INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - AMENDED SENIOR CERTIFICATE EXAMINATION PAST PAPERS AND MEMOS MAY/JUNE 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
GRADE 12
SENIOR CERTIFICATE EXAMINATIONS
MAY/JUNE2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: Systems Technologies (25)
SECTION C: Communication and Network Technologies (20)
SECTION D: Data and Information Management (25)
SECTION E: Solution Development (27)
SECTION F: Integrated Scenario (38) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Write down the question number (1.1.1–1.1.5), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
1.1.1 The result of the expression 7 MOD 5 + 10 DIV 3:
- 2
- 3
- 4
- 5 (1)
1.1.2 A digital signature is used …
- when someone signs an electronic document.
- to identify the sender of an electronic message.
- as the default signature that is added to an e-mail address.
- for trusted communication of sensitive information. (1)
1.1.3 A Trojan virus is designed to …
- delete all system data.
- gain access to administrator privileges.
- cause minor annoying problems when spreading itself over the network.
- appear useful, but to do harm. (1)
1.1.4 A technique used to make electronic communication appear to originate from a legitimate source is known as …
- spamming.
- spoofing.
- spying.
- streaming. (1)
1.1.5 To establish a relationship between two tables in a database, a link must be made from the …
- public key to private key.
- foreign key to private key.
- primary key to public key.
- primary key to foreign key. (1)
1.2 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.2.1–1.2.10) in the ANSWER BOOK.
1.2.1 The amount of data an ISP allows a user to upload and download in a particular time period (1)
1.2.2 A website that is regularly updated with news and events in chronological order (1)
1.2.3 A person who breaks into a system to steal data electronically or to make unauthorised changes to electronic data (1)
1.2.4 An Internet service that translates a domain name to an IP address, e.g. www.abcd.com translates to 169.15.100.123 (1)
1.2.5 The protocol used for secure encrypted transfer of data on the Internet (1)
1.2.6 The process whereby the existing firmware is wiped and replaced by an updated version (1)
1.2.7 An Internet-based alternative to text messaging, in which multimedia can be exchanged in real time via applications, such as WhatsApp (1)
1.2.8 A common format for storing digital music by combining efficient compression techniques and good sound quality (1)
1.2.9 Gaining unauthorised access to and making use of a connection in an unsecured Wi-Fi network (1)
1.2.10 Start-up test performed to ensure that all essential hardware is present and in working order (1)
TOTAL SECTION A: 15
SCENARIO
A travel agency in the local shopping complex requires the help of the IT learners with refurbishing the IT infrastructure on their premises.
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
The travel agency has a LAN in the office building. All agents will need a computer at their work stations.
2.1 A choice has to be made between purchasing fat- or thin-client computers.
Motivate the use of thin-client computers for the office. (2)
2.2 When a computer is switched on, the processor executes the BIOS program.
2.2.1 Where is the BIOS found?(1)
2.2.2 State TWO functions of the BIOS. (2)
2.3 Many factors influence the performance of a computer system.
2.3.1 What term is used to describe the technique where more than one CPU core works on separate applications at the same time? (1)
2.3.2 Caching is used in a variety of situations in a computer system.
- What is the main aim of caching, irrespective of where it occurs? (2)
- Explain how disk caching improves the performance of a computer. (2)
2.3.3 Except for caching, name ONE other factor that can improve the performance of a computer system AND explain how it will improve performance. (2)
2.4 State the common task that is executed by both an interpreter and a compiler. (2)
2.5 Upgrading computer hardware and software can be considered as an alternative to replacing computers.
Suggest TWO aspects that need to be considered when deciding to upgrade hardware or software. (2)
2.6 There are many economic considerations when using the computers in the travel agency.
2.6.1 Besides switching off all computers at night, state TWO other ways in which the electricity usage of computing devices can be decreased. (2)
2.6.2 Explain TWO ways in which the use of computers will be financially beneficial for the travel agency. (2)
2.7 An incorrect statement was made that the use of an effective backup maintenance program will prevent the hard drive from becoming fragmented.
2.7.1 Describe TWO aspects of an effective backup maintenance program. (2)
2.7.2 Define the term disk fragmentation. (1)
2.8 A solid-state drive (SSD) is used for storage in some devices.
Give TWO reasons why SSDs are more suitable for use in portable devices. (2)
TOTAL SECTION B: 25
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
The shopping complex will use a cabled network to connect all the shops.
