Computer Application Technology Paper 2 Grade 12 Questions - NSC Past Papers And Memos September 2020 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH sub-question.
- Generally, one mark is allocated per fact. A 2-mark question would therefore require TWO facts, etc.
- Read the questions carefully and do NOT give more information than the question requires as this will NOT be marked.
- All answers MUST be related to Computer Applications Technology.
- Answers such as ‘cheaper’, ‘slower’/’faster’, ‘easier’, etc. will ONLY be accepted, if they are motivated.
- Do NOT use brand names in answers, unless specifically required.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1–1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 An USB port is used to connect peripherals to a computer. If you have a limited number of USB ports you can use an USB … to extend the number of ports.
- hub
- flash disk
- extension cable
- modem (1)
1.2 Which keys should you press to open Task Manager?
- Alt + Ctrl
- Ctrl + Alt + Enter
- Alt + PrtScr
- Ctrl + Alt + Del (1)
1.3 Which ONE of the following combinations of spreadsheet functions will display a code in capital letters of the last 3 letters of a name?
- CAPITAL
- UPPER
- LEFT
- RIGHT
- (ii) and (iv)
- (ii) and (iii)
- (i) and (iv)
- (iii) and (iv) (1)
1.4 ... refers to an injury that can occur from the continuous use of an input device such as a keyboard.
- CPU
- RSS
- RFID
- RSI (1)
1.5 ... is an example of an e-commerce website.
- Spotify
- eBay
- iCloud
- YouTube (1)
1.6 A(n) … is NOT an example of malware.
- trojan
- ad-blocker
- worm
- keylogger (1)
1.7 Which ONE of the following devices would be used to provide an emergency supply of electricity in the case of a power failure?
- Surge protector
- Power Supply Unit
- UPS
- Router (1)
1.8 Which one of the following is an example of secondary memory?
- RAM
- ROM
- Printer
- Memory Card (1)
1.9 A reason why a webcam would NOT be suitable to take pictures or photographs at a prestigious event such as a prize-giving.
- Face-to-face communication
- High costs
- Low video quality
- Inadequate storage (1)
1.10 To print all comments and changes made in a document, the following must be enabled in the Print dialog box.
- Print Selection only
- Only Print even pages
- Print Mark-up
- Scale to Paper size (1) [10]
QUESTION 2: MATCHING COLUMNS
Choose a term/concept from COLUMN B that matches a description in
COLUMN A. Write only the letter (A–P) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 Q.
COLUMN A | COLUMN B | ||
2.1 | A program that searches the Web for web pages relevant to the keywords or phrases entered by the person looking for information | A | Shaping |
2.2 | A process where a project is funded by multiple small donations from many contributors | B | Driver |
2.3 | An example of a popular, free, online office suite | C | VPN |
2.4 | A communication technology that requires a pairing process | D | Disk Cleanup |
2.5 | A technique used by ISPs to prioritise some services | E | FTP |
2.6 | Protocol for sending large files via Internet | F | PPM |
2.7 | A file type including both audio and video content | G | MP4 |
2.8 | A device that can be used to store data permanently | H | Podcast |
2.9 | Software that allows a computer to communicate with hardware or devices | I | LTE |
2.10 | An utility that can be used to make more storage space available by deleting unnecessary files | J | Internet |
K | Search engine | ||
L | Bluetooth | ||
M | SSD | ||
N | Pop-ups | ||
O | Google Docs | ||
P | Crowd funding | ||
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEM
Indicate whether the following statements are TRUE or FALSE. Write ‘true’ or ‘false’ next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word ‘NOT’ to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
QUESTION | ANSWER | |
Google is the world’s most popular search engine. | True | |
A NIC has slots for hardware components such as the CPU. | False – motherboard | |
3.1 Application software controls and manages resources on a computer. (1)
3.2 A hotspot is an area where you can obtain wireless access to the internet. (1)
3.3 OCR software is used to convert scanned images of text into text that can be edited in a program such as a word processor. (1)
3.4 Phishing redirects users to false web sites without them even knowing it. (1)
3.5 Add-on software, such as flash players, extend the capabilities of a browser. (1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEM TECHNOLOGIES
4.1 An operating system is the most important software that runs on a computer. It allows you to communicate with the computer.
4.1.1 One of the key functions of an operating system is to manage memory. Why is this such a crucial function? (2)
4.1.2 Give TWO examples of how an operating system provides us with a basic level of security. (2)
4.1.3 Utilities form part of system software. What is the function of utilities and what is the ‘relationship’ between utilities and the operating system? (2)
