Information Technology Paper 2 Grade 12 Memorundum - NSC Past Papers And Memos September 2020 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupMEMORANDUM
SECTION A: SHORT QUESTION
QUESTION 1
1.1
1.1.1 Constructor (1)
1.1.2 Composite keys (1)
1.1.3 Bus (1)
1.1.4 Digital Divide (1)
1.1.5 Utility Software (1)
1.1.6 Bandwidth (1)
1.1.7 Identity theft (1)
1.1.8 Core (1)
1.1.9 Outsourcing (1)
1.1.10 RIA (Rich Internet Application) (1)
1.2
1.2.1 A – 2579 (1)
1.2.2 C – 15 (1)
1.2.3 C – Interpreter (1)
1.2.4 B – Click farms (1)
1.2.5 B – Delimiter (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1
2.1.1 Any ONE:
- Refers to operating systems on mobile devices that are designed to keep the device on and working at all times – even when the display is dark.
States that mobile technology is never off, it is always working in the background. (1) - Smartphone
Tablets (2) - Any ONE:
- It makes mobile devices fast and responsive.
- It makes them seem smart and intuitive. (1)
2.1.2
- Wearable refers to devices that you wear on your body instead of carrying them around in a pocket or bag. (1)
- Any TWO:
- Goggle Glass
- Apple Watch / Smart watch
- Pebble/Gear smartwatches (2)
2.2
2.2.1 We want them to perform at their best and deliver results we can rely on. (1)
2.2.2
- Security
- Saving time
- Reliability (3)
2.2.3
- Keep your software installation CD/DVD/download in a place where you can easily find and access them (NOT in a folder on your hard drive, but on some removable storage).
- Make sure you have records of all your license keys and serial numbers / Keep printouts of this information (License keys and serial numbers).
- Make sure you follow a good backup policy and know how to restore your data (3)
2.2.4 A firewall is the hardware or software that monitors which applications are using the communication link and which communication ports are being used.
Any ONE function:
- Checks and changes settings for individual applications and control access to specific ports.
- Restricts computer’s communication to the most common settings. (2)
2.3
2.3.1 Any ONE:
- The disk is fragmented when files are broken up into several pieces and stored all over the disk/storage device.
- The disk is fragmented when the files are scattered all over the disk/storage device. (1)
2.3.2 It takes the computer longer to read files from/write files to a fragmented disk. (1)
2.3.3 Disk defragmentation is the task of running a special software that re- arranges the files on the disk so that the files are stored in sequence. (1)
2.4
2.4.1 Any TWO tips:
- Install only ONE anti-virus product.
- Set the software to download new virus definitions automatically.
- Set the software to scan removable drives automatically when they are plugged in.
- Set your software to scan your entire computer automatically at least once a week. (2)
2.4.2 Any TWO tips:
- Use different passwords for different accounts
- Make your passwords long
- Avoid passwords that can be found in a dictionary
- Avoid personal information about yourself or your family (2)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1
3.1.1 Any THREE permissions
- Read – allows a user to only read or copy a file or folder.
- Write – allows a user to write to and modify the contents of a file or folder.
- Execute – allows a user to view and access a folder and file’s content as well as to execute/run the program file.
- List Folder Contents – allows the listing of files and subfolders in a folder.
- Modify – allows the reading, writing and deletion of files and folders.
- Full Control – allows reading, writing, changing and deleting of files and folders. Also allows you to add, change and remove access permissions for users. (3)
3.1.2 Administrators
Any ONE explanation
- They have full control over the system.
- They can install software and hardware drives.
- They create and modify new user accounts and groups and reset passwords.
- They have full access to all the files and folders.
Standard users
Any ONE explanation
- They are permitted to log on to the computer, run programs, customise their accounts.
- Work with files in their user folders or in those common folders to which they have been granted access.
- They can change their own passwords but not those of others.
- They are restricted from making system changes. (4)
3.2
3.2.1
- BitComet
- uTorrent (2)
3.2.2
- Seeders refer to people who are sharing the file in BitTorrent processing.
