INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - AMENDED SENIOR CERTIFICATE EXAM PAST PAPERS AND MEMOS MAY/JUNE 2016
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER TWO (P2)
GRADE 12
AMENDED SENIOR CERTIFICATE EXAM
PAST PAPERS AND MEMOS 2016
MEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1.1 B ✔ (1)
1.1.2 A ✔ (1)
1.1.3 C ✔ (1)
1.1.4 D ✔ (1)
1.1.5 A ✔ (1)
1.2.1 Cookie ✔ (1)
1.2.2 Plug and Play ✔/PnP (1)
1.2.3 Spoofing ✔/Phishing (1)
1.2.4 SQL injection ✔ (1)
1.2.5 Streaming ✔ (1)
1.2.6 Artificial intelligence ✔(AI) (1)
1.2.7 Mediated search ✔ (1)
1.2.8 DBMS – Database Management Software ✔ (1)
1.2.9 Static website ✔ (1)
1.2.10 Peer-to-peer ✔ (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1
2.1.1
- Any ONE ✔✔
Cache is a small amount of high speed memory where data and instructions likely to be used next by the CPU, is stored eliminating the need to fetch it from the slower RAM.
Concepts:- Saving time in fetching of instructions
- High speed memory
- Cache memory is built in to/not removable ✔ from the processor (1)
- Any TWO ✔✔
- Faster at boot up time/faster access time
- No moving parts so less easily damaged/bigger life/lasts longer/more reliable
- Uses less power
- Generates less heat
- Smaller dimensions (2)
- Any ONE ✔✔
2.1.2
- Any TWO ✔✔
- Provides a user interface
- I/O management (Input/output management)
- Process management
- Manages system memory
- File management/Storage management
- Security
- Optimises efficiency/speed (2)
-
- Android: designed for mobile ✔ devices or example of mobile devices (1)
- Unix: designed to be used mostly in a network ✔ or server or desktop environment (not mobile) (1)
- Recently accessed web pages ✔ are stored locally on the hard drive ✔ and are retrieved faster from cache the next time they are accessed rather than from the web server.✔ (3)
- Any TWO ✔✔
2.2
2.2.1 Any ONE ✔
- Manage/Maintain/Control computer resources.
- Add more functionality for specific management tasks (1)
2.2.2 Any ONE ✔
- Internet filters
- Spam blockers
- Pop-up blockers
- Anti-spam programs
- Phishing filters
- Any other acceptable filtering mechanism (1)
2.2.3 Any ONE explained aspect ✔✔
- Programs often share files which are often spread over different folders, making it impossible to manually find all the files.
- If you delete one of these shared files, another program that was using the file might no longer function correctly
- The registry also has to be 'notified' that a program no longer exists, because that program was associated with certain files types, etc. (2)
2.2.4
-
- Backup: makes a copy ✔ of current files and are used for operational recoveries/to use if file is lost or damaged
- Archiving: moving ✔ less frequently used data/files to another area (2)
- Lossy compression – some insignificant/undetectable portion ✔ of data is sacrificed/lost ✔ when compression takes place. (2)
-
2.3
2.3.1 Virtual memory ✔
Also accept: sector (1)
2.3.2 When the RAM is full ✔, the operating system will move data ✔/ instructions that are not being used to the hard disk ✔ to free up space in RAM
Concepts:
- Reference to RAM being full/shortage
- Make use of hard drive space
- Memory allocations are split (3)
2.4 Any TWO✔✔
- OSS: Access to source code
- OSS: Freedom to adapt and change code to own needs
- OSS: Access to community of users/support (2)
TOTAL SECTION B: 26
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Any TWO ✔✔
- High level of expertise needed to set it up
- Need a high level of security
- Malware can spread easily
- If network develops a problem, no one can work
- A central problem with server could lead to loss of connection to the network/network resources.
