INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS SEPTEMBER 2016
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER TWO (P2)
GRADE 12
EXAM PAPERS AND MEMOS
SEPTEMBER 2016
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX questions:
SECTION A: Short questions (15)
SECTION B: System Technologies (24)
SECTION C: Communications and Network Technologies (26)
SECTION D: Data and Information Management (26)
SECTION E: Solution Development (22)
SECTION F: Integrated Scenario (37) - Answer ALL the questions.
- Read ALL the questions carefully.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question number (1.1.1–1.1.10) in the ANSWER BOOK.
1.1.1 A field that identifies each record with a unique value (1)
1.1.2 Performance of physical tasks, commonly repetitive or dangerous ones, by computer-controlled machines rather than by human beings (1)
1.1.3 A set of rules for encoding and decoding data for transmission across a network (1)
1.1.4 A device that makes it possible for networks to communicate over the Internet, by directing data to its correct destination (1)
1.1.5 A form of malware that tries to monitor and track the way you use your computer to discover confidential information,and then relay this to a third party (1)
1.1.6 Trend whereby separate technologies and functions from multiple devices are combined into a single multi-purpose device (1)
1.1.7 The ‘scrambling’ of text or data using a specified set of rules to ensures the privacy of data during communication, or for security purposes (1)
1.1.8 When the DBMS gets the instructions to reverse a transaction (or series of transactions) and restores the data back to its previous state (1)
1.1.9 A huge collection of data, often accumulated from a range of sources such as separate databases within a company (1)
1.1.10 A type of reasoning that works with probabilities in order to arrive at a decision (1)
1.2 Various options are given as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.2.1–1.2.5) in the ANSWER BOOK.
1.2.1 Copyrighted software provide to a user at no cost is known as …
- shareware.
- wrap ware.
- freeware.
- adware. (1)
1.2.2 Which technique allows the processor of a computer system to run at a speed faster than the motherboard normally supports?
- Pipelining
- Cache
- Hyperthreading
- Clock multiplication (1)
1.2.3 Which one of the following software items is used for developing web pages?
- SQL
- HTTP
- HTML
- CSS (1)
1.2.4 The concept of hiding the details of an object is known as …
- abstraction.
- data mining.
- modular programming.
- encapsulation. (1)
1.2.5 A/An … directly executes, i.e. performs, instructions written in a programming or scripting language, without previously compiling them into a machine language program.
- interpreter
- computer
- compiler
- programmer (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
One of your cousins is a manager at a local plant nursery, one of their computers has stopped working and after sending it for repairs he is told that the motherboard is faulty and needs to be replaced. Here are some of the specifications of the replacement motherboard.
CPU | VGA | ||
Memory | |||
Chipset | Front Side Bus | Expansion Slots | |
[Source: https://www.asus.com/za/Motherboards/P5GCMX1333/specifications/]
2.1 Explain the purpose of the motherboard, by giving THREE core functions. (3)
2.2 Refer to the System Clock and identify the highest system clock speed in the example. Answer the following questions.
2.2.1 What is the highest speed of the System Clock? (1)
2.2.2 State the relationship between System Clock and Front Side Bus. (1)
2.2.3 Which components are connected through the Front Side Bus? (2)
2.3 The CPU speed is given as being a 3.46 GHz processor, 512 MB L2 Cache and 2 MB L3 Cache.
2.3.1 Explain how the processor is able to work with the motherboard, since the motherboard speed is less than that of the processor. (2)
2.3.2 Briefly explain the purpose of cache in the processor. (1)
2.3.3 List AND explain TWO other places in the computer system where the cache is employed. (4)
2.4 You discuss with friends and one suggests that you use a tablet, and that it will do the same job, whilst the other one states that a tablets is not modular designed so it will not do the same job.
2.4.1 Are tablets modular designed? Justify your answer. (2)
2.4.2 Explain TWO advantages of modular design. (2)
2.5 One of your friends indicates that the operating system is very important for the computer system to work, and the best systems are open source.