4.2 You received a ‘zipped’ file as an e-mail attachment and you have scanned it for viruses and it seems to be ‘safe’.
4.2.1 Do you need special software to create a ‘zipped’ file? Briefly motivate your answer. (2)
4.2.2 What is the most common reason to zip a file which you are sending as an e-mail attachment? (2)
4.3 A computer advert advertises a CPU with a ‘cache memory’ size of 8192KB. Explain what ‘cache memory’ is and why it can improve the overall
performance of a computer. (2)
4.4 Study the advertisement of a laptop below:
- 13.3 inch FHD LED Display
- Intel Core i7 8565U Processor
- 16 GB RAM
- 512 GB SSD
- Intel® UHD Graphics 620
- Windows 10 Home
- 3 Year Warranty (Upon Registration)
4.4.1 Explain what each display specification in the first line of the advert refers to. (3)
4.4.2 What is the size of the memory and storage respectively? Make a clear distinction between the TWO concepts you are referring to. (2)
4.4.3 Is Windows 10 a proprietary or an open source operating system? (1)
4.4.4 Name the specific port that the laptop should have to enable the user to connect to the following:
- A data projector (1)
- An external hard drive (1)
4.4.5 State ONE reason for choosing an SSD instead of a HDD. (1)
4.5 State TWO advantages of using HDMI technology instead of VGA technology.(2)
4.6 State TWO ways in which a user could install software on a computer that does not have an optical drive.(2)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 State TWO factors that should be carefully considered when choosing an ISP (internet service provider), other than cost. (2)
5.2 Give TWO limitations of using an ADSL connection. (2)
5.3 Study the internet connection package advertised below and answer the questions that follow.
| 30 GB data per month Shaped |
5.3.1 Would you describe the above package as ‘capped’ or ‘uncapped’? Motivate your answer. (2)
5.3.2 Give the common term used when an Internet Service Provider slows down your internet speed when you download huge amounts of data. (1)
5.3.3 Give TWO factors (besides the one in QUESTION 5.3.2) that can influence Internet speed. (2)
5.4 Learners may be click-jacked when browsing a social media website. Explain the term click-jacking. (2)
5.5 Name the type of internet connection that uses light for data transmission. (1)
5.6 Many companies use video conferencing to communicate with each other over a network.
5.6.1 A person regularly experiences poor picture quality in video conferencing (the picture keeps ‘breaking up’). Suggest TWO long-term solutions for this problem. (2)
5.6.2 Briefly explain what the term bandwidth means. (1)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Explain why using an online questionnaire is an effective option for gathering data, by referring to:
- Data capture
- Data processing (2)
6.2 What is the difference between a survey and an interview? (2)
6.3 What does the term ‘information overload’ refer to? (1)
6.4 How will you know that a web page is authentic and reliable for use in research?(2)
6.5 Give TWO potential advantages of using queries instead of filters in a database.(2)
6.6 Explain why a bibliography should be added to a research report. (1)
[10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Explain how a blog differs from a vlog. (2)
7.2 Big Data is very large structured and unstructured data sets that are analysed using computers to reveal trends and patterns.Discuss TWO skills required by people who wish to follow a career in Big Data.(2)
7.3 When you buy and/or install new software an EULA agreement must be accepted. What is the purpose of this agreement?(2)
7.4 Give TWO potential disadvantages of e-learning, experienced during the COVID-19 pandemic, when compared to the traditional classroom approach, excluding any cost factors.(2)
7.5 Describe the function of virtual assistant software. (2)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 How do you convert an endnote to a footnote? (3)
8.2 Refer to the diagram below and answer the following question.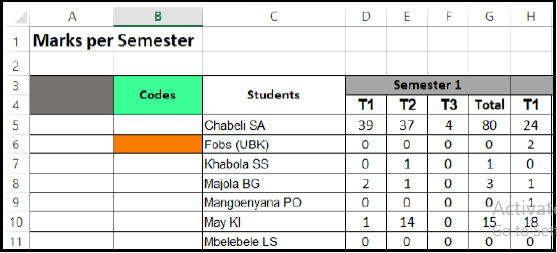
Each student needs a unique code to receive their overall final results.
Write down the function you would use in cell B6 to create this unique code by using the following instructions:
- The first 2 letters of students names (column C); followed by
- The total for the semester (column G).
EXAMPLE: AS80 (4)
8.3 Study the spreadsheet below and answer the questions that follow.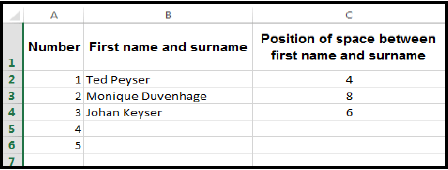
8.3.1 Give only the name of the function that was used in Column C to determine the position of the space between the first name and the surname in Column B.
