Adele
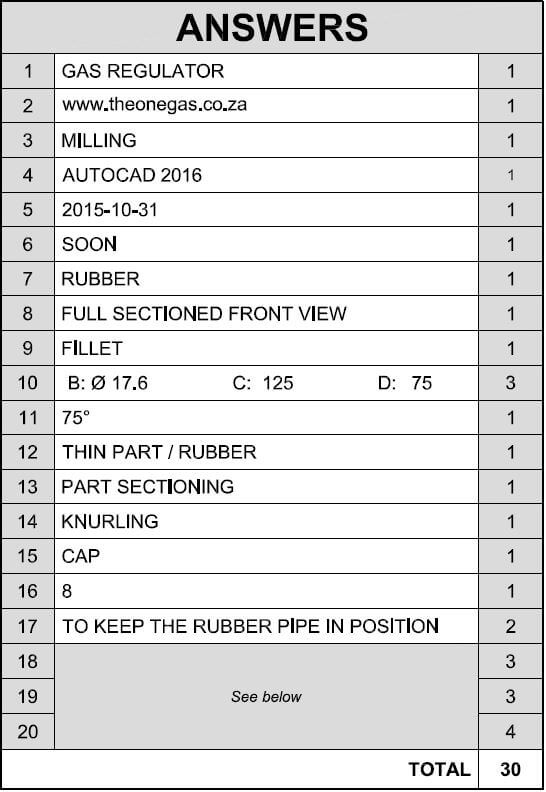
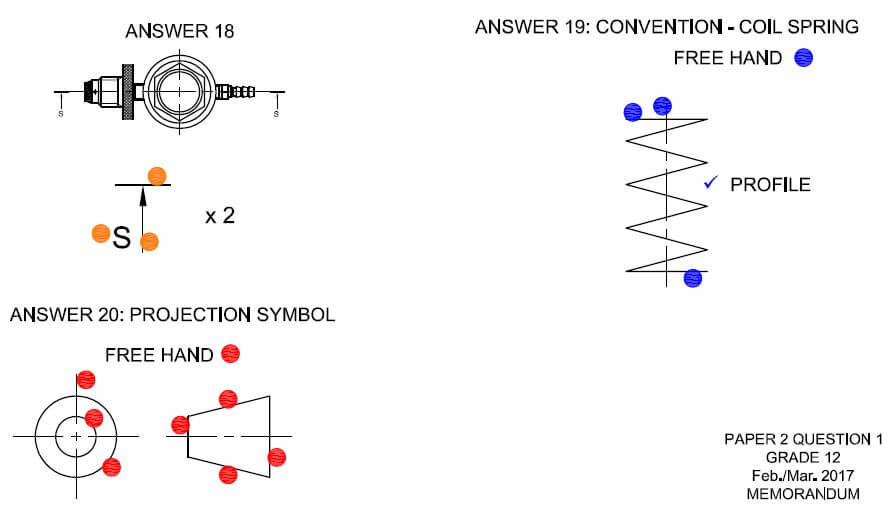
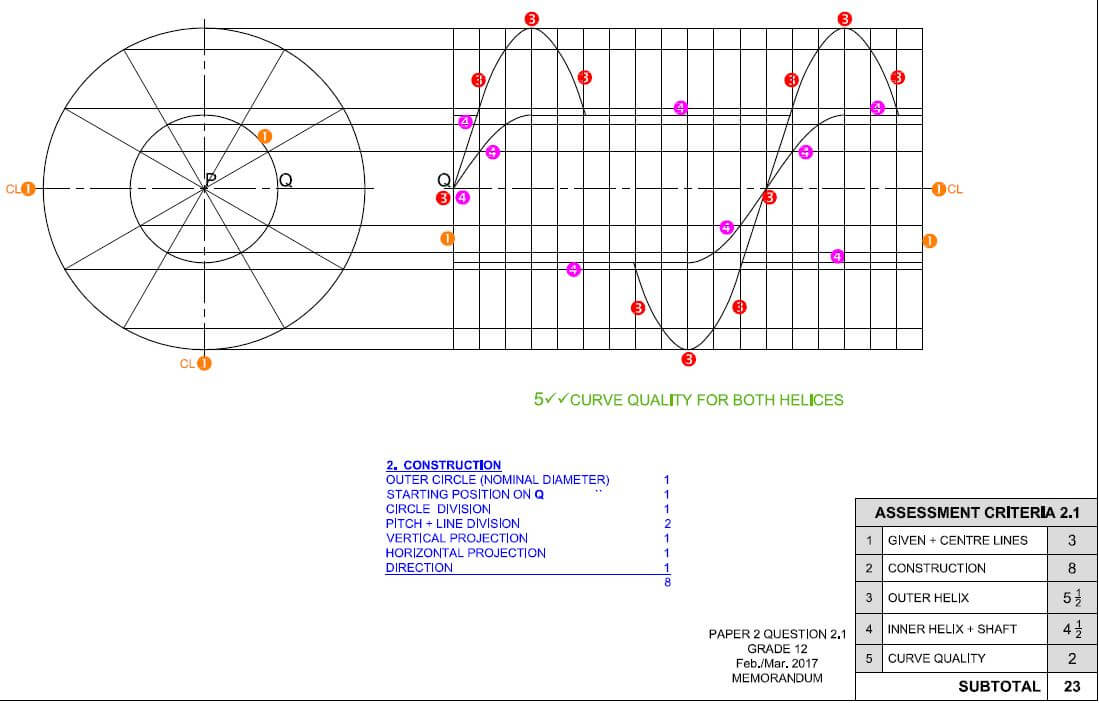
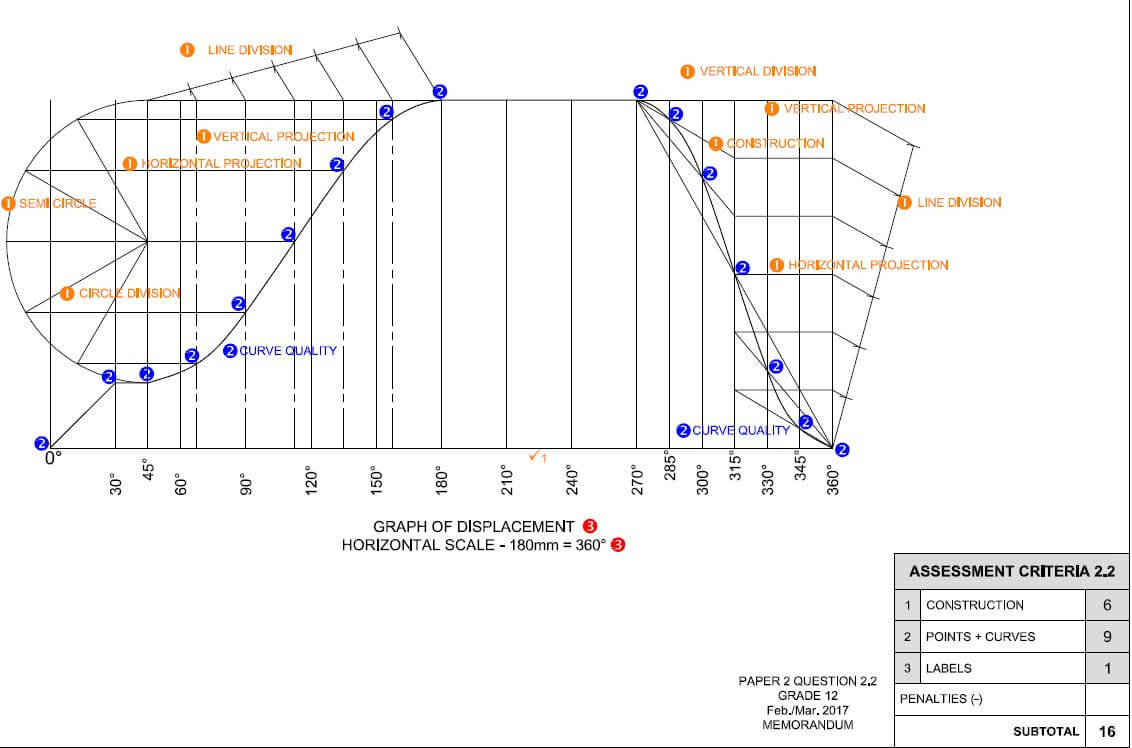
MECHANICAL TECHNOLOGY GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
MECHANICAL TECHNOLOGY
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of TEN questions.
- Write your centre number and examination number in the spaces provided on the ANSWER BOOK.
- Read ALL the questions carefully.
- Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Show ALL calculations and units. Round off ALL answers to TWO decimal places.
- Candidates may use non-programmable, scientific calculators and drawing instruments.
- Take the value of gravitational force as 10 m/s-2.
- All dimensions are in millimetres, unless stated otherwise in the question.
- A formula sheet for your use is attached to this question paper.
- Write neatly and legibly.
- Use the guidelines below to assist you in managing your time.
QUESTION | CONTENT | MARKS | TIME (minutes) |
1 | Multiple-choice questions | 20 | 15 |
2 | Safety | 10 | 10 |
3 | Tools and Equipment | 12 | 10 |
4 | Materials | 13 | 10 |
5 | Terminology | 30 | 20 |
6 | Joining Methods | 25 | 25 |
7 | Forces | 30 | 30 |
8 | Maintenance | 15 | 15 |
9 | Systems and Control | 25 | 25 |
10 | Turbines | 20 | 20 |
TOTAL | 200 | 180 | |
QUESTIONS
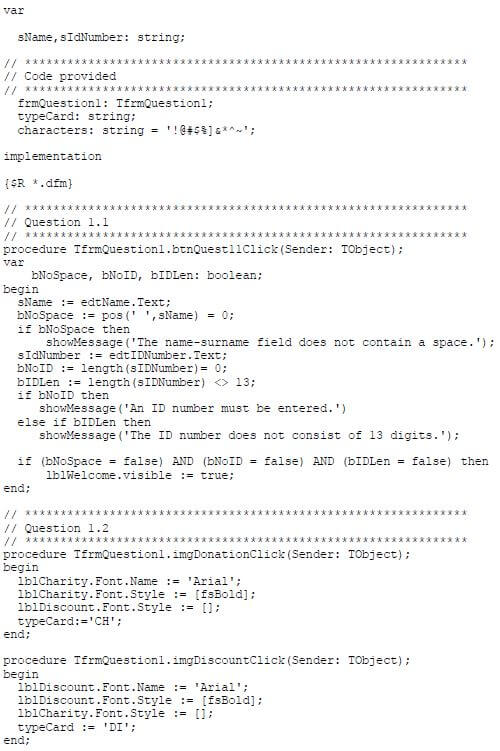
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Write down the question number (1.1–1.20), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE: |
1.1 Which ONE of the following safety measures applies to a power saw?
- Make sure that the cutting speed is set at the highest setting for the best performance.
- Long pieces of material must be supported at the ends.
- Make sure the blade is properly oiled.
- Tighten the blade while the machine is in motion. (1)
1.2 Which ONE of the following safety measures applies to a tensile tester?
- Apply excessive pressure on the tester.
- Use a hammer to remove a test piece.
- Lower the fluid level of the tester.
- Wear eye protection. (1)
1.3 A Rockwell tester is used to test the … of a material.
- tension
- elasticity
- hardness
- brittleness (1)
1.4 Which ONE of the following is a reason for a high carbon-monoxide reading on an internal combustion engine?
- High compression
- Warm valves
- A clogged air filter
- Piston rings set too tight (1)
1.5 An austenite structure is …
- strong and brittle.
- soft and malleable.
- hard and malleable.
- soft and brittle. (1)
1.6 The second arrest temperature (AC2) for carbon steel is …
- 1 000 °C.
- 120 °C.
- 320 °C.
- 800 °C. (1)
1.7 The minimum diameter of a screw thread is measured at the … of the screw thread.
- root
- axis
- crest
- lead (1)
1.8 What is the gear ratio of a Cincinnati dividing head used on a milling machine?
- 60 : 1
- 40 : 1
- 50 : 1
- 30 : 1 (1)
1.9 Which ONE of the following is a common cause of incomplete penetration into a welded joint?
- The welding current was too low
- Slag not removed from the first weld before the second weld was run
- Faulty restart by not restarting at the top of the previous weld run
- Dirty or wet electrodes used when arc welding (1)
1.10 What does the X-ray test on a welded joint detect?
- External defects
- Internal defects
- Surface defects
- Visual defects (1)
1.11 One (1) Pascal can be expressed as …
- 1 kg acting on 1 m2.
- 1 N acting on 1 m2.
- 1 kg acting on 1 mm2.
- 1 N acting on 1 mm2. (1)D
1.12 What is understood by Young's elasticity modulus?
- The force value required to produce a unit area in a tensile test specimen
- The ratio between stress and strain in a metal, provided that the limit of elasticity is not exceeded
- The measurement of the extension or contraction of material due to the load
- The ratio of the deformation because of the application of an external force (1)
1.13 What is represented by point D on the stress-strain graph shown in FIGURE 1.1? 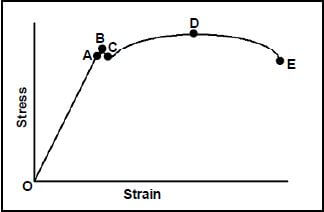
FIGURE 1.1
- The limit of proportionality
- The limit of elasticity
- The minimum stress
- The maximum stress (1)
1.14 Where is extreme pressure (EP) oil used?
- In the engine
- In the power steering
- In the brakes
- In the differential (1)
1.15 What is the purpose of using cutting fluid on a lathe or milling machine?
- Cools the cutting tool
- Makes chips stick to the cutter
- Reduces the quality of the finish
- Serves as a non-lubricant (1)
1.16 FIGURE 1.2 below shows three gears meshing. What is the purpose of idler gear B? 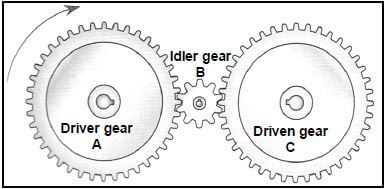
FIGURE 1.2
- Increases the final rotation frequency
- Decreases the final rotation frequency
- Rotates the driven gear in the same direction as the driver gear
- Rotates the driven gear in the opposite direction to the driver gear (1)
1.17 What will the rotation frequency of pulley B be if pulley A rotates at 2 000 r/min, as shown in FIGURE 1.3 below? 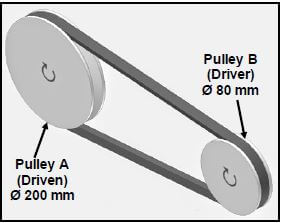
FIGURE 1.3
- 5 000 r/min
- 2 500 r/min
- 2 000 r/min
- 1 000 r/min (1)
1.18 Determine the speed ratio of the chain drive of the bicycle, as shown in FIGURE 1.4. 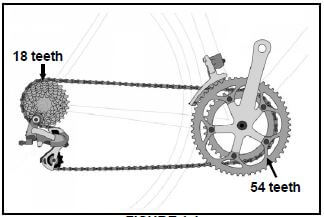
FIGURE 1.4
- 3 : 1
- 1 : 3
- 1 : 18
- 1 : 54 (1)
1.19 The function of a supercharger fitted to an internal combustion engine is to compress air by a/an … action.
- electronic
- mechanical
- electrical
- analogue (1)
1.20 What do you understand by the term boost in respect of turbochargers?
- The pressure that a turbocharger creates in the inlet manifold
- Where the blower is placed before the carburettor
- The centrifugal force to create decompression of the inlet force
- Where the blower is placed after the carburettor (1)
[20]
QUESTION 2: SAFETY
2.1 Which TWO safety precautions must be observed when working with a coil spring compressor? (2)
2.2 State THREE safety precautions that should be observed before pressing a bearing from a shaft using a hydraulic press. (3)
2.3 Thabo uses a beam-bending tester to determine the degree of deflection of a work piece. State TWO safety precautions to be considered when using the beam-bending tester. (2)
2.4 Name ONE distinct safety precaution when using EACH of the following items of testing equipment:
2.4.1 Brinell tester (1)
2.4.2 Gear and bearing puller (1)
2.4.3 Torsion tester (1)
[10]
QUESTION 3: TOOLS AND EQUIPMENT
3.1 Give TWO reasons for low fuel pressure. (2)
3.2 Which precision measuring instrument is used to measure the following accurately:
3.2.1 The depth of a blind hole (1)
3.2.2 The pitch diameter of a V-screw thread (1)
3.3 A depth micrometer reading is shown in FIGURE 3.1. The micrometer is extended with a 50–75 mm interchangeable rod. Give the complete reading with the unit. 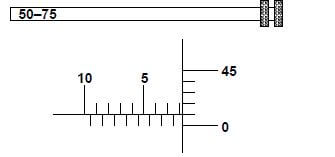
FIGURE 3.1 (2)
3.4 Name TWO measurements that can be taken with a multimeter. (2)
3.5 Explain TWO ways in which you will detect cylinder leakages from an internal combustion engine. (2)
3.6 State TWO uses of the cooling system pressure tester. (2)
[12]
QUESTION 4: MATERIALS
4.1 Name TWO properties of EACH of the following structures of steel:
4.1.1 Cementite (2)
4.1.2 Pearlite (2)
4.2 FIGURE 4.1 shows a diagram. Answer the questions that follow. 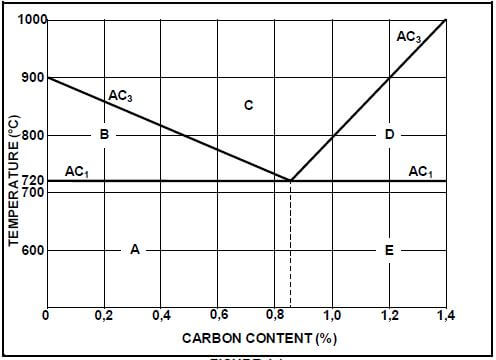
FIGURE 4.1
4.2.1 What is the diagram in FIGURE 4.1 above called? (1)
4.2.2 Label A–E shown on the diagram. (5)
4.2.3 State TWO properties of C on the diagram. (2)
4.3 What is the lower critical temperature for carbon steel with a carbon content of 0,87%? (1)
[13]
QUESTION 5: TERMINOLOGY
5.1 A spur gear with 118 teeth must be cut on a universal milling machine. Calculate the indexing required to cut this gear with the help of a Cincinnati dividing head. (3)
5.2 Use simple line sketches to explain the difference between up-cut milling and down-cut milling on a milling machine. Indicate the work-piece feed and cutter rotation. (4)
5.3 A tapered gib-head key must be made to fit a 102 mm diameter shaft. Calculate the following key dimensions:
5.3.1 The width of the key (2)
5.3.2 The thickness of the key (2)
5.3.3 The length of the key (2)
5.3.4 The thickness of the key at the smaller end (4)
5.4 A spur gear has 60 teeth and a module of 3. Calculate the following in respect of the spur gear:
5.4.1 Addendum (1)
5.4.2 Dedendum (2)
5.4.3 Clearance (2)
5.4.4 Pitch circle diameter (2)
5.4.5 Outside diameter (2)
5.4.6 Cutting depth (2)
5.4.7 Circular pitch (2)
[30]
QUESTION 6: JOINING METHODS
6.1 What welding defect is described as non-metallic solids trapped in the weld metal? (1)
6.2 Name FOUR defects that may be observed during visual inspections. (4)
6.3 State TWO causes of incomplete penetration in a welded joint. (2)
6.4 Name TWO measures to prevent a lack of fusion in a welded joint (2)
6.5 Identify the destructive tests described below that are applied to a welded joint:
6.5.1 To determine the weld hardness and strength (1)
6.5.2 To reveal internal defects (1)
6.5.3 To determine the ductility of the deposit and the heat-affected area adjacent to the weld (1)
6.6 Explain how you will conduct a dye penetration test on a welded joint. (7)
6.7 State ONE function of EACH of the following components on the MIG/MAGS welding equipment:
6.7.1 Wire feed controller (2)
6.7.2 Welding gun (2)
6.8 What is the function of the inert gas used during the MIG/MAGS welding process? (2)
[25]
QUESTION 7: FORCES
7.1 Four pulling forces of 1,2 kN, 2 kN, 3,4 kN and 1,8 kN are acting on the same point, as shown in FIGURE 7.1 below. Determine, by means of calculations, the magnitude and direction of the resultant of the system of forces. 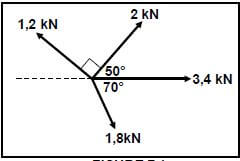
FIGURE 7.1 (13)
7.2 A load of 40 kN is exerted on a brass bush used in a hydraulic press. The outer and inner diameters of the bush are 98 mm and 67 mm respectively. The original length of the bush is 80 mm and Young's modulus for brass is 90 GPa.
