Computer Technology Application P2 Grade 12 Questions - NSC Exams Past Papers and Memos September 2019 Preparatory Examinations
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin.
- Leave a line after EACH subquestion.
- In general, ONE mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1– 1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 Which ONE of the following is NOT web-based software?
- Adobe Photoshop Express
- Office 365
- Linux
- Google Calendar (1)
1.2 Which ONE of the following is an example of a monitor’s refresh rate?
- 5 ms
- 1920 x 1080
- 16:9
- 60 Hz (1)
1.3 Cloud storage refers to ...
- shared data storage on a central server usually managed by a hosting company.
- store and control by a single person over the internet.
- software that allows access to files without an internet connection.
- faster uploading of data. (1)
1.4 How do solid-state drives store data as compared to traditional hard drives?
- Optical
- Electronic
- Magnetic
- Digital (1)
1.5 Which ONE of the following statements about a URL shortener is FALSE?
- A URL shortener is a service used to convert a long URL to a shorter one.
- A website will allow access if you paste a long URL.
- A URL shortener will make a long URL much easier to share.
- All websites prevent URL shorteners from being used. (1)
1.6 Which ONE of the following statement about RAM is FALSE?
- RAM is more expensive per GB than hard drives.
- RAM does not store data and programs when the device is switched off.
- RAM has a much lower capacity than hard drives.
- RAM operates on a mechanical basis and is therefore, relatively slower. (1)
1.7 The automatic movement of text to the next page in a document is known as a ….
- continuous section break.
- soft page break.
- hard page break.
- next page section break. (1)
1.8 The defragmentation utility can be used to ...
- rearrange files in a continuous order.
- remove corrupted files.
- compress unused files.
- increase hard drive space. (1)
1.9 You want to find out how many times a date in 2014 appears in a column of dates consisting of month and year. Look at the screenshot below and complete the formula.
=COUNTIF(B5:B36; ____) 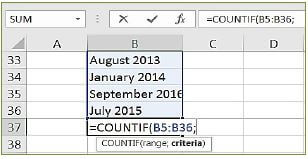
- “>2013”
- 2014
- “*2014”
- =2014 (1)
1.10 If you want to determine how many records appear in a report, you should use the following expression in a calculated field:
- =Sum(([Name of specific field]) + Count([Name of specific field]))
- =Count([Name of specific field])
- =Sum([Name of specific field])
- =Max([Name of specific field]) (1) [10]
QUESTION 2: MATCHING COLUMNS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–P) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 Q.
| COLUMN A | COLUMN B |
2.1 A port usually found on portable devices such as smartphones |
|
(10 x 1) [10]
QUESTION 3: TRUE/FALSE ITEM
Indicate whether the following statements are TRUE or FALSE. Write ‘true’ or ‘false’ next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word ‘NOT’ to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
QUESTION | ANSWER |
Google is the world’s most popular search engine. | True |
A NIC has slots for hardware components such as the CPU. | False – motherboard |
3.1 A multi-touch screen offers more functionality without using menus. (1)
3.2 A solid state drive is a drive that has no moving parts, thus making it quieter and more robust. (1)
3.3 The term Virtual Reality (VR) is associated with simulation of a 3D-environment. (1)
3.4 ICT refers to the trend whereby all sorts of objects and devices increasingly being connected to one another via the Internet. (1)
3.5 Freeware refers to software that has copyright, but may be copied or shared for the purpose of trying it out, with the understanding that an amount should be paid for continuous use. (1) [5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEM TECHNOLOGIES
4.1 Study the advertisement below and answer the questions that follow. 
4.1.1 Name the TWO hardware components for Device A that are most important for the effective working of a computer, other than the hard drive. (2)
4.1.2 Explain how adding more RAM to a computer can improve the overall system performance of the computer. (2)
4.1.3 Give TWO reasons why solid state drives (SSDs) will in future replace hard disk drives as the main storage device of a computer. (2)
4.1.4 Give TWO benefits of buying Device A, which is an ‘all-in-one’ computer. (2)
4.1.5 Give TWO reasons why HDMI output is better than VGA output. (2)
4.2 The following questions refer to Device B:
4.2.1 Name TWO features/functionalities, which were added to a cell phone when multiple technologies converged as a phablet. (2)
4.2.2 Name ONE way in which you could transfer photos from Device B to your desktop computer. (1)
4.2.3 Give ONE example of an action that can be performed on a ‘multi touch sensing screen’. (1)
4.2.4 Name ONE biometric feature of Device B listed in the advert. (1)
4.2.5 Compare the operating systems found on both devices by referring to:
- Cost of the software (2)
- Support from the developer (2)
4.3 Write down the TWO processes in the information processing cycle that have the least influence on the overall performance of the computer. (2)
4.4 Explain why the central processing unit (CPU) of a computer needs cache memory. (2)
4.5 A buyer considers purchasing a 3D printer. Name TWO advantages of buying a 3D printer. (2) [25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Give TWO reasons for compressing files before uploading them to cloud storage. (2)
