INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC PAST PAPERS AND MEMOS NOVEMBER 2019
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
GRADE 12
NOVEMBER 2019
NATIONAL SENIOR CERTIFICATE
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short questions (15)
SECTION B: System Technologies (25)
SECTION C: Communications and Network Technologies (30)
SECTION D: Data and Information Management (20)
SECTION E: Solution Development (20)
SECTION F: Integrated Scenario (40) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/ reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1.1 to 1.1.5) in the ANSWER BOOK, e.g. 1.1.6 D.
1.1.1 The process used to reverse a database transaction and restore the data to a previous state is called …
- default state revert.
- revert.
- state restore.
- rollback. (1)
1.1.2 The technology that combines JavaScript with a browser command and allows the browser to update only a small part of a web page is called …
- XML.
- AJAX.
- IMAP.
- JVM. (1)
1.1.3 A type of reasoning that works with probabilities in order to arrive at a decision is called …
- alternative logic.
- system logic.
- fuzzy logic.
- design thinking. (1)
1.1.4 A method of encryption that utilises two separate keys to encrypt and decrypt data is known as …
- SSL.
- private key encryption.
- hashing.
- public key encryption. (1)
1.1.5 … is a built-in Delphi function that returns the integer part of a floating point number.
- Val()
- Sqr()
- Trunc()
- Frac() (1)
1.2 Choose a term from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question numbers (1.2.1 to 1.2.10) in the ANSWER BOOK, e.g. 1.2.11 U.
| COLUMN A | COLUMN B |
| 1.2.1 A technology that allows the definition of styles based on certain formatting rules that can be used by HTML files to alter the appearance of web pages 1.2.2 Software that enables an operating system to control and communicate with a hardware device 1.2.3 A term that refers to the physical layout of computers in a network 1.2.4 Hardware and/or software that monitors the traffic between a computer and the internet to safeguard against security breaches 1.2.5 A type of backup whereby backup files are made only of new files and files that have been modified since the last backup 1.2.6 Computers in a network that use but do not provide network resources 1.2.7 A professional person who is responsible for the management and maintenance of databases 1.2.8 A type of malware that self-replicates over a network without the need of a host file 1.2.9 The term that describes the loss of signal strength in a network medium over a distance 1.2.10 A policy document that specifies the rights and responsibilities of users within a network or work-related environment |
|
(10 x 1) [10]
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
A few learners from an IT class have decided to help their community by developing free educational apps as part of a community project.
2.1 The learners have to decide which laptop computer to purchase to develop the apps. The specifications of two laptop computers are as follows:
LAPTOP COMPUTER 1
| LAPTOP COMPUTER 2
|
2.1.1 State the amount of RAM that is included with Laptop Computer 2. (1)
2.1.2 Is Laptop Computer 1 bundled with a solid-state drive or a hard disk drive? Motivate your answer. (2)
2.1.3 Laptop Computer 2 has 1,5 TB of storage space. Give the size of the storage space in gigabytes. (1)
2.2 The CPU, also known as the processor, does most of the processing in a computer system.
2.2.1 CPUs work according to a sequence of steps called the machine cycle. Name the first TWO steps of the machine cycle. (2)
2.2.2 Modern operating systems are capable of performing many different processing techniques. Briefly explain the term multithreading. (2)
2.3 The IT learners often discuss the features of the latest graphics cards.
2.3.1 Name TWO factors of a graphics card that affect its graphics processing ability. (2)
2.3.2 Many laptop computers have a built-in (or integrated) graphics adapter and a graphics card.
Give TWO reasons why laptops are designed this way. (2)
2.4 The BIOS, which includes POST, plays a major role in the boot-up process of a computer.
2.4.1 What does the acronym POST stand for? (1)
2.4.2 Briefly explain the role of POST in the boot-up process of a computer. (1)
2.5 The learners are considering making their apps available for mobile devices, such as smartphones.
2.5.1 Define the term convergence. (1)
2.5.2 How can the learners use virtualisation to their advantage in developing the mobile apps? (1)
2.6 Computer systems can encounter slow performance when running educational apps due to the overuse of virtual memory.
State TWO ways in which to address the problem related to virtual memory. (2)
2.7 Desktop computer hardware can be extended easily.
2.7.1 What is the purpose of the ZIF socket on a motherboard? (1)
2.7.2 Most computer peripherals are hot swappable. Explain what is meant by the term hot swappable. (1)
2.8 The learners want to release their educational apps as freeware, but there are many other types of software licenses, such as shareware.