Calculate the:
7.2.1 Stress in the bush material (5)
7.2.2 Strain (3)
7.2.3 Change in length (3)
7.3 FIGURE 7.2 below shows a uniform beam that is supported by two vertical supports, A and B. Two vertical point loads of 200 N and 600 N, together with a uniformly distributed force of 80 N/m over the total length of the beam, are acting on the beam. Determine, by means of calculations, the magnitudes of the reactions in supports A and B. 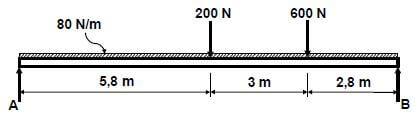
FIGURE 7.2 (6)
[30]
QUESTION 8: MAINTENANCE
8.1 Define preventative maintenance. (2)
8.2 Why is it important to ensure that a machine is switched off and locked out when doing maintenance on belt drives? (2)
8.3 What is clutch-pedal free play? (2)
8.4 What is meant by the term viscosity index? (1)
8.5 Give TWO reasons why the clutch plate in a motor vehicle's clutch assembly is replaced. (2)
8.6 Why does grease have a very high viscosity? (2) 8.7 What is cutting fluid? (2)
8.8 Give a reason why the viscosity of a cutting fluid should be low. (2)
[15]
QUESTION 9: SYSTEMS AND CONTROL
9.1 FIGURE 9.1 below shows a gear-drive system. Driver gear A on the shaft of the electric motor has 18 teeth that mesh with gear B, with 36 teeth, on a countershaft. There is another driver gear, C, with 16 teeth, on this countershaft, which meshes with a gear D, with 46 teeth, on the output shaft. 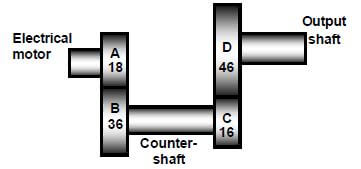
FIGURE 9.1
Calculate the:
9.1.1 Rotation frequency of the output shaft if the electric motor rotates at 1 660 r/min (3)
9.1.2 Velocity ratio between the input shaft and output shaft (2)
9.2 FIGURE 9.2 shows a belt-drive system with a 230 mm driver pulley. The belt speed of the 12 mm thick V-belt is 36 m.s-1. The tensile force in the slack side is 110 N and the ratio between the force in the tight side and the force in the slack side is 2,5. 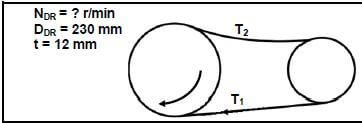
FIGURE 9.2
9.2.1 Rotation frequency of the driver pulley in r/min (revolutions per minute) (4)
9.2.2 Power transmitted (4)
9.3 A hydraulic system is represented diagrammatically inFIGURE 9.3. 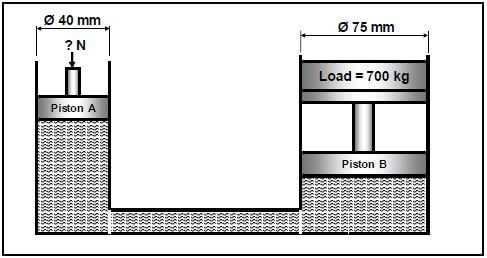
FIGURE 9.3
Calculate the:
9.3.1 Fluid pressure in the hydraulic system when in equilibrium (4)
9.3.2 Effort force needed on piston A to lift the load of 700 kg with piston B (4)
9.4 What is the purpose of the anti-lock brake system (ABS) in a vehicle? (2)
9.5 Explain why a seat belt in a vehicle is described as an 'active' safety feature. (2)
[25]
QUESTION 10: TURBINES
10.1 Name TWO types of impulse turbines. (2)
10.2 FIGURE 10.1 shows a water turbine driving a generator. Answer the questions that follow. 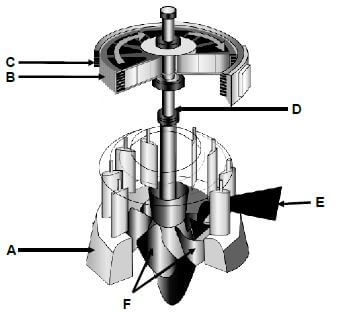
FIGURE 10.1
10.2.1 Identify the type of turbine shown in FIGURE 10.1 above. (1) 10.2.2 Label A–F. (6)
10.2.3 State TWO advantages of the turbine shown in FIGURE 10.1 above. (2)
10.3 State TWO advantages of EACH of the following:
10.3.1 Supercharger (2)
10.3.2 Steam turbine (2)
10.3.3 Gas turbine (2)
10.4 Explain the term turbo lag in terms of a turbocharger. (3)
[20]
TOTAL: 200

INFORMATION TECHNOLOGY PAPER 1 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
INFORMATION TECHNOLOGY
PAPER 1
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper is divided into THREE sections. Candidates must answer ALL THREE sections.
- The duration of this examination is three hours. Because of the nature of this examination it is important to note that you will not be permitted to leave the examination room before the end of the examination session.
- This question paper is set with programming terms that are not specific to any particular programming language (Delphi/Java (using the Netbeans IDE)).
- Make sure that you answer the questions according to the specifications that are given in each question. Marks will be awarded according to the set requirements.
- Answer only what is asked in each question. For example, if the question does not ask for data validation, then no marks will be awarded for data validation.
- Your programs must be coded in such a way that they will work with any data and not just the sample data supplied or any data extracts that appear in the question paper.
- Routines, such as search, sort and selection, must be developed from first principles. You may NOT use the built-in features of a programming language for any of these routines.
- All data structures must be defined by you, the programmer, unless the data structures are supplied.
- You must save your work regularly on the disk/CD/DVD/flash disk you have been given, or on the disk space allocated to you for this examination session.
- Make sure that your examination number appears as a comment in every program that you code, as well as on every event indicated.
- If required, print the programming code of all the programs/classes that you completed. You will be given half an hour printing time after the examination session.
- At the end of this examination session you must hand in a disk/CD/DVD/flash disk with all your work saved on it OR you must make sure that all your work has been saved on the disk space allocated to you for this examination session. Ensure that all files can be read.
- The files that you need to complete this question paper have been given to you on the disk/CD/DVD/flash disk or on the disk space allocated to you. The files are provided in the form of password-protected executable files.
NOTE:- Delphi candidates must use the file DelphiDataENGMarch2017.exe. • Java candidates must use the file JavaDataENGMarch2017.exe.
Do the following:
- Double click on the password-protected executable file.
- Click on the extract button.
- Enter the following password: Prof4U@#!
Once extracted, the following list of files will be available in the folder DelphiDataENGMarch2017/JavaDataENGMarch2017:
| DELPHI FILES | JAVA (NETBEANS) FILES |
| Question1: | Question1: |
| Question1_P.dpr | Question1.form |
| Question1_P.dproj | Question1.java |
| Question1_P.res | Type1.PNG |
| Question1_U.dfm | Type2.PNG |
| Question1_U.pas | |
| Type1.PNG | |
| Type2.PNG | |
| Question2: | Question2: |
| CardHolder_U.pas | CardHolder.java |
| DataJanuary2017.txt | DataJanuary2017.txt |
| Question2_P.dpr | Question2.form |
| Question2_P.dproj | Question2.java |
| Question2_P.res | |
| Question2_U.dfm | |
| Question2_U.pas | |
| Question3: | Question3: |
| Question3_P.dpr | Question3.form |
| Question3_P.dproj | Question3.java |
| Question3_P.res | |
| Question3_U.dfm | |
| Question3_U.pas |
QUESTIONS
SCENARIO Loyalty cards are often used to create profiles for customers. It is also a popular way of motivating customers to visit shops that regularly award loyalty points for purchases made. |
SECTION A
QUESTION 1: GENERAL PROGRAMMING SKILLS
| An applicant must complete an application form to obtain a loyalty card. |
Do the following:
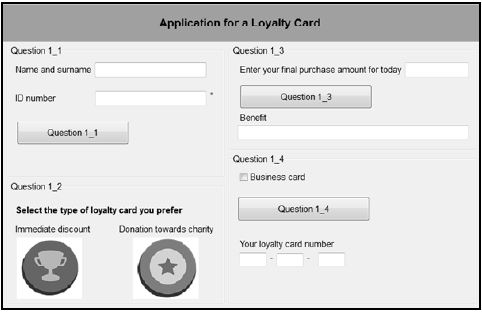
- Compile and execute the program found in the Question1 folder. The user interface displays four different sections named QUESTION 1_1 to QUESTION 1_4. Currently the program has no functionality.
Example of graphical user interface (GUI):
- Complete the code for each section of QUESTION 1, as described in QUESTION 1.1 to QUESTION 1.4 on the next page.
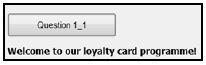
1.1 Button [Question 1_1]
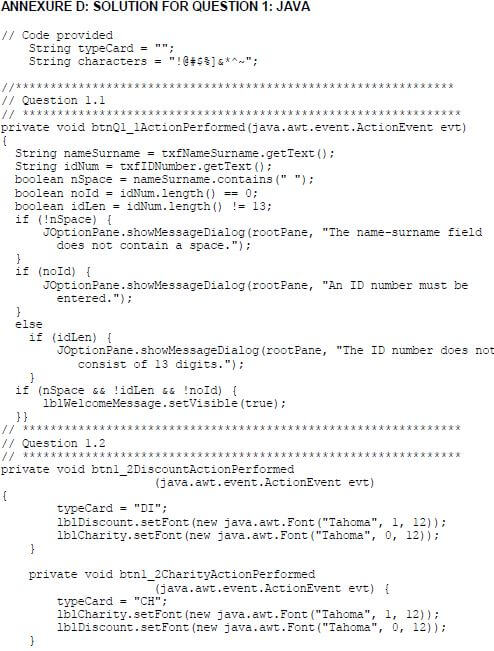
A label called lblWelcomeMessage has been created and set to be not visible. Write code to validate the information entered by the user as follows:
- Name and surname
The input must contain at least one space to be valid. If the input is not valid, display a message to indicate the specific error using a dialog box. - ID number
The asterisk character (*) next to the text box indicates that the field may not be left blank. An ID number must consist of 13 digits to be valid. If the ID number field does not contain any information or the ID number that was entered does not consist of 13 digits, display a message to indicate the specific error that occurred using a dialog box.
If the contents in both fields are valid, the label displaying the welcoming message must be set to visible.
Example of message if no space was entered in the name-surname field:
Example of message if the ID number field was left blank:
Example of message if the ID number that was entered does not consist of 13 digits:
![]() (14)
(14)
1.2 Buttons with images [Question 1_2]
A customer must select the preferred type of loyalty card. The images on the buttons in this section of the GUI show two types of loyalty cards. When a specific image is selected (button clicked), the program must do the following:
- The heading in the label above the selected image must be changed to bold.
- A code for the type of loyalty card that was selected must be assigned to the global variable typeCard that is provided. The code DI represents immediate discount and the code CH represents a donation towards charity.
NOTE: Only the label for the currently selected button must appear in bold. If the user selects the other type of loyalty card, the label of the previously selected loyalty card must NOT appear in bold. (6)
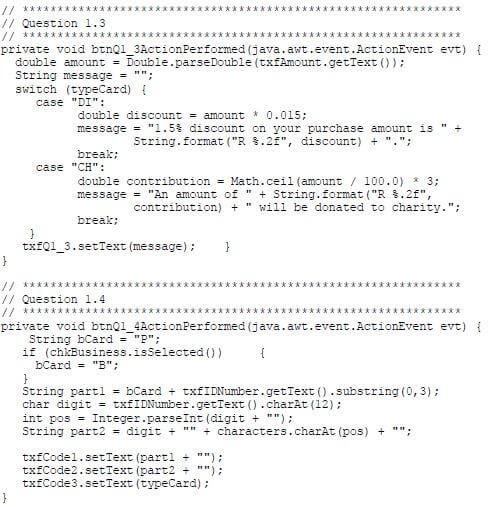
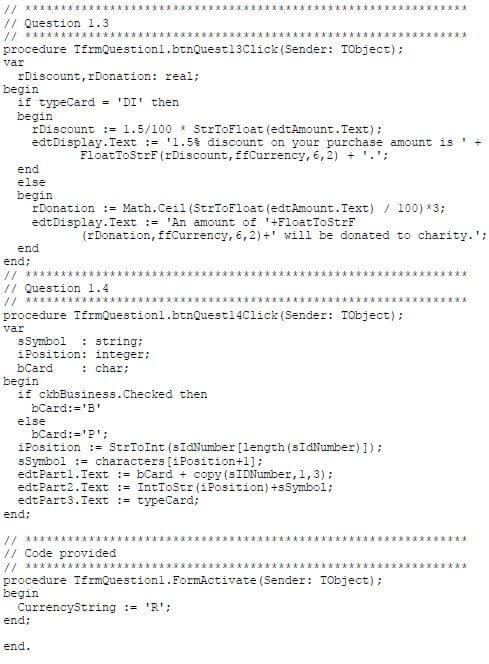
1.3 Button [Question 1_3]
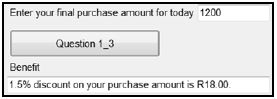
The final purchase amount for today must be entered in the text box.
The program must grant the following benefit towards the holder of the type of loyalty card selected in QUESTION 1_2:
- Immediate discount (DI):
1,5% discount must be granted on the purchase amount. - Donation towards charity (CH):
An amount of R3 will be donated to a charity organisation for every R100 or part of R100 spent by the loyalty card holder.
Display a message describing the benefit granted depending on the type of loyalty card.
Example of output if the code of the loyalty card is DI and the purchase amount R1 200:
NOTE: The discount amount must be displayed as a currency with two decimal digits.
Example of output if the code of the loyalty card is CH and the purchase amount R230:
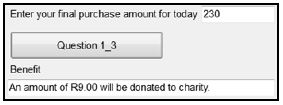
1.4 Button [Question 1_4]
The customer's ID number entered in QUESTION 1_1 and the type of loyalty card selected in QUESTION 1_2 are required to compile the customer's loyalty card number. A loyalty card number consists of three parts. Each part of the number must be compiled as follows and displayed in the components provided:
Part 1:
The first part of the loyalty card number consists of either the letter B if the business card check box was selected or the letter P if the business card check box was not selected, followed by the first three digits of the customer's ID number.
Part 2:
A string called charString, which contains the following 10 characters, has been supplied as part of the code provided:
! @ # $ % ] & * ^ ~
Each character contained in the string represents a digit (0–9). This means that the first character (!) represents the digit 0, the second character (@) the digit 1, and so on.
This part of the loyalty card number must consist of the last digit from the customer's ID number, followed by the character from charString that represents that digit.
Example of this part of the loyalty card number if the customer's ID number is 8802128756084:
4%
Part 3:
This part of the loyalty card number consists of the code representing the type of loyalty card (DI or CH) established in QUESTION 1_2.