3.1 The cabled LAN in the shopping complex will have access to the Internet.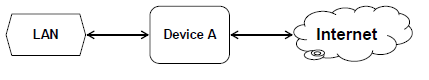
3.1.1 Give TWO reasons to motivate the use of UTP cables for the network in the shopping complex.(2)
3.1.2 Which hardware device (Device A) will be used so that the LAN will have Internet access? (1)
3.1.3 Suggest a suitable topology for the LAN. (1)
3.2 The travel agency uses a client-server network.
State TWO advantages of using a client-server network rather than a peer-to-peer network. (2)
3.3 The system administrator for the travel agency will make sure that software is regularly updated.
3.3.1 Suggest ONE reason for keeping software up to date. (1)
3.3.2 State TWO other responsibilities of the system administrator. (2)
3.4 Security of client data is essential in the travel industry. malware can attack a computer through the network.
3.4.1 Explain what role password protection plays in the security of data. (1)
3.4.2 Define the term malware. (2)
3.4.3 Explain how a firewall assists in providing security to computers on a network. (2)
3.5 The travel agency advertises their products on a website. Some web pages are dynamically generated.
3.5.1 Some websites make use of cookies. What is a cookie in computing terms? (2)
3.5.2 Explain what a dynamic web page is. (2)
3.5.3 How are CSSs (cascading style sheets) used in developing a web page? (2)
3.5.4 A digital certificate is attached to the company's website.
- Why is it recommended that the company's website have a digital certificate? (1)
- State TWO details that are found on the digital certificate. (2)
TOTAL SECTION C: 23
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
The tour company requires the use of a database management system to store details of tours and tour guides.
4.1 Which ONE of the following is an example of a DBMS?
- Oracle
- MS Excel
- FireFox
- Delphi(1)
4.2 Name TWO aspects of database design that should be addressed to ensure effective functionality. (2)
4.3 A record of the tours and the agent responsible for each tour is stored in a table, tblTours. The first five records of the tblTours table are given below.\
| tblTours | ||||
| TourDestination | StartDate | EndDate | TourGuide | GuideTelNum |
| Kruger National Park | 2017-07-01 | 2017-07-06 | Senzo Dladla | 0812345678 |
| Drakensberg | 2017-07-20 | 2017-07-24 | Meredith Peters | 0731112223 |
| Cape Town | 2017-08-14 | 2017-08-24 | Kajal Singh | 0619988772 |
| Sun City | 2017-08-22 | 2017-08-30 | Senzo Dladla | 0812345678 |
| Mozambique | 2017-08-23 | 2017-09-03 | Kajal Singh | 0619988772 |
4.3.1 Explain what a record in a database is. (1)
4.3.2 All the data types have been set to text.
Identify ONE field where the data type needs to be changed AND suggest a more suitable data type. (2)
4.3.3 The design of the tblTours table allows anomalies to occur.
- Explain what an update anomaly is, using the tour guide Kajal Singh as an example. (2)
- Explain the basic steps that should be followed when the tblTours table has to be normalised. (3)
4.3.4 The following SQL statement is executed:
DELETE FROM tblTours
What is the result after executing this statement? (2)
4.4 Parallel data sets can be used to safely store data.
Briefly explain how the use of parallel data sets prevents loss of data. (2)
4.5 The data in the database can be used for data mining.
Explain what data mining is. (2)
4.6 SQL queries are used to obtain information from the database.
Explain how SQL injection can be used as a hacking tool. (2)
4.7 The travel agency uses a distributed database.
4.7.1 Give TWO reasons why distributed databases are used. (2)
4.7.2 Name the TWO models for distributed databases that are used to ensure that data on various servers remain up to date and synchronised. (2)
TOTAL SECTION D: 23
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 The travel agency uses the interface below as a booking form for holiday accommodation. The different types of available accommodation can be categorised as 'campsite', '4-bedroom house', 'B&B' and 'hotel'.
5.1.1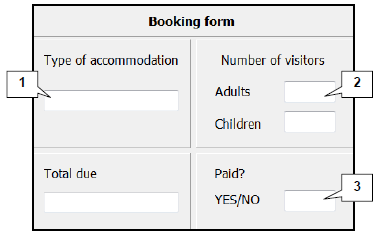
- Numbers 1–3 indicate that edit boxes are used for data input. In each case (numbers 1–3) indicate a more appropriate input component to ensure that valid data is entered.
NOTE: You are not allowed to use a specific component for more than one answer. (3) - Suggest TWO possible details that should also be included in the booking form above. (2)
5.1.2 The data entered using the changed form must be validated and verified.
- Explain the following concepts:
- Valid data (1)
- Verified data (1)
- Explain how the component suggested for data input (1) in QUESTION 5.1.1 will ensure that valid data is entered. (1)
5.2 The two-dimensional array, arrVisitors, represented in the table below, stores the number of visitors to a fun park and an animal park. The calculated totals of visitors for each month will also be stored in the same array.
NOTE: Only the shaded information in the table is stored in the array.
| Number of visitors | |||
| Fun park | Animal park | Total | |
| January | 1112 | 1321 | |
| February | 1943 | 2312 | |
| March | 1721 | 1233 | |
| April | 1512 | 2312 | |
| May | 1412 | 1345 | |
| June | 1121 | 1453 | |
| July | 2121 | 1732 | |
| August | 1211 | 1998 | |
| September | 1211 | 2012 | |
| October | 2142 | 2901 | |
| November | 2132 | 2132 | |
| December | 2111 | 2987 | |
The algorithm below has been compiled to determine the total number of visitors to the two parks for each month and then to store it in the array.