5.2 Study the Internet connection package advertised below and answer the questions that follow.
- 30 GB data per month
- 15 Mbps
- Shaped
5.2.1 Give the common term used when an Internet Service Provider slows down your Internet speed when you download huge amounts of data. (1)
5.2.2 Give TWO factors (besides the one in QUESTION 5.2.1) that can influence Internet speed. (2)
5.2.3 Explain the term shaped and provide ONE example of a situation where it would be necessary to ‘shape’ a connection. (2)
5.3 How would RSS-feeds be used to distribute podcasts? (1)
5.4 You are unable to attend a seminar in Limpopo due to protests. A friend suggests you use a video conference.
5.4.1 How can a video conference be used to share information about the seminar in Limpopo? (2)
5.4.2 Give TWO advantages of using a video conference. (2)
5.5 Your friend complained that he was automatically redirected to a fake website, even when he typed in the correct URL for a specific website. Name TWO ways how he can prevent becoming a victim of pharming. (2)
5.6 What is digital migration? (1) [15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Youth participating in social media has advantages and disadvantages.
6.1.1 Can continuous online participation decrease social interaction between people? Motivate your answer. (2)
6.1.2 Give TWO ways in which social media sites such as Facebook can benefit you in searching for a job. (2)
6.2 A strategy to prevent information overload is to read more accurately and faster. Give TWO more strategies to overcome overload of information. (2)
6.3 Compare plagiarism and copyright infringement by explaining:
6.3.1 What each offence is (2)
6.3.2 How you can avoid being guilty of the offence (2) [10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 Give TWO reasons why it would be necessary for a school or company that has a policy of BYOD to take extra measures to secure their data. (2)
7.2 Computers on any network can be open to ransomware attacks.
7.2.1 What is a ransomware attack and what is required of a user to do? (2)
7.2.2 What is the best way to safeguard/protect yourself against ransomware? (2)
7.3 Briefly explain how bitcoins work to financially benefit entrepreneurs or individuals. (2)
7.4 Social media has been overflowing with fake news recently. Give TWO ways to spot fake news. (2) [10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Name TWO possible data sources to create mailing labels in a mail merge. (2)
8.2 The following message appears when one tries to create a Table of Figures for all images in a document: "No table of figures entries found". What change should you make to the document to ensure a Table of Figures can be generated? (1)
8.3 Study the screenshot below which shows part of a spreadsheet. 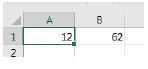
Cell B1 contains the formula =A1 * 5.
Give a possible reason why the answer displayed in cell B1 is not 60. (2)
8.4 Explain the difference between a validation rule and validation text by referring to their functions. (2)
8.5 What is the function of the ‘eye’ icon in the screenshot below? (1)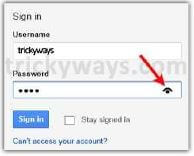
8.6 The screenshot below shows part of a spreadsheet listing movie titles. 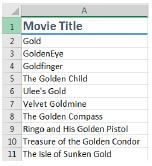
The function =COUNTIF(A2:A11, “Gold*”) returns a result of 3.
8.6.1 Explain the purpose of the ‘*’ in the criterion “Gold*”. (2)
8.6.2 If the criterion were changed to “Gold”, what would the result be? (1)
8.6.3 If the criterion were changed to “*Gold*”, what would the result be? (1)
8.7 The html code
<table border=“3”>
<tr>
<td>Cell 1</td>
<td>Cell 2</td>
</tr>
<tr>
<td>Cell 3</td>
<tr>
</table>
displays the following table in the browser: ![]()
How would you correct the highlighted (bold) line (the third line of code) so that the table will display as shown below? 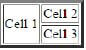 (2)
(2)
8.8 Mention ONE example of metadata that is saved with a word processing document. (1) [15]
TOTAL SECTION B: 75
SECTION C
QUESTION 9: INTEGRATED SCENARIO
Your cousin is a young man who has just completed his studies in Creative Brand Communication. He wants to start his own business of Branding using the savings he accumulated during his years at university. His type of business needs a ‘powerful’ computer/notebook as he has to use graphic design software like Photoshop.