Example of the loyalty card number of a customer with the following profile:
- Application for a business
- ID number: 9210140012083
- Card type: DI
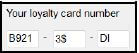 (13)
(13)
|
TOTAL SECTION A: 48
SECTION B
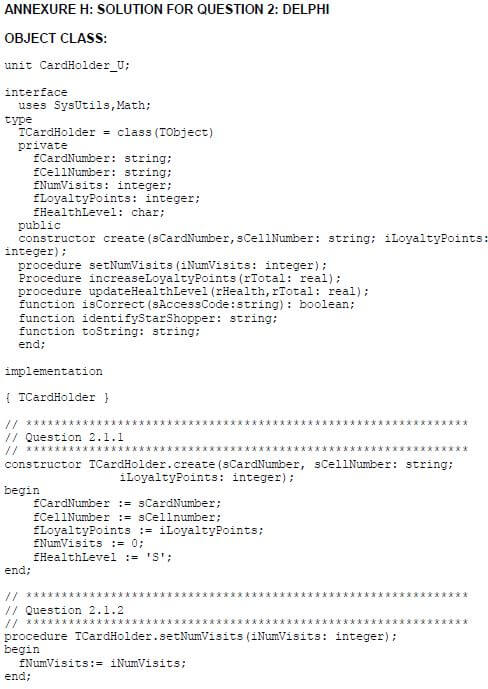
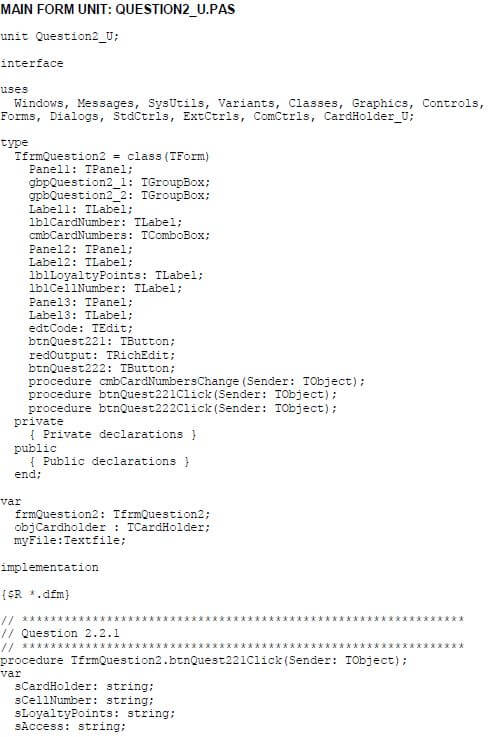
QUESTION 2: OBJECT-ORIENTATED PROGRAMMING
The local supermarket has a loyalty card system where customers can receive rewards depending on the number of visits, the number of loyalty points gathered and the percentage of health food bought.
Do the following:
Delphi programmers | Java programmers |
|
|
- Compile and execute the program. Currently the program has no functionality. Example of graphical user interface (GUI):
- Complete the code for this program, as specified in QUESTION 2.1 and QUESTION 2.2 below.
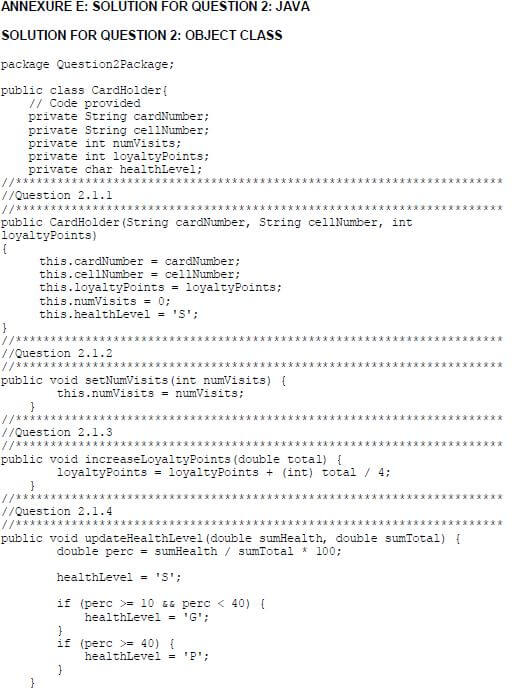
2.1 The given incomplete object class (TCardHolder/CardHolder) contains the declaration of five attributes, the toString() method and an incomplete isCorrect() method.
The given attributes of the CardHolder object:
NAMES OF ATTRIBUTES | DESCRIPTION | |
Delphi | Java | |
fCardNumber | cardNumber | A unique number for the card holder |
fCellNumber | cellNumber | The cellphone number of the card holder |
fNumVisits | numVisits | The number of times the card holder visited the shop during the month |
fLoyaltyPoints | loyaltyPoints | The total number of loyalty points received on this card up to now |
fHealthLevel | healthLevel | A character indicating the health level of the card holder, based on the amount of health food bought during the month: S – Silver (Lowest level) |
Complete the code in the given CardHolder class (TCardHolder/CardHolder) as described in QUESTION 2.1.1 to QUESTION 2.1.6 below.
2.1.1 Write code for a constructor method to receive the card number, cellphone number and loyalty card points already received, as parameter values. Assign these values to the relevant attributes. The lowest code for the health food level (S) must be assigned to the attribute for the health level. The attribute for the number of visits must be set to 0. (5)
2.1.2 Write a mutator method to be able to set the attribute for the number of visits to a value received as a parameter. (2)
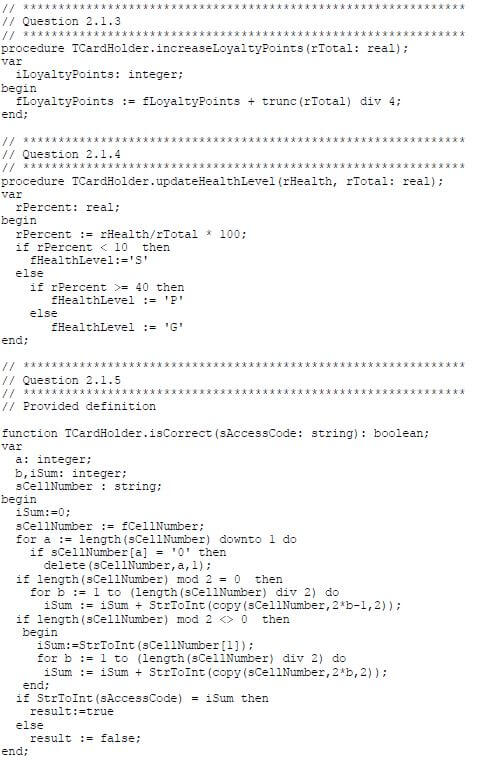
2.1.3 Write code for a method called increaseLoyaltyPoints that receives the total amount spent for this month as a parameter and increases the current number of loyalty points based on the amount received.
Use the following criteria:
- For every four rand (R4) spent, one loyalty point is awarded. (5)
2.1.4 Write code for a method called updateHealthLevel that will receive the total amount spent for this month and the amount spent on health food for this month as parameters. Calculate the percentage that was spent on health food and set the attribute for the health level according to the criteria provided in the table below.
Level code | Percentage indication |
S | Less than 10% |
G | 10% or more, but less than 40% |
P | 40% or more |
(7)
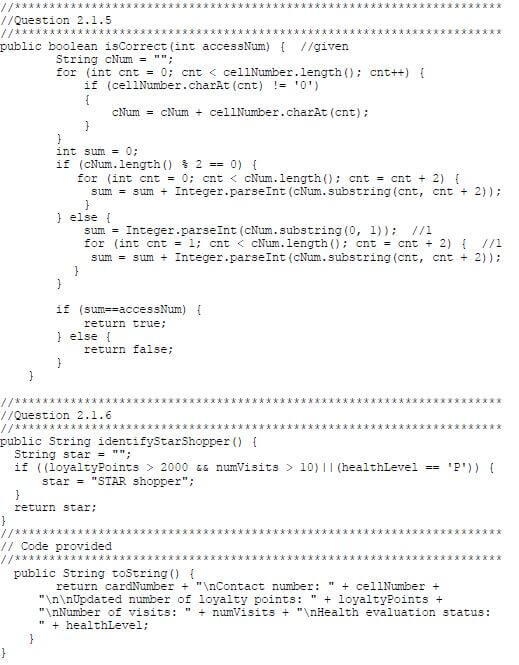
2.1.5 An access code is required to be able to update a customer's loyalty points. The customer's cellphone number has been used to compile the access code.
Write code to complete the isCorrect method provided. The method must test whether the access code received as a parameter is correct by applying the following instructions on the attribute for the cellphone number:
- Remove all zeros (0) from the cellphone number.
- Determine the sum of the remaining digits as follows:
- If the number of remaining digits is even, every two consecutive digits starting on the left-hand side must be regarded as a two digit value. Add all these two-digit values.
Example:
If the original cellphone number was 082 340 2113, the remaining digits without any zeros would be 82342113. The sum of the two-digit values is:
82 + 34 + 21 + 13 = 150 - If the number of remaining digits is odd, the first digit must be regarded as a one-digit value, and thereafter every two consecutive digits must be regarded as a two-digit value. Add all these values.
Example:
If the original cellphone number was 082 034 2101, the remaining digits after removing the zeros are 8234211. The sum of the values is:
8 + 23 + 42 + 11 = 84 (13)
- If the number of remaining digits is even, every two consecutive digits starting on the left-hand side must be regarded as a two digit value. Add all these two-digit values.
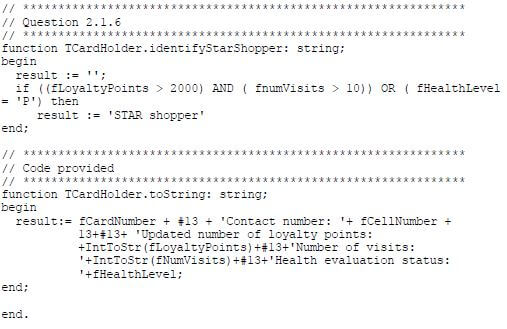
2.1.6 Write code for a method called identifyStarShopper that will return a string to indicate whether the card holder is a STAR shopper or not. A card holder is a STAR shopper if the following applies:
- The card holder earned more than 2 000 loyalty points and the shop was visited more than 10 times during the month.
OR - The health level of the card holder is platinum.
The string to be returned must either be 'STAR shopper' or an empty string. (6)
2.2 Information on the visits and purchases of card holders is saved for one month only in a text file. The text file called DataJanuary2017.txt contains the transactions made by four of the card holders during January.
The contents of text file is as follows:
- Every three lines represent a transaction for a specific loyalty card holder:
- Line 1: The card number of the card holder, for example B921-3$-DI
- Line 2: The total amount of the purchases for this visit, for example 1459.30
- Line 3: The amount spent on health food during this visit, for example 72.30
Example of the first 12 lines of the text file DataJanuary2017.txt:
B921-3$-DI
1459.30
72.30
B870-4%-CH
899.80
22.50
P730-7*-DI
299.30
62.85
B870-4%-CH
869.30
182.55
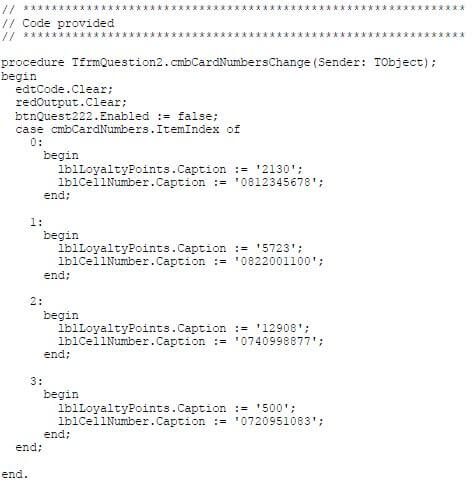
Do the following to complete the code for each button in the main form unit (Delphi)/GUI class (Java), as in the section that follows.
NOTE: The object objCardHolder has been declared globally as part of the provided code.
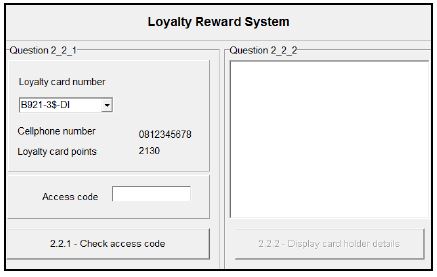
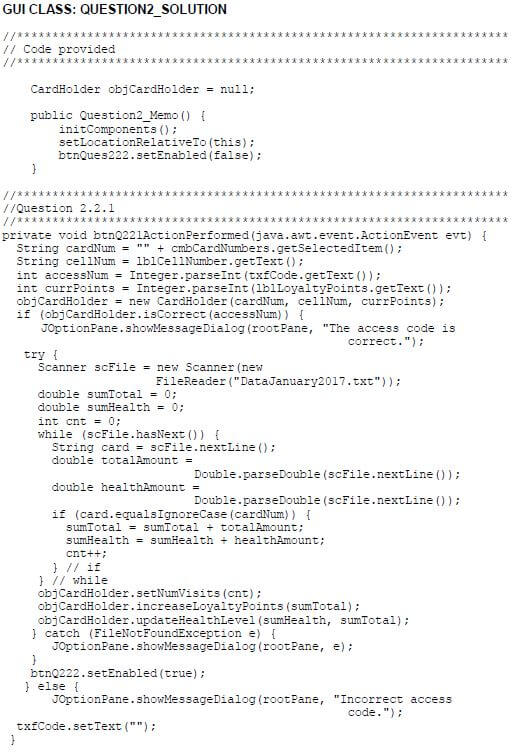
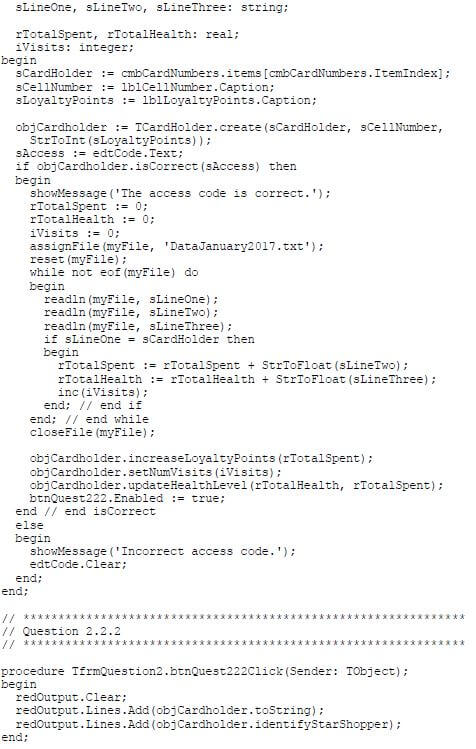
2.2.1 Button – [2.2.1 – Check access code]
The user is required to select a card number from the four card numbers provided in the combo box.
Once a card number has been selected in the combo box, the cellphone number of the card holder and the number of loyalty points already earned from previous purchases are displayed with the provided code.
The user must enter the correct access code for the selected card number to allow the program to process the data of the card holder saved in the text file.
Write code to do the following:
- Use the card number, cellphone number and loyalty points of the card holder to instantiate a card holder object.
- Use the method isCorrect to determine whether the access code that was entered is the correct access code for this card holder or not.
If the correct access code has been entered, use the data in the DataJanuary2017.txt text file to determine the following regarding the purchases of the card holder:
- The total amount spent for the month
- The amount spent on health-related products
- The number of times the user visited the shop and made purchases
Use this information and the relevant methods from the object class to update the number of loyalty points, the health level code and the number of times the card holder visited the shop for purchases.
Enable the button for QUESTION 2.2.2.
If the access code is NOT correct, display a message to indicate that the login was not successful and clear the access code text box.
The data in the table below can be used for testing purposes.
Card number | Access code |
B921-3$-DI | 188 |
B870-4%-CH | 41 |
P730-7*-DI | 338 |
B810-2#-DI | 170 |
(24)
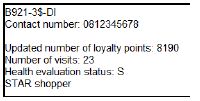
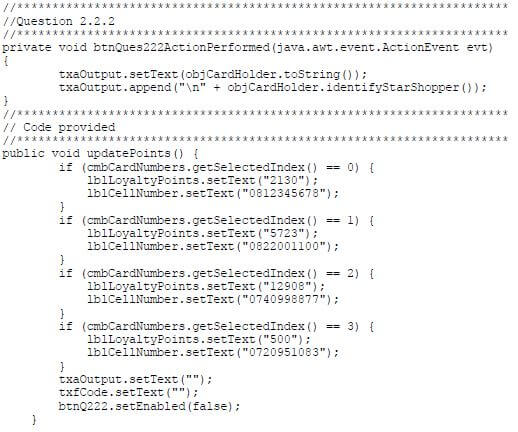
2.2.2 Button – [2.2.2 – Display card holder details]
Write code to use the toString method to display the card holder object data in the output area provided.
The method created in QUESTION 2.1.6 must be used to indicate if the card holder is a STAR shopper.
Example of output for card number B921-3$-DI:
Example of output for card number B870-4%-CH: 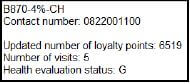 (3)
(3)
|
TOTAL SECTION B: 65
SECTION C
QUESTION 3: PROBLEM-SOLVING PROGRAMMING
SCENARIO A social media companion app called Dine-Is-Fine has been designed specifically for the 10 restaurants at your local mall. You and your friends are registered users of this app. The app can be used to share your location with other registered users. |
Do the following:
- Compile and execute the program in the Question3 folder. Currently the program has no functionality.
- Complete the code for each question, as described in QUESTION 3.1 to QUESTION 3.3.
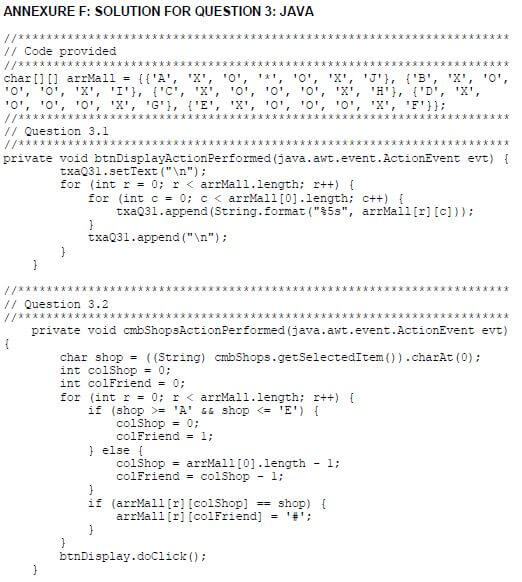
Supplied GUI: 
Supplied data:
You are provided with a two-dimensional array called arrMall filled with characters that represent the layout of the mall. The characters A to J represent 10 restaurants that you and your friends regularly visit.
Output area:
Decide on a suitable output component to be placed in the output area provided to display the content of the two-dimensional array.
NOTE:
- You are NOT allowed to modify supplied data manually. Code must be written to manipulate the supplied data according to the requirements.