Study the algorithm to answer QUESTION 5.2.1 and QUESTION 5.2.2:
- Load values into the arrVisitors array for the first two columns
- For counter1 ← 1 to 12
- total ← 0
- For counter2 ←1 to 2
- total ← total + arrVisitors [counter1,counter2]
- End inner loop
- End outer loop
The given algorithm is missing a statement that causes a logical error.
5.2.1 Explain what is meant by a logical error. (2)
5.2.2 To solve the logical error, the total number of visitors for each month must be stored in the 2D array, using the following statement:
arrVisitors[ x , y ] ← total
- Replace x and y in the statement, so that the total for each month will be correctly stored in the 2D array. (2)
- Which ONE of the statements (A–C) below describes the position in the algorithm where this statement must be inserted CORRECTLY?
- Between lines 6 and 7
- Between lines 3 and 4
- Added as line 8 (1)
5.2.3 Indicate the changes that need to be made in lines 2 to 5 of the given algorithm if the sum of the columns must be determined, instead of the sum of the rows.
NOTE: You do not have to save the sum of the columns in the array. (2)
5.2.4 Two values in the array have been captured incorrectly. The values for 'Fun park' and 'Animal park' for May must be swapped.
Write pseudocode to swap the two values in the array. (3)
5.3 The incomplete UML diagram below represents a Booking class in OOP.
| Booking |
|
| + constructor(accommodationType, numAdults, numChildren, startDate, endDate) + getAccommodationType() + setStartDate(startDate) - calcDays() + toString() |
5.3.1 What does the abbreviation OOP refer to? (1)
5.3.2 What is the purpose of a constructor method in a class? (1)
5.3.3 Motivate why it is NOT necessary to have the field numberOfDays as an attribute of the class. (1)
5.3.4 What is the implication of declaring the method calcDays() as a private method? (1)
5.3.5 The starting date of the booking has been initialised in the constructor. Explain why a setStartDate() method may still be required? (2)
5.3.6 Explain the purpose of a toString() method. (2)
TOTAL SECTION E: 26
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The travel agents must be able to conduct business from their office building or by using their mobile office. Internet access is required as most of the business is conducted online.
6.1 The agents will be able to use their smartphones to access the company's network when working away from the office.
6.1.1 Except for making calls and accessing the network, state ONE way in which a smartphone can be useful as a business tool. (1)
6.1.2 Discuss TWO disadvantages of doing business using a smartphone. (2)
6.1.3 Which online service is used to ensure that travel agents will have access to the latest versions of their documents on all of their devices at all times? (1)
6.2 There is a need for access control at the travel agent's office building.
State TWO methods that the agency can use to control access to the building electronically. (2)
6.3 The travel agency's AUP prohibits the use of social networking sites on the agency's computers.
6.3.1 Write out the abbreviation AUP in full. (1)
6.3.2 Except for the example already given, name TWO other aspects that should be included in the travel agency's AUP. (2)
6.3.3 Motivate TWO reasons why the prohibition of social networking sites at work is justified. (2)
6.4 The agents will also need access to the company's intranet.
6.4.1 What is an intranet? (2)
6.4.2 Suggest a way in which the travel agents could gain access to the travel agency's intranet securely when working on their tablet computers from home.(1)
6.5 An Ethernet connection with MAC address 20-89-84-DE-C9-F4 refers to the NIC of a computer at the office.
6.5.1 What is the function of an NIC? (1)
6.5.2 What is the purpose of a MAC address? (1)
6.6 A multifunction printer has been ordered for the office and will be accessible on the cabled network.
6.6.1 It has been argued that the image scanner function is a waste of money.
Suggest another way in which travel documents can be captured as images to be saved on the computer system. (1)
6.6.2 Besides sharing of the printer, give TWO other reasons for the networking of devices. (2)
6.6.3 A client has succeeded in sending a document from his tablet to the printer.
Which technology will allow a user, not connected to a cabled network, to print on the printer? (1)
6.7 The administration and accounting side of the travel agency will be run on cloud applications.
6.7.1 What software is needed to run cloud applications? (1)
6.7.2 SaaS (Software as a Service) can be provided as an integrated product, for example Office 365.
State TWO advantages of using SaaS as an integrated product. (2)
6.7.3 Explain how cloud computing uses virtualisation to provide powerful online services. (2)
6.7.4 Briefly describe TWO disadvantages of cloud computing. (2)
6.8 Customers will be able to book and pay online, using the digital currency BitCoin.
6.8.1 Online transactions are encrypted. Explain the term encryption. (2)
6.8.2 Online security methods include the use of public key encryption. Briefly explain the public key encryption method. (2)
6.8.3 State ONE disadvantage of using BitCoin to pay online. (1)
6.9 BitTorrent software is blocked on the network in the office.
6.9.1 What is BitTorrent? (2)
6.9.2 State TWO benefits of using BitTorrent. (2)
6.10 Downloading software may sometimes be considered as software piracy.
Give TWO examples when downloading software will not be regarded as piracy. (2)
TOTAL SECTION F:38
GRAND TOTAL:150