COMPUTER APPLICATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS FEBRUARY/MARCH 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATION TECHNOLOGY
PAPER 2
GRADE 12
NSC PAST PAPERS AND MEMOS
FEBRUARY/MARCH 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- In general, a mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1–1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 Which ONE of the following units refers to processor speed?
- GHz
- dpi
- Mbps
- ppm (1)
1.2 The ... operating system utility would be helpful to people who experience challenges using their hands.
- Sticky Keys
- Sticky Notes
- Magnifier
- Narrator (1)
1.3 Which ONE of the following acronyms has to do with software licensing?
- GUI
- WWW
- WLAN
- EULA (1)
1.4 Which concept does the table below attempt to illustrate?
Application version 1.0 runs on OS version 1.0 |
Application version 1.0 does not run on OS version 2.0 |
- Downloading
- Archiving
- Accessibility
- Compatibility (1)
1.5 Which ONE of the following statements is NOT true about web applications?
- One may have to pay for the service.
- More than one person can work on a document at the same time.
- One does not need an Internet connection to access the resources.
- Data can be synced across multiple devices. (1)
1.6 While editing videos on a mobile device, most of the battery life will be used by the …
- microphone.
- CPU.
- screen.
- speaker. (1)
1.7 Which ONE of the following criteria will retrieve records based on a field value that ends with 'ad'?
- ad*
- ad
- a*d
- *ad (1)
1.8 The main task of the Disk Cleanup utility is to …
- delete individual files selected by the user.
- automatically delete unused files.
- format the hard disk when it is full.
- reorganise files and keep related files together. (1)
1.9 Which ONE of the following acronyms is NOT associated with hardware?
- HDD
- NIC
- EULA
- BYOD (1)
1.10 A/An … is NOT an example of malware.
- trojan
- ad-blocker
- worm
- keylogger (1) [10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 U.
COLUMN A | COLUMN B |
2.1 Currently the fastest standard for cellular data transmission |
|
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write 'true' or 'false' next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word 'NOT' to change the statement.)
NO mark will be awarded if only FALSE is written down.
EXAMPLES:
QUESTION | ANSWER |
Google is the world's most popular search engine. | True |
An NIC has slots for hardware components, such as the CPU. | False – motherboard |
3.1 A social network blocks hacking attempts from the Internet to a LAN. (1)
3.2 A keylogger is an advertisement that opens in a new web browser window while the user is working on the computer. (1)
3.3 A DoS attack occurs when a computer or network is flooded with a huge amount of useless data. (1)
3.4 Automatic index is a term used to describe pre-set formatting. (1)
3.5 A task definition is a set of questions that can have a selection of possible answers to choose from. (1) [5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 Why do many users prefer using an external mouse on a laptop computer that has a built-in trackpad? (1)
4.2 Give TWO reasons why one would buy laptop computers instead of desktop PCs for a CAT classroom. (2)
4.3 State TWO disadvantages of SSDs in comparison with hard disk drives. (2)
4.4 Smartphones have become very popular.
4.4.1 Give TWO examples of how smartphones can be used for educational purposes in the classroom. (2)
4.4.2 Discuss TWO disadvantages of using smartphones for playing games instead of using desktop PCs. (2)
4.4.3 Suggest TWO ways to wirelessly connect smartphones to other devices (NOT to other smartphones). (2)
4.4.4 How would one know that the geotagging feature of a smartphone was used when a photo was taken? (1)
4.5 Micro USB ports are commonly used in smartphones.
4.5.1 Why do these devices not have a standard USB port? (1)
4.5.2 Besides smartphones/cellphones, give TWO examples of ICT devices that use micro USB ports. (2)
4.6 You received an e-mail attachment with the file name Image01.exe.
4.6.1 Why should you NOT open this attachment? (1)
4.6.2 Suggest ONE way to deal with this attachment. (1)
4.7 Give TWO reasons why one should not use a pirated antivirus program? (2)
4.8 Suggest TWO ways to troubleshoot a computer that repeatedly does not load the operating system after it is switched on. (2)
4.9 Discuss TWO reasons why a CD created by your friend does not work on your computer. (2)
4.10 State TWO benefits of installing the latest operating system patches. (2) [25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Consider the packages below that advertise Internet access for video streaming at home. 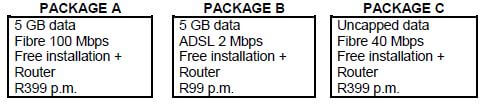
5.1.1 Which package would one use to daily stream HD videos at home? Give TWO reasons for your answer. (3)
5.1.2 Which package would be sufficient for general home use, such as sending e-mails and browsing the web, for which no video streaming is required? Motivate your answer. (2)
5.2 The web browser message below is displayed even when an ADSL connection is working. 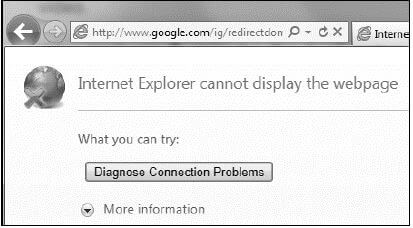
