and 1994 by conducting investigations and holding hearings. This period is seen as the most severe ‘crime against humanity’ by the apartheid regime. It also had to facilitate the granting of amnesty to persons who made full disclosure of all the relevant facts related to acts associated with a political objective. In addition, the Commission was required to restore the human and civil dignity of victims, recommend reparation measures and to compile a report of its findings and activities. They also had to recommend measures to prevent future violations of human rights. The Truth and Reconciliation Commission (TRC), as it was duly (accordingly) established, consisted of three committees. The first of these was the Human Rights Violation Committee, which had to look into the accounts of victims through hearings and investigations. The second was the Amnesty Committee, which had to evaluate amnesty applications. It had to apply the Norgard principles to determine whether an application qualified for amnesty. The third committee, the Reparation and Rehabilitation Committee, had to formulate a reparation policy to restore and rehabilitate the lives of victims and survivors of human rights violations. |
[From Country of my Skull by A. Krog]
SOURCE 2B
This source focuses on how and why Amy Biehl was murdered in Cape Town on the 25st August 1993.
Shortly before the end of the apartheid era, Amy Biehl was murdered. She was a victim of racial violence. Amy Biehl was white. She dedicated herself to ending apartheid in South Africa and was based at the University of the Western Cape and working in underprivileged communities. She also helped with voter registration in advance of the ‘Freedom Day’ elections. Amy knew Gugulethu and its people well, or thought she did. She was to be found in the township almost every day or night, could speak isiXhosa and do the phantsula. “That’s how much she fitted in here”, said Melanie Jacobs, the black woman who shared a house with Amy in Cape Town. “She loved Africa. She wasn’t just another white person”. On the evening of 25 August, 1993, Amy drove through Gugulethu township and fell prey (victim) to an angry group of black youths. They pelted (bombarded) Biehl’s car with rocks, forcing her to stop, then dragged her from her car and murdered her, yelling, ‘Kill the Settler!’. Her parents were informed that their daughter had been beaten and stabbed to death. Police arrested two teenage suspects, student members of a militant nationalist group, the Pan Africanist Congress, whose slogan is, ‘One settler, one bullet’. In Cape Town, the killing of the popular scholar has stirred a black backlash (reaction) against the militant group that promoted hatred for whites. The African National Congress offered its township network to help identify the killers. Friends and colleagues, after memorialising Miss Biehl with freedom songs, paraded through Gugulethu with placards declaring, ‘Comrades come in all colours’. |
[From https://www.nytimes.com1993/08/27/world/how-american- sister-died-in-atownship.html. Accessed on 1 September 2019.]
SOURCE 2C
This source focuses on the amnesty hearing of the murderers of Amy Biehl on the 8 July 1997 in Cape Town.
The four youths, Mzikhona Nofemela, Ntobeka Peni, Vusumzi Ntamo and Mongezi Manqina that were convicted of murdering Amy and given a prison sentence of eighteen years, applied for amnesty. The killers of Amy apologised to the parents for what a Truth Commission lawyer described as mindless savagery by a ‘pack of murderers’. The four Pan Africanist Congress (PAC) supporters were challenged on their claims before the Amnesty Committee that the mob killing was politically motivated. Biehl’s parents, Peter and Linda, shook hands with relatives of the four men at the start of the proceedings. In written affidavits submitted to the TRC’s Amnesty Committee, the four said they regretted the murder and asked Biehl’s parents for forgiveness. “I feel sorry and very down-hearted, especially today, realising the contribution Amy Biehl played in the struggle,” Peni said. However, he and his co- applicants insisted that the killing was politically motivated and inspired by the PAC’s slogan, ‘One settler, One bullet’. Peni testified Paso’s executive had ordered its members to make Gugulethu ungovernable and to assist the PAC’s armed wing, the Azanian People’s Liberation Army, in winning back black people’s land. “I regarded this as an instruction to also harm, injure and kill white people.” In 1998, Biehl’s killers were pardoned by the TRC (a decision the family endorsed) and released from prison after serving four years. The Biehls said they believe their daughter would have supported the Commission’s decision to grant amnesty. |
[From www.justice.gov.za/trc/media/1997/9707/s970708f.htm. Accessed on 1 September 2019.]
SOURCE 2D
This photograph shows the killers of Amy Biehl at the amnesty hearing on 8 July 1997 in Cape Town.
[From images amy biehl newpaper. jfif-photos. Accessed on 1 September 2019.]
QUESTION 3:
WHAT IMPACT DID MULTI-NATIONAL CORPORATIONS (MNC’s) HAVE ON GLOBAL CULTURES IN THE 1990s?
SOURCE 3A
The source below explains the meaning of globalisation.
| Globalisation is a process of interaction and integration among the people, companies and government of different nations, a process driven by international trade and investment and aided by information technology. This process has effects on the environment, on culture, political systems, economic development and prosperity and on human physical well-being in societies around the world. Globalisation is not new, though. For thousands of years, people and later corporations have been buying from and selling to each other in lands at great distances. Likewise, for centuries, people and corporations have invested in enterprises in other countries. Policy and technological developments of the past decades have spurred (encouraged) increases in cross-border trade, investment and migration so large that many observers believe the world has entered a qualitatively new phase in its economic development. Since 1950, for example, the volume of world trade has increased by 20 times; from 1997 to 1999 flows of foreign investment nearly doubled, from $468 billion to $827 billion. Distinguishing this current wave (trend) from earlier ones, author Thomas Friedman has said that today globalisation is, ‘faster, cheaper and deeper’. |
[From https://www.globalisation101.org>what-is-globalisation. Accessed on 17 September 2019.]
SOURCE 3B
This source describes the impact of globalisation on the cultures of developing countries.
| Globalisation has many benefits but is also detriment (disadvantage) to the culture in developing countries. Many developing countries’ cultures have been changed through globalisation and imitation others cultures such as America and European countries. Before globalisation it would not have been possible to know about other countries and their cultures. Due to important tools of globalisation like television, radio, satellite and internet, it is possible today to know what is happening in any other country. Moreover, people worldwide can know each other better through globalisation. Today we can clearly see the heavy effect that globalisation has on the young people in the different poor nations. It is very common to see teenagers wearing Nike T-shirts and sneakers, Adidas footwear, playing Hip-Hop music, using Apple iPad, eating at McDonalds, KFC and Domino’s Pizza. It looks like you can only distinguish them by their language. On the other hand, many developing countries are concerned about the rise of globalisation because it might lead to destruction of their own culture, traditions, identity, customs and their language. In many Arab countries, for example, some people wear and behave like developed nations, and only a few people wear their traditional clothes as they used to. Furthermore, globalisation leads to the disappearance of many words and expressions from local languages because many people use English. |
[From http://www.tigweb.org/youth-media/panorama/article.html?Contentl. Accessed on 10 September 2019.]
SOURCE 3C
The extract below describes how civil society protested against the multi-national company, ‘Nike’, in 1998.
| Nike, a leading sportswear manufacturer, is one of the business world’s shining examples of how to clean up an image. In the 1990s, the company was plagued (troubled) by reports that it used sweatshops and child labour. Pressure grew until 1998, when Nike co-founder Phil Knight publicly committed to changing the company’s practices, and Nike spent the next decade doing just that. Now, Nike’s sweatshop problem is threatening a comeback. On July 29, students and activists around the world participated in a day of protest against Nike, organised by United Students Against Sweatshops (USAS). The demonstrators, in cities such as Boston. Washington D.C., Bangalore and San Pedro Sula, represented an escalation of allegations against Nike that have been slowly bubbling (boiling) up. Among them are claims that workers at a Nike factory in Hansae, Vietnam, that suffered wage theft and verbal abuse and laboured for hours in temperatures well over the legal limit of 90 degrees, to the point that they would collapse at their sewing machines. Nike is also accused of cutting jobs at the Hansae factory and pulling production from a factory in Honduras with a strong union presence, resulting in hundreds of workers losing vital jobs. The company has also allegedly denied the independent monitoring group, Workers Rights Consortium (WRC) access to inspect its contract factories. |
[From https://qz.com/1042298/nike-is-facing-a-new-wave--of-anti-sweatshops-protest. Accessed on 10 September 2019.]