- Good programming techniques and modular design must be applied in the design and coding of your solution.
- NO marks will be assigned for hardcoding. Use control structures and variables where necessary.
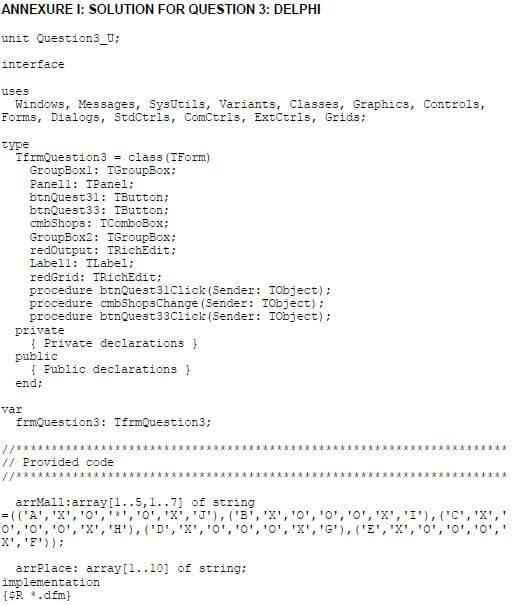
3.1 Button [Display layout]
The program must display the layout of the mall. Write code to use the data supplied in the two-dimensional array to display the layout in neat columns.
Example of output:  (5)
(5)
Explanation of the data in the array:
- The characters A to J represent the position of each of the 10 restaurants in the mall.
- The character X is a placeholder indicating that none of your friends are currently in a restaurant.
- The character O indicates the open area where one can move around.
- The asterisk character (*) indicates your position (first row and fourth column).
NOTE: You will always remain in the same position for the purpose of this question.
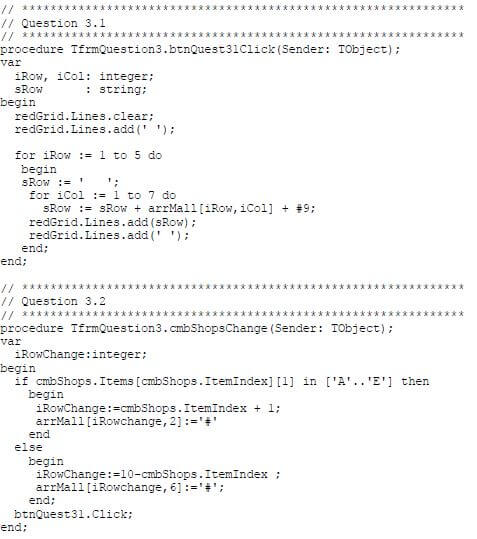
3.2 Combo box with restaurant codes
You are requested to select a restaurant from the combo box where one of your friends will dine.
Write code to replace the X placeholder at the selected restaurant with a hashtag symbol (#) to indicate that a friend is at the restaurant and display an updated layout of the mall.
Example of output if two of your friends are dining at restaurant C and F respectively:  (13)
(13)
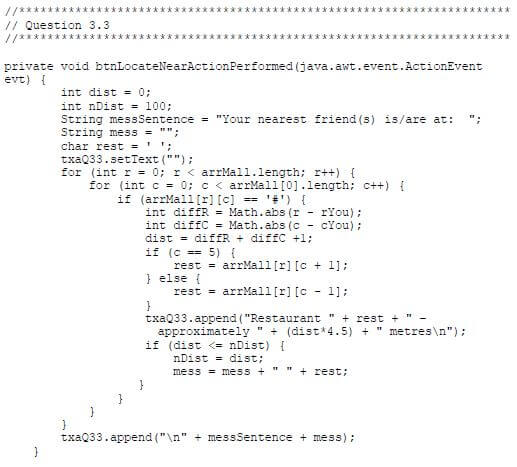
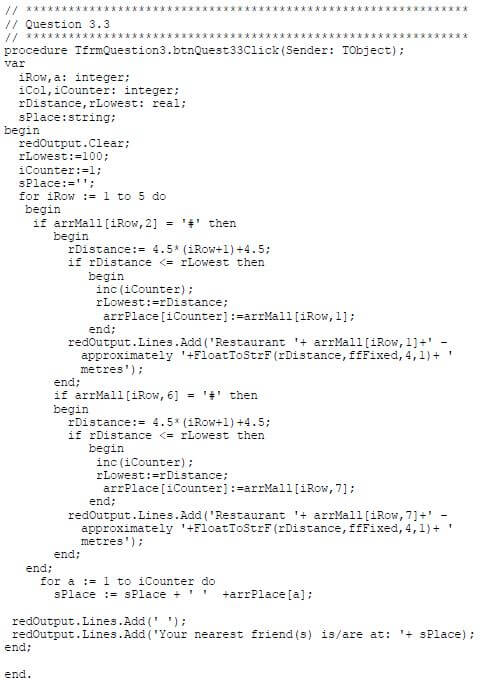
3.3 Button [Locate nearest friend(s)]
The program must determine at which restaurant(s) in the mall your friends currently are and how far they are from where you are. Every vertical or horizontal movement on the matrix represents a distance of 4,5 metres. From the restaurant(s) where your friends are, determine and display the restaurant(s) closest to where you are.
Example of output if your friends are dining at restaurants C and F: 
Example of output if your friends are dining at restaurants C, F and H: 
NOTE: You cannot move diagonally on the matrix.
MARK ALLOCATION FOR QUESTION 3.3
Locate the friends | 3 |
Determine the name of the restaurant | 4 |
Calculate the distance | 6 |
Find the nearest friend(s) | 3 |
Output to indicate position of friend(s) and distance | 2 |
Correct format of output for the nearest friend(s) | 1 |
TOTAL | 19 |
|
TOTAL SECTION C: 37
GRAND TOTAL: 150
INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
INFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A:Short Questions (15)
SECTION B:Systems Technologies (25)
SECTION C:Communication and Network Technologies (20)
SECTION D:Data and Information Management (25)
SECTION E:Solution Development (27)
SECTION F: Integrated Scenario (38) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.10), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE:
1.1.11 ![]()
1.1.1 Which ONE of the following does NOT conform to sound network etiquette?
- Send short attachments in e-mails.
- Always add a subject in the subject line of an e-mail.
- Always perform a spell check on an e-mail before sending.
- Respond only to high-priority e-mail messages. (1)
1.1.2 Which ONE of the following is a technique that is classified as social engineering?
- Analysing a password by using a round-robin attack tool
- Acquiring a username by calling a person and posing as a system administrator
- Accessing a system by using software vulnerabilities, such as buffer overflow
- Using a backdoor to gain access to a system to restore data (1)
1.1.3 Which ONE of the following has the largest storage capacity?
- 200 KB folder
- 32 GB flash disk
- 2 TB hard drive
- 740 MB DVD (1)
1.1.4 Which ONE of the following represents access speed in descending order?
- Cache, RAM, hard disk, magnetic tape
- RAM, cache, magnetic tape, hard disk
- Magnetic tape, hard disk, RAM, cache
- RAM, cache, hard disk, magnetic tape (1)
1.1.5 A software company requires '1 GB RAM minimum and 2 GB RAM recommended' for its new operating system. Which ONE of the following will be the likely outcome of attempting to install the operating system on a computer with 1 GB RAM?
- Files will fail to save.
- Peripheral devices will not work.
- The computer will not function at its optimum performance.
- The operating system will fail to install. (1)
1.1.6 The acronym for the connection on the motherboard between the CPU and the RAM is …
- USB.
- FSB.
- ZIF.
- NIC. (1)
1.1.7 Which ONE of the following icons represents a network drive? 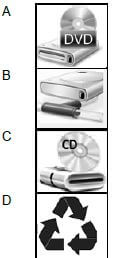
1.1.8 The correct conversion of D416 to a decimal number is …
- 212.
- 228.
- 77.
- 3 392. (1)
1.1.9 Which ONE of the following logic statements can be used to do a search for blue cars owned by a person with the surname Thomas or Moore?
- (CarColour = blue OR Surname = Thomas) OR Surname = Moore
- CarColour = blue OR (Surname = Thomas OR Surname = Moore)
- CarColour = blue AND (Surname = Thomas AND Surname = Moore)
- CarColour = blue AND (Surname = Thomas OR Surname = Moore) (1)
1.1.10 Which ONE of the following statements will calculate the bonus of a staff member correctly, if all staff members get a R100 bonus and a further 2% of their salary for each year of service?
- Bonus = Salary * 0.02 + YearsOfService + 100
- Bonus = (100 + YearsOfService) * Salary * 0.02
- Bonus = YearsOfService * Salary + 100 * 0.02
- Bonus = 100 + YearsOfService * Salary * 0.02 (1)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.2.1–1.2.5) in the ANSWER BOOK.
1.2.1 Copyright license that allows you to use, copy and distribute parts of published work for non-profit purposes (1)
1.2.2 An international community that develops open standards to ensure the long-term growth of the Web (1)
1.2.3 Companies that pay workers to repeatedly click on website elements to artificially increase or boost the status of a product or web page (1)
1.2.4 Increasing the speed of the system bus/clock, hence increasing the speed of all components of a computer system to enhance the performance (1)
1.2.5 The execution of physical tasks by computer-controlled machines rather than by human beings (1)
TOTAL SECTION A: 15
SCENARIO The IT class will be hosting a computer games evening as part of a fundraising campaign for the school. The gamers will be required to bring in their own computers and other devices for the evening. The computers and other devices used for the evening must meet certain basic hardware and software requirements to be used effectively for the selected games. |
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1 One of the gamers enquired whether or not his computer had sufficient capacity to be used for a specific game.
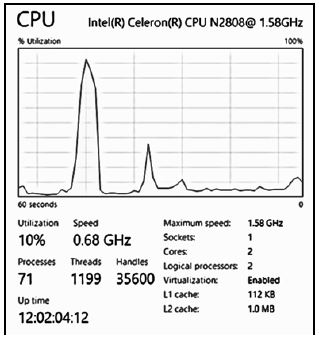
In the task manager of the computer system the performance of the CPU is indicated with the image below. Answer the questions that follow based on the information in the image.
2.1.1 Briefly explain what 'Threads' refers to in terms of processing when a program is executed. (2)
2.1.2 At the time when the image was captured, the operating system managed 71 active processes. Explain what process management, as executed by the operating system, entails. (2)
2.1.3 The speed of the processor with two cores is 1.58 GHz. Does the presence of two cores mean that tasks will be processed at double the speed of the CPU, that is 3.16 GHz? Explain your answer. (2)
2.1.4 The image indicates the sizes of L1 and L2 cache memory.
- What is cache memory? (2)
- What is the purpose of caching? (2)
2.2 One of the gamers asked your opinion on the upgrading of the hard drive of his computer. He wants you to explain the image below, which was part of an advertisement.
2.2.1 What does the abbreviation SSD stand for? (1)
2.2.2 Explain why the following will be features of an SSD:
- Silent operation (1)
- Faster performance (1)
2.2.3 All the system software, programs, data and more than one TB of music and videos are saved on the gamer's current hard disk.
He plans to keep the current hard drive and to add an SSD.
Suggest, with reasons, the best way to configure the computer to use the disks optimally. (4)
2.3 Gamers were advised to update the antivirus software on their computers. Why is it necessary to always keep the antivirus software up to date? (2)
2.4 The motherboards of the computers normally used by gamers have high-performance video cards slotted into the expansion slots.
2.4.1 Name the expansion slot provided for a video card. (1)
2.4.2 Explain why most modern laptop computers have a built-in (or integrated) video adaptor as well as a video card. (2)
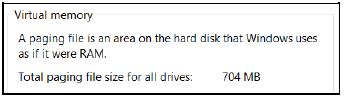
2.5 The performance of a computer used for gaming is important. When opening the performance window, the following is displayed:
2.5.1 When will the operating system use virtual memory? (1)
2.5.2 Does the availability of virtual memory mean that adding more RAM to the computer system to improve the performance is no longer necessary? Motivate your answer. (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
Players who registered for the online gaming event can use any device and can play from any location worldwide. Below is a representation of the different ways communication could take place while playing the games.
3.1 Gamers at the school will link their desktop and laptop computers into a LAN that will be set up in the school hall.
3.1.1 Give TWO reasons why UTP cables will be the most suitable type of cable to connect the computers in the school hall. (2)
3.1.2 Explain why the school LAN would require both a router and a switch by referring to the function of each device. (3)
3.1.3 Explain the purpose of TCP/IP in a LAN setup. (2)
3.2 Different types of communication will take place using different types of media during the gaming event.
3.2.1 What type of network would use a 3G modem? (1)
3.2.2 One of the media types used for wireless communication in networks is radio waves. Name TWO other types of wireless media used in networks. (2)
3.3 Gamers will be required to locate at least one Pokémon at some stage during the gaming event. To take part in the Pokémon GO location-based augmented reality game, a mobile device with GPS technology is required.
3.3.1 What does the abbreviation GPS stand for? (1)
3.3.2 Briefly explain how a GPS can determine your physical position. (2)
3.4 Online media stores, like iTunes and Amazon, that provide the facility of media repositories, will be used to play music in the school hall during the event.
3.4.1 Explain what a media repository is in this context. (2)
3.4.2 Why is it acceptable to use this type of repository for music files, but not for video files? (2)
3.5 The IT learners have been tasked to investigate RIA as a possible feedback mechanism to evaluate the success of the event.
3.5.1 Briefly describe what an RIA is. (2)
3.5.2 Give ONE example of a well-known RIA. (1)
TOTAL SECTION C: 20
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A database will be used to store the details of the participants and to keep a record of the games played.
The following tables have been designed for the database:
tblPlayers | ||
Key | FieldName | DataType |
PlayerID | Text | |
PName | Text | |
PSurname | Text | |
tblGames | ||
Key | FieldName | DataType |
GameID | Text | |
GameTitle | Text | |
GameMaker | Text | |
tblGamesPlayed | |||
Key | FieldName | DataType | Description |
GameNumber | Number | A unique number allocated for each game played in sequence starting from 1 | |
GameID | Text | The ID of the game that was played | |
PlayerID | Text | The ID of the player who played the game | |
TimePlayed | Date/Time | The starting time of the game | |
Score | Number | The score the player obtained for the game | |
Example of data from the tblPlayers table:
PlayerID | PName | PSurname |
X782 | Yeng | Xu |
D901 | Marilyn | Fredriks |
F566 | Loyiso | Nkosi |
G639 | Lenny | Govender |
Example of data from the tblGames table:
GameID | GameTitle | GameMaker |
G101 | Arche Adventure | Lee Andrew |
G102 | 3D Electro Sim | Kernal Yen |
G103 | Car frenzy | Ney Abramo |
G104 | Shadow Impact | Jian Shume |
Example of data from the tblGamesPlayed table:
GameNumber | GameID | PlayerID | TimePlayed | Score |
1 | G102 | D901 | 09:45 | 156 |
2 | G104 | X782 | 10:06 | 567 |
3 | G102 | F566 | 12:57 | 233 |
4 | G103 | X782 | 13:23 | 134 |
4.1
4.1.1 What is the term given to the GameID field in the tblGamesPlayed table? (1)
4.1.2 How many games will each player be able to play per day based on the construction of the database? Choose the answer from the options (A–C) provided below.
- One game per day
- Two games per day
- Any number of games per day (1)
4.1.3 The following message is displayed when attempting to delete the player with PlayerID F566 from the tblPlayers table: ![]()
- Explain why this message is displayed. (2)
- State a possible solution to delete a record from the tblPlayers table successfully. (2)
4.2 Write SQL statements for EACH of the following queries, using the tables provided:
4.2.1 Display all details of the games played from 12:00 to 15:00. (4)
4.2.2 The scores for games with GameID G103 were processed incorrectly. All scores for records with this GameID must be increased by 15%. (4)
4.3 The following SQL statements were given to the administrator to interpret:
4.3.1 Explain what will be the output of the following SQL statement:
SELECT GameID, MAX(Score) as Maximum
FROM tblGamesPlayed
Group by GameID
Order by Max(Score) DESC (3)
4.3.2 Write down the output of the SQL statement given below, using the tblPlayers table and the first record from tblGamesPlayed table.
SELECT GameNumber, Left(PName,1) & Left(PSurname,1) & Right(PSurname,1) & "-" & Score AS Reference
FROM tblPlayers, tblGamesPlayed
WHERE tblPlayers.PlayerID = tblGamesPlayed.PlayerID (4)
4.4 It has been suggested that an ID number field and a date of birth field should be included in the tblPlayers table. Explain why adding the suggested fields to the tblPlayers table will result in data redundancy. (2)
4.5 The school needs to take measures to ensure that the player and game information stored in the database will not be compromised. State TWO ways of preventing an SQL injection attack on the database by hackers. (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
The IT learners will write application programs to assist with organising the gaming event and processing information.
5.1 The following data structures can be used in the application programs:
- One-dimensional array
- Two-dimensional array
- Variable
- Text file
Which ONE of the data structures above will be the most suitable to use in EACH of the following cases?
NOTE: Each data structure from the list above can be used once only as an answer.
5.1.1 A large amount of data about the participants needs to be saved to be used at a later stage. (1)
5.1.2 An alphabetically-sorted list of names of the organisers is required. (1)
5.1.3 The scores of participants need to be stored in rows and columns. (1)
5.1.4 Find the name of the player who achieved the highest score. (1)
5.2 Two object classes need to be designed: one for the players and one for the games.
5.2.1 Object-orientated programming uses encapsulation. Give the definition of encapsulation. (2)
5.2.2 State TWO advantages of using object-orientated programming when multiple developers are involved in coding an application. (2)
5.2.3 Indicate whether the following statements about object-orientated programming are TRUE or FALSE. Write down only 'true' or 'false' next to the question number (5.2.3(a) and 5.2.3(b)).
- More than one object of a class can be instantiated. (1)
- The number of parameters received by a constructor must always be the same as the number of private attributes. (1)
5.3 In one of the games played, the user needs to enter the number of rows of a figure. The figure is made up of a sequential list of numbers starting from the value of 1 and must contain the number of rows that was entered. Each row in the figure will have 2 x (row number) – 1 number of numbers.