5.2.1 Give TWO possible reasons for receiving this message. (2)
5.2.2 What is the function of the circular arrow to the right of the address bar? (1)
5.2.3 Comment on the security of the intended connection, based on the information in the URL. (2)
5.3 Criminals often use hotspots to target unsuspecting users.
5.3.1 How would one use a mobile device to check if a hotspot is available? (1)
5.3.2 How can one prevent a keylogger from sending information back to the hacker? (2)
5.4 Give ONE reason why one would install a browser plug-in. (1)
5.5 How would an RSS feed on a blog benefit its users? (1) [15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 When does data become information? (1)
6.2 Explain why using an online questionnaire is an efficient option for gathering data, by referring to:
- Data capture
- Data processing (2)
6.3 The following rule was entered into a database to prevent inaccurate input:
<=0 OR >=18
Give TWO reasons why irrelevant or unusable data can still be entered. (2)
6.4 Explain why you would NOT use information found on the Internet, even if it was written by an expert author. (2)
6.5 What word processing feature could be used to view the changes made by multiple authors to a single document? (1)
6.6 How can one prevent changes being made to a spreadsheet opened in a spreadsheet application? (1)
6.7 How can one prevent the input of duplicate records when capturing data in a database table? (1) [10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Give ONE indication that a message you have received is a hoax. (1)
7.2 State TWO ways in which ICTs may negatively impact the workplace. (2)
7.3 Why are governments concerned about the widespread use of Bitcoin? (2)
7.4 Telecommuting saves time and travelling costs. Why do many employers still not allow telecommuting? (2)
7.5 Smart home appliances can connect to the Internet. State ONE advantage of having Internet-connected (IoT) appliances, such as a washing machine. (1)
7.6 Besides cheating, discuss TWO reasons why some schools ban the use of smartphones. (2) [10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Give a reason why an HTML page you created is not opening in a browser. (1)
8.2 How would you ensure that pictures in an HTML document are not too small or too large when viewed in a browser? (1)
8.3 The field names below were used in a database table to store the records of community members.
Field Name | Data Type | Description |
Name | Short Text | Name of member |
Address | Short Text | Residential address |
Gender | ||
Age | Number | Age on 1 January |
School | Short Text | Name of school |
Notes | Short Text | Additional comments |
8.3.1 Explain why none of the fields above can be used as a primary key. (1)
8.3.2 Suggest TWO data types for the Gender field so that one would not need to use a keyboard to input values into the table. (2)
8.3.3 Name a database feature that could be used to automatically place the same data into the School field for each new record. (1)
8.3.4 Currently a maximum of only 255 characters can be entered in the Notes field. How can one store more text in the Notes field? (1)
8.4 What feature of a word processing application allows you to copy formatting quickly from one section to another? (1)
8.5 You pasted the following data, separated by tabs, from Notepad into a word processing document:
State TWO ways in which this text can be placed in a table with three columns and three rows. (2)
8.6 The spreadsheet below shows supermarket employee wages.
8.6.1 The values in the Total column are not displayed. What can be done to display these values correctly, without changing any formatting? (1)
8.6.2 The function below (used in column D) fails to allocate a bonus to employees who worked longer than 27 hours per week:
=IF(B4<=27,200,0)
Discuss TWO alternative ways in which the mistake in the function could be corrected. (2)
8.6.3 Which spreadsheet function would one use to determine the number of bonuses paid to employees? (1)
8.7 On which field was the report below grouped? 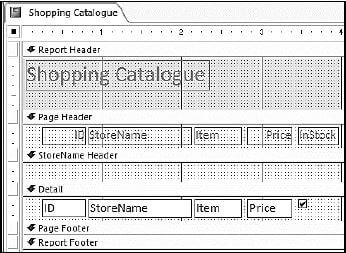 (1)
(1)
[15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
Your school principal asked you to use your CAT skills to give advice with establishing an online school newspaper. Computer equipment will have to be purchased for this purpose.
