Computer Applications Technology Paper 2 Questions - Grade 12 September 2021 Preparatory Exams
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- Generally, one mark is allocated per fact; therefore, a 2-mark question would require TWO facts, etcetera.
- Read the questions carefully. DO NOT give more than the question requires as this will NOT be marked.
- All answers MUST be related to Computer Applications Technology.
- Answers such as ‘cheaper’, ‘slower’/’faster’ and ‘easier’ will ONLY be accepted, if they are motivated.
- Do NOT use brand names in your answers, unless specifically required.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are given as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1 to 1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 A physically disabled person who cannot use the keyboard with ease, will benefit from using this specific program/software when he/she wants to type a letter on the computer.
- Dragon Naturally Speaking
- MathPad
- Mouse skills
- CorelDraw (1)
1.2 What is the difference between upgrading of software and updating of the software?
- There is no difference, in both cases you have to go online.
- For updating software like Word, you need a license number but for upgrading it is unnecessary.
- When you update software, you probably buy a newer version and when you upgrade, you download fixes.
- When you upgrade software, you probably buy a newer version and when you update, you download fixes. (1)
1.3 Which ONE of the data types in MS Access ensures that the field serves as a primary key?
- Hyperlink
- AutoNumber
- OLE Object
- Memo/Long Text (1)
1.4 You want to use a function to search for a value that appears the most in a data range. The best function to use is:
- VALUE
- IF
- MEDIAN
- MODE (1)
1.5 Sales or holiday bookings over the Internet are known as …
- e-commerce.
- Tweets.
- VoIP.
- Ergonomics. (1)
1.6 Once data has been collected, it must be processed. A spreadsheet is an ideal tool for analysing data. Which ONE of the features mentioned below does NOT contribute to the analysis of data?
- Graphs/Charts
- Track changes
- Conditional formatting
- Functions and Formulas (1)
1.7 Which method/source would be the most suitable to use to gather information about residents’ opinions on service delivery?
- Survey
- Community (local) newspapers
- National newspapers
- Interviews (1)
1.8 The catch phrase “It’s criminal if it’s not original!” describes …
- the theft of intellectual property.
- hacking into a computer.
- software piracy.
- text encryption. (1)
1.9 Which ONE of the following is NOT a formula that is av in a Word table? ailable for calculations
- LEN
- SUM
- AVERAGE
- COUNT (1)
1.10 The overall design of an entire document including colours, fonts and effects, is known as …
- style.
- template.
- theme.
- autotext. (1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question numbers (2.1 to 2.10) in the ANSWER BOOK, for example 2.11 Q.
COLUMN A | COLUMN B | |
2.1 | The trend where separate technologies and functions that required different devices in the past are combined into a single device |
|
2.2 | It includes utility programs/software pre-installed onto your computer to help maintain the system | |
2.3 | The total amount of data transferred from one point to another within a specific time span | |
2.4 | Data identified on a website can be stored temporarily on the hard drive in a sub-directory of the browser and at the next session it is retrieved instead of opening the website via the Internet | |
2.5 | A collection of independent networked computers that act together to perform very large tasks | |
2.6 | A horizontal line, which is a little longer than a hyphen, used to express ranges and parenthetical expressions | |
2.7 | The different parts of the files can become scattered across the disk, causing the computer to become slower in retrieving the files in order to open or save them | |
2.8 | The ratio between the width and height of a screen | |
2.9 | The specification in which the speed of a printer is measured | |
2.10 | The setting on the camera for measuring the sensitivity to light | |
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write ‘true’ or ‘false’ next to the question numbers (3.1 to 3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (Do NOT simply use the word ‘NOT’ to change the statement.)
NO mark will be awarded if only FALSE is written.
EXAMPLES:
QUESTION | ANSWER | ||
Facebook is an example of a social networking website. | True | ||
A NIC has slots for hardware components such as the CPU. | False – motherboard | ||
3.1 A header is text that appears within the bottom margin of all pages in a document or file. (1)
3.2 A check box allows the user to choose only one from a given set of options. (1)
3.3 The wild card character can be used in the Find and Replace feature of a word processor. (1)
3.4 A hyperlink is a built-in connection to another related webpage or website, usually indicated as underlined text or graphics. (1)
3.5 An e-mail program may reject an attachment based on the date of the file. (1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEM TECHNOLOGIES
4.1 Every general-purpose computing device needs both RAM (memory) and storage.
4.1.1 Briefly explain the function of RAM. (1)
4.1.2 Give ONE difference between RAM and storage, besides their difference in function. (1)
4.2 Give TWO input devices that are found in a smartphone, but not in a typical desktop computer. (2)
4.3 Give TWO reasons why portable computers are increasingly being designed NOT to include optical drives. (2)
4.4 You are working with a wired mouse that suddenly ‘freezes’ (fails to respond). Assume that the mouse itself is clean and not damaged. Give TWO trouble-shooting techniques you could try to get the mouse working again. (2)
4.5 Discuss TWO ways in which a user could ensure that data is not deleted or altered by mistake. (2)
4.6 Explain why business invoices, statements etcetera. are generally converted to PDF files before they are sent to customers. (1)
4.7 Give TWO limitations of data projectors for showing computer output, compared to normal monitors. (2)
4.8 Name TWO pieces of equipment one would need for VR (Virtual Reality). (2)
4.9 State ONE example of how VR (Virtual Reality) can be used, except for gaming. (1)
4.10 The IT learners are considering constructing a drone as part of an awareness drive for new technology. A 3D printer will be used to print the parts of the drone.