Example of output if the value of 5 has been entered. 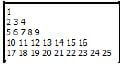
Write a solution to the problem in the form of pseudocode.
NOTE:
- The number of numbers per row can be calculated using the formula 2 x (row number) – 1.
- There is one number in row 1, three numbers in row 2, five numbers in row 3 and so on. (10)
5.4 Another part of the game requires that a random number in the range of 4 to 50 be generated. Determine whether the number generated randomly is a perfect number, or not.
NOTE: A perfect number is when the number is equal to the sum of the factors of the number, excluding the number itself.
Example:
The number 6 was randomly generated.
The sum of the factors of 6, excluding 6, is: 1 + 2 + 3 = 6
The number 6 is therefore a perfect number.
The following pseudocode was given to solve the problem:
| Row Instruction |
|
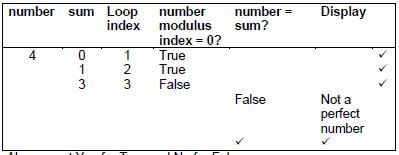
5.4.1 Use the following headings and complete the trace table with the number 4 as the randomly generated number. Show EACH step of your trace.
number | sum | Loop index | number modulus index = 0? | number = sum? | Display |
| 4 |
(5)
5.4.2 One of the players presented an alternative solution. The suggestion is that line 3 of the solution should read as follows:
3. Loop index from 1 to num
In order to display the same results as in QUESTION 5.4.1, one other line in the pseudocode would need to be changed as well.
Indicate the line number and the edited contents of this line to provide the same output as the given solution. (2)
TOTAL SECTION E: 27
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The school will host a website and be a part of a social network to allow for players to register and to play games online. |
6.1 One of the players sent an e-mail with the following e-mail address to the organisers:
This email address is being protected from spambots. You need JavaScript enabled to view it.
6.1.1 State the domain name of the e-mail. (1)
6.1.2 Name the e-mail recipients below that will not be disclosed in the e-mail to others. 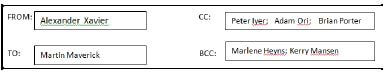 (1)
(1)
6.1.3 What is the general name of malware that refers to the forging of an e-mail header, so that the e-mail appears to originate from a different source? (1)
6.2 The host school has a website with SSL where participants can register and make the required payments.
6.2.1 Explain what SSL is. (2)
6.2.2 A digital certificate will be accessible to the browser to verify the website from which the school wants to download the game. State TWO pieces of information that can be found on a digital certificate. (2)
6.3 The games administrator wants to archive certain files on the server to free up disk space.
6.3.1 Explain what is meant by archiving files. (2)
6.3.2 Will more disk space be saved if archived files are moved from a physical server to a virtual server? Motivate your answer. (2)
6.4 At a previous gaming event gamers complained that too much bandwidth was used while streaming games.
6.4.1 For the current gaming event gamers were informed that they can configure the settings on their computers to optimise game play. Explain what can be done to save bandwidth while streaming. (1)
6.4.2 The gamers want to restrict the websites that can be accessed in order to reduce network traffic. Explain how a firewall could be used for this purpose. (2)
6.4.3 Why is it usually quicker to use BitTorrent protocol to download a file rather than downloading the file directly from a server? (2)
6.4.4 Someone mentioned that BitTorrent protocol should be avoided as it is illegal to use. Is this statement true? Motivate your answer. (2)
6.5 The IT learners will make gamers aware of the NFC (near field communication) feature that is available on their tablets and other hand-held devices. 
6.5.1 Explain what near field communication (NFC) means. (2)
6.5.2 NFC originated from a communication standard that uses radio waves. What is this communication standard called? (1)
6.6 Separate versions of some of the gaming software applications have been developed to provide for different operating systems, such as Android and IOS.
6.6.1 Motivate why the same application needs to be programmed differently for different operating systems. (2)
6.6.2 An important feature of an operating system is backward compatibility. Use an example to explain the concept of backward compatibility. (2)
6.7 During an interview with the author of one of the games, the response to a question on the features of a successful online game was as follows:
'Scalability, fast response time, security and low cost to set up'
6.7.1 Why is scalability important when designing online games? (2)
6.7.2 Why will security be a challenge for a peer-to-peer network? (1)
6.8 'The "app-ification" of the Web' has seen many well-known websites developing apps that people can use to access the information on their websites.
6.8.1 Briefly explain what an app is. (1)
6.8.2 Give TWO reasons why gamers wanting to register for the gaming event might prefer to use an app instead of the website. (2)
6.9 One of the gamers will use the headset in the illustration below. 
[Source: http://www.bestbuy.com/site/ video-games-accessories/gaming-headset]
6.9.1 Many of these types of devices contain firmware. Explain what firmware is. (2)
6.9.2
- The headset supports plug-ins. Explain what a plug-in is. (1)
- How does the fact that the headset supports plug-ins benefit the gamer? (1)
6.9.3 These types of devices normally contain sensors. Name TWO possible types of sensors found on gaming devices. (2)
6.9.4 What is the field called when a computer system simulates human decision-making and reacts on the basis of input gained from sensors? (1)
TOTAL SECTION F: 38
GRAND TOTAL: 150
INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
INFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
MEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 D ✔ (1)
1.1.2 B ✔ (1)
1.1.3 C ✔ (1)
1.1.4 A ✔ (1)
1.1.5 C ✔ (1)
1.1.6 B ✔ (1)
1.1.7 B ✔ (1)
1.1.8 A ✔ (1)
1.1.9 D ✔ (1)
1.1.10 D ✔ (1)
1.2
1.2.1 Creative Commons License ✔
1.2.2 World Wide Web consortium (W3C) ✔ (1)
1.2.3 Click farms ✔ (1)
1.2.4 Overclocking ✔ (1)
1.2.5 Robotics ✔ (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1
2.1.1 Threads are part of the same program ✔ that runs simultaneously and independently. ✔ (2)
2.1.2 Process management is the task of making sure that each process gets enough CPU time and access to memory, storage and other hardware so that it can work without interfering with, or being interfered with, by other processes.
Concepts:
- Access to CPU, memory, storage ✔
- No interference with other processes ✔ (2)
2.1.3 No ✔
- Each core can process one task at a speed of 1.58 GHz ✔ (2)
2.1.4
- Cache memory is special high speed memory ✔ close to or on the CPU ✔ (2)
- To prevent a slower medium ✔ from slowing down the performance ✔ of a faster medium
OR
The speed of the CPU is higher than most motherboards and RAM. So extensive use is made of cache to keep the CPU running at optimum capacity. (2)
2.2
2.2.1 Solid state drive ✔ (1)
2.2.2
- There is no physical moving parts when writing or reading on an SSD ✔ (1)
- There is no time spent to move to the position where file is saved/can access it immediately. ✔ (1)
2.2.3 Set up the SSD as the system/primary drive on which the operating system ✔is installed for faster boot up and system performance. ✔
Set up the HDD as a secondary drive ✔ which contains all your music/video files. ✔ (4)
2.3 Any TWO ✔✔
- To ensure that the latest viruses will not attack the system
- New features of the virus are added
- Update the virus database (2)
2.4
2.4.1 PCI-E expansion slot on the motherboard ✔ (1)
2.4.2 The built-in video card is used when doing routine tasks ✔ because it uses much less power and battery life
The video adapter will be used when programs require high resolution/good graphics✔ (2)
2.5
2.5.1 Any ONE ✔
- Too many applications open
- Programs too large to run from available RAM (1)
2.5.2 No, ✔
- access to virtual memory is slower than access to RAM ✔ (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1
3.1.1 Any TWO ✔✔
- Short distance
- Cheap
- Easy to install (2)
3.1.2
- A router makes communication possible between different networks/Allows access to the Internet. ✔
- A switch makes communication possible between devices on a network ✔
- School needs both router and switch since there may be gamers who will participant online from outside the school's network. ✔ (3)
3.1.3
- TCP/IP is primarily used for a point-to-point set up, meaning it allows for communication from one point (server) ✔ in the network to another point (client). ✔ (2)
3.2
3.2.1 A cellular network ✔
Also accept: WAN and 4G (1)
3.2.2 Any TWO ✔✔
- Microwaves
- Light
Also accept Electro-magnetic waves (2)
3.3
3.3.1 Global positioning system ✔ (1)
3.3.2 The GPS will receive signals sent by at least three satellites ✔and triangulate the position ✔using trilateration. (2)
3.4
3.4.1 It is storage space in the cloud ✔ to which you are given access once you purchased the media. ✔ (2)
3.4.2 High bandwidth ✔and a lot of data are required to watch movies online ✔ (2)
3.5
3.5.1 A Rich Internet Application is a web application ✔ that is designed to deliver the functions and features of a traditional desktop application. ✔ (2)
3.5.2 Any ONE ✔
- Google Docs
- Microsoft Office Live (1) TOTAL SECTION C: 20
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1
4.1.1 Foreign key ✔ (1)
4.1.2 Answer C – any number of games per day ✔ (1)
4.1.3
- There is a relationship between tblPlayers table and tblGamesPlayed table. ✔ The PlayerID F566 is contained in the tblGamesPlayed table and therefore cannot be deleted from the table where it is a primary key. ✔ (2)
- All records containing PlayerID F566 must first be deleted from tblGamesPlayed table ✔ and then only can this record be deleted from tblPlayers table. ✔ (2)
4.2
4.2.1 SELECT * FROM tblGames WHERE TimePlayed >= #12:00# AND TimePlayed <= #15:00#
- ✔ SELECT *
- ✔ FROM tblGames
- ✔ WHERE TimePlayed >= #12:00#
- ✔ AND TimePlayed <= #15:00# (4)
4.2.2 UPDATE tblGamesPlayed SET Score = Score * 1.15 WHERE GameID = "G103"
- ✔ UPDATE tblGamesPlayed
- ✔ SET Score
- ✔ = Score * 1.15
- ✔ WHERE GameID = "G103" (4)
4.3
4.3.1 The highest score ✔ achieved for each game ✔ sorted from highest to lowest according to the score ✔ (3)
4.3.2
- 1 ✔
- MF ✔
- s- ✔
- 156 ✔ (4)
4.4 We only need the IDNumber field since the date of birth can be derived ✔ from the first six digits of the IDNumber field. ✔ (2)
4.5 Any TWO ✔✔
- Validate data fields.
- Avoid entering SQL statements into data fields.
- Restrict access to the database.
- Avoid disclosing database error information. (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Text file ✔ (1)
5.1.2 One-dimensional array ✔ (1)
5.1.3 Two-dimensional array ✔ (1)
5.1.4 Variable ✔ (1)
5.2
5.2.1 Restricting access to a class's attributes ✔ by declaring the attributes as private ✔ (2)
5.2.2 Any TWO ✔✔
- Developers can work on separate modules of the software independently/save time/get the project done faster
- Code can be written once and re-used
- Code can be debugged easily/Less code to work through with debugging. (2)
5.2.3
- TRUE ✔ (1)
- FALSE ✔ (1)
5.3
Counter ? 1 ✔
NumberOfRows? input from keyboard ✔ Any order
Loop K from 1 to NumberOfRows ✔
RowLine ? "" ✔
Loop L from 1 ✔ to 2 * K – 1 ✔
RowLine ? RowLine ✔+ Counter + " " ✔ Must be in this order
Increment (Counter) ✔
Display RowLine ✔ (10)
 5.4
5.4
5.4.1 (5)
Also accept Yes for True and No for False
5.4.2 Line 6: ✔ If number = sum – number ✔ (2)
TOTAL SECTION E: 27
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 windermere.co.za ✔ (1)
6.1.2 Marlene Heyns and Kerry Mansen ✔ (1)
6.1.3 Spoofing ✔ (1)
6.2
6.2.1 Secure Sockets Layer is an encryption protocol ✔ for managing the transmission of sensitive data over the Internet. ✔ (2)
6.2.2 Any TWO ✔✔
- Identification information of the user
- Identification details of the website used
- The validity period of the digital certificate
- Serial number of digital certificate
- Digital signature of issuer
- Name of issuer
- Owners of public key (2)
6.3
6.3.1 Files are compressed on the same disk ✔ and the original file is deleted thereby creating space. ✔
OR
Old/unused files are usually moved to a secondary storage device (other computer/hard drive dedicated for this purpose
Concepts:
- Compressed/moved to secondary storage
- Original files deleted (2)
6.3.2 No, ✔
- a virtual server will not save space as it uses the resources of the existing machine ✔
OR
Yes, If the cloud is used as a server.
NOTE:
The first mark is only awarded if the justification is correct. (2)
6.4
6.4.1 Any ONE ✔
- Turn down the quality settings to a lower setting.
- Adjust the operating systems built-in content distribution network used for streaming large files. (1)
6.4.2 A firewall could be configured to allow specific/authorised ✔ incoming/outgoing traffic. ✔
Also accept
- A firewall could be configured to block specific/unauthorised incoming/outgoing traffic. (2)
6.4.3 With BitTorrent parts of the file ✔are downloaded from multiple clients. ✔ (2)
6.4.4 No, BitTorrent itself is merely a file sharing protocol ✔ and is not illegal to use however the user must guard against downloading illegal software. ✔ (2)
6.5
6.5.1 NFC is a set of communication standards which allow peer-to-peer data exchanges ✔ between two closely held end points. ✔ (2)
6.5.2 RFID (Radio Frequency Identification) ✔ (1)
6.6
6.6.1 Each Operating system uses different architectures✔ and has different ways of interfacing with software ✔so a different 'version' has to be written for each OS platform. (2)
6.6.2 An example would be if a game was installed using Windows 7 ✔ it must still work if the operating system was updated to Windows 8 or Windows 10. ✔ (2)
6.7
6.7.1 The ability of the server to access more resources when required ✔ and to decrease the use when no longer required so that the game does not hang/stop when many users ✔ are playing.
Concepts:
- Adapt to requirements
- Continuous changes (2)
6.7.2 The data does not pass through any central point. ✔ (1)
6.8
6.8.1 Apps are programs designed to run on mobile devices. ✔ (1)
6.8.2 Any TWO ✔✔
- Dedicated access/immediate access/faster access.
- Can register from anywhere using a mobile device.
- Allows users to receive automatic notification as soon as the registration has been done/immediate notification. (2)
6.9
6.9.1 Software ✔ that is permanently installed ✔ on a ROM chip. (2)
6.9.2
- A plug in is software that adds a specific feature/functionality ✔ to an existing software. (1)
- If this device supports plug-ins, a program from the web can be used to play embedded audio and video files without the need for a dedicated media player. ✔ (1)
6.9.3 Any TWO ✔✔
- Movement
- Sound
- Light (2)
6.9.4 Artificial Intelligence ✔ (1)
TOTAL SECTION F: 38
GRAND TOTAL: 150
INFORMATION TECHNOLOGY PAPER 1 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
INFORMATION TECHNOLOGY
PAPER 1
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
GENERAL INFORMATION:
- These marking guidelines are to be used as the basis for the marking session.
- They were prepared for use by markers.
- All markers are required to attend a rigorous standardisation meeting to ensure that the guidelines are consistently interpreted and applied in the marking of candidates' work.
- Note that learners who provide an alternate correct solution to that given as example of a solution in the marking guidelines will be given full credit for the relevant solution, unless the specific instructions in the paper were not followed or the requirements of the question were not met.
- Annexures A, B and C (pages 3–9) include the marking grid for each question for using either one of the two programming languages.
- Annexures D, E and F (pages 10–17) contain examples of solutions for Java for QUESTION 1 to QUESTION 3 in programming code.
- Annexures G, H and I (pages 18–29) contain examples of solutions for Delphi for QUESTION 1 to QUESTION 3 in programming code.
- Copies of Annexures A, B and C (pages 3-9) should be made for each learner and completed during the marking session.
