COMPUTER APPLICATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS NOVEMBER 2021
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25)
SECTION B (75)
SECTION C (50) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave an open line after EACH subquestion.
- Generally, one mark is allocated per fact; therefore, a 2-mark question would require TWO facts, etc.
- Read the questions carefully. DO NOT give more answers than the question requires as it will NOT be marked.
- All answers MUST be related to Computer Applications Technology.
- Unless otherwise specified, answers such as 'cheaper', 'slower'/'faster', etc. will NOT be accepted.
- Do NOT use brand names in your answers, unless specifically required.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are given as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1 to 1.10) in the ANSWER BOOK, e.g. 1.11 D.
1.1 Which ONE of the following options allows for data to become useful information?
- Backup
- Processing
- Communication
- Storage
(1)
1.2 … is an online income tax return service provided by the South African government to its citizens.
- e-Filing
- e-Learning
- e-Portal
- e-Government
(1)
1.3 A computer connected to the internet that has been compromised by a hacker is known as a …
- server.
- work station.
- zombie.
- firewall.
(1)
1.4 Which ONE of the following words would return a result of 4 when used with the LEN function in a spreadsheet?
- Array
- Text string
- Number
- Link
(1)
1.5 Which ONE of the following options is NOT a function of the operating system?
- Manages computer hardware
- Provides cloud storage
- Provides the user interface
- Manages the programs
(1)
1.6 … technology can assist game rangers to monitor and detect poaching activities.
- Systems
- Blockchain
- Assistive
- Drone
(1)
1.7 The … attribute in HTML specifies the distance between the border of a table cell and the text in the cell.
- cellpadding
- cell align
- cellspacing
- cell width
(1)
1.8 The date and time when a photo was taken can be found in the … of the photo.
- resolution
- metadata
- pixels
- aspect ratio
(1)
1.9 … uses special high-speed memory to store data that is frequently used to improve computer performance.
- Syncing
- Backup
- Compression
- Caching
(1)
1.10 Which communication technology enables a person to tap his/her bank card on a device to pay?
- LTE
- Wi-Fi
- NFC
- Bluetooth
(1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question numbers (2.1 to 2.10) in the ANSWER BOOK, e.g. 2.11 U.
| COLUMN A | COLUMN B |
| 2.1 A legal agreement between a software company and a user for the use of their software 2.2 A utility program that can free up space on a storage medium 2.3 The act of opening a bank account using someone else's personal details 2.4 A spreadsheet function that totals the values in a range based on a certain condition 2.5 Software that can monitor all attempts made to access your computer 2.6 A technology that tries to solve problems in the way that humans do 2.7 Data needs to be loaded into this type of memory before it can be processed 2.8 A reference found at the bottom of a page in a word processing document 2.9 Technology using radio waves to communicate with a tag attached to an object 2.10 A circuit board that may be faulty if your computer will not start up |
|
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Write 'true' or 'false' next to the question numbers (3.1 to 3.5) in the ANSWER BOOK. If the statement is true, write 'TRUE'. If the statement is false, write 'FALSE' and change the underlined word(s) to make the statement TRUE. (Do NOT simply use the word 'NOT' to change the statement.)
No mark will be awarded if FALSE is written without a correct answer.
EXAMPLES:
| QUESTION | ANSWER |
| The initial start-up instructions are stored in the ROM. | True |
| Social engineering is the study of the design of equipment for the comfort and the safety of people in a working environment. | False, Ergonomics |
3.1 An internet-based protocol for sending and receiving web pages is www. (1)
3.2 Social networks create a platform to connect groups of people with similar interests. (1)
3.3 Throttling causes certain internet services to be given priority over others. (1)
3.4 When you restore a document, the program icon will appear on the task bar and the document will no longer be displayed on the desktop. (1)
3.5 File properties can be used to view the date on which a file was accessed. (1) [5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 What is the purpose of a product key when installing software? (1)