- The more seeders a torrent has, the faster you are likely to able to download the file. (2)
3.3
3.3.1 Remote controlling a computer – allows you to control a computer (from anywhere in the world) as if you are sitting in front of it. Virtual Private Network (VPN) – allows you to log on to a network from a remote location via the Internet. (4)
3.3.2 Third party remote access/control software:
Any TWO
- TeamViewer
- LogMeIn
- GoToMyPC (2)
3.4
3.4.1 Digital signature is an electronic signature that is used to identify the sender of a message or signatory/signer of a document.
Any ONE function:
- It provides proof to the recipient that the file or email comes from the person who claims to have sent it.
- It verifies the data has not been altered/changed in any way since the moment it was signed. (2)
3.4.2
- Thawte
- Verisign
Accept any other verifiable CA. (2)
3.5
3.5.1 Appification is the trend for information to be accessed via dedicated apps on mobile devices. (1)
3.5.2 Any THREE reasons
- An app’s interface is easier to navigate.
- An app has a dedicated purpose and does not result in distraction and loss of focus.
- With an app you do not have to remember the URLs or manage menus of bookmarks to get where you want to go.
OR
- The app knows where to find its data and does not need to be directed by you.
- All the interface data (pictures, layout etc.) is already installed on your device as part of the app and does not need to be downloaded.
- Apps can be set to fetch data on their own in the background, even when you are not using them and also notify you automatically of significant changes or events.
- Apps can work with a syncing service.
- Apps can use additional sensors in your mobile device (e.g. GPS, compass, accelerometers etc). (3)
3.6 The Internet of Things/IoT (1)
3.7
- Local storage – data is stored on the user’s computer/local hard drive.
- Online storage – data is stored on the web server. (4 ÷ 2) (2)
TOTAL SECTION C: 28
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1 DBMS is the software that allows you to work with electronic databases. (1)
4.2 Transaction refers to any activity regarding the creation, loading, editing, saving or deleting of data managed by a DBMS. (1)
4.3
- Commit/Post – occurs when the DBMS gets the instruction to save whatever changes have been made back to storage.
- Purge/Consolidate – removes deleted records from the database to compact and streamline the file. (2)
4.4
- The unnecessary repetition of data across multiple fields in a database, which can lead to update anomalies.
- The intentional duplication or distribution of the database across multiple storage media to ensure that the data will always be available and accessible even if one storage medium fails OR Mirroring the database. (2)
4.5
4.5.1 Parallel data set is a technique whereby multiple copies of data are kept.
- It is used immediately, resulting in no downtime when there is data failure. (2)
4.5.2 Doubling the storage requirements for the system. (1)
4.5.3 For safety and security. (1)
4.6
- Overflow is an error condition that occurs when there are not enough bits available to represent an integer value accurately.
- Truncation is the misrepresentation of a string variable because there are not enough bytes available to store all the characters in the string. (2)
4.7
4.7.1 Any ONE:
- To ensure that there is no redundant data.
- To ensure that data is not being repeated in one way or another.
- To ensure that there is no duplication of data.
- To ensure that a database is in an optimal state, with no chance of anomalies. (1)
4.7.2
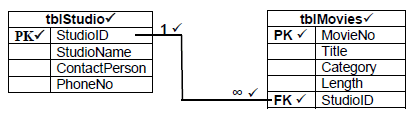 (7)
(7)
4.7.3
 (4)
(4)
TOTAL SECTION D: 24
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Try / Except (1)
5.1.2 Any ONE:
- Bug
- Exception (1)
5.1.3 Step-and-watch refers to a debugging facility in Delphi used to control execution of the program and view the values of variables while the programming code is executed. (2)