MEMORANDUM
ANNEXURE A:
SECTION A:
QUESTION 1: MARKING GRID- GENERAL PROGRAMMING SKILLS
CENTRE NUMBER: | EXAMINATION NUMBER: | |||
QUESTION | DESCRIPTION | MAX. MARKS | LEARNER'S MARKS | |
A learner must be penalised only once if the same error is repeated. | ||||
1.1 | Button - [Question 1_1] Extract name and surname from textbox✔ Extract ID number✔ If nameSurname string includes a space✔ AND ID number is not empty✔ AND ID number has 13 digits ✔ | 14 | ||
1.2 | Buttons with Icons showing type of Loyalty card | 6 | ||
1.3 | Button - [Question 1_3] | 15 | LEARNER'S MARKS |
1.4 | Button - [Question 1_4] Part 2: Part 1 ✔ | 13 | |
TOTAL: | 48 |
ANNEXURE B:
SECTION B
QUESTION 2: MARKING GRID - OBJECT-ORIENTED PROGRAMMING
CENTRE NUMBER: | EXAMINATION NUMBER: | |||
QUESTION | DESCRIPTION | MAX. MARKS | LEARNER'S MARKS | |
2.1.1 | Constructor: | 5 | ||
2.1.2 | Mutator method: | 2 | ||
2.1.3 | increaseLoyaltyPoints method: | 5 | ||
2.1.4 | updateHealthLevel method: | 7 | ||
2.1.5 | isCorrect method: (Method definition provided) Loop through the digits in the ID number ✔ remove the 0 digits ✔ from the string Initialise variable for sum✔ If even number of digits left in string ✔ Loop correct number of times ✔ Add values with 2 digits to sum variable from left hand side of string ✔ If odd number of digits left in string ✔ Add first left hand side digit from string as a one digit value to sum✔ Loop correct number of times ✔ Add two-digits values to sum variable ✔ If sum is equal to access code parameter ✔ return true✔ else return false✔ | 13 | LEARNER'S MARKS |
2.1.6 | identifyStarShopper method: Empty string variable - if not Star shopper ✔ If (loyalty points > 2000✔ AND number of visits > 10)✔ OR✔ (healthLevel is 'P') ✔ Set variable to string 'STAR shopper'✔ Return string variable | 6 |
QUESTION 2: MARKING GRID – continued
2.2.1 | Button – [2.2.1 – Check access code] Extract the card number from the combo box✔ Extract cellphone number from label ✔ Extract access code from text box ✔ Extract loyalty points from label and convert to integer✔ Instantiate object ✔ sending correct arguments in correct order✔ (6) If access code is correct Test if access code is correct ✔ using isCorrect method ✔ Read text file and process data {Delphi: AssignFile, Reset and CloseFile Java: Create object to read from file} ✔ Initialise variables for counters and sum ✔ Loop through file ✔ Read card number ✔ Read total amount spent and convert to double data type ✔ Read health amount spent and convert to double ✔ Test if it is correct card number ✔ Add total amount to sumTotal ✔ Add health amount to sumHealth ✔ Increment counter ✔ Call setVisits method ✔ Call increaseLoyaltyPoints method – send sumTotal as argument ✔ Call updateHealthLevel method – send sumTotal and sumHealth as arguments ✔ end loop Enable button for Q2.2.2 ✔ If access code is NOT correct Display message indicating that access code was incorrect ✔ Clear the access code text box ✔ (18) | 24 | LEARNER'S MARKS |
2.2.2 | Button – [2.2.2 - Display card holder details] Display object details using toString ✔ in the output area ✔ Display shopper status using identifyStarShopper method ✔ | 3 | |
TOTAL: | 65 |
ANNEXURE C:
SECTION C
QUESTION 3: MARKING GRID – PROBLEM SOLVING
CENTRE NUMBER: | EXAMINATION NUMBER: | |||
QUESTION | DESCRIPTION | MAX. MARKS | LEARNER'S MARKS | |
3.1 | Button [3.1 – Display layout] Outer loop for rows ✔ Inner loop for columns ✔ Display symbol from two dimensional array ✔ In row ✔ and in column ✔ | 5 | ||
3.2 | Combo box – Select Restaurants Extract shop as character from combo box ✔ Initialise variables for position (row and column ✔) Loop through the rows ✔ If the shop is within characters A-E (to the left)✔ Set col for shop to 0 (first column) ✔ Set col for friend to 1 (second column) ✔ If the shop is within characters F-J (to the right) ✔ Set col for shop to last col of arrMall ✔ Set col for friend to one less than col for shop ✔ Test if character at current position in array ✔ equals selected shop's character ✔ Replace X with # ✔ Update display ✔ End loop | 13 | ||
3.3 | Button [3.3 - Locate nearest friend(s)] Initialise nearest distance to a large value✔ Outer loop for rows ✔ Inner loop for columns/if for right hand side ✔ If character at position is # ✔ Determine difference in row positions ✔ as positive value ✔ Determine difference in column positions✔ as positive value ✔ Calculate newDistance ✔ If friend is in A-E or display shop name ✔ If friend is in F-J ✔ display shop name ✔ If newDistance < = nearest distance ✔ Add shop name to output message ✔ Replace nearest with newDistance ✔ Displayshop name ✔ and distance * 4.5 ✔ Display output message indicating nearest friends ✔ | 19 | ||
TOTAL: | 37 | |||
SUMMARY OF LEARNER'S MARKS:
CENTRE NUMBER: | EXAMINATION NUMBER: | |||
SECTION A | SECTION B | SECTION C | ||
QUESTION 1 | QUESTION 2 | QUESTION 3 | GRAND TOTAL | |
MAX. MARKS | 48 | 65 | 37 | 150 |
LEARNER'S MARKS | ||||


HOSPITALITY STUDIES GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
HOSPITALITY STUDIES
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of FOUR sections.
SECTION A: Short questions (all topics) (40)
SECTION B: Kitchen and restaurant operations; Hygiene, safety and security (20)
SECTION C: Nutrition and menu planning; Food commodities (80)
SECTION D: Sectors and careers; Food and beverage service (60) - Answer ALL the questions in the ANSWER BOOK.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1
1.1 MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.10), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
EXAMPLE:
1.1.11 A good source of vitamin C is …
- milk.
- meat.
- bread.
- oranges.
1.1.11 ![]()
1.1.1 E-mails, websites and cellphones used to market products are … marketing tools.
- audio
- visual
- electronic
- audio-visual (1)
1.1.2 A grape variety used to make wine:
- Cultivar
- Vintage
- Product
- Origin (1)
1.1.3 An enzyme in raw pineapple that prevents a gelatin mixture from setting:
- Ficin
- Bromelain (Bromelin)
- Papain
- Casein (1)
1.1.4 A pizza provides eight portions. The total cost of the pizza is R72,00. The cost of ONE portion is …
- R9,00.
- R12,00.
- R36,00.
- R80,00. (1)
1.1.5 When a person suffers from diabetes, it means that the body does not produce enough …
- cholesterol.
- calories.
- lactose.
- insulin. (1)
1.1.6 A flavouring used in the preparation of desserts, which is made from cocoa beans:
- Vanilla
- Coffee
- Chocolate
- Caramel (1)
1.1.7 The difference between the actual cost to produce an item and the money that it is sold for:
- Gross profit
- Indirect cost
- Direct cost
- Net profit (1)
1.1.8 A method where meat is covered with thin slices of fat:
- Larding
- Marinating
- Tenderising
- Barding (1)
1.1.9 … includes activities that ensure that prospective guests are aware of the types of accommodation available at an establishment.
- Pricing
- Marketing
- Financing
- Targeting (1)
1.1.10 Choux pastry filled with cream and stacked together with caramel is called …
- croquembouche.
- churros.
- profiteroles.
- beignets. (1)
1.2 MATCHING ITEMS
Choose the description from COLUMN B that matches the terminology in COLUMN A. Write only the letter (A–I) next to the question number (1.2.1–1.2.6) in the ANSWER BOOK, for example 1.2.7 J.
COLUMN A TERMINOLOGY | COLUMN B DESCRIPTION |
1.2.1 Dusting |
(6 x 1) (6) |
1.3 ONE-WORD ITEMS
Give ONE term/word for each of the following descriptions. Write only the term/word next to the question number (1.3.1–1.3.10) in the ANSWER BOOK.
1.3.1 Wine of which the alcohol has been removed before it is bottled
1.3.2 A sweet wine that is served after a meal
1.3.3 The Act that regulates the sale of alcohol
1.3.4 The term that refers to pastry shells that are pre-baked with rice or dried beans
1.3.5 Advertising a product by phoning potential customers
1.3.6 Fat distributed between the muscle fibres of a meat cut
1.3.7 A traditional sauce served with roast beef
1.3.8 Rice rolled with cooked seafood or raw fish, wrapped in seaweed sheets
1.3.9 A mixture of chopped fruit or vegetables, flavoured with spices, sugar and vinegar and cooked to a thick pulp
1.3.10 Legumes used to make textured vegetable proteins (10)
1.4 SELECTION
1.4.1 Identify TWO items that are included in overheads:
- Stationery
- Salaries
- Staff training
- Cleaning materials (2)
1.4.2 Identify TWO steaks cut from the fillet:
- Rump
- Tournedo
- Medallion
- T-bone (2)
1.5 MATCHING ITEMS
Choose a description from COLUMN B that matches a dessert in COLUMN A and then match it with an example in COLUMN C. Write only the letter (A–G) and number (i–vii) next to the question number (1.5.1–1.5.5) in the ANSWER BOOK, for example 1.5.6 H (viii).
COLUMN A | COLUMN B | COLUMN C |
1.5.1 Starch-based milk dessert | A fruit dipped in a batter and shallow fried | (i) vacherin |
1.5.2 Baked custard | B several layers of ice cream moulded in a dome shape | (ii) bavarois |
1.5.3 Frozen dessert | C starch boiled with milk, placed in a pie dish, dotted with butter and baked in the oven | (iii) crème brulée |
1.5.4 Meringue | D rich egg custard topped with a crust of caramelised sugar and served in the mould | (iv) bombe |
1.5.5 Moulded cold custard | E whisked egg white added to a confectioner's custard base and baked in a bain-marie | (v) sago pudding |
F whisked egg white and sugar baked into a hard basket shape to hold whipped cream | (vi) crème pâtissiére | |
G custard base with gelatin and whipped cream, poured into a mould and chilled to set | (vii) malva pudding (5 x 2) (10) |
TOTAL SECTION A: 40
SECTION B: KITCHEN AND RESTAURANT OPERATIONS;
HYGIENE, SAFETY AND SECURITY
QUESTION 2
2.1 Study the statement below and answer the questions that follow.
Gastro-enteritis and TB are two of the reasons for the high rate of absenteeism in the food and beverage industry in South Africa. |
2.1.1 What is the incubation period for gastro-enteritis? (1)
2.1.2 Explain how a food handler may prevent gastro-enteritis from affecting others in the workplace. (5)
2.1.3 State THREE symptoms of each of the following:
- Gastro-enteritis (3)
- TB (3)
2.2 Study the statement below and answer the questions that follow.
Good service differs from one restaurant to the next. |
2.2.1 Define the term good service. (2)
2.2.2 Critically discuss the statement above. (3)
2.3 A restaurant manager considers buying the system below. Study the photograph and answer the questions that follow.
2.3.1 Identify the type of system. (1)
2.3.2 Explain TWO benefits of the system above. (2)
TOTAL SECTION B: 20
SECTION C: NUTRITION AND MENU PLANNING;
FOOD COMMODITIES
QUESTION 3
3.1 Read the extract below and answer the questions that follow.
A variety of fresh and preserved cherry products are displayed at the annual Cherry Festival in Ficksburg. |
3.1.1 Name TWO methods that can be used to preserve excess cherries other than bottling. (2) |
3.1.2 Discuss step by step how you would prepare bottled cherries. (4)
The following information about a dinner held for 100 guests at the Cherry Festival was given to the organisers: Selling price of the menu: R10 000 |
3.2
3.2.1 Calculate the total net profit. (3)
3.2.2 Calculate the cost for each guest. (3)
3.2.3 Suggest FOUR important aspects that the organisers of the dinner should include on their quotation. (4)
3.3 Study the method of preparing choux pastry below and answer the questions that follow.
Method:
|
3.3.1 Give reasons for the following steps:
- Step 4 (1)
- Step 7 (2)
3.3.2 Suggest TWO toppings that may be used as decoration for the choux pastry. (2)
3.3.3 Predict the end result if the water had been boiled for too long during the preparation of the choux pastry. (2)
3.4 Differentiate between a pollo-vegetarian and a pesco-vegetarian. (4)
3.5 Give reasons for EACH of the following statements:
3.5.1 White and red speckled beans should be cooked separately. (1)
3.5.2 Do not boil dried beans without soaking. (1)
3.6 Read the extract below and answer the questions that follow.
You are planning a cocktail function for your parents' anniversary. The function will last for two hours. |
3.6.1 Determine the number of snacks to be served per person. (1)
3.6.2 Describe FOUR guidelines to follow when preparing the cocktail snacks. (4)
3.6.3 Evaluate the suitability of serving sticky ribs at the cocktail function. (3)
3.6.4 Recommend THREE sweet bite-size cocktail snacks that you may include on the menu. (3)
[40]
QUESTION 4
4.1 Study the photograph of stewed lamb shanks below and answer the questions that follow.
4.1.1 Distinguish between the characteristics of raw lamb and raw beef. (4)
4.1.2 Explain why stewing is a suitable cooking method to prepare the lamb shanks. (2)
4.1.3 Suggest a suitable accompaniment for the stewed lamb shanks. (1)
4.2 Read the extract below and answer the questions that follow.
The Savera Hotel has a kosher kitchen. The hotel has been requested to host a banquet for 100 Jewish guests. |
4.2.1 Define the term banquet. (2)
4.2.2 Name TWO departments that would be required to plan and prepare for the banquet. (2)
4.2.3 Discuss THREE requirements to consider when planning the banquet menu for the Jewish guests. (3)
4.2.4 Determine the number of waiters you will need for the function. (1)
4.3 Study the photograph of a vol-au-vent below and answer the questions that follow.
4.3.1 Identify the pastry used to make the vol-au-vent. (1)
4.3.2 State the functions of the following ingredients in the preparation of the pastry above:
- Butter (2)
- Water (2)
4.3.3 Suggest TWO savoury fillings that may be used in the vol-au-vent. (2)
4.3.4 What are the characteristics of a successful vol-au-vent? (3)
4.4
4.4.1 Name TWO types of gelatin. (2)
4.4.2 Predict the results of the following when preparing a gelatin dish:
- Adding too much sugar (1)
- Adding lemon juice (1)
- Setting the dish at 20 °C (1)
4.5 Study the photograph of the Christmas pudding below and answer the questions that follow.
4.5.1 Describe the technique for cooking the dessert above. (2)
4.5.2 Explain how the dessert above may be presented. (2)
4.5.3 Recommend TWO suitable sauces for this dessert. (2)
4.6 Good nutrition is vitally important for HIV positive people. Justify the statement above. (4)
[40]
TOTAL SECTION C: 80
SECTION D: SECTORS AND CAREERS;
FOOD AND BEVERAGE SERVICE
QUESTION 5
5.1 Study the advertisement below and answer the questions that follow. 
5.1.1 Name THREE aspects that will determine the target market for the Springbok Game Lodge. (3)
5.1.2 Determine whether promotion was used as a marketing strategy and give a reason for the answer. (2)
5.1.3 Name ONE disadvantage of using promotion as part of your marketing mix. (1)
5.1.4 Describe TWO requirements of the packaging of the snacks. (2)
5.1.5 Identify FOUR aspects that the Springbok Game Lodge could have included in their business description. (4)
5.1.6 Explain how the Springbok Game Lodge may contribute to job creation and give TWO examples. (4)
5.2
5.2.1 Classify the terms below into revenue and non-revenue-generating areas in the hospitality industry.
finance; bars; security; food and beverage; maintenance; guest rooms |
Tabulate your answer as follows:
REVENUE-GENERATING AREAS | NON-REVENUE GENERATING AREAS |
(6)
5.2.2 Explain the interrelationship between sales and marketing and the finance department. (2)
5.2.3 Identify THREE duties of the security staff. (3)
5.2.4 Name THREE entrepreneurial opportunities that may be found in the beverage sector. (3)
[30]
