COMPUTER APPLICATIONS TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - AMENDED SENIOR CERTIFICATE PAST PAPERS AND MEMOS MAY/JUNE 2017
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATIONS TECHNOLOGY PAPER 2
GRADE 12
SENIOR CERTIFICATE EXAMINATIONS
MAY/JUNE2017
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A:(25 marks)
SECTION B:(75 marks)
SECTION C:(50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- In general, a mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Write down the question number (1.1–1.10), choose the answer and make a cross (X) over the letter (A–D) of your choice in the ANSWER BOOK.
1.1 Which ONE of the following options best describes RAM?
- Permanent
- Temporary
- Multi-core
- Part of CPU (1)
1.2 OCR software allows for …
- getting an editable version of a scanned document.
- ordering printing supplies.
- installation of drivers.
- saving a word processing document as a web page. (1)
1.3 Which ONE of the following devices allows a computer to safely shut down in the event of a power failure?
- USB
- GPU
- PSU
- UPS (1)
1.4 Which ONE of the following data transmission technologies does NOT belong with the others?
- Wi-Fi
- 3G
- Fibre
- LTE (1)
1.5 The same application can be used to open the file types …
- MP3 and PNG.
- DOCX and RTF.
- EXE and PDF.
- ISO and ACCDB. (1)
1.6 Wide usage of ICTs has resulted in ...
- less advertising.
- a decrease in processing speed.
- a slowing down of the economy.
- telecommuting. (1)
1.7 Social engineering does NOT involve …
- running multiple programs at the same time.
- looking at the screen over someone's shoulder.
- an offer of help from a bystander at an ATM.
- receiving e-mails from strangers. (1)
1.8 Plagiarism can be defined as …
- the protection of intellectual rights.
- allowing others to use your work.
- passing off someone else's work as your own.
- unauthorised access to information. (1)
1.9 What concept is represented by the picture below?
- Hardware
- Ergonomics
- Hacking
- Biometrics (1)
1.10 Which ONE of the following formulas gives the output in cell C2 below: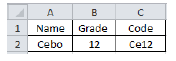
- A =CONCATENATE(RIGHT(A2,2),B2)
- B =CONCATENATE(LEFT(B2,2),A2)
- C =CONCATENATE(LEFT(A2,2),B2)
- D =CONCATENATE(MID(A2,2,2),B2) (1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 U.
| COLUMN A | COLUMN B |
| 2.1 A program in an office suite where the copy-down/auto-fill feature is more likely to be used 2.2 A monitor specification indicating image quality 2.3 A critical component of a computing device 2.4 An operator that allows a user to compare two values in conditional functions 2.5 A criterion used to check whether the source of information is objective 2.6 A technology to help avoid security threats on a network 2.7 A company that provides Internet connectivity 2.8 A possible disadvantage of using cloud services 2.9 A protocol that makes it more difficult for a hacker to see what a user is doing online 2.10 A limitation of Bluetooth for data transfer |
|
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write 'true' or 'false' next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word 'NOT' to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
| QUESTION | ANSWER |
| Google is the world's most popular search engine. | True |
| An NIC has slots for hardware components, such as the CPU. | False – motherboard |
3.1 Facebook is the largest non-profit online encyclopaedia. (1)
3.2 Antivirus updates fix known bugs. (1)
3.3 The SUMIF function is an alternative to using nested IF statements. (1)
3.4 Reducing the size of attachments and not typing in capital letters are phishing rules. (1)
3.5 A minus operator before a key word will exclude search results containing that word. (1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 What is the difference in function between the Ctrl-X and Ctrl-C keyboard shortcuts? (1)
4.2 What is the function of the Recycle Bin on the desktop? (1)
4.3 State an advantage of distributed computing. (1)
4.4 Files with an HTML extension open in Notepad instead of a browser.
Suggest a possible solution to this problem. (1)
4.5 Name TWO devices that allow a computer to communicate with other computers. (2)
4.6 Suggest a way to add a folder to a file. (1)
4.7 Create a strong password by applying at least FOUR rules. (Do NOT explain what these rules are.) (4)
4.8 There are different ways to connect a monitor to a computer. Study the picture below and answer the questions that follow.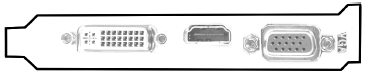