4.10.1 What is a drone? (1)
4.10.2 State TWO possible benefits of using a 3D printer for printing parts of the drone. (2)
4.11 A computer game has the following hardware system requirements:
Intel i3 (or higher) |
4.11.1 Give the general function (in any computer) of the item specified as ‘Intel i3’. (1)
4.11.2 Assuming that the DVD drive will only be used to install the game, briefly explain how one could install the game on a computer that does NOT have a DVD drive. (1)
4.11.3 Give ONE other common hardware requirement, besides those listed above. (1)
4.12 State THREE advantages of SSDs. (3)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
The diagram below illustrates the network of a small business.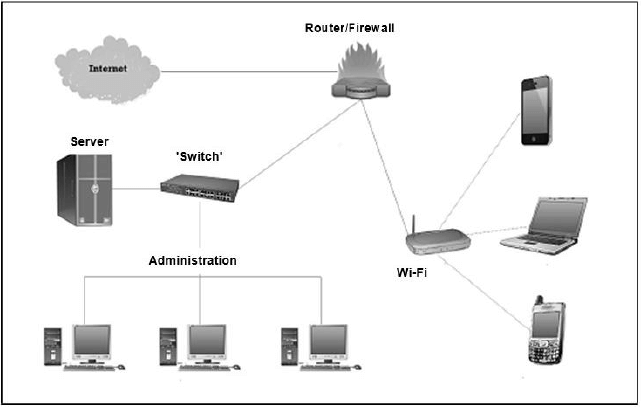
5.1 The computers in the cabled network are used by all staff members and the WLAN is used by clients.
5.1.1 Give ONE reason why a wireless network is more suitable for the clients. (1)
5.1.2 Give ONE reason why all devices must have a unique IP address. (1)
5.1.3 Give TWO possible reasons why clients using the WLAN could experience slow connection speed sometimes. (2)
5.2 The LAN in the administration office uses a client-server model and provides internet access.
5.2.1 Name TWO services that can be provided by an ISP besides the connection to the internet. (2)
5.2.2 State TWO benefits of using an ADSL connection. (2)
5.2.3 Explain the function of the switch as part of the LAN. (2)
5.3 The LAN to be used by the administration staff uses fibre-optic cables.
5.3.1 What medium is used by fibre-optic cables to transmit signals? (1)
5.3.2 Give TWO reasons why fibre-optic cables will be more suitable for use in a LAN than UTP cables. (2)
5.4 Give TWO disadvantages of FTP technology for the transfer of larger files over the internet. (2)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Refer to a formal written report, such as your PAT, and explain the purpose of a:
6.1.1 Task definition (1)
6.1.2 References (1)
6.2 When you did research for your PAT, you found some of the information on the topic appeared to be unsuitable.
State TWO indications that some of the information found may not be accurate and cannot be used in your report. (2)
6.3 Closed questions have a set of answers to choose from.
6.3.1 Discuss ONE limitation of using closed questions in a questionnaire. (1)
6.3.2 Give TWO benefits for a researcher when closed questions are answered electronically. (2)
6.4 State THREE ways in which a chart/graph can be made easier to interpret when it is included in a report. (3)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Communicating via e-mail has become the norm for society at large.
7.1.1 Give TWO indications that a received e-mail may be a possible phishing attempt. (2)
7.1.2 Give ONE possible reason as to why your e-mail program is set to block .exe files. (1)
7.1.3 Give TWO types of theft that can be committed with the aid of computers, apart from the theft of hardware and data/intellectual property. (2)
7.2 The geotagging function of modern cameras is useful for holiday-makers and tourists. Explain what this statement means by explaining what geotagging is. (2)
7.3 Give TWO potential disadvantages of e-learning when compared to the traditional classroom approach, excluding any cost factors. (2)
7.4 Give ONE indication that a message you have received is a hoax. (1)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 How do you convert an endnote to a footnote? (3)
8.2 Refer to the diagram below and answer the following question.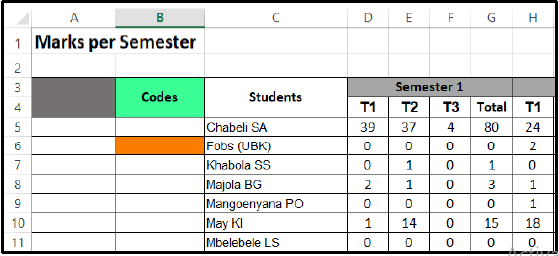
Each student needs a unique code to receive their overall final results.