QUESTION 6
6.1 Study the photographs below and answer the questions that follow.
 |  |
| A | B |
| TABLE CLOTH | RED WINE GLASS |
6.1.1 Define the term opening mise-en-place. (2)
6.1.2 Identify the opening mise-en-place that should be checked for the table cloth in A. (3)
6.1.3 Explain the procedure that should be followed when cleaning the glass in B. (3)
6.1.4 Determine the suitability of serving a glass of Chardonnay with a fish starter. (2)
6.1.5 Discuss the correct position of the glass above on a cover. (3)
6.1.6 Explain how red wine bottles should be stored. (4)
6.2
6.2.1 Differentiate between on-consumption and off-consumption liquor licenses. Tabulate your answer as follows:
ON-CONSUMPTION | OFF-CONSUMPTION |
(4)
6.2.2 Discuss the procedure that should be followed for plated service. (3)
6.2.3 Motivate the use of plated service for a formal dinner. (3)
6.3 The walk-in refrigerator at a local game lodge reaches 22 °C. Determine the impact of this situation on the game lodge. (3)
[30]
TOTAL SECTION D: 60
GRAND TOTAL: 200
HOSPITALITY STUDIES GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
HOSPITALITY STUDIES
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
MEMORANDUM
SECTION A
QUESTION 1
1.1 MULTIPLE-CHOICE QUESTIONS
1.1.1 | C√ |
1.1.2 | A√ |
1.1.3 | B√ |
1.1.4 | A√ |
1.1.5 | D√ |
1.1.6 | C√ |
1.1.7 | A√ |
1.1.8 | D√ |
1.1.9 | B√ |
1.1.10 | A√ |
(10)
1.2 MATCHING ITEMS
1.2.1 | I√ |
1.2.2 | F√ |
1.2.3 | A√ |
1.2.4 | B√ |
1.2.5 | C√ |
1.2.6 | G√ |
(6)
1.3 ONE-WORD ITEMS
1.3.1 | De-alcoholised√ |
1.3.2 | Hanepoot√/Jeripigo√/Muscadel√ |
1.3.3 | Liquor Act√ |
1.3.4 | Baking blind√ |
1.3.5 | Tele-marketing√ |
1.5.6 | Marbling √ |
1.3.7 | Horseradish/gravy/jus√ |
1.3.8 | Sushi√ |
1.3.9 | Chutney√ |
1.3.10 | Soya√ |
(10)
1.4 SELECTION
1.4.1 | A √D√ |
1.4.2 | B√ C√ |
(4)
1.5. MATCHING ITEMS
1.5.1 | C√ (v) √ |
1.5.2 | D √ (iii) √ |
1.5.3 | B√ (iv) √ |
1.5.4 | F√ (i) √ |
1.5.5 | G√ (ii) √ |
(10)
TOTAL SECTION A: 40
SECTION B: KITCHEN AND RESTAURANT OPERATIONS. HYGIENE, SAFETY AND SECURITY
QUESTION 2
2.1
2.1.1 24–48 hours√ (1)
2.1.2
- Food handlers with gastroenteritis should inform their employer as soon possible√
- Food handlers should not work if they have diarrhoea√
- Food handlers should maintain good personal hygiene√/(wash hands after using the toilet, refuse, after touching your body, your hair, nose etc..)√
- They should wash and sanitise equipment and surfaces after handling raw meat and poultry√
- They need to ensure that food is thoroughly cooked especially chicken, fish and eggs√
- Insects and rodents should be eliminated from the kitchen√ by installing screen on windows√
- The kitchen should comply with proper storage regulations√
- All food should be covered when stored√
- Cooked foods should be separated from raw foods√
- Food should not be stored on the floor√
- Waste should not be left to accumulate√; lids must be kept on the bins at all times. √
(Any 5) (5)
2.1.3
- GASTROENTERITIS
- Diarrhoea√
- Nausea and vomiting√
- Dehydration√
- Stomach ache√
- Headache√
- Fever√
(Any 3) (3)
- TUBERCULOSIS
- Continuous cough√
- Feeling tired all the time√
- Weight loss√
- Loss of appetite√
- Coughing up blood√
- Night sweats√
- Chest pains√
- Shortness of breath√
(Any 3) (3)
2.2
2.2.1 Good service is meeting customers’ needs timely√, by professional people√ in a pleasant environment√/in the way they want and expect them to be met√ (Any 2) (2)
2.2.2
- The management decides on the level of service they would like in their restaurant√. The level of training differs√,
- Service is often linked to the price√ Example: well-trained waiters work in upmarket restaurants where clients are willing to pay for a high level of service√
- The more expensive the dish , the better the service is supposed to be√ (Any 3) (3)
2.3
2.3.1 Point of sale system (POS)√ (1)
2.3.2 The system will assist restaurant employees to complete their daily tasks that include : food and beverage orders,√ communication of tasks to the kitchen√, guest bill settlement√, credit card processing√, and charges posted to guest accounts in the hotel√ (Any 2) (2)
TOTAL SECTION B: 20
SECTION C: NUTRITION:
MENU PLANNING AND FOOD COMMODITIES
QUESTION 3
3.1
3.1.1
- Make jam√
- It can be glazed√
- It can be canned √
- It can be frozen √ (Any 2) (2)
3.1.2
- Wash and remove the pips from the cherries√
- Prepare a sugar syrup√
- Boil the food in the syrup until soft√
- Scoop the cherries into sterilised jars√
- Fill with syrup and seal√ (Any 4) (4)
3.2
3.2.1 Net profit: selling price-total cost (food cost + overhead cost)√
- = R10 000 – (R3500+R2500) √
= R10 000 – R6000√
= R4000,00√ (Any 3) (3)
3.2.2 Cost per person= Selling price/number of people
- =R10 000/100 people√
= R100,00 per person√ (Any 3) (3)
3.2.3
- Name of the company, address, contact details√
- Personal information of the client: name, contact number, address√
- Information regarding the function: date, time, dietary requirement, type of function√
- Additional charges√
- Special requests√
- Payment terms√ (Any 4) (4)
3.3
3.3.1
- Step 4: to prevent the eggs from cooking√/curdling√ (Any 1)
- Step 7:
- to finish the baking process√, to allow for the pastry to dry out√, so the cavity is encased in a delicate, crispy shell√
- To prevent burning√ (Any 2) (3)
3.3.2
- Chocolate√
- Caramel √
- Vanilla/chocolate icing√
- Fondant√
- Spun sugar√
- Sprinkled with icing sugar√ (Any 2) (2)
3.3.3 Too much water will evaporate√ resulting in too little steam√ and the final product will be reduced in volume√ (Any 2) (2)
3.4 (4)
POLLO VEGETARIAN | PESCO VEGETARIAN |
|
|
3.5
3.5.1 White beans will take on the colour of the red speckled beans√ (1)
3.5.2 It takes longer to cook√, and the beans may break or separate from the skins√ (Any 1) (1)
3.6
3.6.1 3-5 cocktail snacks√ (1)
3.6.2
- The snacks must be bite sized√
- Include hot and cold savoury snacks√
- Include two to three sweet snacks√
- They must be visually attractive and colourful√
- They must be tasty and well-seasoned√
- They must include a variety of flavours√
- Ingredients should be easily recognisable√
- Personal and kitchen hygiene is essential√ (Any 4) (4)
3.6.3 Unsuitable√
- The guest will dirty their fingers√, or may need a finger bowl√
- Need a side plate to serve√ (3)
3.6.4
- Fruits dipped in chocolate√
- M7ilk tartlets√
- Chocolate truffles√
- Scones√ (Any relevant answer) (3)
[40]
QUESTION 4
4.1
4.1.1 (4)
BEEF | LAMB |
Colour: bright red to cherry red√ Texture: smooth, fine and firm√ Fat: creamy or yellow colour √ Bones: Whiter and harder√ (Any 2) |
|
4.1.2
- It is a tough cut of meat/contains a lot of connective tissue√
- Stewing is a moist heat cooking method√, converting the white connective tissue to gelatine√, this slow cooking method makes is tender √ (Any 2) (2)
4.1.3
- Mashed potatoes√
- Cous cous√
- Pap√ (Any relevant answer) (1)
4.2
4.2.1 A banquet is a formal meal to which a group of guests will be invited to celebrate an event, to honour special guests or any other type of special occasion√ (2)
4.2.2
- Food and Beverage Service√
- Food preparation√ (2)
4.2.3
- Jews only consume food that is kosher/clean√
- They do not eat the hindquarter of an animal√
- They may not mix meat and dairy products during a meal√
- All shellfish, snails and birds of prey are forbidden√
- Pork and pork products are not permitted√ (Any 3) (3)
4.2.4 8-10 waiters√ (1)
4.3
4.3.1 Puff pastry√ (1)
4.3.2
- Butter: contributes to the rich flavour√, contributes to colour√ (2)
- Water: develops the gluten in the flour√, transforms into steam√ and helps to leaven the pastry√. (Any 2) (2)
4.3.3
- Creamed spinach√
- Chicken and mushroom √
- Steak and kidney√
- Mince√
- Fish√ ( Any relevant answer) (2)
4.3.4
- Light in texture√
- Flaky layers√
- Light golden brown colour√
- Uneven surface√ (Any 3) (3)
4.4
4.4.1
- Flavoured and unflavoured√
- Powdered/Granulated√
- Leaf/sheet√ (Any 2) (2)
4.4.2
- Too much sugar will weaken the gel√, retards the setting process√ (Any 1) (1)
- Weakens the jelly√, retards the setting process√, will melt more easily√ (Any 1) (1) (c) Dish will start to melt√ (Any 1) (1)
4.5
4.5.1
- The batter is steamed in moulds in a steamer or a big pot with water and then turned out for service. √
- Make sure that no water splashes into the bowl when steaming as this will cause the pudding to be soggy. √ (2)