SOURCE 3D
This poster attacks giant corporations in 1998 in Washington D.C.
[From New Generation History by S. Govender et al]
ACKNOWLEDGEMENTS
Visual sources and other historical evidence were taken from the following:
Govender, S.et.al. 2007. New Generation History (New Generation Publishers)
http://www.tigweb.org/youth-media/panorama/article.html?Content
https://qz.com/1042298/nike-is-facing-a-new-wave--of-anti-sweatshops-protest
https://www.globalisation101.org>what-is-globalisation
https://www.nytimes.com1993/08/27/world/how-american- sister-died-in- atownship.html
images amy biehl newpaper. jfif-photos
Krog. A. 1999. Country of my Skull (Vintage Publishers)
Price, L. 2013. Steve Biko (Sached Books (Pty) Ltd)
Van Wyk, C. 2007. We Write What We Like (Wits University Press)
Wilson, L. 2011. Steve Biko (Jacana Media (Pty) Ltd)
www.justice.gov.za/trc/media/1997/9707/s970708f.htm
Zapiro, Daily Maverick
History Paper 2 Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
INSTRUCTIONS AND INFORMATION
- This question paper consists of SECTION A and SECTION B based on the prescribed content framework in the CAPS document.
SECTION A: SOURCE-BASED QUESTIONS
QUESTION 1: CIVIL RESISTANCE, 1970s TO 1980s: SOUTH AFRICA
QUESTION 2: THE COMING OF DEMOCRACY TO SOUTH AFRICA AND COMING TO TERMS WITH THE PAST
QUESTION 3: THE END OF THE COLD WAR AND A NEW WORLD ORDER, 1989 TO THE PRESENT
SECTION B: ESSAY QUESTIONS
QUESTION 4: CIVIL RESISTANCE, 1970s TO 1980s: SOUTH AFRICA: THE CRISIS OF APARTHEID IN THE 1980s
QUESTION 5: THE COMING OF DEMOCRACY TO SOUTH AFRICA AND COMING TO TERMS WITH THE PAST: NEGOTIATED SETTLEMENT AND THE GNU
QUESTION 6: THE END OF THE COLD WAR AND A NEW WORLD ORDER: THE EVENTS OF 1989 - SECTION A consists of THREE source-based questions. Source material that is required to answer these questions may be found in the ADDENDUM.
- SECTION B consists of THREE essay questions.
- Answer THREE questions as follows:
4.1 At least ONE must be source-based question and at least ONE must be an essay question.
4.2 The THIRD question can either be a source-based question or an essay question. - You are advised to spend at least ONE hour per question.
- When answering questions, candidates should apply their knowledge, skill and insight.
- You will be disadvantaged by merely rewriting the sources as answers.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SOURCE-BASED QUESTIONS
Answer at least ONE question, but not more than TWO questions, in this section. Source material to be used to answer these questions is contained in the ADDENDUM.
QUESTION 1: HOW DID THE PHILOSOPHY OF BLACK CONSCIOUSNESS INFLUENCE THE SOUTH AFRICAN YOUTH IN THE 1970s?
Study Sources 1A, 1B, 1C and 1D and answer the questions that follow.
1.1 Refer to Source 1A.
1.1.1 Define the term Black Consciousness in your own words. (1 x 2) (2)
1.1.2 Comment on what Biko meant in his message: ‘Do not be part of your oppression’. (2 x 2) (4)
1.1.3 Why, according to the source, was Black Consciousness a crucial intervention? (1 x 2) (2)
1.1.4 How useful will the information in the source be to a historian studying the importance of the formation of the BCM? (2 x 2) (4)
1.1.5 What, according to the source, did the Black Consciousness Movement (BCM) instil in black South Africans? (4 x 1) (4)
1.2 Read Source 1B.
1.2.1 Name TWO ideas of the BCM that helped transform Veli Mbele’s thinking. (2 x 1) (2)
1.2.2 Comment on what Veli implied with his statement, ‘At the time the environment was not entirely friendly towards the BCM’. (1 x 2) (2)
1.2.3 What, according to the source, could happen to Veli and his accomplices if they did not abandon their political beliefs? (2 x 1) (2)
1.3 Study Source 1C.
1.3.1 Why, according to the source, did the government perceive the students to be dangerous? (1 x 2) (2)
1.3.2 Why, do you think, black students were at the forefront of the struggle in 1976? (2 x 2) (4)
1.3.3 Explain why Biko, for the first time in three years, could speak in public. (1 x 2) (2)
1.3.4 Why, do you think the South African government refused to listen? (1 x 2) (2)
1.4 Consult Source 1D.
1.4.1 What does the caption, ‘I write what I like’ imply about Steve Biko? (2 x 2) (4)
1.4.2 Explain what is meant by ‘the bolded fist on Biko’s chest’. (1 x 2) (2)
1.5 Compare Sources 1A and 1D. Explain how the information in Source 1A is similar to the evidence in Source 1D regarding the influence of the philosophy of Black Consciousness on black South Africans. (2 x 2) (4)
1.6 Using the information in the relevant sources and your own knowledge, write a paragraph of about EIGHT lines (about 80 words) explaining how the philosophy of Black Consciousness influenced the South African youth in the 1970s. (8)
[50]
QUESTION 2: HOW SUCCESSFUL WAS THE TRUTH AND RECONCILIATION COMMISSION (TRC) IN DEALING WITH THE MURDER OF AMY BIEHL?
Study Sources 2A, 2B, 2C and 2D to answer the following questions.
2.1 Refer to Source 2A.
2.1.1 What, according to the source, were the aims of the TRC? (2 x 1) (2)
2.1.2 Using the information in the source and your own knowledge, explain why apartheid was perceived as a crime against humanity. (1 x 2) (2)
2.1.3 Define the term amnesty in the context of the TRC. (1 x 2) (2)
2.1.4 Comment on why you would regard the information in the source as useful when researching the role of the TRC. (2 x 2) (4)
2.1.5 Identify the THREE committees that did the work of the TRC. (3 x 1) (3)
2.2 Consult Source 2B.
2.2.1 Why, according to the source, was Amy murdered? (2 x 1) (2)
2.2.2 What kind of information did Amy’s parents receive regarding the death of their daughter? (2 x 1) (2)
2.2.3 Why, do you think, the ANC assisted in finding Amy’s killers? (2 x 2) (4)
2.2.4 What do you think the PAC meant when using the slogan, ‘One settler, one bullet’? (2 x 2) (4)
2.3 Read Source 2C.
2.3.1 Name the THREE youths convicted of killing Amy Biehl. (3 x 1) (3)
2.3.2 Comment on the reasons as to why the killers apologised to Amy’s parents. (2 x 2) (4)
2.3.3 Quote evidence from the source indicating that Peni showed remorse for his actions. (1 x 2) (2)
2.4 Use Source 2D.
2.4.1 What message is conveyed by this photograph regarding the aims of the TRC? (1 x 2) (2)
2.4.2 Why, do you think, did the men appear before the Amnesty Committee? (1 x 2) (2)
2.5 Compare Sources 2C and 2D. Explain how the information in Source 2C supports the evidence in Source 2D regarding the murder of Amy Biehl. (2 x 2) (4)
2.6 Using the information in the relevant sources and your own knowledge, write a paragraph of about EIGHT lines (about 80 words) explaining how successful the Truth and Reconciliation Commission (TRC) was in dealing with the death of Amy Biehl. (8)
[50]
QUESTION 3: WHAT IMPACT DID MULTI-NATIONAL CORPORATIONS (MNC’S) HAVE ON GLOBAL CULTURES IN THE 1990s?