Write down the function you would use in cell B6 to create a code in capital letters by using the first 2 letters of students’ names (column C). (3)
8.3 An examination session took place from 4 April 2018 to 15 April 2018. Change the properties of the ExaminationDate field in a database to ensure that only valid dates can be entered. (3)
8.4 Write down the tags used to insert a red colour horizontal line (hr/) in an HTML web page with a width of 50%. (2)
8.5 Which spreadsheet feature will systematically insert automatic numbers from 1 to 50 in consecutive rows? (1)
8.6 Name THREE possible data sources to create mailing labels in a mail merge. (3)
[15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
| Your school is launching a major drive to embrace the digital era. The expansion of their network, linked with increased Internet availability, has made it possible for them to better utilise new technologies and ICT. Apart from all the benefits, the increased use of computers and online services pose challenges in terms of providing improved hardware and educating users. |
9.1 Name TWO IT/CAT-related jobs that will be created when setting up and expanding the network. (2)
9.2 Access to the server room must be controlled. The administrative staff members use biometrics to gain access to the server room.
9.2.1 Explain the term biometrics. (2)
9.2.2 Give a suitable example of biometrics to be used in this scenario. (1)
9.3 It has been suggested that the other staff members use RFID tags to gain access to the server room.
State TWO disadvantages of using RFID tags for this application. (2)
9.4 Learners complain that their computers become very slow quickly when they open more applications. It has been suggested that they may be using too much virtual memory.
9.4.1 What is virtual memory? (1)
9.4.2 Which software implements and manages virtual memory in a computer system? (1)
9.4.3 How can the use of virtual memory be limited? (1)
9.5 A logical effect of the improvements at the school has been an increase in the use of cloud computing.
9.5.1 Cloud computing includes cloud software services, such as Office365. Explain how cloud applications work in general. (2)
9.5.2 State TWO disadvantages of using online software services. (2)
9.6 Parents/Custodians are concerned about learners’ exposure to social networking sites and cybercrime.
9.6.1 Suggest THREE ways of using social networking sites responsibly. (3)
9.6.2 Give TWO reasons why cybercrime is prevalent. (2)
9.6.3 A general crime people commit is using unsecured Wi-Fi internet connections without permission. What term is used to describe this crime? (1)
9.7 Ransomware is a type of malicious software from crypto virology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid.
9.7.1 How can you prevent ransomware attacks? (2)
9.7.2 How would you remove ransomware from your computer? (2)
9.7.3 Anonymous payment services are used for ransomware payment. Name ONE method of payment that can be used. (1)
[25]
QUESTION 10
| The local university is upgrading their library and the ICT infrastructure. The university's website can be used to check timetables and make reservations for access to the research section of the library. |
10.1 An AUP document has been compiled for the library. One of the points listed in the document states that, where possible, electronic documents should be used instead of printed documents.
10.1.1 What does the acronym AUP stand for? (1)
10.1.2 Briefly explain the purpose of having an AUP. (2)
10.2 Some of the electronic documents are stored in an online storage facility to facilitate file syncing. Explain the concept of file syncing. (2)
10.3 The university employed a web designer to redesign the website.
10.3.1 Name TWO skills that a web designer would need when creating a website. (2)
10.3.2 Students can access the website from their mobile devices. State TWO factors that a web designer must take into consideration when designing websites to be accessible from mobile devices. (2)
10.4 Some students watch videos on their electronic devices as part of research projects. The videos are saved with metadata on an SSD.
10.4.1 What is metadata? (1)
10.4.2 Suggest a suitable format for the compression of videos. (1)
10.5 Schedules for short-course lectures and webinars are displayed on the website.
10.5.1 What is a webinar? (1)
10.5.2 How can the students remain informed of changes in the schedules without visiting the website? (2)
10.6 University staff want to be sure that information sent over the network will be safe and secure. Encryption will be used to secure the data.
10.6.1 Explain what the term encryption means. (2)
10.6.2 A yellow lock is displayed on the URL bar when the user opens the university’s website.
What other visual indication is displayed that indicates that the website is secure, besides the yellow lock? (1)
10.6.3 When a user clicks on the yellow lock, the following dialogue box is displayed: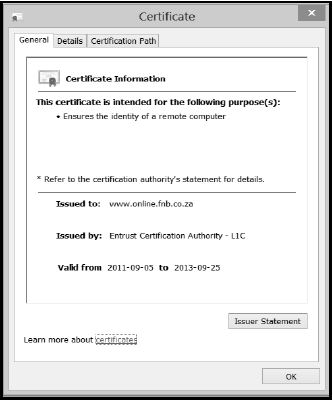
Which TWO pieces of information on the certificate can be used to verify that the website is legitimate? (2)
10.7 Staff members are often warned against social engineering.
10.7.1 Explain what social engineering is. (2)
10.7.2 What is a consequence of falling victim to social engineering? (2)
10.8 Green computing has become a focal point in the ICT field.
Suggest any TWO initiatives for the library to implement green computing. (2)
[25]
TOTAL SECTION C: 50
GRAND TOTAL: 150