2.5.1 State TWO functions of operating system software. (2)
2.5.2 List TWO advantage of open source software. (2)
2.5.3 List TWO disadvantage of open source software. (2)
TOTAL SECTION B: 24
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES QUESTION 3
Computers, laptops, tablets and phones need to connect in order to share data, pictures, documents and databases amongst the three plant nursery branches, one in East London, another in Port Elizabeth and this one in Mthatha.
3.1 Advise on AND define the type of network that must be set up:
3.1.1 Between the branches (1)
3.1.2 At each branch (1)
3.2 Apart from cables, you want to know what hardware will be required to set up the network at each branch. Motivate why EACH of the following items are required by briefly explaining the function of each item in a network:
3.2.1 Network interface cards (NIC) (3)
3.2.2 Switch (2)
3.3 In order to communicate amongst each other one of the managers suggests that they must use twitter or Skype.
3.3.1 Which one of the two uses VOIP? (1)
3.3.2 Expand and explain the acronym VOIP. (2)
3.3.3 Which one of the two mediums of communication mentioned, refers to a microblog? (1)
3.3.4 Define a microblog by comparing it to a blog. (2)
3.4 While researching on a certain flower plan, you visit a website and you see the following message:
| 'This site uses cookies, by clicking and continuing browsing, it means you are in agreement …’ |
3.4.1 Explain what cookies are. (2)
3.4.2 State the main advantage of using cookies as the user. (1)
3.4.3 How can you ensure/verify that that the information found on the site is reliable? (2)
3.4.4 You also discover that the site uses digital certificates. What is the purpose of a digital certificate? (1)
3.5 Sharing files online using a popular cloud storage facility has been recommended for your team by the network administrator.
3.5.1 Provide at least TWO file sharing facilities/websites available online. (1)
3.5.2 The shared folders with information usually have different permissions, depending on the user. State AND explain TWO types of permissions that can be granted to a user of a shared folder. (4)
3.5.3 Are documents saved in these shared folders safe from viruses? Explain why. (2)
TOTAL SECTION C: 26
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A database has been designed with information about the plants available in the nurseries.
4.1 The database needs to be accessible by the POS systems and other applications including the website, from all three centres but will be administered from one location.
4.1.1 Identify the appropriate type of database management system to use. (1)
4.1.2 Give an appropriate example of the database management system mentioned in QUESTION 4.1.1. (1)
4.1.3 Give TWO advantages of this type of database management system. (2)
4.1.4 Would you recommend this type of database management system for a worldwide corporation whose information changes every minute, from location to location? Substantiate your answer. (2)
4.2 Whilst discussing with the database administrator it is mentioned that the database must be data independent and data security needs to be implemented.
4.2.1 Give TWO functions of a database administrator. (2)
4.2.2 What does data independence mean? (1)
4.2.3 Give TWO advantages of data independence. (2)
4.2.4 Explain what is meant by data security. (1)
4.2.5 Suggest TWO ways of securing the data. (2)
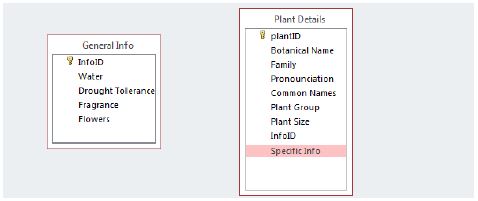
4.3 Whilst designing the database, the following tables are proposed:
4.3.1 What does the term foreign key refers to? (1)
4.3.2 Identify the foreign key field in the Plant Details table. (1)
4.3.3 An attempt to normalise the database has been made. Explain what is meant by the term normalisation. (2)
4.3.4 Name THREE common types of anomalies associated with a poorly designed database. (3)
4.4 In order to create queries SQL is being used.
4.4.1 Write a statement to show all the information from the Plant Details table. (2)
4.4.2 Write a statement that will update the botanical name called ‘Merwilla pumbea’ to ‘Merwilla plumbea’. (3)
TOTAL SECTION D: 26
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
Programs to be used in the administrative office are being developed.