4.8.1 What is the name of the component on which one will find the three ports shown above? (1)
4.8.2 Name the port shown in the middle. (1)
4.8.3 State TWO disadvantages of the port on the right. (2)
4.9 What type of input device is used to capture natural handwriting? (1)
4.10 Where would you commonly find new apps for a mobile device? (1)
4.11 You have downloaded an app that asks permission to access some data and features on your mobile device.
Motivate why you would NOT grant an app certain permissions. (2)
4.12 State TWO hardware specifications to consider when buying a desktop computer, which will save you desk space. (2)
4.13 State TWO criteria, other than the name of the file, which can be used in Windows Explorer when searching for a file. (2)
4.14 Explain the purpose of system utilities and give an example. (2)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Name the device that connects a LAN to the Internet. (1)
5.2 Give TWO advantages of a file server in a network. (2)
5.3 Name TWO types of network technologies that notebook computers support. (2)
5.4 You have two switches, each with four Ethernet ports.
How would you go about connecting six computers in a network, using only these switches? (2)
5.5 Why would a 10 Mbps ADSL line be unsuitable for someone who needs an upload bandwidth of 10 Mbps? (2)
5.6 Why would one flag/star an e-mail? (1)
5.7 Broken hyperlinks on websites affect the user experience negatively.
5.7.1 Which aspect of a website could be compromised if it has broken hyperlinks? (1)
5.7.2 Give TWO reasons for broken hyperlinks on a web page. (2)
5.8 What is the minimum number of participants in a chat room, given its purpose? (1)
5.9 How is the Internet different from the World Wide Web? (1)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Why must one include the URLs of websites used for research on your bibliography? (1)
6.2 The following list was taken from a record sheet:
| Name and Surname | Grade | Task 1 |
| 40 marks | ||
| Lungisa Mbongwe | 12 | 35 |
| Songela Dumisa | 12 | 12 |
| Hendrik Williams | 12 | 16 |
| Zodwa Cele | 12 | 42 |
| John Mokoena | 12 | 36 |
| Average | 12 | 28.2 |
Identify TWO errors in the record sheet above which affect the quality of the information. (2)
6.3 State TWO advantages of organising data in a database, rather than in a spreadsheet. (2)
6.4 Study the graph below and answer the questions that follow.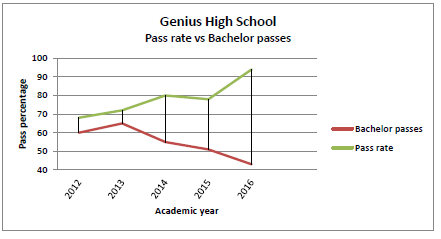
6.4.1 Which year had most bachelor passes? (1)
6.4.2 Identify TWO trends seen in this graph. (2)
6.4.3 What do the trends, represented by the graph, show about the quality of the school's results? (1)
6.4.4 Give ONE recommendation based on the information in the graph. (1)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Define online identity theft. (1)
7.2 Give TWO examples of a situation when the right to access information may be more important than the right to privacy. (2)
7.3 State TWO negative implications of 3D printers, which are becoming more common. (2)
7.4 Recommend TWO strategies to control social unrest with the use of ICTs. (2)
7.5 Recently a prominent smartphone manufacturer had to withdraw exploding devices from the global market.
7.5.1 State ONE advantage for society of the withdrawal of the faulty devices. (1)
7.5.2 What is a possible negative effect of this withdrawal on consumers? (1)
7.5.3 How is the incident likely to affect the manufacturer? (1)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Name TWO features common to spreadsheet AND database applications to ensure the accuracy of data. (2)
8.2 What is the effect of using the spreadsheet feature 'Format as Table' on a cell range? (2)
8.3 Give an example of a spreadsheet function that cuts off only the decimal portion of a number. (1)
8.4 State TWO common problems when importing data from a CSV file into a database. (2)
8.5 Which TWO automatic referencing features of a word processing application are only available if the 'Manage Sources' feature has been used? (2)
8.6 A heading that was later added to a document does not appear in the automatic table of contents.
State TWO steps to take to ensure that this new heading will appear in the automatic table of contents. (2)
8.7 An image on a web page you created does not display fully in the browser.
Suggest TWO ways to ensure that the image is fully visible. (2)
8.8 The following HTML code was taken from a working HTML document:
<table>
<tr><td></td></tr>
</table>
8.8.1 How many cells should be displayed in the first row? (1)
8.8.2 Why will this code not display anything in the browser? (1)
[15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
Your community has established a community policing forum (CPF). The chairperson of the forum has asked you to help with improving their ICT system.