Study Sources 3A, 3B, 3C and 3D to answer the following questions.
3.1 Read Source 3A.
3.1.1 Define the term globalisation in your own words. (1 x 2) (2)
3.1.2 How, according to the source, is the process of globalisation driven? (2 x 1) (2)
3.1.3 Quote a sentence from the source that indicates globalisation was not new. (1 x 2) (2)
3.1.4 Explain what Thomas Friedman meant when he said that globalisation is ‘faster, cheaper and deeper’. (2 x 2) (4)
3.2 Refer to Source 3B.
3.2.1 Which countries’ cultures have been imitated by developing countries? (2 x 1) (2)
3.2.2 Name TWO important tools of globalisation which make it possible to know what is happening in any other country. (2 x 1) (2)
3.2.3 Comment on how globalisation has positively affected people’s cultures around the world. (2 x 2) (4)
3.2.4 Explain the reliability of the source to a historian studying the impact of globalisation on the cultures of developing countries. (2 x 2) (4)
3.3 Consult Source 3C.
3.3.1 How, according to the source, were Nike products manufactured? (2 x 1) (2)
3.3.2 Name TWO cities where demonstrations were held. (2 x 1) (2)
3.3.3 Use the information in the source and your own knowledge to explain why demonstrations were held against the Nike company. (2 x 2) (4)
3.4 Study Source 3D.
3.4.1 What message is conveyed by this poster regarding corporations? (2 x 2) (4)
3.4.2 Comment on whether the criticism against multi-national corporations was justified. (2 x 2) (4)
3.5 Refer to Sources 3C and 3D. Explain how the information in Source 3C supports the evidence in Source 3D regarding the reasons for demonstrations against multi-national corporations. (2 x 2) (4)
3.6 Using the information in the relevant sources and your own knowledge, write a paragraph of about EIGHT lines (about 80 words) explaining the impact
that multi-national corporations had on global culture. (8)
[50]
SECTION B: ESSAY QUESTIONS
Answer at least ONE question, but not more than TWO questions, in this section.
Your essay should be about THREE pages long.
QUESTION 4: CIVIL RESISTANCE, 1970s TO 1980s: SOUTH AFRICA: THE CRISIS OF APARTHEID IN THE 1980s
Explain to what extent demonstrations, boycotts, sanctions and disinvestments by the international anti-apartheid organisations contributed to the eventual demise of the apartheid regime in the 1980s.
Substantiate your line of argument by using relevant evidence. [50]
QUESTION 5: THE COMING OF DEMOCRACY TO SOUTH AFRICA AND COMING TO TERMS WITH THE PAST
‘South Africa’s road to democracy was beset (affected) with various challenges, dilemmas (problems) and obstacles. It was the spirit of intense negotiations, resolute (firm) leadership and commitment to democracy that eventually led to the birth of a democratic dispensation in 1994.’
Critically discuss the statement. Support your line of argument with relevant evidence. [50]
QUESTION 6: THE END OF THE COLD WAR AND A NEW WORLD ORDER: THE EVENTS OF 1989
‘It was the collapse of the Soviet Union in 1989 that significantly contributed to the political transformation that occurred in South Africa.’
Do you agree with the statement? Substantiate your line of argument by using relevant evidence. [50]
TOTAL: 150
History Paper 1 Grade 12 Memorandum - NSC Past Papers And Memos September 2020 Preparatory Examinations
MEMORANDUM
SECTION A: SOURCE BASED QUESTIONS
QUESTION 1: HOW DID THE DEPLOYMENT OF MISSILES TO CUBA CONTRIBUTE TO COLD WAR TENSIONS BETWEEN THE SOVIET UNION AND THE UNITED STATES IN THE 1960s?
1.1
1.1.1 [Extraction of evidence from Source 1A – L1]
- United States of America (1 x 1)(1)
1.1.2 [Extraction of evidence from Source 1A – L1]
- War-minded reactionary elements of the United States have long since been conducting an unbridled (unchecked) propaganda campaign against the Cuban Republic calling for an attack on Cuba.
- An attack on Soviet ships carrying the necessary commodities and food to the Cuban people, in one word, calling for war.
- The President of the United States asked Congress to permit the call-up of 150 000 reservists to the armed forces of the United States. (3 x 1) (3)
1.1.3 [Interpretation of evidence from Source 1A – L2]
- Cuba approached Russia for help after the failed Bay of Pigs invasion.
- Cuba was a communist country and therefore the USSR supported her.
- To resist the impact of American isolation and boycotts.
- To protect Cuba’s existence as a communist country.
- Any other relevant answer. (Any 1 x 2) (2)
1.1.4 [Evaluation of limitations of Source 1A – L3]
- The source is biased towards Russia
- The source portrays the USA as an aggressive, hostile force
- The source denies that the USSR provided Cuba with nuclear missiles.
- The source does not show the USSR's real reasons for deploying missiles to Cuba.
- Any other relevant answer. (Any 2 x 2)(4)
1.2 1.2.1 [Interpretation of evidence from Source 1B – L2]
- Map shows that Cuba has nuclear weapons.
- Map shows that the nuclear missiles were within striking distance of all major US cities.
- Photo shows that Cuba was a threat to the USA.
- Any other relevant answer. (Any 2 x 2)(4)
1.2.2 [Interpretation of evidence from Source 1B – L2]
- They were upset about the installation of the nuclear missiles
- They discussed different options to stop the threat.
- They decided to launch a blockade to force Russia to withdraw the missiles.
- They announced Defcon 2 – military readiness for possible war.
- Any other relevant answer. (Any 1 x 2)(2)
1.3
1.3.1 [Extraction of evidence from Source 1C – L1]
- Soviet military build-up on the island of Cuba (1 x 2) (2)
1.3.2 [Extraction of evidence from Source 1C – L1]
- To provide nuclear strike capability against the Western Hemisphere (1 x 2)(2)
1.3.3 [Definition of a historical concept from Source 1C – L1]
- The blockade of international waters around Cuba to prevent the delivery of nuclear weapons to that country.
- Any other relevant answer. (1 x 2)(2)
1.3.4 [Interpretation of evidence from Source 1C – L2]
- He wanted to make the American people aware of the potential threat they were facing
- He wanted to assure the American public that he was in control of the situation
- He wanted to bring some reassurance to the American public
- Any other relevant answer. (Any 2 x 2)(4)
1.4 [Comparison of evidence from Sources 1B and 1C – L3]
- Source 1C states that the USA had maintained surveillance over Cuba– this is supported by the map (1B) which was the result of the surveillance.
- Source 1C states that the missiles had the potential to destroy large cities such as Washington – this is supported by the map (Source 1B) which shows that large US cities were within strike range of the missiles.
- Both sources show that Cuba was equipped with nuclear missiles
- Any other relevant answer. (Any 2 x 2)(4)
1.5
1.5.1 [Extraction of evidence from Source 1D – L1]
- ‘... I suggest will declare that our ships, bound for Cuba, are not carrying any armaments.’
- ‘You would declare that the United States will not invade Cuba with its forces …’
- ‘… and will not support any sort of forces which might intend to carry out an invasion of Cuba.’ (Any 2 x 1)(2)
1.5.2 [Extraction of evidence from Source 1D – L1]
- As aggressive, piratical actions (1 x 2) (2)
1.5.3 [Interpretation of evidence from Source 1D – L2]
- He implied that the US had escalated the crisis to a point where the US itself will not be able to stop the crisis.