2.8.1 Explain what the use of shareware entails. (2)
2.8.2 Many software development companies use the SaaS distribution model.
- Explain how SaaS works. (1)
- Name ONE advantage of the use of SaaS. (1)
2.9 A common problem associated with the use of hard drives is disk fragmentation.
What is disk fragmentation? (1)
TOTAL SECTION B: 25
SECTION C: COMMUNICATIONS AND NETWORK TECHNOLOGIES
QUESTION 3
You started a freelance business and need to set up a network for the business.
3.1 When setting up a small office network, some possible essential pieces of equipment could include cables and routers.
3.1.1 Name ONE type of network cable that could be used. (1)
3.1.2 Explain the purpose of a router. (2)
3.2 It has been suggested that you consider a wireless set-up for your network.
3.2.1 Name TWO benefits of a wireless network. (2)
3.2.2 Access points in wireless networks are essential.
Explain what an access point is. (2)
3.3 Wireless networks are prone to piggybacking.
3.3.1 Explain what piggybacking entails. (1)
3.3.2 Suggest TWO ways in which a network can be protected from piggybacking. (2)
3.4 You plan on developing a website to be used as part of your marketing strategy.
3.4.1 Explain the benefit of a dynamic website. Refer to the properties of a dynamic website in your answer. (3)
3.4.2 How can you ensure that your website will appear in a search list, even if your business type is not really relevant to the search? (1)
3.4.3 You decided to use the HTTPS protocol.
- What is a protocol? (2)
- Motivate why it is more advisable to use the HTTPS protocol than the HTTP protocol. (1)
3.5 You need to access your business files, which are stored on your home network, from any location.
3.5.1 Explain why the use of a PAN will NOT be suitable. (1)
3.5.2 Give TWO reasons why the use of a VPN will be more suitable. (2)
3.6 You decided to use rich internet applications (RIA) to save on expenses.
3.6.1 Explain what RIA is. (2)
3.6.2 Give an example of a RIA. (1)
3.7 Mobile apps have become a trending phenomenon, driven by an increasing reliance on mobile devices.
Give TWO reasons why you should consider creating an app for your business to be used on a mobile device. (2)
3.8 Location-based computing can be useful for your business.
3.8.1 What is location-based computing? (1)
3.8.2 What type of technology is used to implement location-based computing? (1)
3.9 Freelancers are constantly on the move and often use podcasts to stay up to date with the most recent developments in their respective fields while travelling.
3.9.1 What is a podcast? (2)
3.9.2 Podcasts are often streamed. Explain the concept of streaming. (1)
TOTAL SECTION C: 30
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
A small local business operating from a single site store their business data in a database with two tables called tblClients and tblOrders.
The table design for the tblClients table is as follows:
| Field Name | Data Type |
| ClientSAID | Short Text |
| LastName | Short Text |
| FirstName | Short Text |
| ContactNumber | Short Text |
NOTE: The ClientSAID field in the tblClients table contains the client's 13-digit South African identity number.
The table design for the tblOrders table is as follows:
| Field Name | Data Type |
| InvoiceNumber | Short Text |
| ClientSAID_Ref | Short Text |
| Amount | Currency |
| Paid | Yes/No |
NOTE: The ClientSAID_Ref field in the tblOrders table contains the client's 13-digit South African identity number.
