Information Technology Paper 2 Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (23)
SECTION C: Communication and Network Technologies (28)
SECTION D: Data and Information Management (24)
SECTION E: Solution Development (24)
SECTION F: Integrated Scenario (36) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Give the correct computer term for each of the following descriptions. Write only the term next to the question number (1.1.1–1.1.10) in the ANSWER BOOK.
1.1.1 A method in object-oriented programming used to build an object in memory (1)
1.1.2 The combination of more than one field to uniquely identify a record (1)
1.1.3 A set of electrical paths etched on the motherboard, used to transfer data between different parts of a computer (1)
1.1.4 The gap between people that have access to computers and technology and people that do not (1)
1.1.5 Programs that are part of the system software and maintenance and administrative tasks (1)
1.1.6 Total amount of data that can be transferred from one point to another in a given period of time (1)
1.1.7 The type of crime when someone steals your details in order to pretend to be you (1)
1.1.8 A single complete working CPU circuit (1)
1.1.9 Contracting specialist businesses to run aspects of your own business that are essential for proper functioning, but do not fall within your own area of expertise (1)
1.1.10 A web application that is designed to deliver the functions and features of a traditional desktop application (1)
1.2 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.2.1–1.2.5) in the ANSWER BOOK, for example 1.2.6 D.
1.2.1 The conversion of hexadecimal number A13 to a decimal number is …
- 2579.
- 2560.
- 2563.
- 2576. (1)
1.2.2 What will the value of iNum be when the following statement is executed?
iNum := 7 + 5 * 9 div 3 – sqrt(49);
- -7
- 6
- 15
- 9 (1)
1.2.3 Software that translates programming instructions into machine code one line at a time is called …
- compilers.
- coding.
- interpreters.
- translator. (1)
1.2.4 … refer to businesses that use groups of low paid workers whose work is to repetitively click on links to fake high web traffic.
- Mediated searches
- Click farms
- Context-ware searches
- Customised searching (1)
1.2.5 A sequence of one or more characters used to specify the boundary between separate independent regions in plain text is called …
- separator.
- delimiter.
- limiter.
- grouping. (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
The reality is that there is no single specification that determines the speed or performance of a computing device. Instead, a whole lot of different components and specifications all play a role in determining the overall performance of the machine.
2.1 In today’s modern times, mobility and portability have become the norm in terms technology.
2.1.1 Mobile technology is driven by ease of access, user experience, the need, the desire to be always on and always connected.
- What does the always on concept mean in terms of technology? (1)
- List TWO devices that have the always on technology. (2)
- Why is the always on an advantage in mobile devices? (1)
2.1.2 If you had to carry around multiple devices, no matter how powerful they are, you would become irritated and frustrated because you would be overloaded with devices and forget to bring the device you need.
- Briefly explain the concept wearable technology. (1)
- List TWO examples of wearable devices. (2)
2.2 Things tend to decay and descend into chaos when you just leave them to themselves – this also applies to computing devices and data. The simple answer to this problem is that we need to manage our computing devices.
2.2.1 Briefly explain in simple terms the importance to manage our computers. (1)
2.2.2 List the THREE important factors that drive or influence computer management. (3)
2.2.3 Name THREE things you need to do, which will assist you quickly and economically to rebuild a system, if your hard drive crashes. (3)
2.2.4 It is essential to have a firewall when using the Internet. Explain what a firewall is and what function it performs. (2)
2.3 Study the following dialogue box and answer the questions below.
2.3.1 What do we mean when we say the disk is fragmented? (1)
2.3.2 Why does a fragmented disk slow down a computer? (1)
2.3.3 Explain the concept disk defragmentation. (1)
2.4 There are lots of campaigns done by banking industries and the government about a variety of methods to deal with scams and malware.
2.4.1 Give TWO general tips related to the use of anti-virus software. (2)
2.4.2 Mention TWO items or points that should be included in a good password policy besides changing passwords on a regular basis. (2)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
Connecting devices in a network brought a whole new dimension to the use of computers and technology.
3.1 Configuring a network covers a wide range of concepts – from choosing or buying hardware and software, to planning and implementing user rights and permissions.
3.1.1 List and briefly explain THREE different permissions that can be granted in a network. (3)
3.1.2 There are two main groups of users on a network. List and explain the TWO main groups of users on a network and the role played by each group. (4)
3.2 BitTorrent is a peer-to-peer protocol used to transfer and share large files across a network such as the Internet. To use a BitTorrent you need to install a client software.