- He implied that the US's refusal to lift the quarantine could lead to a nuclear war
- He implied that if the two powers failed to resolve the crisis peacefully, it would lead to nuclear war
- He implied that the crisis had reached a stalemate which could only be decided by war
- Any other relevant answer. (Any 2 x 2)(4)
1.5.4 [Interpretation of evidence from Source 1D – L2]
- Leaders reached a compromise
- Russia would withdraw the missiles from Cuba on condition that the USA would not invade Cuba
- The USA secretly agreed to withdraw its missiles from Turkey
- Any other relevant answer. (Any 2 x 2)(4)
1.6 [Interpretation, analysis and synthesis of evidence from relevant sources – L3]
Candidates can use the following points to answer the question:
- Cuba requested Russian aid following the failed Bay of Pigs invasion (own knowledge)
- Russia insists that US wants to attack Cuba as well as Russian ships on their way to Cuba (Source 1A)
- Tensions worsened when in the US 150 000 reservists were called up (Source 1A)
- Russia acknowledged providing weapons to Cuba for defensive purposes (Source 1A)
- The USA considers missile deployment to Cuba as a threat (Sources 1A and 1B)
- Tensions worsened when the USA published a map showing all major USA cities were within range of the missiles (Source 1B)
- President Kennedy makes people aware of the danger and promises to oppose it (Source 1C)
- Kennedy initiates a blockade of Cuba and threatens to sink Russian ships (Source 1C).
- Russia instructs its captains to ignore the naval blockade (own knowledge and Source 1D)
- Russia warns that the missile crisis would lead to a disastrous nuclear war (Source 1D)
- Russia declares that it is in favour of a peaceful solution to the crisis (Source 1D).
- Any other relevant response.
Use the following rubric to assess the paragraph:
CRITERIA | MARKS | |
LEVEL 1 |
| 0–2 |
LEVEL 2 |
| 3–5 |
LEVEL 3 |
| 6–8 |
(8)
[50]
QUESTION 2:
WHY DID FOREIGN POWERS BECOME INVOLVED IN THE ANGOLAN WAR OF INDEPENDENCE?
2.1
2.1.1 [Definition of historical concepts from Source 2A – L1]
- The right to govern a country without any interference from foreign powers
- Any other relevant answer. (Any 1 x 2)(2)
2.1.2 [Extraction of evidence from Source 2A – L1]
- MPLA
- FNLA
- UNITA (3 x 1)(3)
2.1.3 [Interpretation of evidence from Source 2A – L2]
- Each movement wanted to govern the country on their own
- They had too many ethnic differences
- They had too many ideological differences
- There was too much foreign interference
- They distrusted each other which hampered the power-sharing agreement.
- Any other relevant answer. (Any 1 x 2)(2)
2.1.4 [Interpretation of evidence from Source 2A – L2]
- MPLA was communist
- MPLA was opposed to SA's apartheid policy
- MPLA allowed the ANC to open bases to continue the armed struggle against SA
- MPLA allowed SWAPO to set up bases to continue the struggle for independence
- Any other relevant response. (Any 2 x 2)(4)
2.1.5 [Interpretation of evidence from Source 2A – L2]
- Almost all the superpowers became involved in the civil war
- Superpowers provided military assistance to protect their own interests in Angola
- Superpowers became involved to expand their ideology in Angola
- Any other relevant answer. (Any 1 x 2)(2)
2.2
2.2.1 [Extraction of evidence from Source 2B – L1]
- The total onslaught of communism. (1 x 2)(2)
2.2.2 [Extraction of evidence from Source 2B – L1]
- To secure and to protect its own interests
- To protect South Africa from the increasing communist threat.
- The USSR and Cuba were enlarging their support to the MPLA
- The concentration of SWAPO insurgents on the southern Angola border furthermore endangered SA’s interests in SWA.
- As such, SA was pressured by some in the international community to get involved in Angola for the first time
- The international community put pressure on South Africa to become involved
- It is in their own and regional interest. (Any 3 x 1)(3)
2.2.3 [Interpretation of evidence from Source 2B – L2]
- Both organisations were indirectly controlled by Russia
- Russia provided both organisations with weapons to maintain its communist agenda in Africa
- Any other relevant answer. (Any 1 x 2)(2)
2.2.4 [Interpretation of evidence from Source 2B – L2]
- The US was opposed to communist invasion of Angola because it would jeopardise their capitalist interests there.
- The US did not want to get directly involved and so they asked SA to protect capitalism in Southern Africa
- The US was under pressure after their failed campaign in Vietnam and did not want to deploy troops to Angola.
- Any other relevant answer. (Any 2 x 2)(4)
2.3 2.3.1 [Extraction of evidence from Source 2C – L1]
- USA trained Angolan combat units
- USA personnel … carrying out reconnaissance and supply missions
- CIA spent over a million dollars on an ambitious mercenary programme
- Many American guerrillas were fighting in Angola against the MPLA
- CIA was also directly financing the arming of British mercenaries. (Any 4 x 1)(4)
2.3.2 [Interpretation of evidence from Source 2C – L2]
- To take the attention away from their own involvement in Angola
- To justify their intervention in Angola
- Any other relevant answer. (Any 1 x 2)(2)
2.3.3 [Determining usefulness of Source 2C – L3]
Useful to a great extent
- Source shows that the US provided military assistance to certain liberation organisations
- Source shows that the US was directly involved in the Angolan Civil War
- Source also shows that the US provided financial assistance to realise its own goals in Angola
- Source shows that the US also used propaganda to shift the attention away from their intervention in Angola.
- Any other relevant answer. (Any 2 x 2) (4)
2.4 2.4.1 [Interpretation of evidence from Source 2D – L2]
- It shows that Neto and Castro had a very good relationship
- It shows that Castro supported the MPLA.
- Source shows that many people were happy with the MPLA government
- It shows that Castro contributed to the MPLA's assumption of power
- Any other relevant answer. (Any 2 x 2) (4)
2.4.2 [Evaluating the limitations of Source 2D – L3]
- It can be considered as propaganda.
- Not all citizens supported the MPLA as the source wants to suggest
- The source does not show the divisions that existed in Angola after independence.
- Any other relevant answer. (Any 2 x 2) (4)
2.5 [Interpretation, analysis and synthesis of evidence from relevant sources – L3]
Candidates may include the following aspects in their responses:
- Foreign powers become involved in Angolan War of independence to further their economic and ideological interests (Source 2A)
- They delivered military assistance to their preferred clients (Source 2A)
- SA supports UNITA and the FNLA because they were anti-communist (Source 2B)
- Both UNITA and the FNLA pledged to counter SWAPO attacks on South Africa. (Source 2B)
- SA was opposed to the communist MPLA. (Source 2B)
- SA saw a need to secure and protect its own interests (Source 2B)
- The USA wanted to contain the spread of communism in Angola and Southern Africa (Source 2C)
- The US had oil contracts in Angola and was opposed to communist expansion which would put it at risk. (Own knowledge)
- Russia and Cuba supported the MPLA because they were communists (Own knowledge and Source 2D)
- Angola’s geographical location was of strategic value to both the USA and Russia (Own knowledge)
- Cuba became involved at the request of the MPLA (Own knowledge and Source 2D)
- Cuba became involved to stop the South African military's advance in Angola (Own knowledge)
- Any other relevant response.
Use the following rubric to assess the paragraph:
CRITERIA | MARKS | |
LEVEL 1 |
| 0–2 |
LEVEL 2 |
| 3–5 |
LEVEL 3 |
| 6–8 |
(8)
[50]
QUESTION 3:
WHAT WAS THE IMPACT OF BLACK POWER MOVEMENT ON AFRICAN AMERICANS IN THE 1960s?
3.1
3.1.1 [Definition of historical concepts from Source 3A – L1]
- Civil Rights are the social and political rights given to all citizens who resides in the same borders irrespective of skin colour.