4.1 No primary key is indicated.
Name the distinct property of a primary key in a table. (1)
4.2 Only orders with the value of an amount of at least R500,00 will be inserted into the tblOrders table. Suggest a data validation technique that can be used to enforce this condition. (1)
4.3 No relationship is indicated between the tblClients table and the tblOrders table.
4.3.1 Which fields can be used to set a relationship between the tables? (1)
4.3.2 Identify the type of relationship which will be formed AND indicate the table that will appear on each side of the relationship. (2)
4.4 A suggestion has been made to add the client's age, ClientAge, as an additional field to the tblClients table.
Evaluate why this suggestion would lead to a poor table design. (1)
4.5 Suggest whether the business should use a desktop or a server database management system. Motivate your answer. (2)
4.6 The following error message is displayed when you want to insert a record in the tblOrders table: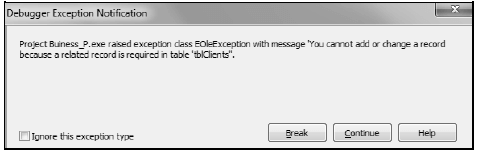
4.6.1 Is the error message above caused by a syntax, runtime or logical error? (1)
4.6.2 Name the database design concept related to the error message above. (1)
4.7 A decision has been made that data mirroring will be used for the database.
Define the term mirroring. (1)
4.8 As a business owner, it is important to have a good password policy.
Suggest TWO guidelines for a good password policy in terms of the compilation of passwords. (2)
4.9 One of your clients enquired about his personal information that was used to send him messages from unknown sources. You answered, 'It is invisible data capturing.'
What is meant by the term invisible data capturing? (2)
4.10 Using a data warehouse will enable you to do data mining.
Explain the concept of data mining. (1)
4.11 The business will be audited for tax purposes.
Briefly discuss how an audit trail can be used to assist the auditing firm in their investigation. (2)
4.12 Record locking is a mechanism used in most databases.
Explain how recordlocking works. (2)
TOTAL SECTION D: 20
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 Write down the most appropriate data types for variables to be used for the following scenarios:
5.1.1 A South African cellphone number needs to be stored, e.g. 083 112 4393. (1)
5.1.2 A system needs to keep track of the number of times a client has placed an order. (1)
5.2 The following programming statements have been provided:
K = 10;
L = 5.0;
M = False;
Evaluate the following expressions and indicate if it will result in True or False.
Show ALL steps.
5.2.1 NOT ((K > L) OR (M)) (2)
5.2.2 (M = NOT True) AND (L = K / 2) (2)
5.3 Consider the following Delphi code and answer the questions that follow: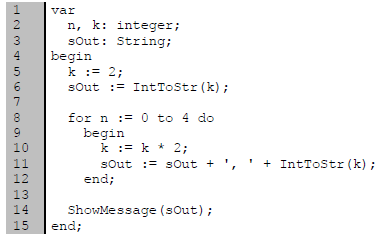
5.3.1 What is the value of sOut before the loop has been executed? (1)
5.3.2 How many times will the loop be repeated? (1)
5.3.3 What will be the value of k when the variable n reaches the value of 1? (2)
5.4 Specify the correct minimum AND maximum values that can be generated as a result of the following Delphi statement:
iRandomNumber := Random(8) + 5; (2)
5.5 Name a built-in Delphi function that will consistently round up a decimal number, such as 47.3 or 34.5, to the next whole number. (1)
5.6 A linear search, also known as sequential search, is one of the most popular search algorithms, but can be inefficient.
Give ONE reason why a linear search can sometimes be considered to be inefficient. (1)
5.7 An algorithm must be developed to display an output of stars when any string of digits is entered as text, as shown in the examples below.
Example of output if the input was '534':
| ***** *** **** |
Example of output if the input was '49813':
| **** ********* ******** * *** |
Complete the algorithm below to produce the correct output according the string of digits that was entered, as explained above.
| Display 'Please enter a string of digits' sInput ← input ... |
(6)
TOTAL SECTION E: 20
SECTION F: INTEGRATED SCENARIO
QUESTION 6
Freelancing is becoming more popular as people prefer to work from home. There are hundreds of freelance job opportunities available on the internet.