- Cost of hardware (2)
3.2
3.2.1
✔ switch/central connection point
✔ computers/nodes
✔ connected separately to the switch
2 Marks for a diagram without labels 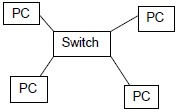 (3)
(3)
3.2.2 Any TWO ✔✔
- Easy to troubleshoot
- Easy to add new nodes
- Can remove any computer that does not work without affecting network/Stability
- Easy to set up
- Faster transmission of data to correct computer through a switch (2)
3.3
3.3.1 Any ONE ✔
- Cheap to install
- Easy to install
- Flexibility of cables
- High bandwidth over short distances (1)
3.3.2 Any TWO ✔✔
Not sensible because:
- Expensive cabling
- Need expert to install these cables
- More suited to a backbone network
OR
Sensible because
- High bandwidth
- Many users (2)
3.4
3.4.1 HTTPS ✔ (1)
3.4.2 Making voice/audio/video calls over the Internet/network✔
OR
Provides a variety of methods for establishing two-way multimedia communication over the Internet. (1)
3.5
3.5.1 Video on Demand ✔ (1)
3.5.2 Hotspot ✔ (1)
3.5.3 To provide Internet access ✔
OR
Internet service provider (1)
3.5.4 Wi-Fi/Wireless connectivity ✔ (1)
3.5.5 Any ONE✔
- Short range
Speed of transfer is slow
Reduced battery life (1)
- Short range
3.6
3.6.1 GPS ✔ (1)
3.6.2 Any ONE ✔
- Marketing/Advertising when in close proximity to the venue
- Tracking system in the event devices are stolen (1)
3.7
3.7.1 The server will notify the device that a new message has arrived✔ and automatically download ✔ the message to the device
OR
E-mail is automatically downloaded to the device without the user having to check his e-mail
Concepts:
- Automatic download
- Notification/no user action (2)
3.7.2 Any TWO ✔✔
- Attachments can use up storage
- Attachments are not automatically downloaded
- Limited to the number of messages that can be stored on the device
- May not have app to open attachments
- Not easy to read certain documents because of size of screen (2)
TOTAL SECTION C: 23
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1
4.1.1 Any TWO ✔✔
- Only 1 option can be selected at a time
- Only the valid/specific options are available
- Saves time – no need to type
- Do not have to check spelling, uppercase, etc. (2)
4.1.2 Any ONE ✔
- Use a mask edit (Delphi)
- Use 2 combo boxes – one for hours and one for minutes
- Give an example of time format in the text box (1)
4.1.3 (1 mark for valid with correct example) ✔(1 mark for correct with correct example) ✔
Valid – adhere to the specifications, e.g. hours must be in the range of 0 to 24
Correct – The data is within the specifications but incorrect based
on the specific information, e.g. instead of entering 10 which is the correct hour another incorrect but valid hour (e.g. 11) is entered.
Or any other correct explanation (2)
4.2
4.2.1 ComputerNumber is the primary key in the tblComputers table ✔ and must be placed in the tblUsers table as a foreign key. ✔ The ComputerNumber field in both tables can used to link the tables.
Concepts:
- Table set up: third table or add field to current table
Correct fields connected: primary and foreign keys (2)
NOTE: Ignore quote symbols in all SQL statements
- Table set up: third table or add field to current table
4.2.2
- SELECT LogoutTime FROM tblUsers WHERE PaymentMethod = 'Debit Card' ORDER BY LogoutTime
✔ SELECT LogoutTime
✔ FROM tblUsers
✔ WHERE PaymentMethod = 'Debit Card'/ LIKE ‘Debit%’
✔ ORDER BY LogoutTime (ASC optional)
Cannot be in descending order (DESC) (4) - UPDATE tblUsers SET PaymentMethod = 'Credit Card' WHERE UserIDNo = '7311017564076'
✔ UPDATE tblUsers
✔ SET PaymentMethod = 'Credit Card'
✔ WHERE UserIDNo = '7311017564076' (3) - SELECT Count(tblUsers.UserIDNo) AS CountCashIds
FROM tblUsers
WHERE PaymentMethod ='Cash';
✔ SELECT Count(UserIDNo)
✔ AS CountCashIds
✔ FROM tblUsers
✔ WHERE PaymentMethod='Cash'
NOTE: any field can be used to count the number of users (4) - SELECT * FROM tblUsers WHERE (LoginTime > '12:00') AND (LoginDate = #2016/02/25#)
✔ SELECT * FROM tblUsers
✔ WHERE (LoginTime >'12:00')
✔ AND
✔ (LoginDate = #2016/02/25#)
Also accept UserId as the field (4)
- SELECT LogoutTime FROM tblUsers WHERE PaymentMethod = 'Debit Card' ORDER BY LogoutTime
4.3 Audit trail – records who makes changes ✔ to the database and when the changes were made ✔ (2)
4.4
4.4.1 Any TWO ✔✔
- Using credit card or loyalty card when purchases are made
- With the completions forms for competitions, etc.