4.2 Give TWO differences between the user interfaces of laptops and smartphones. (2)
4.3 Briefly explain TWO ways to repair a flash drive when the operating system reports that there are errors on it. (2)
4.4 All hardware in a computer require drivers to work.
4.4.1 What is a driver AND what is its main function? (2)
4.4.2 Why do you NOT have to install a driver when connecting plug-and-play devices? (1)
4.5 The SD card on your camera is full.
Which device would you use to upload the photos to your computer without connecting your camera to the computer? (1)
4.6 Health trackers are often worn by athletes and people who are health conscious.
Name TWO types of outputs a user would expect to find on his/her health tracker. (2)
4.7 You formatted a document on your computer that you wish to send to a friend. 4.7.1
Give TWO reasons why the document will sometimes not display in the way you created it on your friend's computer. (2)
4.7.2 How can you ensure that a document you create on your computer will display as you created it on someone else's computer? (1)
4.8 Give TWO reasons why the use of online applications/software has become popular. (2)
4.9 The quality of cameras on smartphones improves every year.
Explain why smartphone cameras have not made dedicated cameras obsolete yet. (2)
4.10 Give TWO reasons for using voice recognition software. (2)
4.11 State TWO possible problems associated with 3D printing. (2)
4.12 Pop-ups can suddenly appear in the browser window when browsing the internet.
4.12.1 Give TWO disadvantages of pop-ups appearing on a web page in a browser window, other than being distracting and irritating for a user. (2)
4.12.2 Why does a pop-up blocker not block all pop-ups automatically? (1)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Give TWO advantages of grid computing. (2)
5.2 Give TWO similarities between VoIP and streaming. (2)
5.3 Study the diagram below and answer the questions that follow.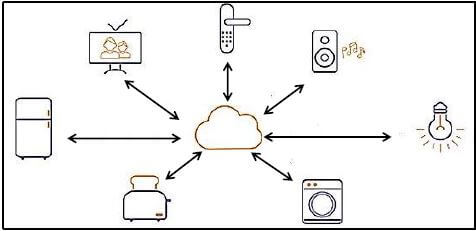
5.3.1 Name the technology that is represented by the diagram above. (1)
5.3.2 What do the arrows in the diagram represent? (1)
5.3.3 State ONE concern that could arise around the technology in the diagram above. (1)
5.4 Why would you use a browser add-on? (1)
5.5 Give ONE reason why you would adjust the home page settings in a browser. (1)
5.6 From an end-user point of view, explain TWO disadvantages of deleting the browser history and cache. (2)
5.7 Explain the concept of a cap in the context of internet access. (2)
5.8 Suggest TWO benefits of synchronising the calendar in a web-based e-mail client. (2)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Explain why it is important to use current information for research purposes and not to rely on information that is old. (1)
6.2 Give TWO possible negative effects on society as a result of research based on fake news. (2)
6.3 Discuss TWO reasons why you should NOT use blogs as sources for academic research. (2)
6.4 Surveys are commonly used to gather information.
6.4.1 Give ONE reason why you would conduct a survey instead of doing research on the internet. (1)
6.4.2 Give TWO different ways in which a survey can be done without the respondent being in the same physical place as the person who set the questions. (2)
6.5 State TWO considerations when designing a user-friendly and well-presented website. (2)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Give the term for a type of malware designed to encrypt or block access to your computer system and files until you pay a sum of money. (1)
7.2 Why do recruitment agencies check the social media accounts of jobseekers? (1)
7.3 Some free apps are not really free.
Give ONE reason to support the statement above. (1)
7.4 Explain how user-centred design (UCD) can be applied when creating an electronic form that will be used by partially sighted people. (2)
7.5 Give TWO measures to prevent cyber criminals from accessing a computer system. (2)
7.6 Study the diagram below that represents a group on social media.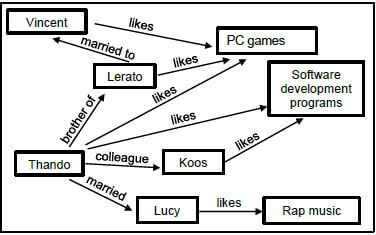
7.6.1 What is the purpose of this diagram? (1)
7.6.2 Suggest a product that could be advertised for this particular social group. Motivate your answer. (2)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Give TWO reasons why you would use the hyphenation feature in a word processing document. (2)
