INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS NOVEMBER 2019
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
NOVEMBER 2019
MARKING GUIDELINES
NATIONAL SENIOR CERTIFICATE
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 D✓ (1)
1.1.2 B ✓ (1)
1.1.3 C ✓ (1)
1.1.4 A or D ✓ (1)
1.1.5 C ✓ (1)
1.2
1.2.1 J ✓ CSS (1)
1.2.2 F ✓ Driver (1)
1.2.3 D ✓ Topology (1)
1.2.4 N ✓ Firewall (1)
1.2.5 K ✓ Incremental backup (1)
1.2.6 A ✓ Client (1)
1.2.7 R ✓ DBA (1)
1.2.8 I ✓ Computer worm (1)
1.2.9 B ✓ Attenuation (1)
1.2.10 C ✓ AUP (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1.1 8/ 2 x 4 GB ✓ (1)
2.1.2 HDD✓
RPM/ spinning disk/ moving parts/ rotation speed. ✓(2)
2.1.3 1500 - 1536 GB / gigabytes ✓ (1)
2.2.1 Fetch✓instructions and data from memory (RAM).
Decode✓the instructions. (2)
2.2.2 Programs are split into smaller tasks called threads. ✓
Threads can be run simultaneously as if they are separate independent programs. ✓ (2)
2.3.1 Any TWO: ✓✓
- Speed of processing cores/ processing power/ clock speed.
- Number of processing cores/ pipelining.
- Amount of memory/ dedicated memory.
- Type of RAM
- GPU Cache
- The speed of its communication with the motherboard/
Whether it is installed into a PCI-Express x 8 or PCI Express x 16 slot. (2)
2.3.2 The built-in graphics adapter is used when performing tasks that don’t require intense graphics processing✓ to conserve battery power. ✓
When programs are executed that require more intense graphics processing, the laptop switches over to use the graphics card.
ANY TWO Concepts
- Improved graphics processing
- Conserve battery power
- Decrease the load of the CPU
- Cannot Add/Upgrade the graphics card in the laptop (2)
2.4.1 Power On Self Test✓ (1)
2.4.2 POST checks/tests that all important hardware (RAM, HDD, etc.) is working✓ (1)
2.5.1 Separate technologies and functions are combined into a single multi-purpose device. ✓ (1)
2.5.2 They can emulate/ test different smartphones/OS/platforms on a computer. v (1)
2.6 Any TWO: ✓✓
- Close unnecessary programs to free up memory.
- Add more RAM to your computer.
- Ensure that you run a 64-bit operating system. Otherwise you can’t use more than 4 GB.
- Replace with a faster storage (SSD).
- The use of the cloud/server for storage/processing (2)
2.7.1 To connect/house the CPU. ✓ (1)
2.7.2 Hardware can be added or removed while the computer is on. ✓ (1)
2.8.1 Any TWO: ✓✓
- Limited features / full version subject to time-limit.
- License must be bought to use full version.
- Available as a trial version/ try before buy (2)
2.8.2
- A regular (usually monthly) subscription fee is paid to use the software/ rented software. ✓ (1)
- Any ONE: ✓
- User always gets the latest version of the software.
- Only pay for what you use/ scalability of software
- Processed in another place like cloud/ server/ another location
- Saves storage space/ no need to install on hard drive
- No need for backups
- Accessibility on different devices/ locations (1)
2.9 The scattering/ spreading of parts of a file ✓ to several sectors on the disk which slows down the disk’s data access speed. (1)
TOTAL SECTION B: 25
SECTION C:
COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1
3.1.1 UTP / STP/ Ethernet cable/ Fibre✓ (1)
3.1.2 The router directs/redirects/sends data over a network✓ and chooses the best route to the destination ✓
Concepts
- Transferring data between networks/ Internet
- Finding the correct destination/redirecting (2)
3.2
3.2.1 Any TWO: ✓✓
- Easy to set up a wireless network
- It is easy to add new / more devices.
- Lower setup cost.
- Increased mobility/ Provides flexible layout to users of wireless/mobile devices.
- Provides a connection where cabling is not possible.
Any answer related to no cables needed (2)
3.2.2 It is a sender and receiver with an antenna ✓to send and/or receive radio waves. ✓
Any TWO concepts
- Connection to the Internet/network/wifi
- Send and receive signals
- Uses radio waves (2)
3.3
3.3.1 Gaining access to and using someone else’s Internet connection unlawfully/ without permission. ✓ (1)
3.3.2 Any TWO: ✓✓
- Don’t keep the default password – replace it with a good original password.