9.1 The CPF office has three computers for administrative work. These computers have the following specifications:
- Intel Dual Core 1.2 GHz
- 1 GB RAM
- 240 GB HDD
- DVD writer
- 15'' LED screen 800 x 600
- Keyboard and mouse
- Windows 7
9.1.1 These computers are quite slow. Suggest TWO ways to improve their performance. (2)
9.1.2 The mouse on one of the computers is not working. Discuss how you would go about checking what the problem may be. (1)
9.1.3 Currently these computers cannot be networked wirelessly. Name TWO devices that can be added as components to the computers to make wireless communication possible. (2)
9.1.4 State TWO ways in which one can know that these computers are old. (2)
9.2 The CPF has decided to install a surveillance system using cameras around their office. All videos will be stored on hard drives (HDDs).
9.2.1 Explain why the CPF should purchase high-capacity hard drives. (1)
9.2.2 Suggest ONE way to manage the situation when the HDDs are full, but recording must continue. (1)
9.2.3 State TWO disadvantages of using wireless cameras. (2)
9.3 The CPF has been using social media for communication with community members.
9.3.1 Give TWO reasons why it may not be a good idea to discuss victims of crime on social media. (2)
9.3.2 Explain why it would be good to use WhatsApp for alerting residents to possible threats (2)
9.3.3 What type of software could be used to help blind residents to access the contents of text messages? (1)
9.4 Give TWO reasons why it would be a good idea for the CPF to back up their data to a cloud service. (2)
9.5 Residents' personal details have been captured in a database. The chairperson would like you to analyse this data.
9.5.1 Name TWO database features that can be used to determine the number of females who are older than 60 years. (2)
9.5.2 What is the advantage of using an input form instead of a table in Datasheet View to capture data? (1)
9.6 Study the graph on crime statistics below and answer the questions that follow.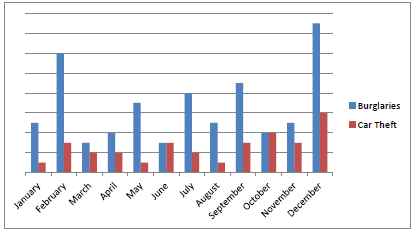
9.6.1 Suggest THREE ways to make the graph easier to understand. (3)
9.6.2 Why would a pie graph not be suitable to represent this information? (1)
[25]
QUESTION 10
Your friends are planning a trip to the Cango Caves. They need your advice on how to make their experience more enjoyable with the help of ICTs.
10.1 Your friends want to rent a car in Oudtshoorn.
10.1.1 Name a type of software application necessary to book a car on a rental agency website. (1)
10.1.2 How would you book a car on a mobile device without using the rental agency website? (1)
10.1.3 State TWO ways to pinpoint the different places you visit on your mobile device in order to view them later on a map. (2)
10.1.4 How could ICTs help you communicate with your taxi driver if he does not speak your language? (1)
10.2 Your friends might want to visit a local coffee shop on their way to the caves. You found directions to a coffee shop online.
10.2.1 State TWO disadvantages of following online recommendations as a way to find a good coffee shop. (2)
10.2.2 Give TWO technical reasons why a mobile phone payment may be unsuccessful. (2)
10.2.3 Discuss TWO ways to protect yourself from falling victim to bank card fraud at the coffee shop. (2)
10.3 Your friends will be using their smartphones in the caves.
10.3.1 Give TWO reasons why the picture quality of a smartphone camera is poorer than that of a professional camera (DSLR). (2)
10.3.2 Why can't your friends use a map app for automatic turn-by-turn directions in the caves? (1)
10.3.3 Name TWO techniques to remove unwanted parts from a photograph after it was taken. (2)
10.4 Your friends want to keep in regular contact with their families.
10.4.1 State TWO advantages of using Wi-Fi hotspots for making VoIP calls. (2)
10.4.2 Discuss TWO security issues associated with using Wi-Fi hotspots. (2)
10.4.3 Give TWO reasons why your friends should NOT consider using satellite broadband while they are travelling. (2)
10.4.4 What can be the reason for poor video quality of a Skype call if there are no issues with either bandwidth or connectivity? (1)
10.4.5 How could you access all the pictures of the trip on your friend's cloud account? (2)
[25]
TOTAL SECTION C:50
GRAND TOTAL:150