8.2 A diagram using five different shapes was created in a word processing document.
How would you move this diagram to a new position in the document so that it moves as one complete diagram? (1)
8.3 How would you insert ALL the text from another long document into an existing word processing document without using the copy and paste method? (1)
8.4 Study the Mail Merge Recipients dialog box below and answer the questions that follow.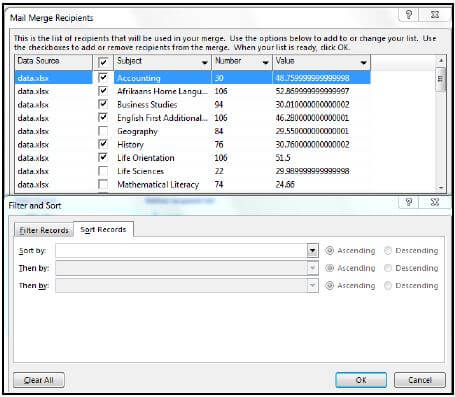
8.4.1 Explain the purpose of the 'Then by' option in the 'Filter and Sort' dialog box. (1)
8.4.2 Some records in the 'Subject' column have been excluded because they are not checked (ticked) in the 'Mail Merge Recipients' dialog box, as shown above.
Explain how you could achieve the same result without having to manually remove the ticks (uncheck) or to deselect certain check boxes. (2)
8.5 The spreadsheet window in the image does not show the full nested IF in the formula bar for cell K1, as shown below.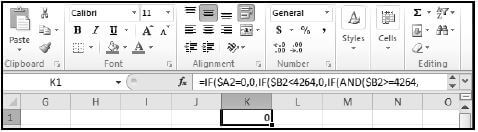
Explain TWO ways in which one would be able to see the whole function. (2)
8.6 In the image below, the cells in column D contain a function that refers to cells in column C.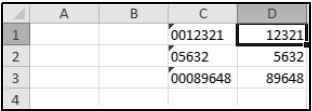
Name the function that was used in column D to display the numbers in column C without the leading zeros. (1)
8.7 Which data type in a database table is associated with the entry of a picture into a field? (1)
8.8 A field in a database table requires the input of a number in the range from 100 to 200.
Which data validation technique would you use to ensure a value entered satisfies the criteria? (1)
8.9 Describe the output of the following HTML code by referring to the shape AND the element that will be displayed on the web page:
<img src="/1.jpg" width="250" height="250"> (2)
8.10 What is the purpose of inserting a horizontal rule/line when creating a web page? (1)
[15]
TOTAL SECTION B: 75
SECTION C
QUESTION 9: INTEGRATED SCENARIO
Your school has offered to take a leading role in using ICTs to assist learners to improve their results. Learners would be able to get assistance online or physically attend classes over weekends.
9.1 The school management wishes to purchase laptops for a computer centre to be used for self-study or research purposes.
9.1.1 How will the school's IT technician install software on the laptops if the school decides to purchase laptops that do NOT have CD/DVD drives? (2)
9.1.2 Name ONE hardware specification that could be used to prevent other people from being able to access and use a laptop. (1)
9.1.3 Explain the concept of mobile learning AND why it should be included in the assistance programme. (2)
9.1.4 A data projector cannot be connected to a laptop, although both devices work perfectly.
Suggest ONE reason why the data projector cannot be connected to the laptop AND give a possible solution to address this problem. (2)
9.2 The school plans to create a spreadsheet for capturing class attendance data.
9.2.1 Which online system could the school use for learners to submit their attendance details so that teachers will automatically receive the responses in a spreadsheet? You may use a brand name in your answer. (1)
9.2.2 Suggest ONE spreadsheet feature that can be used to indicate a pattern in the attendance behaviour of the learners. (1)
9.2.3 The screenshot below shows how learner attendance for every weekend was captured in a spreadsheet.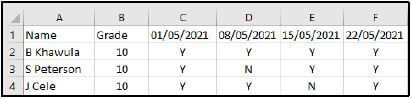
Give ONE spreadsheet function that can be used to determine the number of learners that were absent on a specific date. (1)
9.3 Give TWO reasons for setting up a network in the computer centre. (2)
9.4 Internet access will be provided in the computer centre. 9.4.1
Discuss TWO reasons why the school should use a fibre connection for internet access in the computer centre. (2)