9.1 Your cousin needs to start shopping for two computers: a notebook for himself and another one for his secretary.
9.1.1 You mention to your cousin that the notebook he needs to buy for the secretary should meet the minimum system requirements. What does this mean? (2)
9.1.2 You recommend to him that he has to buy a notebook with higher specifications for himself than the requirements for his secretary. Give TWO reasons why this is good advice. (2)
9.1.3 Your cousin has been given a trial version of a program by the software developers. Give ONE advantage of using a trial version of software before installing the full version. (1)
9.2 RFID tags and bar codes have similar functions.
9.2.1 What medium does an RFID reader use to read RFID tags? (1)
9.2.2 What medium does a bar code scanner use to read bar codes? (1)
9.3 Give ONE advantage of using a QR code to advertise his business. (1)
9.4 Your cousin has stored a lot of confidential information on his notebook.
9.4.1 Mention TWO practical ways in which he can prevent his notebook from being stolen from his office, besides being locked on the desk. (2)
9.4.2 Give TWO examples of biometric features to ensure secure access to a notebook. (2)
9.5 The secretary wants to telecommute on some days (wants to work from home instead of actually being present at the workplace). Give TWO general advantages of telecommuting or teleworking for the employee. (2)
9.6 Besides social networking sites, your cousin wants to use a blog for the business. Suggest TWO ways in which he can attract or maintain their interest in reading the blog in future. (2)
9.7 Your cousin wants to carefully consider certain aspects when choosing an Internet Service Provider (ISP). List TWO possible aspects to consider when choosing between different Internet Service Providers (ISP). (2)
9.8 The user has a choice of allowing an automatic download of a patch. Mention TWO disadvantages of choosing an automatic download of a patch. (2)
9.9 There will be instances where your cousin would want some of the hard copies to be converted and used electronically on his notebook.
9.9.1 Which device would be suitable to do this? (1)
9.9.2 Which software does the device use and briefly mention how this software works? (2)
9.9.3 Mention TWO disadvantages of using the device you mentioned in QUESTION 9.9.1 to create soft copies. (2) [25]
QUESTION 10
Your school is planning to roll out tablets to be used in the class. The school needs your support to make this transition smooth with the help of ICTs (Information and Communication Technologies).
10.1 The following are specifications of a tablet the school would like to purchase.
Technical Specifications: 1.3GHz Spreadtrum T-Shark quad-core processor |
10.1.1 Give TWO uses for a front camera of a tablet. (2)
10.1.2 What does it mean when the tablet is both Wi-Fi and SIM Card enabled? (2)
10.1.3 Give the name of the specification that 1024 x 600 refers to. (1)
10.1.4 Explain what the term micro SD refers to, and what the purpose of the micro SD is. (2)
10.1.5 What is meant by a quad-core processor and what is the significance of such a processor? (2)
10.2 When used in a classroom, tablets have both advantages and disadvantages.
10.2.1 Name TWO tasks associated with teaching and learning in the class that can best be done by using a tablet. (2)
10.2.2 Give TWO ways in which educators can make sure that their learners are unable to access inappropriate websites while ‘surfing’ the web. (2)
10.2.3 Name TWO ways in which the use of tablets in class can promote ‘green computing’. (2)
10.2.4 Some sight impaired learners are struggling with viewing work on the tablets due to the size of the screen. Recommend TWO solutions how this challenge can be overcome. (2)
10.3 ISPs offer data bundles which provide different limitations in the amounts of data that can be downloaded and uploaded in a month.
10.3.1 Why is it better for the school to have uncapped data? (2)
10.3.2 Explain the difference between a hard cap and a soft cap. (2)
10.4 The school should have a backup policy.
10.4.1 Name TWO measures that should be included in such a policy. (2)
10.4.2 Name TWO advantages of dedicated backup programs. (2) [25]
TOTAL SECTION C: 50
GRAND TOTAL: 150