- Change the password on a regular basis/ good password policy
- Don’t leave your Wi-Fi connection open – secure it with a password/ use a password
- Limit the amount of data/devices/list of users
- Make the hotspot invisible
- Verification of the Mac address
- Limit the range
- Switch off when not in use (2)
3.4
3.4.1 The website uses the saved preferences of a user to generate the site/ It will differ for every user/ This personalizes the user experience of your business.
Interactivity✓
Easy updates✓
Any 3 concepts
- Personalisation/ Differs for all users
- Generated on the server
- Based on parameters
- Interactivity
- Easy to manage content (3)
3.4.2 Make use of search engine optimisation(SEO) (1)
3.4.3 (a) A set of rules ✓ for encoding and decoding of data for transfer ✓ (2)
3.4.3 It is a secure ✓ protocol for transactions (1)
3.5
3.5.1 PAN: has a range of a few metres/ limited/ small range✓ (1)
3.5.2 VPN: virtual private network – uses the Internet / public network✓ ,
Sign in with same privacy/ same security as a LAN ✓ (2)
3.6
3.6.1 Web application ✓ with functions and properties of traditional applications / software. ✓ (2)
3.6.2 Any ONE: ✓
- Google Docs
- Microsoft Office Live
- Office 365
- Microsoft Office 365 (1)
3.7 Any TWO: ✓✓
- Ease of use/ convenience
- Accessibility
- Marketing of business by app stores
- Notifications
- Using extra sensors/ functions/ properties in mobile device (2)
3.8
3.8.1 Processing, where the physical location✓ of objects /devices / persons is used. (1)
3.8.2 GPS ✓ (1)
3.9
3.9.1 A podcast is an audio file/recording ✓ available on the internet/network for download✓ (2)
3.9.2 Any ONE: ✓
- Real-time delivery of media content to a receiving device.
- Playing a file from an online source where the file is not permanently saved on the receiving device. (1)
TOTAL SECTION C: 30
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1 Value must be unique/ no duplicates. ✓ (1)
4.2 Range check/ Validation rule ✓ (1)
4.3
4.3.1 ClientSAID and ClientSAID_Ref ✓ (1)
4.3.2 One-to-Many relationship ✓
On the One side: tblClients table
On the Many side: tblOrders table✓
Concepts
- Correct type of relationship
- Correct table indicated for one and for many side (2)
4.4 Adding the ClientAge field will result in data redundancy as the age can be derived from the ID field. ✓ (1)
4.5 Desktop DBMS ✓
Desktop DBMS will be sufficient as the business is small and operates from a single building. ✓
OR
Server DBMS
Server DBMS will be more scalable/better accessibility.
Learner suggest desktop/server DBMS with suitable motivation for two marks (2)
4.6
4.6.1 Run-time error✓ (1)
4.6.2 Referential integrity/ relational tables ✓ (1)
4.7 Keeping identical copies✓ of a database (1)
4.8 Any TWO: ✓✓
- Use different passwords for different accounts.
- Make passwords long in length.
- Avoid using words that can be found in a dictionary.
- Avoid using personal information about yourself or your family.
- Change passwords on a regular basis.
- Include a combination of special characters, uppercase and lowercase characters and numbers.
- Avoid keyboard patterns (2)
4.9 The capturing of private/ unrelated information✓ without the users’ knowledge. ✓ (2)
4.10 The practice of examining large datasets in existing databases (and data warehouses) in order to generate new information/finding patterns/trends✓in data. (1)
4.11 Keeps track of / records ✓ changes ✓in the database
OR
Who made the changes.
When the changes were made. (2)
4.12 When a record is open for editing / inserting, the record is flagged as 'in use'✓
No other entity can make changes to that specific record until 'in use' flag/lock is removed.✓ (2)
TOTAL SECTION D: 20
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 String/ Text ✓ (1)
5.1.2 Integer/ Number ✓ (1)
5.2
5.2.1 Any ONE: ✓
NOT((10 > 5.0) OR (False))
NOT(True OR False)
The final answer
False ✓ (2)
5.2.2 Any ONE: ✓
(False = NOT True) AND (5.0 = 10 / 2)
True AND True
The final answer
True ✓ (2)
5.3
5.3.1 2 ✓ (1)
5.3.2 5 times ✓ (1)
5.3.3 4 ✓✓ (the contents of the loop has not been executed) (2)
5.4 Minimum: 5 ✓
Maximum: 12 (2)
5.5 Ceil() ✓ (1)
5.6 Any ONE: ✓
- Every single element needs to be compared / checked.
- In large datasets this can take a long time to perform. (1)
5.7 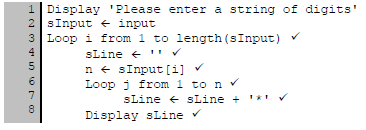
Concepts
Correct outer loop (1)
Initialize output variable before inner loop (1)
Inner loop (1) from 1 to character at outer loop position (1)
Add ‘*’ to output variable (1) in inner loop
Display output variable (1) (6)
TOTAL SECTION E: 20
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 A mobile office refers to a situation where you can carry/have with your portable tools essential for your business and the communication equipment ✓ that makes you reachable✓.