4.5.2
- Choose the right size and shape of the plate√
- Pudding must be turned out on the middle of the plate√
- Arrange, decorate and garnish the pudding on the plate√
- The dessert can be flambéed√ – pour brandy over and set it alight√ (Any 2) (2)
4.5.3
- Custard√
- Cream√
- Ice Cream√
- Brandy sauce√ (Any 2) (2)
4.6
4.6.1
- People with HIV have greater nutritional needs and adequate diet is essential to promote a strong immune response to help HIV people to manage the symptoms√.
- Good nutrition slows down the progression from HIV to Aids√, and is required to optimise the benefits of Anti retro viral drugs√.
- A healthy diet can prevent and cure malnutrition, but it cannot cure HIV and Aids√
- People with Aids need to maintain a healthy body weight and take in enough protein so that they can maintain their muscle mass√
- The diet should consist of fresh fruits and vegetables in order to boost the immune system√ (Any 4) (4)
[40]
TOTAL SECTION C: 80
SECTION D: FOOD AND BEVERAGE SERVICE
QUESTION 5
5.1
5.1.1. The target market will be determined by:
- Demographic factors√ e.g. marital status, age, family size i.e. Pay a single midweek rate and your friend/partner stays free when sharing with you, Needs and income√
- Psychographic factors: activities√ i.e. Daily game drives, tennis and sauna√
- Product related factors√, which describe which products or services the customers prefer i.e. Luxurious accommodation on a game farm midway between Cathcart and Queenstown, in the heart of Eastern Cape. √ (Any 3) (3)
5.1.2
- Yes promotion has been used√
Give away 2 for 1: pay the single midweek rate of R600 and your friend/partner stays free when sharing with you. √ (2)
5.1.3 It is expensive√ because you are getting only one amount for two people√. (1)
5.1.4.
- The size of the container should not mislead the customer as to the size of the actual contents√
- Packaging should be easy to handle√
- Information on packaging should be clear√
- Packaging should be suitable for the contents√
- It should be strong, hygienic and clean√
- If possible, it should be recyclable and reusable√ (Any 2) (2)
5.1.5
- Business address√
- Form of business√
- Branding√
- Short, medium and long term goals√
- Street map√
- Site plan showing the layout of the business√ (Any 4) (4)
5.1.6 Springbok Game lodge contributes to job creation by:
- Direct job creation: positions in the hospitality industry√ examples:
Lodge receptionist√, Room attendant√, Tour guide√, Masseurs√ , chef√, waiters√, doorman√ (Any 2) - Indirect job creation: positions that does not form part of the hospitality industry√ examples:
Manufacturers of the linen used in the lodge√, suppliers of food, drinks√, producers of furniture√ (Any 2) (4)
5.2
5.2.1 (6)
REVENUE GENERATING AREAS | NON-REVENUE GENERATING AREAS |
|
|
5.2.2 These two departments depend on each other because sales and marketing is responsible for making potential customers aware of the products and services that the establishment offers√. They ensure that customers make use of the products and services which provides an income for the business√. The financial department ensures that the income is spent according to the budget and needs of the establishment√. (Any 2) (2)
5.2.3
- Supervises personnel√, property√ and key control√
- They must protect the establishment, staff and the guests from the following criminal activities:
- credit card skimming√
- liability or insurance fraud
- terrorism√
- information technology√
- gambling fraud√ (Any 3) (3)
5.2.4
- Movable cocktail bar√/Liquid chefs√
- Drinks on wheels√
- Vendor√
- children birthday party drinks√ (Any 3) (3)
[30]
QUESTION 6
6.1
6.1.1 Refers to getting equipment (cutlery, crockery) and tablecloths ready before meal is served√./ to put in place√/pre-preparation√ (2)
6.1.2 Check to see if the table cloth is:
- Clean √and has no food stains√ or wax stains from candles√.
- not burnt, shabby or worn out√ ironed√
- hanging evenly from each side of the table√
- not upside down√ (Any 3) (3)
6.1.3
- The glass should be washed in warm water with dishwashing liquid√
- Rinse in clean warm water√
- Airdry√
- Steam the glass over a bowl of boiling water√
- Polish using a clean, dry cloth√ (3)
6.1.4 Chardonnay is suitable√ because white meat (fish) goes well with white wine√
6.1.5 The red wine glass must be positioned 2.5cm√ from the tip of the main course knife√ and at 45° angle to the left of the white wine glass√ White wine glass first and red wine glass second√ M159 F 52 (2) (Any 3) (3)
6.1.6
- The red wine needs to be stored in the dark√ to avoid damage from ultra violet light√
- Place red wine bottles on their side so that the corks stay moist
- and swollen√ providing an airtight seal.
- Store red wine bottles upside down in a box√
- Store similar wines together√
- Pack and store wine bottles with the label to the top or to the front√ Wine prefers a slightly damp location free from vibration√
(Any 4) (4)
6.2
6.2.1 (4)
ON-CONSUMPTION | OFF-CONSUMPTION |
Allows the liquor to be consumed where it is bought√, liquor not taken off the premises√ | Allows liquor to be bought but consumed elsewhere√/ removed from premises√ |
6.2.2 In plated service food is plated directly onto individual plates√ in the kitchen or at a service point√ and then served to customers√ on the right hand side√ (3)
6.2.3
- Better portion control√
- Less wastage√
- More creativity from the chef who plates the food√
- Specialised training in terms of serving food from the platter is not required√
- Skilled waiters for carrying plates without disturbing food arrangement on the plates√ (Any 3) (3)
6.3
- Food will be spoiled√
- Food wastage will cost the lodge√
- The menu may need to be adapted and therefore the guests may not receive their preferred orders √failure e.g. a gelatine dish wont set√
- Unexpected cost will be incurred in order to fix the fridge.√
(Any 3) (3)
TOTAL SECTION D: 60
GRAND TOTAL: 200
ENGINEERING GRAPHICS AND DESIGN PAPER 1 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
ENGINEERING GRAPHICS AND DESIGN
PAPER 1
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of FOUR questions.
- Answer ALL the questions.
- ALL orthographic drawings are in first-angle projection, unless otherwise stated.
- ALL drawings must be completed using instruments, unless otherwise stated.
- ALL answers must be drawn accurately and neatly.
- ALL the questions must be answered on the QUESTION PAPER as instructed.
- ALL the pages, irrespective of whether the question was attempted or not, must be re-stapled in numerical sequence in the TOP LEFT-HAND CORNER ONLY.
- Proper planning is essential in order to complete all the questions.
- Print your examination number in the block provided on every page.
- Any details or dimensions not given must be assumed in good proportion.
QUESTIONS
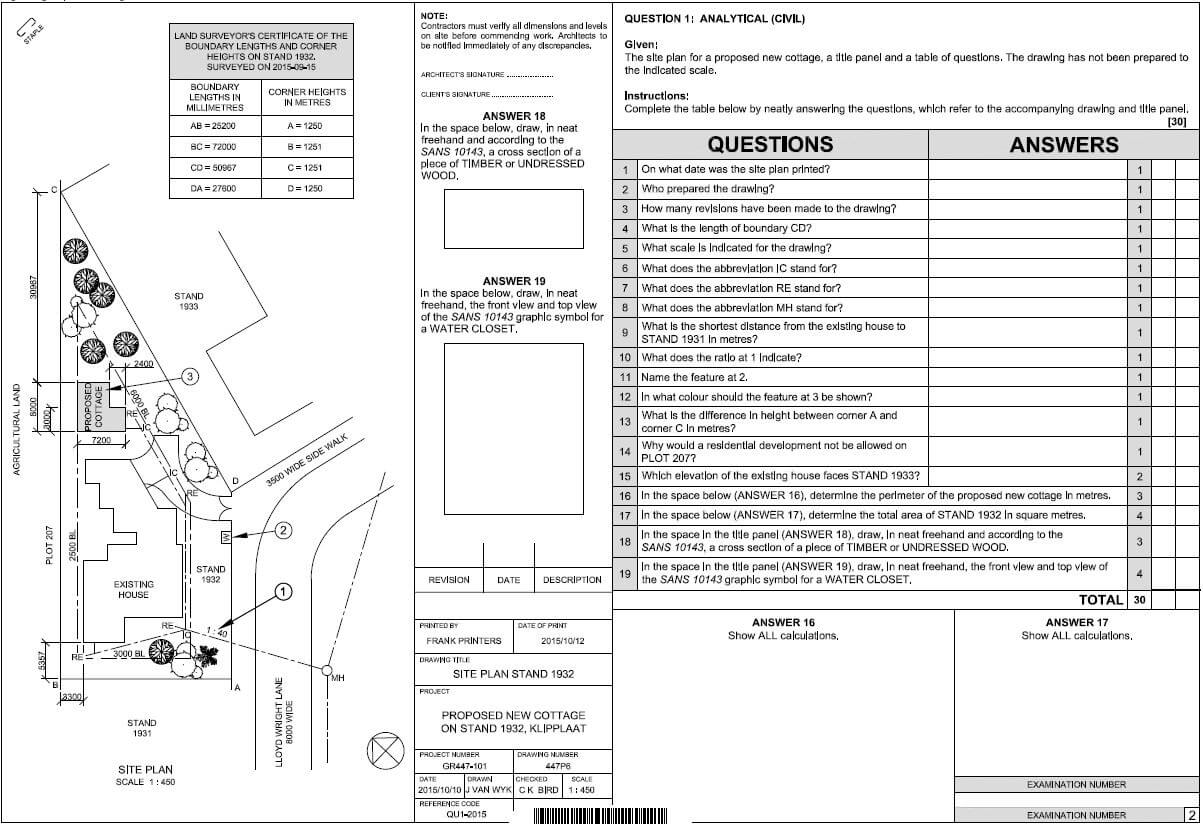
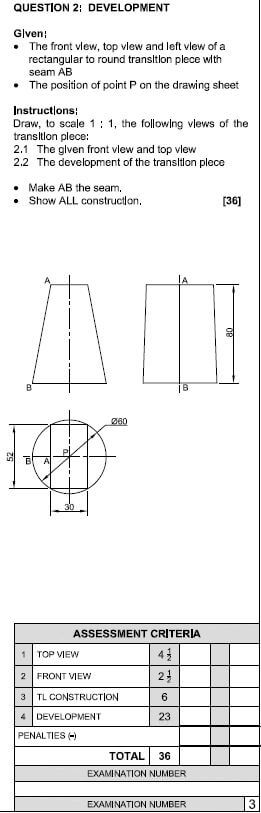
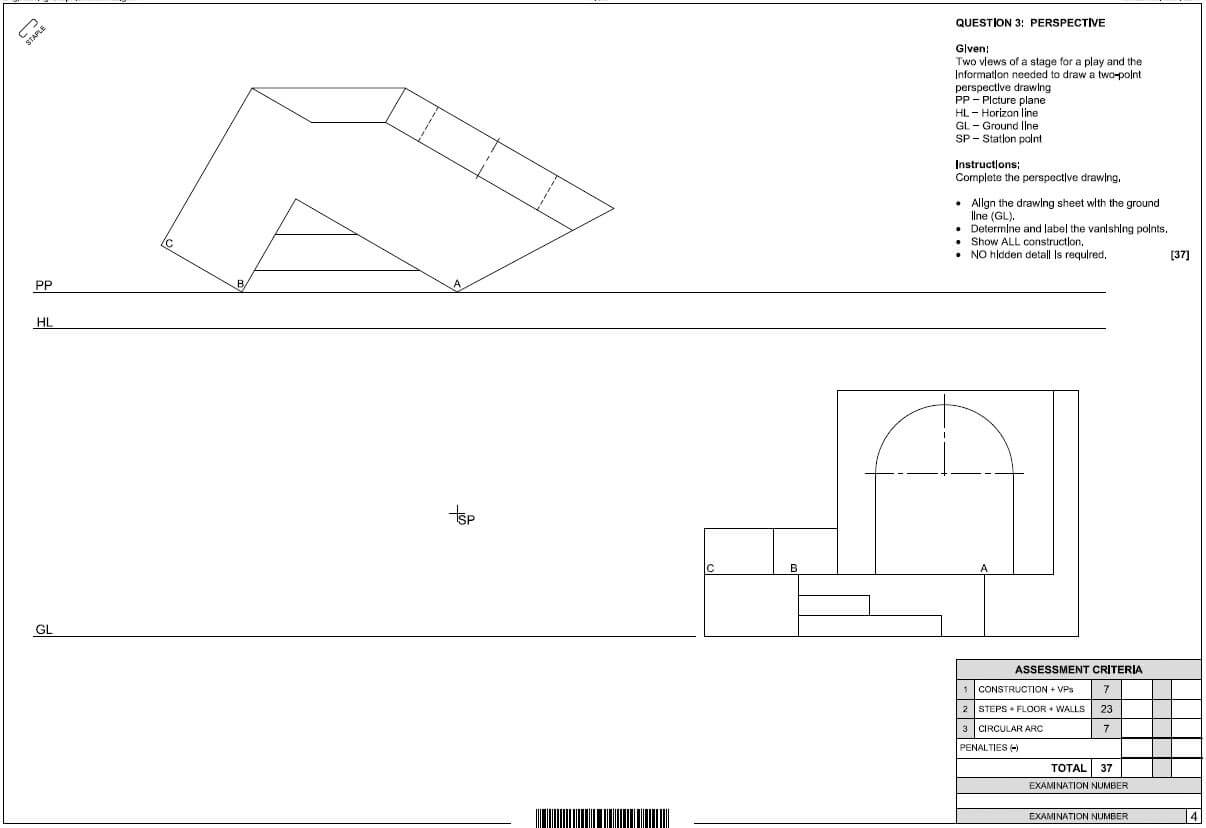
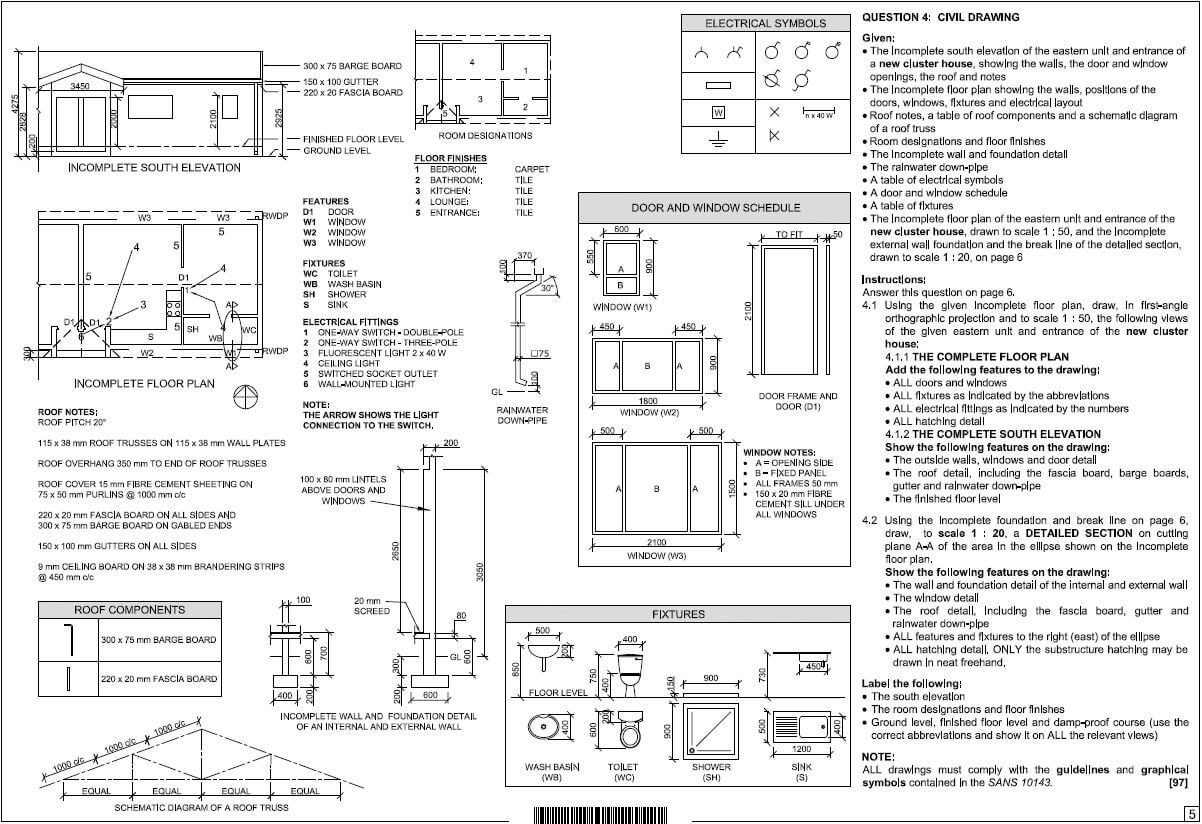
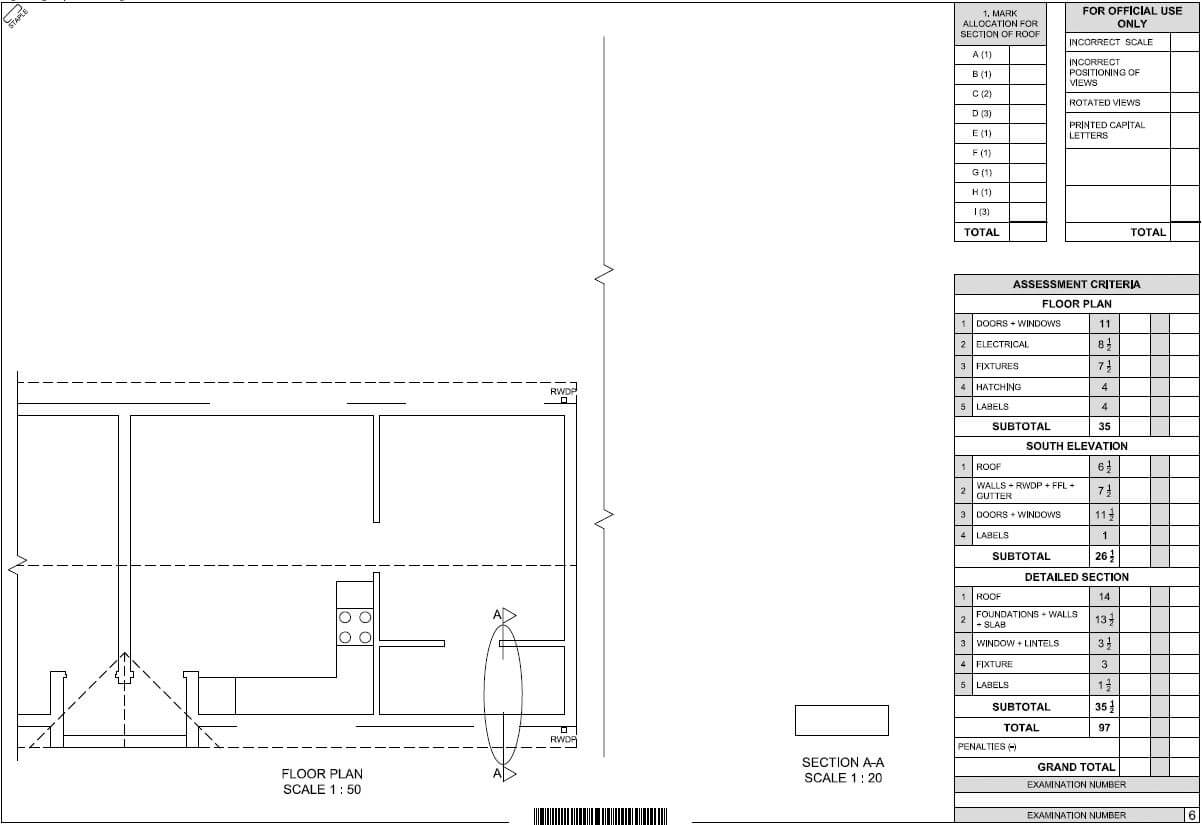
ENGINEERING GRAPHICS AND DESIGN PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
ENGINEERING GRAPHICS AND DESIGN
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of FOUR questions.
- Answer ALL the questions.
- ALL orthographic drawings are in third-angle projection, unless otherwise stated.
- ALL drawings must be completed using instruments, unless otherwise stated.
- ALL answers must be drawn accurately and neatly.
- ALL the questions must be answered on the QUESTION PAPER as instructed.
- ALL the pages, irrespective of whether the question was attempted or not, must be re-stapled in numerical sequence in the TOP LEFT-HAND CORNER ONLY.
- Proper planning is essential in order to complete all the questions.
- Print your examination number in the block provided on every page.
- Any details or dimensions not given must be assumed in good proportion.
QUESTIONS
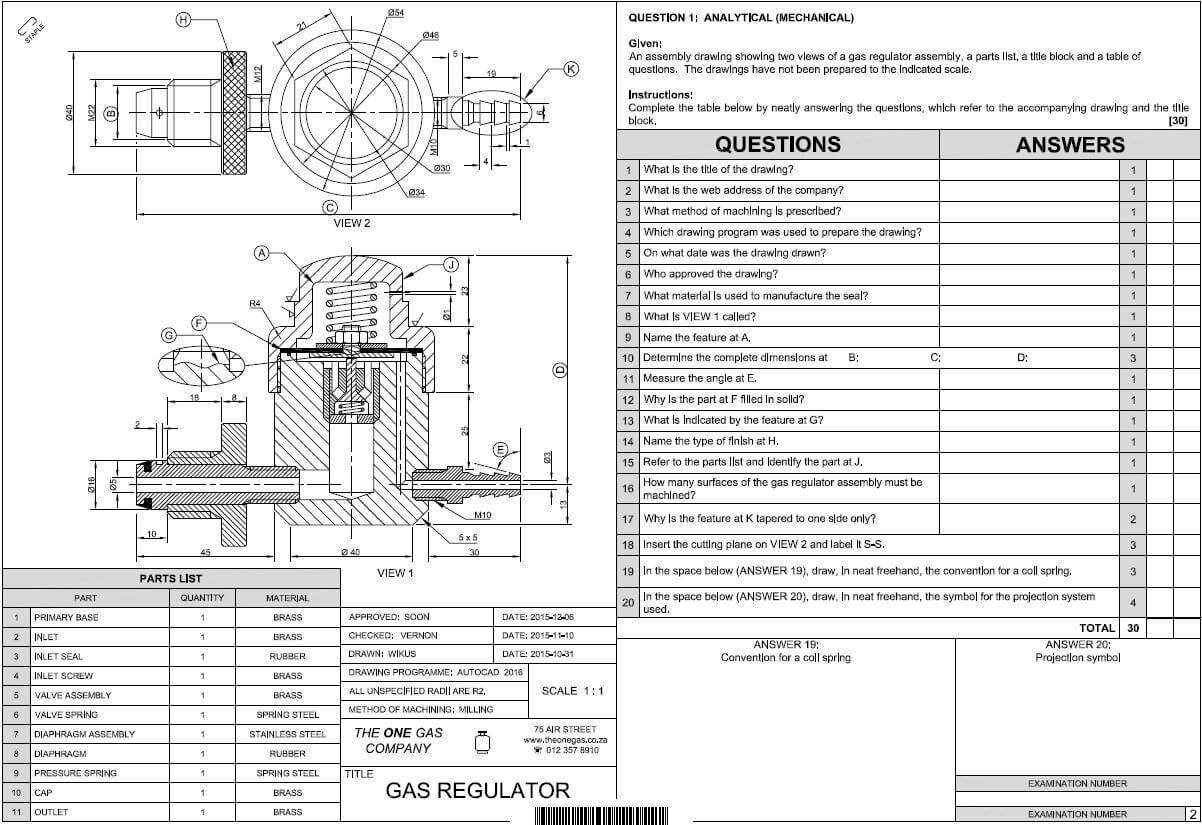

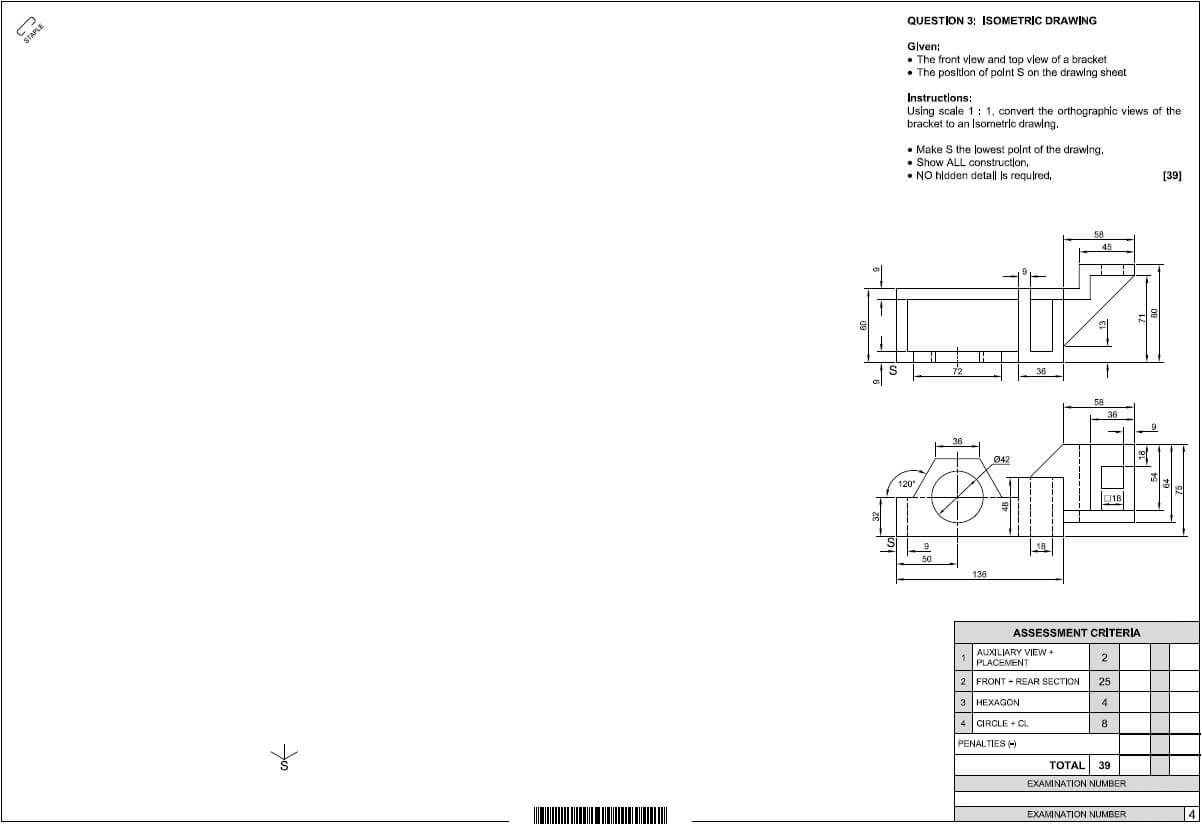
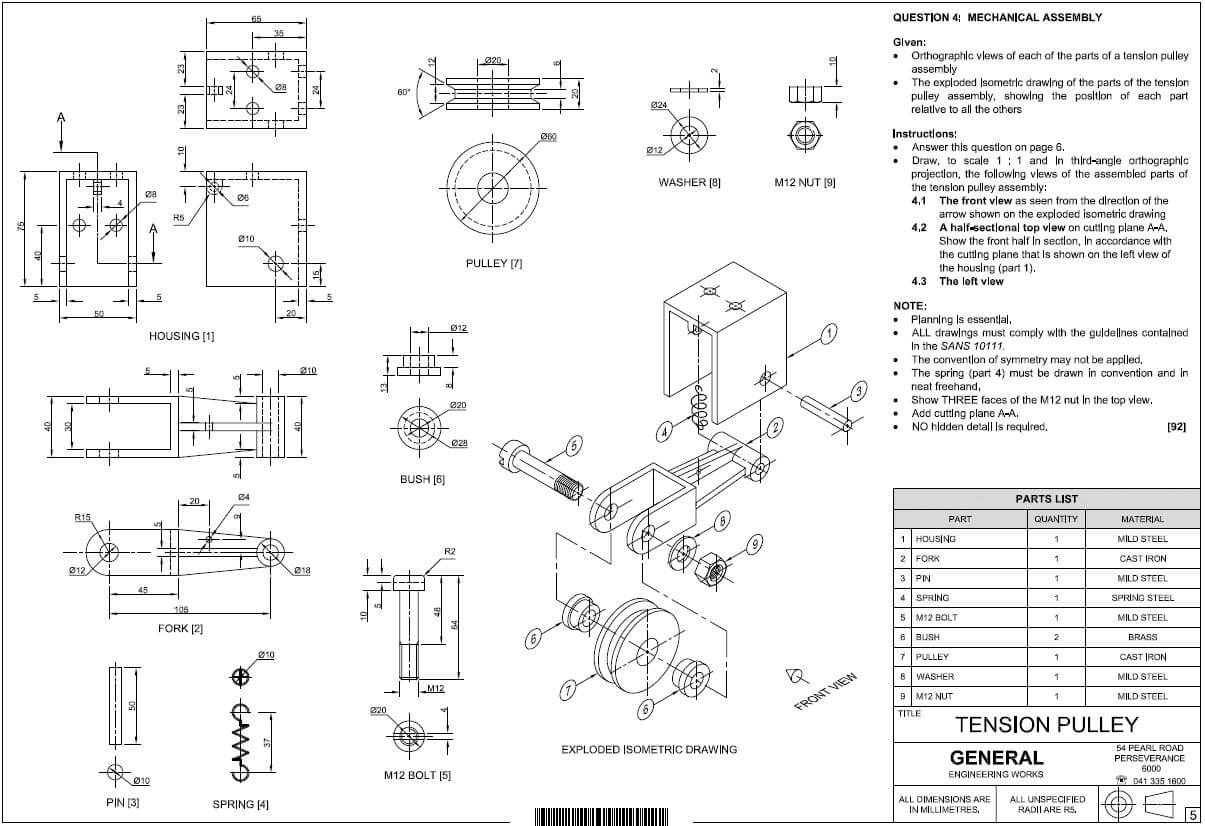
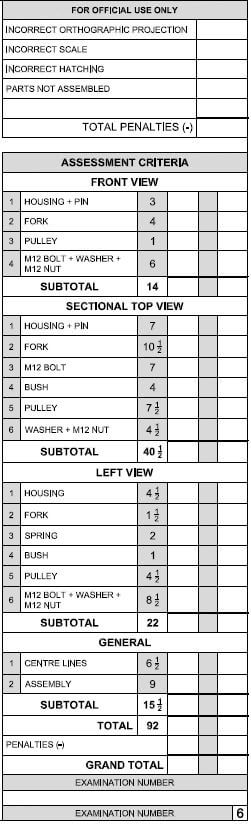
ENGINEERING GRAPHICS AND DESIGN PAPER 2 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2017
ENGINEERING GRAPHICS AND DESIGN
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2017
MEMORANDUM