9.4.2 State TWO ways to ensure that learners do not abuse the internet access. (2)
9.5 Teachers plan to use video conferencing to conduct online lessons with learners.
9.5.1 Name TWO hardware devices each computer must have to enable video conferencing. (2)
9.5.2 Give TWO examples of software that can be used to conduct video conferencing. You may use brand names in your answer. (2)
9.5.3 State ONE way in which learners can reduce their data usage during a video conference. (1)
9.6 The school management will need to report on the success of the intervention programme.
9.6.1 The school secretary prepared a text document in a spreadsheet program.
Give TWO reasons why a spreadsheet program is less suitable than a word processor for this task. (2)
9.6.2 Which View option in a word processor will allow the secretary to see the headings and move the cursor quickly to the position of a heading in the document? (1)
9.6.3 Give ONE word processing feature that can be used to acknowledge sources in a document. (1)
[25]
QUESTION 10: INTEGRATED SCENARIO
The school principal asks you to do research and suggest ways to reduce the impact of load shedding on the ICT equipment at the school.
10.1 When you started searching for solutions on the internet, the following message appeared: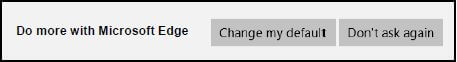
10.1.1 Explain the reason for the message to change the default browser. (1)
10.1.2 Name the operating system associated with the Edge browser. (1)
10.1.3 Give TWO ways in which you would evaluate information found on a website. (2)
10.1.4 You found a suitable website on load shedding solutions, but did not have time to read it immediately.
Which browser feature would you use so that you can access that website quickly in future? (1)
10.2 The school principal asked you to research possible UPS solutions for the computer centre during load shedding.
10.2.1 State TWO functions of a UPS. (2)
10.2.2 Explain the purpose of a two-step authentication process if the UPS is bought and paid for online. (1)
10.2.3 Give ONE example of a two-step authentication notification during online purchases. (1)
10.2.4 Name the device that must be connected to the UPS to ensure that the computer centre will have internet connectivity during load shedding. (1)
10.3 The school principal wishes to explore ways of connecting to the internet during load shedding.
10.3.1 Name the wireless technology that will allow internet access via communication towers that have battery backup. (1)
10.3.2 State TWO ways in which to verify that the school can connect to the internet via a specific connection using communication towers with a battery backup. (2)
10.4 You downloaded the power provider's load shedding schedule to see how your school and home area are affected.
Study the screenshot below and answer the questions that follow.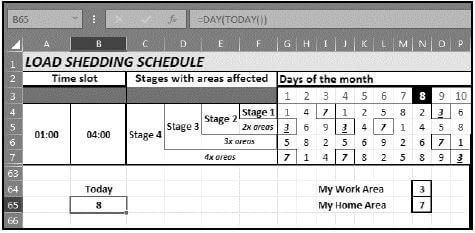
10.4.1 How is it possible that row 63 appears directly after row 7 in the screenshot? (1)
10.4.2 Explain why the content of cell B65 is NOT displayed as a date even though the formula '=DAY(TODAY())' was used. (1)
10.4.3 What spreadsheet feature could have been used to format multiple cells in the range G4:P7 all at once? (1)
10.5 Some people prefer a load shedding app that will send alerts if there are changes on the load shedding schedule.
10.5.1 Which app on your smartphone allows you to download and install more apps? You may use a brand name in your answer. (1)
10.5.2 Which technology will the app use to automatically give you the schedule for the area you are currently in? (1)
10.5.3 State TWO ways in which teachers can avoid wasting teaching and learning time when using a computer when they know when there will be load shedding. (2)
10.6 Suggest how electricity used by ICTs at your school can be reduced.
In your answer, use the following aspects:
- Hardware
- Software
- User behaviour (3)
10.7 Certain programs on the school computers need to run automatically during the day.
Which utility can be used to ensure that these programs do NOT run during load shedding times? (1)
10.8 The anti-malware program is set to update as soon as the computer centre comes online after load shedding to prevent possible infections.
Name the type of malware that tricks users into clicking on an item that hides a link to another website. (1)
[25]
TOTAL SECTION C: 50
GRAND TOTAL: 150