3.2.1 List TWO examples of BitTorrent client software. (2)
3.2.2 Briefly explain the concept seeders and describe the role played by seeders in BitTorrent. (2)
3.3 Remote access technology is divided into TWO groups.
3.3.1 List and briefly explain TWO groups of remote access technologies. (4)
3.3.2 List TWO third-party software used by ONE of the groups. (2)
3.4 When the usage of the Internet expanded to include e-commerce, anonymity became a huge problem. Solutions had to be found that would allow users to trust businesses, banks etc. Digital certificates and digital signatures are the solutions currently in use.
3.4.1 Briefly explain what a digital signature is and the function it performs. (2)
3.4.2 Give TWO examples of Certificate Authorities (CAs) tasked with issuing digital certificates. (2)
3.5 A consequence of appification is that browsing and browser-based discovery of sites is decreasing and search engines are struggling to make money because of appification.
3.5.1 Explain what appification is. (1)
3.5.2 Give THREE reasons why the apps have become so popular on mobile devices. (3)
3.6 What is the term used to describe the concept that more and more devices, objects are being connected to the Internet, with the ability to communicate with other devices and objects and to take intelligent decisions based on the input received. (1)
3.7 Name the TWO web data storage models and briefly outline the main difference between these two models. (2)
TOTAL SECTION C: 28
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
Traditionally, data was organised in file formats. DBMS was a new concept then, and all the research was done to make it overcome the deficiencies in the traditional style of data management.
4.1 Briefly explain what a DBMS is (the meaning of the acronym is not required). (1)
4.2 Briefly explain the concept transaction. (1)
4.3 Distinguish between Commit/Post and Purge/Consolidate. (2)
4.4 Data redundancy covers two concepts. Briefly describe these two concepts. (2)
4.5 Parallel data set is a buzzword associated with databases.
4.5.1 Explain what a parallel data set is and what it is used for. (2)
4.5.2 Give the main disadvantage of implementing parallel data sets. (1)
4.5.3 Why should a parallel data set be kept in separate places? (1)
4.6 Differentiate between overflow and truncation. (2)
4.7 A database table has been setup containing details about all the movies and studios.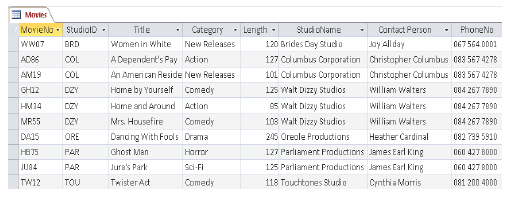
4.7.1 The table is not normalised. What is the general aim of normalisation in a database? (1)
4.7.2 Normalise the above table (Movies). Indicate the primary keys and foreign keys for each table. Create the relationship between tables. (7)
4.7.3 Use the tables in QUESTION 4.7.2 to design an ER diagram and show the relationship that exist between entities. (4)
TOTAL SECTION D: 24
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
| A common problem-solving method among programmers is to break a large problem into a series of smaller problems and then to solve each of the smaller problems. |
5.1 Computers, however, cannot make mistakes. Mistakes are made by humans. The user of the program either enter incorrect or invalid data or the programmer did not write programs with built-in measures to handle invalid operations or the correct logic was not applied when writing the programming code.
5.1.1 What is the programming tool called that allows the programmer to control how a program responds to abnormal or erroneous data and allows the program to continue running by building in a code to solve the error? (1)
5.1.2 What is another name of an error in programming called? (1)
5.1.3 Define the concept step-and-watch in programming. (2)
5.1.4 What is a tool called that is used to identify logical errors, by working through the program manually step by step and recording the results of each step in a table? (1)
5.2 All programming languages have structures available to store data.
5.2.1 Explain what a data structure is and give TWO examples of data structures. (3)
5.2.2 Which example of data structure in QUESTION 5.2.1 is classified as a temporal data structure? (1)
5.2.3 Write the output of the following program statements:
Var
Name, sLine : string;
Long, iPos : integer;
sLine := ‘I just LOVE Delphi’;
- Long := Length(sLine); (1)
- iPos := POS(‘O’, sLine); (1)
- Name := COPY(sLine, 1, iPos-1); (1)
- DELETE (sLine, 1, iPos); (1)
- INSERT(‘XTRA’, sLine, 2); (1)
5.3 UML is designed to help plan and design classes and objects. It is a powerful and complex modelling tool. A class diagram is one of the UML tools which is divided into three sections (class name section, attributes section and methods section).