Concepts
- A description of mobility
- Office equipment (2)
6.1.2 Any ONE: ✓
- Can work from anywhere
- A freelance worker avoids the expense of paying rent
- Resources and equipment are always on hand
- Working hours not dependant on access to office (1)
6.2
6.2.1 Cloud / Internet / Cyberspace/ Web (1)
6.2.2 Any TWO correct examples of cloud storage services:✓✓
- Google Drive
- DropBox
- OneDrive
- MediaFire
- MEGA
- iCloud
- NextCloud
- SkyDrive (2)
6.2.3 Any TWO: ✓✓
- Image files
- Video files
- Sound files
- Text
- Media file (2)
6.2.4 Any ONE: ✓
- Media platform for professionals with the same interest
- Create a work/ experience profile/ job search
- Marketing platform for professionals (1)
6.2.5 Any TWO: ✓✓
- Do not provide personal/their details such as cell phone numbers or ID/ Do not provide passwords/Social engineering
- Enable privacy settings
- Disable share location settings/whereabouts
- Block unwanted users
- Disable cookies
- Limit third party applications
- Do not befriend strangers (2)
6.3 The process of getting two or more sets of data across multiple devices/ locations updated with the latest/same versions ✓of the data. (2)
6.4
6.4.1 Any TWO: ✓✓
- Easy to upgrade outdated hardware.
- Easy to repair/replace broken/defective hardware.
- Allows for customisation (2)
6.4.2 Any ONE: ✓
- Webcam/ camera/ smartphone
- Speakers/ ear phone/ head phone
- Microphone
- Wireless headset (1)
6.5
6.5.1 Distributed computing is a system whereby the resources of different computers are shared/combined✓ and used at the same time to solve a single problem✓.
Concepts
- More than one computer
- Perform a specific/one task (2)
6.5.2 By downloading and installing software on their computers✓, which will automatically start working on the project when their computers are idle✓.
Any TWO concepts✓✓
- Give permission for the use of your computer
- Provide/ share processing power
- Computer is idle/ not in use
- Install the appropriate software on their computers (2)
6.6
6.6.1 Artificial Intelligence✓ (1)
6.6.2 Since the developer makes use of a knowledge base ✓ there are a fixed number/possible outcomes/answers ✓ for each question or criterion. (2)
6.7
6.7.1 (a) Any TWO: ✓✓
- Anti-malware products/ Antivirus
- Operating system/ System software
- Firewall
- Firmware/ BIOS
- Web browser
- Product specific updates (2)
6.7.1(b) Anti-malware/ Antivirus products: to allow for newer forms of malware to be detected
All other software: malware exploits bugs or weaknesses in the security of software. ✓ (2)
6.7.2 Malware that locks or encrypts data/devices ✓ until a ransom is paid✓.
Concepts
- Malware makes data/devices unavailable / unreadable.
- Ransom/Money must be paid to make data accessible again or decrypt data. (2)
6.8
6.8.1 An attack that makes a web site unavailable ✓by using thousands of computers/botnet to request data from the site at the same time/ overloading the system. ✓ (2)
6.8.2 Script kiddie✓ (1)
6.9
6.9.1 Any ONE: ✓
Device that uses a battery to supply power.
Device used in the event of a power failure/problem to supply power. (1)
6.9.2 Any ONE: ✓
- Helps to protect the computer/storage devices against power surges and spikes.
- Keeps the computer on to allow the user to save data/ shut down the computer. (1)
6.9.3 Lossy ✓ (1)
6.10
6.10.1 Digital rights management ✓ (1)
6.10.2 Any ONE: ✓
- BitTorrent/ Torrent/ UTorrent
- FTP (1)
6.11
6.11.1 Any TWO: ✓✓
- Turn off radio wave transferring and receiving devices such as Bluetooth, GPS, Wi-Fi, etc.
- Turn on battery-saving mode.
- Disable sync functionalities.
- Limit background activity.
- Close open apps not in use (multitasking).
- Turn down screen brightness.
- Avoid playing media or video games on smartphones, as it drains battery rapidly.
- Carry a battery pack. (2)
6.11.2 Any ONE: ✓
- An Internet connection is required.
- Both users need to utilise the same software in order to communicate using VoIP.
- Credits need to be purchased in order to call telephones that are not on the Internet.
- VoIP can transfer a lot of data, especially for video calls, which can make it expensive or use up data caps quickly.
- Call quality is easily negatively affected due to slow or poor quality Internet connections. (1)
TOTAL SECTION F:40
GRAND TOTAL:150