5.1 The following class diagram has been designed for the plant management program.
| Plant | |
Attributes | Methods |
-fplantID:String -fplantName:String; -fBotanicalName:String; -fPrice:Real -finStock:Boolean; | +getName:String; +getBotanicalName:String; -getStock:Real; +Constructor Create(cplantID, cplantName, cBotanicalName:String,cPrice:Real) +toString:String; |
5.1.1 Explain what the (-) and the (+) signs mean. (2)
5.1.2 Identify an accessor method in the Plant class. (1)
5.1.3 What is the purpose of the constructor method? (1)
5.1.4 Would it be possible to use the class Plant without the constructor method? Explain your answer. (2)
5.2 Analyse the following flowchart. 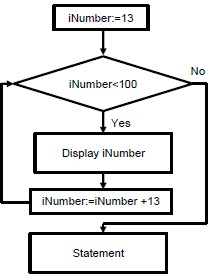
5.2.1 Identify the type of loop indicated in the flowchart diagram above. (1)
5.2.2 Identify the statement(s) that are repeated. (2)
5.2.3 How many repetitions will take place? (1)
5.2.4 What is the condition for the loop to stop? (1)
5.2.5 Write the Pseudo code described by the flowchart. Display appropriate statements where needed. (6)
5.3 Arrays will be used to store and manipulate some of the data.
5.3.1 Define an array. (2)
5.3.2 Write an example of a one-dimensional constant array declaration. (3)
TOTAL SECTION E: 22
SECTION F: INTEGRATED SCENARIO
QUESTION 6
A website showcasing the company’s services and plants has been designed. Short videos, pictures and descriptions of plants including important information about the workers are all available on the site.
6.1 The website is hosted on website hosting company’s servers.
6.1.1 Name the type of software program that can be used to access the website. Give ONE example. (2)
6.1.2 Which protocol (give full name) will be used to transmit the website data when another computer on the internet requests information from the hosting company’s server? (1)
6.1.3 The monthly bandwidth allowed by the hosting company is 10 GB. Explain what is meant by the term bandwidth. (2)
6.1.4 Will it be possible for the company to host the website on their own to avoid paying the website hosting company? Substantiate your answer. (3)
6.2 The company has hired security consultants to advise them on many security aspects to help protect them from computer criminals and theft. The company plans to use e-mail, Twitter and Facebook extensively for their marketing activities online.
6.2.1 Name THREE items of personal information that should not be posted on a social networking site. (3)
6.2.2 Explain how hackers may use your e-mail to steal your personal information. (2)
6.2.3 Give ONE name used to describe this occurrence in QUESTION 6.2.2. (1)
6.2.4 One of the managers explains that he was trolled online. What is trolling? (1)
6.2.5 What measures can the manager take to avoid trolling? (1)
6.2.6 List THREE types of computer theft. (3)
6.2.7 List THREE types of computer criminals. (3)
6.3 An app has been designed by one of the programmers you hired which will enable buyers to select the plants that they may need to put in their gardens. One of the managers claims that appification has taken over the Internet.
6.3.1 What is an app? (1)
6.3.2 Suggest TWO devices that can be loaded with this app. (2)
6.3.3 What does the term appification mean? (2)
6.4 Each nursery has a Wi-Fi network to enable the managers and workers to share work.
6.4.1 What is Wi-Fi? (1)
6.4.2 One of the managers comes to you and complains that sometimes he is connected to the Wi-Fi but does not have Internet access.
Explain how this is possible. (2)
6.4.3 Which term is used to refer to the practice of intercepting data packets on a network? (1)
6.4.4 For EACH of the following technologies, state whether it is possible to protect the nursery’s data from being intercepted and used. Give a reason for your answer in EACH case.
- Firewall (2)
- Encryption (2)
- Virus Scan (2)
TOTAL SECTION F: 37
GRAND TOTAL: 150