5.1.4 Trace table (1)
5.2
5.2.1 Data structure refers to the way data is organised.
- Arrays and Text files (3)
5.2.2 Arrays (1)
5.2.3
- 18 (1)
- 9 (1)
- I just L (1)
- VE Delphi (1)
- VEXTRA Delphi (1)
5.3
5.3.1 Constructor is a method used create an object in memory and to initialise the properties/private fields of an object. (2)
5.3.2 Free OR Destroy (2)
5.4
Line No | Value1 | Value2 | Value3 | Value4 | Value5 | Screen Output |
1 | 9 | |||||
2 | Solution | |||||
3 | 12 | |||||
4 | 6 | |||||
5 | 6 | |||||
6 | 48 | |||||
7 | 54 | |||||
8 | 0 | |||||
9 | 3 | |||||
10 | 3 | |||||
11 | 54 |
(12 ÷ 2) (6)
TOTAL SECTION D: 24
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1
- Any ONE
- E-waste refers to broken, outdated and discarded hardware that we neither want nor need.
OR - E-waste is anything electronic or related to electronics that is thrown away. (1)
- E-waste refers to broken, outdated and discarded hardware that we neither want nor need.
- Any THREE
- Old computers
- Old CRT monitors
- Broken hard drives
- Dead or unwanted cellphones
- TVs
- Gaming devices
- Batteries (3)
- Any TWO
- Cancer
- Pollution
- Causes radiation
- Poison water
- Damage living things that come into contact with them
- Contamination (2)
- Poisonous parts are removed properly before the materials get put into the dump site. (1)
6.1.2 Green computing refers to initiatives to design, use and dispose of technology in an environmentally or eco-friendly way. (1)
6.2
6.2.1
- Spammer refers to someone who sends out unsolicited / unasked- for/unwanted e-mails in the form of advertisements. (1)
- Any ONE
- Spam clogs the Internet with a lot of unnecessary traffic (impacts on speed).
- It also wastes time because you have to sift through so much junk in inbox. (1)
- Any ONE
- Use a spam filter in your e-mail client program.
- Avoid entering your e-mail address into website forms. (1)
6.2.2
- There is low risk of physical danger (They are not physically present when they commit the crime).
- It is difficult to detect the crime.
- It is difficult to trace who committed the crime. (3)
6.2.3 Malware / Virus (1)
6.2.4 Zombie PC (1)
6.3
6.3.1
- Decision Support Systems (DSS)
- Expert systems / Knowledge-based systems (2)
6.3.2 Any THREE
- Genetic research
- Weather modelling and climate prediction
- Physics research (e.g. nuclear research)
- Circuit design
- Financial modelling
- Web searching / indexing (3)
6.3.3 Any ONE
6.4
6.4.1 Any TWO
- Turn off notifications on your mobile device when you are busy.
- Only enable them for a limited group of people.
- Set aside specific time for engaging with social media.
- When doing important work, switch off your phone or put it on silent and disable vibrate option.
- Try to remove yourself from FOMO (Fear of Missing Out) phobia. (2)
6.4.2 Any TWO
- The Internet never forgets.
- The Internet is a public space.
- You cannot be sure how your information/uploads are going to be shared.
- The personal information you share today/now might come back to haunt you in future.
- There is nothing stopping anyone who can access what you have shared from copying it, saving it or sharing it in other places. (2)
6.5 Transaction Processing System (1)
6.6 Software as a Service refers to the concept of renting software instead of buying a license to use it forever. (1)
6.7 Any TWO places
- DRM (Digital Rights Management)
- ATM
- Internet browsers
- Skype calls
- Online storage services (2)
6.8 Backdoor is a hidden way to gain access to a computer, system or software. (1)
6.9
- Skimmer reads the electronic details from a card.
- Video camera records your PIN/password. (2)
6.10 Any TWO effects
- Decreased discretionary spending (we spend a lot of money on things to make us safer).
- Decreased productivity (time that could be spent on productivity is wasted on preventing crime).
- Increased social stratification (it separates different social classes from each other).
- Development of a culture of fear and suspicion. (2)
TOTAL SECTION F: 36
GRANDTOTAL: 150