- Any other relevant response (Any 1 x 2)(2)
3.1.2 [Interpretation of evidence from Source 3A – L2]
- It changed the way Black people looked at themselves
- BP created a force that was prepared to fight Whites for what they believed in
- BP sought to achieve racial independence and not to be absorbed into the white-dominated society
- Brought about a period of racial violence and turmoil in the USA
- Any other relevant response. (Any 2 x 2)(4)
3.1.3 [Extraction of evidence from Source 3A – L1]
- Blacks still received lower wages than whites
- Higher crime rate in their neighbourhoods
- They also faced unspoken, but palpable racial discrimination
- Civil Rights Movement as too mainstream to generate real social change
- They wanted to quicken the process and give black opportunities as whites
- They felt that Civil Rights Movement was based more on white perceptions of civil rights than black perceptions. (Any 3 x 1)(3)
3.1.4 [Interpretation of evidence from Source 3A – L2]
- They became disillusioned with the slow pace of change brought about by the Civil Rights Movement.
- The Civil Rights Movement failed to adequately address the social and economic inequalities of Blacks.
- They felt that the Civil Rights Movement was too moderate and based more on white thinking than black thinking
- The Civil Rights Movement’s policy on non-violence did not appeal to some blacks. (Any 2 x 2)(4)
3.2
3.2.1 [Extraction of evidence from Source 3B – L1]
- Black Panther Party (1 x 2) (2)
3.2.2 [Extraction of evidence from Source 3B – L1]
- The Black Nationalist party was vilified (criticised) in the news media
- Feared by those intimidated by its message of black power
- Its commitment to ending police brutality and subjugation of Black Americans (3 x 1)(3)
3.2.3 [Interpretation of evidence from Source 3B – L2]
- They wanted to improve learning in black schools
- Blacks were excluded from the federal government’s food programmes.
- The Black Panthers perceived hunger as a means of oppression that must be stopped through feeding schemes.
- To increase academic performance.
- To raise the standard of living of Black Americans.
- To lay the foundation of political activism/fuelling revolution
- Any other relevant response. (Any 1 x 2)(2)
3.2.4 [Interpretation of evidence from Source 3B – L2]
- The children were just enjoying the food and were not aware of the political undertones
- Their focus was only on the breakfast and they did not have an interest of knowing why the food was served to them
- They did not have an interest in the Black Panther Party’s politics
- Any other relevant response. (Any 1 x 2)(2)
3.2.5 [Evaluation of evidence from Source 3B – L3]
Successful
- The children weren’t falling asleep in class
- They weren’t crying with stomach cramps
- Children were different. (Any 2 x 2)(4)
3.3 3.3.1 [Interpretation of evidence from Source 3C – L2]
- To show that the Black Panther’s programme was successful
- To show that blacks had the ability to do things for themselves
- To foster a culture of pride in being black
- To show that Blacks could eradicate poverty and hunger without federal support.
- Any other relevant response (Any 2 x 2)(4)
3.3 [Comparison of sources to determine similarities – L3]
- Source 3B states that Black Panther Party started a programme of serving black children a breakfast meal, whilst Source 3C shows how black children are being served with a breakfast.
- Both sources show that Black Panthers can do things for themselves without relying on white assistance.
- Both sources show how happy the children are to receive the food.
- Any other relevant response (Any 2 x 2)(4)
3.4
3.4.1 [Extraction of evidence from Source 3D – L1]
- As a student at Lincoln University in Pennsylvania, she was involved in the Black Student Congress (1 x 2)(2)
3.4.2 [Extraction of evidence from Source 3D – L1]
- An article in the magazine showing Huey without a shirt strapped to a hospital gurney, with a bullet wound in his stomach (1 x 2)(2)
3.4.3 [Interpretation of evidence from Source 3D – L2]
- Women played a critical role in every aspect of the party life of the Black Panther Party
- Women occupied key positions in the party due to its gender equality programme
- Almost half of the membership of the BPP were women
- Black women kept the work of the party going
- Women occupied leadership positions to fill the vacant posts as men were charged or killed by the federal government
- Women were able to open BPP branches – Connecticut.
- Any other relevant response. (Any 2 x 2)(4)
3.5 [Interpretation, analysis and synthesis of evidence from relevant sources – L3]
Candidates may include the following aspects in their responses:
- Blacks became discouraged with the Civil Rights Movement because they had to wait too long for their freedom (Source 3A)
- BPM was a turning point in black-white relations (Source 3A)
- BPM offered blacks economic and political independence (Source 3A)
- Black Power Movement encourages blacks to start doing things for themselves (Own knowledge)
- BPP started the free breakfast programme for children (Source 3B and 3C)
- Breakfast programmes had positive effects on black children (Source 3B and 3C)
- The aim of the breakfast programmes aim was to fuel the revolution (Source 3B)
- BPP also offered health clinics and literacy classes for blacks (Own knowledge)
- BPP clashed with the police to end police brutality (Own knowledge)
- BPP programmes were successful and as a result the federal government disliked the Black Panther Party (Source 3B and 3C)
- BPP proclaimed self-sufficiency – educated their own children (Own Knowledge)
- Many women joined the BPP like Erica Huggins (Source 3D)
- Women played an active and critical role in the BPP – forming branches like Erica Huggins (Source 3D)
- Women occupied key positions left by men who were either imprisoned or killed by the federal government (Source 3D)
- Any other relevant response.
Use the following rubric to assess the paragraph:
CRITERIA | MARKS | |
LEVEL 1 |
| 0–2 |
LEVEL 2 |
| 3–5 |
LEVEL 3 |
| 6–8 |
(8)
[50]
SECTION B: ESSAY QUESTIONS
QUESTION 4: THE COLD WAR: CASE STUDY – CHINA
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates must indicate to what extent the Great Leap Forward and the Cultural Revolution succeeded in transforming China from a backward agrarian state into an industrial state. Candidates must discuss the reasons for the implementation as well as the impact of the policies.
MAIN ASPECTS
Candidates may include the following aspects in their response:
Introduction: Candidates must indicate to what extent the Great Leap Forward and the Cultural Revolution succeeded in transforming China from a backward agrarian state into an industrial state.
ELABORATION
- 1949 Mao signed a Treaty of Friendship with Russia to help him rebuild his country.
- Russia gave them money, machines and experts; with his help he implemented his First Five Year Plan.
- This plan was a success – coal doubled its output and that of oil tripled.
- Agricultural output increased but could not produce enough grain for urban consumption.
- Mao introduced the Great Leap Forward to transform China into an industrial state.
- He believed that collectivisation would feed the industrial workers in the city and produce cash crop for exports.
- Farms were taken over by the state – state targets were set and revised
- None of these targets were achieved
- Industrial output fell – coal dropped to 180 million tonnes
- Heavy industry fell by 65%
- Light industry fell by 30%
- These targets were not met because the farmers produced slowly as they were angry because their farms were taken away.
- The production of iron and steel dropped and the quality thereof was poor.
- In 1960 Mao had an argument with Russia – Russia withdrew their experts leading to the collapse of all major projects in China.
- In that same year there was a huge drought which led to a famine where 30 million people died.
- Mao stepped down as president but remained the chairman of the Communist Party.
- The moderates that took over implemented capitalist reforms to improve the economy of the country.
- Mao was against capitalism and launched the Cultural Revolution.
- He called on the Chinese public to eliminate everyone and everything that was associated with capitalism.
- He urged them to destroy the 4 Olds (Old Ideas, Old habits, Old customs, and Old culture).
- The students answered Mao’s call and formed the Red Guard. They attacked and destroyed churches, schools and universities.
- Teachers, parents and party officials were publicly humiliated and killed.