5.3.1 Explain the purpose of a constructor in classes and objects. (2)
5.3.2 To remove the object from memory, we use the keyword:
ObjectName. .......................................... OR ObjectName. .................................................... (2)
5.4 Study the following code and answer the question that follows:
procedure TForm1.btnEnterValuesClick(Sender: TObject);
var
Value1, Value2, Value3, Value4, Value5 : integer; begin
- Value1 := 9;
- redOutput.Lines.Add('Solution');
- Value2 := StrToInt(InputBox('Enter Number','Enter an integer value.',''));
- Value3 := StrToInt(InputBox('Enter Number','Enter an integer value.',''));
- Value5 := Value1 - (Value2 - Value3) DIV 2;
- Value4 := 4 * Value2;
- Value2 := Value4 + Value5;
- Value3 := Value2 MOD 3;
- Value1 := (Value5 DIV 2) + (Value3 * Value3);
- redOutput.Lines.Add(IntToStr(Value1));
- redOutput.Lines.Add(IntToStr(Value2)); end;
Copy the trace table provided below into your ANSWER BOOK and complete to determine output. Assume that 12 and 6 are entered in an inputbox as Value2 and Value3 respectively.
Line No | Value1 | Value2 | Value3 | Value4 | Value5 | Screen Output |
1 | ||||||
2 | ||||||
3 | ||||||
(12 ÷ 2) (6)
TOTAL SECTION E: 24
SECTION F: INTEGRATED SCENARIO
QUESTION 6
| ICT has revolutionised the way in which people use media to communicate socially. ICT has changed the workplace in terms of employment practices and the physical nature of the space. |
6.1 Electronic devices become increasingly smart and versatile, security cameras that previously supplied raw video data are now also able to analyse data. This enables you to alter your product ranges.
6.1.1 It is fair to say that every human activity has some greater or lesser impact upon the environment. Reasonably this means that ICT also has an environmental impact.
- Explain the term e-waste. (1)
- Name THREE typical examples of e-waste. (3)
- Give TWO reasons why e-waste is dangerous to the environment. (2)
- Be responsible and recycle your used equipment. Briefly explain what happens in the recycling process. (1)
6.1.2 Preserving power is another form of encouraging green computing. Briefly explain the term green computing. (1)
6.2 Computer criminals always seem shrouded in mystery and cloaked with some sort of cyber-superpower. In movies and on television they are able to do amazing things with just a few lines of code or magical mouse clicks and they always seem to be able to keep one step ahead of the law.
6.2.1
- Explain what a spammer is. (1)
- Briefly explain why spam is a problem except that is regarded as annoying. (1)
- List TWO tips that can be applied to avoid spam. (2)
6.2.2 Cyber-crime is any crime committed by using ICT as a tool. Name THREE advantages to the criminals of using ICT as a tool to commit crime. (3)
6.2.3 What do criminals use to control computing devices to commit crime? (1)
6.2.4 What is the name of the computer that is compromised in a network used to commit crime? (1)
6.3 Computers are essential tools in managing projects of national and international importance for government, academic research and business enterprises.
6.3.1 Name TWO computer-based systems that can help us to make informed decisions. (2)
6.3.2 Name THREE general applications for distributed computing. (3)
6.3.3 Name a specific example of distributed computing in practice. (1)
6.4 Concentration is a valuable asset. You need the ability to focus if you are to work effectively, be productive and achieve your goals.
6.4.1 Explain TWO advices/tips that you can apply to manage social networking to improve your concentration and make you more productive. (2)
6.4.2 Almost all social networking tools, sites and apps encourage you to share information. The problem is that you are encouraged to share and you are told of the benefits of sharing but you are not made aware of the possible negative consequences. Name TWO things you need to be aware of before publishing or sharing information on the Internet. (2)
6.5 People keep discovering new ways to extract information from databases and new ways to store and process data. What does TPS stand for? (1)
6.6 Describe the concept Software as a Service. (1)
6.7 Automatic encryption is something that happens without you consciously choosing to use the software to encrypt data. Name TWO places where automatic encryption is used. (2)
6.8 Hackers may steal data either because they want to sell it or they want to use it themselves or to blackmail someone. Explain the concept backdoor in terms of theft of data. (1)
6.9 Criminals place a skimmer and a video camera on an ATM machine. Explain the purpose of the skimmer and a video camera in this context. (2)
6.10 The way we behave and the things we do change the way in which society operates. When crime changes our behaviour and habits, it has a set of consequences on how our society operates. Name TWO effects or societal consequences of cybercrime. (2)
TOTAL SECTION F: 36
GRAND TOTAL: 150