(1)
8.3.2 Name the spreadsheet feature that was used to display the words in cell C1 below one another within the same cell. (1)
8.3.3 Name the spreadsheet feature that was used in Column A to systematically insert automatic numbers from 1 to 5 in consecutive rows. (1)
8.4 Study the screenshot extract of a database table below and answer the questions that follow.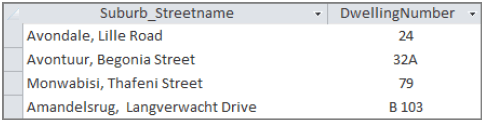
8.4.1 Which criterion would you enter in a query to extract suburbs starting with ‘A’? (2)
8.4.2 State which data type was used for the field DwellingNumber. (1)
8.4.3 Which criterion would you enter in a query to find those records that do not have a value entered in the DwellingNumber field? (1)
8.5 Briefly explain what the Widow/Orphan control in a word processor is used for. (1)
[15]
TOTAL SECTION B: 75
SECTION C
QUESTION 9: INTEGRATED SCENARIO
Your parents have decided to buy a laptop. The salesman convinced them to also buy a VRX5 as it is part of modern technology. They have never heard of VRX5 before. Below is an image of the VRX5. Assist them by answering the following questions.
|
9.1 Identify AND describe the type of device (VRX5) above. (2)
9.2 Name ONE use and ONE disadvantage of the VRX5. (2)
9.3 Give TWO reasons why you would prefer to have a laptop instead of a desktop computer in this context. (2)
9.4 Identify TWO software-related problems that could reduce the speed of a computer.Write down a potential solution for EACH of the problems. (4)
9.5 You will be sharing your laptop with your partially sighted brother. Name TWO devices that could assist him to interact with the content on the monitor. (2)
9.6 Skype is a popular software package that uses VoIP technology. Give TWO disadvantages of using VoIP software, besides the fact that an internet connection is needed. (2)
9.7 Give TWO possible uses for voice recognition software other than for security purposes. (2)
9.8 Ransomware is a type of malicious software from crypto virology that threatens to publish the victim's data or perpetually block access to it unless a ransom is paid.
9.8.1 How do you prevent ransomware? (2)
9.8.2 Why do many people pay the ransom? (2)
9.8.3 Anonymous payment services are used for ransomware payment. Name ONE method of payment that can be used. (1)
9.9 Windows 10 has no option to turn off automatic system updates.
9.9.1 Give TWO reasons why software developers release updates. (2)
9.9.2 State TWO potential disadvantages of not being able to disable automatic updates. (2)
[25]
QUESTION 10: INTEGRATED SCENARIO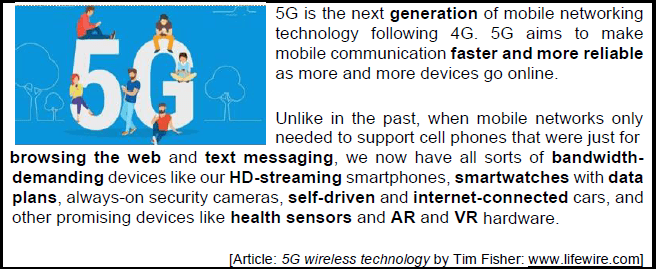
10.1 What does the ‘G’ in 4G or 5G stand for? (1)
10.2 Name TWO ways (protocols) in which on-line devices would wirelessly connect to each other. (2)
10.3 Name ONE wearable computer mentioned in the article above and give ONE task that a user can perform with this device. (2)
10.4 What is the computer called that would centrally store all information received from connected devices? (1)
10.5 Explain why HD-streaming will demand a lot of bandwidth. (2)
10.6 Name the unit in which transfer speed to or from the internet is measured. (1)
10.7 Give ONE reason why upload speeds are normally slower than download speeds. (1)
10.8 Match the data plan in COLUMN B to a user in COLUMN A. Just write the question number (10.8.1–10.8.2) and the letter (A–C) of the data plan down, for example 10.8.4 D.
COLUMN A USER | COLUMN B DATA PLAN | ||
10.8.1 | Student who uses the internet as needed for research | 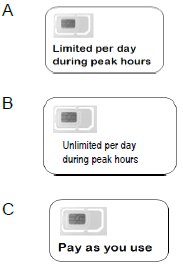 | |
10.8.2 | Business user who does meetings via Skype with clients across the globe | ||
10.8.3 | Office user who mostly uses e-mails and visit social networking sites | ||
(3 x 1) (3)
10.9 During the COVID-19 pandemic schools want to function digitally (paperless) as much as possible.
10.9.1 Name TWO advantages for education when mobile communication becomes faster and more reliable. (2)
10.9.2 Learners will use instant messaging for communicating with teachers and each other. Give TWO examples of instant messaging applications. (2)
10.10 The school provided tablets to learners during the pandemic. A database was created to keep track of the tablets.
The following fields were created:
Field Name | Data Type | Description |
Name | Short Text | The name of the recipient of the tablet, e.g. Mpho Dlamini |
Category | Short Text | The grade of a learner, e.g. Gr 12 |
Value | 10.10.1 | The value of the tablet, e.g. R4 500.00 |
TabletID | 10.10.2 | A photograph of the serial number of the tablet, e.g. SN 123654785.png |
Answer the following questions based on the design of the database table above:
10.10.1 Give the most appropriate data type for the Value field. (1)
10.10.2 Give the most appropriate data type for the TabletID field. (1)
10.11 List TWO general advantages of using computer-based training software. (2)
10.12 Name TWO ways in which AR and/or VR technology can be of benefit to the health sector. (2)
10.13 Name TWO disadvantages of 3D printers. (2)
[25]
TOTAL SECTION C: 50
GRAND TOTAL: 150