6.1 Freelance jobs are often done from a mobile office.
6.1.1 Define the term mobile office. (2)
6.1.2 How will a freelancer benefit from using a mobile office? (1)
6.2 The following conclusion was published in a report based on a survey about freelancing in the media industry:
'In line with the fact that the majority of freelancers work in the digital/online space, it makes sense that social media is considered an important marketing tool for creative entrepreneurs. 32% of respondents cite Facebook as their primary marketing platform, followed by LinkedIn.'
6.2.1 What is the common term used for digital/online space? (1)
6.2.2 Give TWO examples of online data storage services. (2)
6.2.3 When working with dynamic web pages, the term 'online storage' is used often. This refers to storage on a web server.
Give TWO other examples of files that would be saved online for use by a dynamic web page, apart from database files. (2)
6.2.4 Explain the purpose of the LinkedIn media platform. (1)
6.2.5 State TWO guidelines for protecting users' privacy when using social media platforms. (2)
6.3 Data synchronisation is of the utmost importance for freelancers on the move.
Briefly explain what data synchronisation entails. (2)
6.4 Different types of hardware and software are required to conduct video conferences for the purpose of freelancing.
6.4.1 State TWO main advantages of modular design in hardware. (2)
6.4.2 Name a device that can be attached to a personal computer to conduct a video conference. (1)
6.5 An NGO company does research on weather patterns. Therefore they require a lot of computer processing power.
They decide to use distributed computing.
6.5.1 Describe the term distributed computing. (2)
6.5.2 Briefly describe how the general public can become involved in distributed computing. (2)
6.6 An expert system is an application of AI.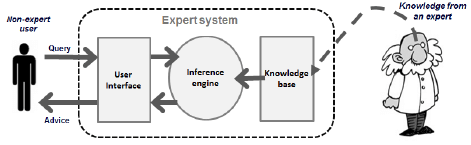
6.6.1 What does AI stand for in this context? (1)
6.6.2 Many freelancers use their skills to develop software.
Explain, with reference to the diagram above, why a rule-based system, such as an expert system, can be developed without the developer being an expert in a specific field. (2)
6.7 Cyber security is very important, especially for freelancers who often rely on the internet to save and process their data.
6.7.1 Malware threats can be reduced by updating your software.
State the TWO types of software that should be updated. (2)
Explain for EACH type of software in QUESTION 6.7.1(a) why updating the software would prevent malware threats. (2)
6.7.2 Define the term ransomware. (2)
6.8 Website developers need to guard against many types of cybercrime.
6.8.1 Explain the concept of a DDoS attack. (2)
6.8.2 Give the term used for an amateur programmer who modifies virus templates and then releases it. (1)
6.9 A reliable backup and compression system is important to save data.
6.9.1 A UPS is one way of securing data.
Briefly explain what an uninterruptable power supply (UPS) entails. (1)
6.9.2 State how a UPS is able to secure data. (1)
6.9.3 What type of compression sacrifices insignificant data to conserve space? (1)
6.10 DRM technologies were developed in response to the rapid increase in online piracy of commercially marketed material, which increased through the widespread use of peer-to-peer file sharing applications.
6.10.1 What does DRM stand for? (1)
6.10.2 Name ONE popular and well-known example of a protocol that uses peer-to-peer file sharing over the internet. (1)
6.11 The modern smartphone is an essential device for freelancers.
6.11.1 Suggest TWO practical tips for freelancers to keep their smartphone batteries charged for a longer period of time. (2)
6.11.2 Freelancers can use their smartphones to make video calls with apps that utilise VoIP.
State ONE other disadvantage that is associated with the use of VoIP, other than the use of battery power. (1)
TOTAL SECTION F:40
GRAND TOTAL:150