- Students now also attacked parents who were suspected of being ant- communist.
- The country was now in a state of civil war and Mao was forced to call in the army to restore law and order.
- Millions of students were sent to the countryside for re-education.
- Mao died in 1976 and that led to the end of the Cultural Revolution.
- Another 4 million people died as a result of this policy.
- A whole generation of Chinese did not get any formal evaluation as schools and universities were destroyed.
- The economy went into a crisis as agricultural production dropped.
- Many Chinese lost confidence in the Communist Party.
- Any other relevant response
- Conclusion: Candidates should tie up their arguments with relevant conclusions. [50]
QUESTION 5:
INDEPENDENT AFRICA: COMPARATIVE CASE STUDY – THE CONGO AND TANZANIA
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates need to critically discuss how Nyerere and Sese Seko confronted their economic and political challenges after independence.
MAIN ASPECTS
Candidates should include the following aspects in their response:
Introduction: Candidates should critically discuss the successes and challenges facing Tanzania and the Congo with specific reference to their economic and political development after gaining independent from colonial rule.
ELABORATION
ECONOMY
- The Congo and Tanzania inherited a single-product economy from their colonisers.
- Tanzania followed a socialistic economic model
- Congo followed a capitalistic model
- Both countries struggled to develop their respective economies.
- Nyerere adopted an African Socialism model outlined in the Arusha Declaration which led to the nationalisation of industries and land.
- Its aim was to cut ties with Western countries and create self-sufficiency and self- dependency.
- Society would be stable and free of economic inequalities.
- Mobuto initially nationalised industries using the Zaireanization policy – which involved taking farms and businesses from the foreign owners who were replaced by Congolese.
- When it failed due to lack of skills and poor management he adopted a capitalistic model and returned businesses to foreign owners.
- Nyerere introduced Villagisation or Ujaama.
- A rural community with farming / collective labour.
- Lack of tools, water and management skills led to resistance which the police and military forces could not control.
- This led to destruction and abandonment of fields.
- Tanzania remained the poorest and most underdeveloped country.
- Tanzania reduced corruption of government officials through the ‘Leadership Code’.
- Both countries had to accept foreign aid and allow investments which Nyerere initially viewed as neo-colonialism.
POLITICAL ASPECTS
Congo:
- Attaining independence through democratic elections (the Congo 1960) J. Kasavubu became President and P Lumumba became the prime minister
- After holding multi-party elections at independence, the Congo became a one- party state within the first five years after gaining independence
- Mobuto Sese Seko remained as president for life until his death in 2007
- Mobuto Sese Seko created a kleptocracy where a group of appointed public officials abused their position for financial gain
- Brought back African values
- Strong centralised government
- Political stability (though based on authoritarianism)
- Any other relevant response.
Tanzania
- Attaining independence through democratic elections (Tanzania 1961: J Nyerere– amended the constitution to become President (1962)
- Smooth transition (peaceful change/racial harmony/commitment to promotion of human equality and dignity
- After holding multi-party elections at independence, it became a one-party state
- Nyerere remained as president for life between the 1960s and 1970s
- Nyerere introduced the Leadership Code in the Arusha Declaration which demanded high levels of integrity from public officials
- African Socialism / Ujamaa was appropriate for inhabitants
- Establishment of the United Republic of Tanzania (1964)
- Centralised and unitary state
- Any other relevant response.
- Conclusion: Candidates should tie up their arguments with relevant conclusions. [50]
QUESTION 6:
CIVIL SOCIETY PROTESTS FROM THE 1950s TO THE 1970s – THE BLACK POWER MOVEMENT IN THE USA
[Plan and construct an original argument based on relevant evidence using analytical and interpretative skills.]
SYNOPSIS
Candidates must state whether they agree or disagree with the statement. By taking a stance they need to support it with relevant historical evidence.
MAIN ASPECTS
Candidates should include the following aspects in their response:
Introduction: Candidates should indicate whether they agree with the statement or not.
ELABORATION
- Rosa Parks (background)
- In 1960 a small group of black students started a sit-in at a restaurant in Greensboro that refused to serve black people
- They occupied the ‘Whites only’ seats and placed their orders; but were not served. Within two months the sit-ins spread to 54 cities in 9 states
- The students were physically and verbally abused but they followed King's non- violent strategy of not fighting back
- The campaign was successful and a few weeks later six restaurants in Nashville desegregated and started to serve all people regardless of their skin colour
- This was followed by successful campaigns against segregated transport, restaurants, swimming pools, theatres, libraries, beaches and public parks
- In 1961 CORE organised the Freedom Rides where both black and white Americans drove southward to test the effectiveness of the Court's desegregation decision
- In Alabama, one of the buses was burned and a few activists assaulted. This violence was broadcast on national television and resulted in national attention for the Freedom Rides.
- This forced the Federal Government to step in to protect the activists and to enforce the Supreme Court decision. In this way, the Freedom Rides led to the desegregation of more bus services in the southern States
- Blacks in America could only vote if they could pass a literacy test. Black and white students from the North visited churches and schools in the South and taught Blacks how to read and write
- The Black Power Movement then shifted their focus to obtain voting rights for Blacks in Mississippi by means of a strategy entitled ‘Freedom Summer.’
- They were abused and harassed and at least three activists were killed. In spite of this, the Freedom Summer campaign continued and was a success because many more Blacks could now pass the literacy test
- In this way more Blacks were now able to vote
- Birmingham was a strong KKK fortress and described as America’s most racist city.
- In April 1963 King led a march to protest against segregation and unfair employment in the city.
- He was arrested. He consequently used children to continue the campaign in Birmingham. The police suppressed the march with violence
- The images of children being sprayed with high-pressure water pipes and being attacked by dogs and police, caused international news and condemnation.
- The media had once again shown America what life was like for African Americans in the South
- The march was ended through a compromise. The protest action was stopped and the city's facilities were desegregated and more Blacks were employed in the city’s departmental stores
- On 28 August 1963, King led a march of more than 200 000 Americans in Washington for jobs and freedom
- He wanted to emphasise the political and social challenges that black Americans faced each day. The march tried to address the unemployment of Blacks and to gain full racial equality
- It culminated in Martin Luther King Jr.'s ‘I have a dream’ speech, a spirited call for racial justice and equality
- This led to the Federal Government passing the Civil Rights Act of 1964 that banned segregation in public accommodation and discrimination in education and jobs
- This was followed up by the Voting Rights Act of 1965, which removed all restrictions on voting rights
- Literacy tests and extra taxes would no longer be allowed to prevent African Americans from voting.
- Any other relevant answer.
- Conclusion: Candidates should tie up their argument by mentioning the success of the Civil Rights Movement in effecting changes in the United States of America.[50]
TOTAL: 150
History Paper 1 Grade 12 Addendum - NSC Past Papers And Memos September 2020 Preparatory Examinations
ADDENDUM
QUESTION 1:
HOW DID THE DEPLOYMENT OF MISSILES TO CUBA CONTRIBUTE TO COLD WAR TENSIONS BETWEEN THE SOVIET UNION AND THE UNITED STATES IN THE 1960s?
SOURCE 1A
This source is an extract from a Soviet statement on a potential Cuban attack by the United States (11 September 1962).