9.1 Describe TWO hardware characteristics of entry-level computers that make them different from high-end machines. (2)
9.2 Suggest TWO examples of application software that may need to be installed to facilitate the publishing of the school newspaper. (2)
9.3 The home page of the newspaper website will be based on a template. Explain what a template is. (1)
9.4 As part of your advice you drew a diagram of how the newspaper office network (LAN 1) should be connected to the school network (LAN 2). 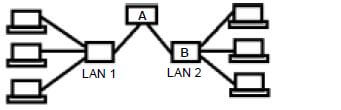
9.4.1 Name device A connecting the two LANs. (1)
9.4.2 Name device B on LAN 2. (1)
9.4.3 State TWO ways in which access to the LAN 1 network can be controlled. (2)
9.4.4 State TWO advantages of using cables to connect the computers in the network. (2)
9.5 Links to the newspaper articles will be posted on social media. State TWO advantages of using Facebook to share the newspaper. (2)
9.6 Give ONE reason why FOSS instead of proprietary software should be used at the newspaper office. (1)
9.7 The error message below appeared on one of the computers in the newspaper office, preventing it from getting updates.
9.7.1 Discuss TWO possible reasons for the error. (2)
9.7.2 State ONE implication of the error message. (1)
9.8 State TWO ways in which the school can backup their data so that it is stored in another location. (2)
9.9 A database table with author and article names as fields will be used to store the information about learners who contribute towards content in the newspaper.
9.9.1 Discuss TWO reasons why it would be better to use a form instead of the datasheet view of a table for capturing data. (2)
9.9.2 Name TWO database tools that can be used to determine who contributed the most articles towards the newspaper. (2)
9.10 Give TWO reasons why it would be a good policy to have USB ports disabled by default on the LAN used by the newspaper office? (2) [25]
QUESTION 10
Your school is hosting a talent concert. You have been asked to help with ICT-related matters.
10.1 Many learners would like to access profiles of participants using the Internet.
10.1.1 Name TWO hand-held mobile devices that can be used for this purpose. (2)
10.1.2 State TWO disadvantages for participants of having profiles that are accessible on the Internet. (2)
10.1.3 State TWO ways in which to ensure that it is legal to use pictures sourced from the Internet. (2)
10.1.4 The following HTML code will be used to display a table with information about each contestant:
<table border="2" cellpadding="1" cellspacing="4">
<tr> <td colspan="2"> </td> <td> </td> </tr>
<tr> <td> </td> <td> </td> <td> </td> </tr>
</table>
How many rows and columns are there in the table? (2)
10.2 You are required to assist with upgrading the old and slow computers for the talent concert.
10.2.1 Give TWO software-related reasons why these computers may have slowed down. (2)
10.2.2 What hardware components on old computers must commonly be replaced to improve performance? (2)
10.2.3 Some recently installed applications are not working after hardware upgrades. Discuss TWO ways in which this problem can be resolved. (2)
10.2.4 Suggest TWO strategies to deal with computers that cannot be upgraded. (2)
10.3 The screenshot below contains system information of a computer that will be used for the talent concert.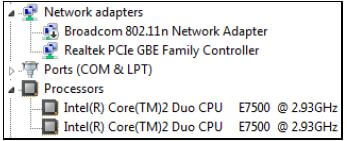
10.3.1 There is one CPU in the computer. Why does the CPU appear twice under Processors? (1)
10.3.2 What is the role of the Broadcom 802.11n Network Adapter? (1)
10.4 The spreadsheet chart below was used to analyse voting results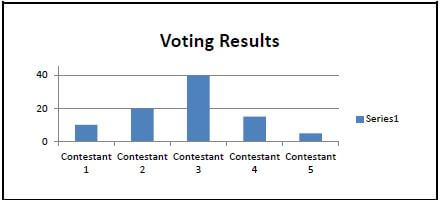
10.4.1 State TWO features that could have been added to this chart to improve understanding. (2)
10.4.2 Name TWO spreadsheet tools, other than the chart, that could have been used to analyse the voting results. (2)
10.5 The table and query result below were used by the judges to analyse competition results. 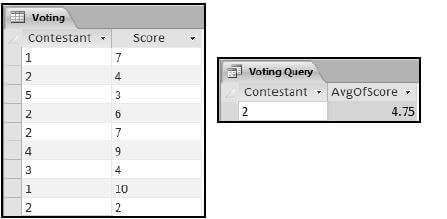
10.5.1 What data type was used for the field Score? Motivate your answer. (2)
10.5.2 There are four records for Contestant 2 in the database table. How was the average function used to return only one row? (1) [25]
TOTAL SECTION C: 50
GRAND TOTAL: 150