The Government of the U.S.S.R. deems it necessary to draw the attention of the governments of all countries and world opinion to the provocations the United States Government is now staging, provocations which might plunge the world into the disaster of a universal world war with the use of thermonuclear weapons. War-minded reactionary elements of the United States have long since been conducting an unbridled (unchecked) propaganda campaign against the Cuban Republic, calling for an attack on Cuba, an attack on Soviet ships carrying the necessary commodities and food to the Cuban people, in one word, calling for war. The President of the United States asked Congress to permit the call-up of 150 000 reservists to the armed forces of the United States … Such a step by the United States Government cannot be assessed otherwise than a screen for aggressive plans and intentions of the United States itself and will inevitably lead to aggravating the international atmosphere. … We do not hide from the world public that we really are supplying Cuba with industrial equipment and goods which are helping to strengthen her economy and raise the well- being of the Cuban people. … It will be recalled that a certain amount of armaments is also being shipped from the Soviet Union to Cuba at the request of the Cuban government in connection with the threats by aggressive imperialist circles. The Cuban statesmen also requested the Soviet Government to send to Cuba Soviet military specialists, technicians who would train the Cubans in handling up-to-date weapons, because up-to-date weapons now call for high skill and much knowledge. It is but natural that Cuba does not yet have such specialists. The armaments and military equipment sent to Cuba are designed exclusively for defensive purposes and the President of the United States and the American military just as the military of any country know what means of defence are. How can these means threaten the United States? |
[From http://www.mtholyoke.edu/acad/intrel/precrisis.htm. Accessed on 21 November 2019.]
SOURCE 1B
The following source is a map that the USA published to indicate the impact of the nuclear missiles in Cuba.
[From https://www.gettyimages.com/photos/cuban-missile-crisis?mediatype=photography&phrase=cuban%20missile%20crisis&sort=mostpopular. Accessed on 15 December 2019.]
SOURCE 1C
This source is an extract from President John F. Kennedy’s speech to the nation on radio and television about the Soviet missiles in Cuba on October 22, 1962.
Good evening, my fellow citizens. This Government, as promised, has maintained the closest surveillance of the Soviet military build-up on the island of Cuba. Within the past week, unmistakable evidence has established the fact that a series of offensive missile sites is now in preparation on that imprisoned island. The purpose of these bases can be none other than to provide a nuclear strike capability against the Western Hemisphere. The characteristics of these new missile sites indicate two distinct types of installations. Several of them include medium range ballistic missiles, capable of carrying a nuclear warhead for a distance of more than 1 000 nautical miles. Each of these missiles, in short, is capable of striking Washington, D.C., the Panama Canal, Cape Canaveral, Mexico City, or any other city in the south-eastern part of the United States, in Central America, or in the Caribbean area. To halt this offensive build-up, a strict quarantine on all offensive military equipment under shipment to Cuba is being initiated. All ships of any kind bound for Cuba from whatever nation or port will, if found to contain cargoes of offensive weapons, be turned back ... We are not at this time, however, denying the necessities of life as the Soviets attempted to do in their Berlin Blockade of 1948. |
[From https://spartacus-educational.com. Accessed on 16 December 2019.]
SOURCE 1D
This source is a translation of a telegram from Khrushchev to Kennedy sent from the Embassy in the Soviet Union to the Department of State, Moscow, October 26, 1962.
Let us therefore show statesmanlike wisdom. I propose we, for our part, will declare that our ships, bound for Cuba, are not carrying any armaments. You would declare that the United States will not invade Cuba with its forces and will not support any sort of forces which might intend to carry out an invasion of Cuba. Then the necessity for the presence of our military specialists in Cuba would disappear. Mr President, I appeal to you to weigh well what the aggressive, piratical actions, which you have declared the USA intends to carry out in international waters, would lead to. You yourself know that any sensible man simply cannot agree with this, cannot recognise your right to such actions. If you did this as the first step towards the unleashing of war, well then, it is evident that nothing else is left to us but to accept this challenge of yours. If, however, you have not lost your self-control and sensibly conceive what this might lead to, then, Mr President, we and you ought not now to pull on the ends of the rope in which you have tied the knot of war, because the more the two of us pull, the tighter that knot will be tied. And a moment may come when that knot will be tied so tight that even he who tied it will not have the strength to untie it, and then it will be necessary to cut that knot. And what that would mean is not for me to explain to you, because you yourself understand perfectly of what terrible forces our countries dispose. Consequently, if there is no intention to tighten that knot and thereby to doom the world to the catastrophe of thermonuclear war, then let us not only relax the forces pulling on the ends of the rope, let us take measures to untie that knot. We are ready for this. |
[From https://microsites.jfklibrary.org/cmc/oct26/doc4.html. Accessed on 16 December 2019.]
QUESTION 2:
WHY DID FOREIGN POWERS BECOME INVOLVED IN THE ANGOLAN WAR OF INDEPENDENCE?
SOURCE 2A
This source explains the power struggles that erupted after Angola became independent in 1974.
| Three main military movements had been fighting for Angolan independence since the 1960s. The Popular Movement for the Liberation of Angola (MPLA) was a Marxist organisation centred in the capital, Luanda, and led by Agostinho Neto. The National Front for the Liberation of Angola (FNLA) led by Holden Roberto, was based in the north of the country and had strong ties to the US ally (friend), Mobutu Sese Seko, in neighbouring Zaire. The National Union for the Total Independence of Angola (UNITA), an offshoot of the FNLA, was by Jonas Savimbi and supported by the country’s largest ethnic group, the Ovimbundu. Following the Portuguese coup (revolution), these three revolutionaries met with representatives of the new Portuguese government in January 1975 and signed the Alvor Agreement that granted Angolan independence and provided for a three-way power sharing government. However, trust quickly broke down among the three groups, and the country descended (fell) into civil war as each vied (competed) for sole (total) power. The crisis in Angola developed into a Cold War battleground as the superpowers and their allies delivered military assistance to their preferred clients. The United States supplied aid and training for both the FNLA and UNITA while troops from Zaire assisted Holden Roberto and his fighters. China also sent military instructors to train the FNLA. During the summer of 1975, the Soviet-supported MPLA was able to consolidate power in Luanda and oust the U.S.-supported FNLA from the capital, but the FNLA continued to attack. |
[From https://history.state.gov/milestones/1969-1976/angola. Accessed on 05 April 2020.]
SOURCE 2B
The source below outlines the reasons for South Africa’s involvement in Angola during the 1970s.
SA’s first intervention of Angola seems to have resulted from the need to secure and protect its own interests. The government was severely anti-communist at this time, as the notion of the ‘total national strategy’ against the ‘total onslaught’ of communism became the all-encompassing factor that determined foreign policy. SA’s détente politics toward Africa at this time was pursued rather successfully prior to the Angolan intervention in order to establish buffer zones, which would hopefully protect SA from the increasing communist threat. In addition, SA was becoming increasingly worried about this possible threat as the USSR and Cuba were enlarging their support to the MPLA after the coup in Portugal in 1974. The concentration of SWAPO insurgents on the southern Angola border furthermore endangered SA’s interests in SWA, as SWAPO was one of the MPLA’s biggest African allies. Both the MPLA and SWAPO were seen as Soviet proxies during the Cold War. In addition, SA was pressured by some in the international community to get involved in Angola for the first time. The USA, like SA, was also strongly anti-communist and supported SA’s initial involvement to some extent. France also had concerns. SA also saw its limited initial involvement as an opportunity to establish a less hostile government in Angola, than what was already established in Mozambique. The FNLA, UNITA and several African and international actors such as Zaire and even Zambia made similar requests. South Africa decided that it would be in its own as well as the region’s best interest to intervene in the Angolan conflict. |
[From South Africa’s Intervention in Angola: Before Cuito Cuanavale and Thereafter file:///E:/Angola%202/labuschagne_south_2009.pdf. Accessed on 05 April 2020.]
SOURCE 2C
The extract below indicates how the United States of America supported UNITA during the Angolan Civil War.
The Central Intelligence Agency (CIA) made its first major weapons shipment to the FNLA in July 1975. Thus, like the Russians and Chinese, the United States was giving aid to one side of Angolan Civil War on a level far greater than it had ever provided during the struggle against Portuguese colonialism. The United States was directly involved in the civil war to a marked (noticeable) degree. In addition to training Angolan combat units, US personnel did considerable flying between Zaire and Congo carrying out reconnaissance (investigation) and supply missions, and the CIA spent over a million dollars on an ambitious mercenary (hired soldiers) programme. Several reports appeared in the US press stating that many American guerrillas were fighting in Angola against the MPLA from ‘scores’ to ‘300’ and that many others were recruited and trained in the United States to join them. But John Stockwell, the head of CIA’s Angola task force, puts the number of American mercenaries who actually made it to Angola at only 24. The CIA was also directly financing the arming of British mercenaries (fighting in Angola). Subsequently (later) the Secretary of the State, Henry Kissinger, informed the Senate that ‘the CIA is not involved’ in the recruitment of mercenaries for Angola. … Through recruited journalists representing major news service, the Agency (CIA) was able to generate international coverage of false reports for Soviet advisers in Angola. One CIA story, announced to the press by UNITA, was that 20 Russians and 35 Cubans had been captured. Another fabrication (lie) concerned alleged rapes committed by Cuban soldiers in Angola; this was elaborated to include their capture, trial and execution … |
[From http://williamblum.org/chapters/killing-hope/angola. Accessed on 7 March 2020.]
SOURCE 2D
This poster depicts President Agostinho Neto and Fidel Castro after Angolan independence celebrations.
[From https://mrdivis.wordpress.com/2016/12/02/remembering-fidel-castros-impact-in-southern-africa/.
Accessed on 7 March 2020.]
QUESTION 3:
WHAT WAS THE IMPACT OF THE BLACK POWER MOVEMENT ON AFRICAN AMERICANS IN THE 1960s?
SOURCE 3A
The extract below outlines Stokely Carmichael’s explanation regarding the philosophy of Black Power.
The Black Power Movement grew out of the Civil Rights Movement that had steadily gained momentum through the 1950s and 1960s. Although not a formal movement, the Black Power Movement marked a turning point in black-white relations in the United States and in how blacks saw themselves. The movement was hailed (welcomed) by some as a positive and proactive force aimed at helping blacks achieve full equality with whites, but it was reviled (hated) by others as a militant, sometimes violent faction whose primary goal was to drive a wedge (division) between whites and blacks. In truth, the Black Power Movement was a complex event that took place at a time when society and culture were being transformed throughout the United States, and its legacy reflects that complexity. Blacks still faced lower wages than whites, higher crime rates in their neighbourhoods, and unspoken but palpable (deep) racial discrimination. Young blacks in particular saw the Civil Rights Movement as too mainstream to generate real social change. What they wanted was something that would accelerate (quicken) the process and give blacks the same opportunities as whites, not just socially but also economically and politically. Perhaps more important, they felt that the Civil Rights Movement was based more on white perceptions of civil rights than black perceptions. By the mid-1960s, dissatisfaction with the pace of change was growing among blacks. The term 'black power' had been around since the 1950s, but it was Stokely Carmichael, head of the Student Non-violent Co-ordinating Committee (SNCC), who popularised the term in 1966. |
[From http://www.encyclopedia.com/social-sciences-and-law/sociology-and-social- reform/socialreform/black-power-movement. Accessed on 18 November 2019.]
SOURCE 3B
The source below explains the reasons why the Black Panther Party launched their breakfast programme.
In 1969, a group of children sat down to a free breakfast before school. On the menu: chocolate milk, eggs, meat, cereal and fresh oranges. The scene wouldn’t be out of place in a school cafeteria these days – but the federal government wasn’t providing the food. Instead, breakfast was served thanks to the Black Panther Party. At the time, the militant Black Nationalist party was vilified (criticised) in the news media and feared by those intimidated by its message of black power and its commitment to ending police brutality and subjugation (suppression) of black Americans. But for students eating breakfast, the Black Panther’s politics were less interesting than the meals they were providing. “The children, many of whom had never eaten breakfast before the Panthers started their program,’’ The Sun reporter wrote, “think the Panthers are ‘groovy’ and ‘very nice’ for doing this for them.’’ The program may have been groovy, but its purpose was to fuel revolution by encouraging black people’s survival. From 1969 through the early 1970s, the Black Panthers’ Free Breakfast for School Children Program fed tens of thousands of hungry kids. … School officials immediately reported results in kids who had free breakfast before school. “The school principal came down and told us how different the children were’’, Ruth Beckford, a parishioner who helped with the program, said later. “They weren’t falling asleep in class, they weren’t crying with stomach cramps.’’ … Food wasn’t the only part of the BPP’s social programs; they expanded to cover everything from free medical clinics to community ambulance services and legal clinics. |
[From //www.hist.com/news/free-school-breakfast-black-panther-party. Accessed on 07 March 2020.]
SOURCE 3C
This photograph shows members of the Philadelphia Black Panthers organisation, serving breakfast to children.
[From https://www.cbsnews.com/pictures/inside-the-black-panthers-photographer-stephen-
shames/16/. Accessed on 21 November 2019.]
SOURCE 3D
The source below is an extract of an article written by Mary Philips called Power of the First-person narrative: Ericka Huggins and the Black Panther Party.
Born Ericka Cozette Jenkins on January 5, 1948, in Washington, DC, Huggins joined the BPP in 1967 in Los Angeles. As a college student at Lincoln University in Pennsylvania, she was involved in the Black Student Congress (BSC), a campus organisation, despite the fact that the BSC was resistant to female membership: “They didn’t appreciate women joining the Black Student Congress as it was called then but they did let me join” (Interview by the author, July 20, 2011). In college, she read a Ramparts magazine article on charges against Huey P. Newton for the murder of an Oakland police officer. Moved by the inhumane treatment of Newton after his arrest, Huggins mentioned the picture in that Ramparts magazine article showed Huey without a shirt strapped to a hospital gurney, with a bullet wound in his stomach. The white police officer was obviously guarding the camera. Inspired by the image and the story, she and her lover, John Huggins, decided to leave school, move to California, and join the BPP. She later married Huggins and they had a daughter, Mai. In the BPP, Ericka Huggins served in many capacities, including working as editor of the BPP newspaper, The Black Panther, also known as The Black Panther Intercommunal News Service. When her husband was murdered by COINTELPRO agents, Huggins moved to her hometown and opened a BPP branch in New Haven, Connecticut. After her arrest, trial, and release in 1971, she served as director of the BPP’s Oakland Community School (OCS), maintaining its daily affairs from 1973 to 1981. She co-wrote the curriculum as well as grants for the school, in addition to supervising and managing staff members. While serving as director, she travelled the country delivering presentations on the school’s pedagogy. |
[From https://www.erickahuggins.com/resources. Accessed on 21 November 2019.]
ACKNOWLEDGEMENTS
Visual sources and other historical evidence were taken from the following:
http://www.mtholyoke.edu/acad/intrel/precrisis.htm
https://www.gettyimages.com/photos/cuban-missile- crisis?mediatype=photography&phrase =cuban%20missile%20crisis&sort=mostpopula
https://spartacus-educational.com.
https://microsites.jfklibrary.org/cmc/oct26/doc4.html
https://history.state.gov/milestones/1969-1976/angola
South Africa’s Intervention in Angola: Before Cuito Cuanavale and Thereafter file:///E:/Angola%202/labuschagne_south_2009.pdf.
http://williamblum.org/chapters/killing-hope/angola
https://mrdivis.wordpress.com/2016/12/02/remembering-fidel-castros-impact-in- southern-africa/.
http://www.encyclopedia.com/social-sciences-and-law/sociology-and-social- reform/socialreform/black-power-movement
www.hist.com/news/free-school-breakfast-black-panther-party.
https://www.cbsnews.com/pictures/inside-the-black-panthers-photographer-stephen- shames/16/.
https://www.erickahuggins.com/resources