- Browsing the Internet/selecting webpages
- When using e-tags
Or any other correct answer (2)
4.4.2 Data mining (1)
TOTAL SECTION D: 27
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Once ✔✔ (2)
5.1.2 Infinite/Endless loop/Continuously/Never-ending ✔✔ (2)
5.2
5.2.1 Space is created in memory✔ to keep the attributes of the specific object ✔
OR
The constructor is used to create an instance of the object class
OR
Instantiation is the creation of a real instance or particular
realisation of an abstraction or template (such as a class) of an object. (2)
5.2.2
- Accessor: to get access to private data/field/attribute values✔ (1)
- Mutator: allows field/attribute values to be changed ✔ or set (1)
5.2.3
✔ get log in minutes
✔ get log out minutes
✔ get log in hour
✔ get log out hour
✔ calculate the number of hours
✔ calculate the number of minutes
✔ convert hours to minutes and add minutes
✔ multiply with 3
Solution1:
loginMin? copy the login minutes
logoutMin ? copy the logout minutes
loginHr ? copy the login hour
logoutHr ? copy the logout hour
totalMinLogin ? loginHr*60 + loginMin
totalMinLogout ? logoutHr * 60 + logoutMin
numberofMinutes ? totalMinLogout – totalMinLogin
cost ? numberofMinutes x 3
Solution 2:
loginMin? copy the login minuteslogoutMin ? copy the logout minutes
loginHr ? copy the login hour
logoutHr ? copy the logout hour
numberof Minutes ? (logoutHr – loginHr) *60+logoutMin – loginMin
cost ? numberofMinutes x 3
Or any other correct solution (8)
5.3
Found | Is Found true? | randomNum | Is randomNum = number? | Counter | Display | |
False | No/False | |||||
5 | No | xxxx | ||||
40 | Yes | xxxxx |
1mark first 2 columns initial values
1 mark to indicate that counter and display will be undefined
Errors
1 mark initialise counter
1 mark increment regardless of if statement
Counter has not been initialised before the loop
If Counter is set to 0 :
Add 1 to Counter before it is displayed
OR
Change the If-statement as follows:
If number = randomNum then
Found = true
Increment Counter
OR
Also including the increment in the else part of the if
OR
Initialise counter to 1 (2 marks)
(4)
5.4 0 1 0 0 ✔
0 1 1 1 ✔ (2)
TOTAL SECTION E: 22
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 Radio waves ✔/explanation of how the technology works (1)
6.1.2 Any TWO ✔✔
- Item can be tracked
- Easy to do stock take/can scan tag
- Don't have to be very close to read the tag
- Can read more than 1 tag at a time
- Can read hidden tags
- Interact with data stored on the tag
- Use tag to broadcast information (e.g. temperature) about the environment
Any other valid example (2)
6.2
6.2.1 Specialised network software skills and knowledge are required to manage the network. ✔
Also accept an example of specialised duties
Do not accept: maintenance of the network (1)
6.2.2 Any TWO ✔✔
- Use a password with many characters
- Include special characters
- Do not use common words
- Do not use your personal details
- Uppercase and lowercase
- Avoid patterns/repetitions (2)
6.2.3 Remote desktop (or suitable example) ✔ uses software to view the screen of the server on the local computer and control the server remotely. ✔
VPN (or suitable example) ✔ is a secure connection to the server via the Internet ✔ (4)
6.2.4 Any ONE ✔
- Install a firewall
- Install anti-virus software
- Keep anti-virus software up to date
Any other correct answer (1)
6.2.5 Any TWO ✔✔
- Allocating user rights
- Adding and removing users
- Making backups
Any other correct answer
Do NOT accept: issuing passwords and avoiding virus attacks (2)
6.3
6.3.1 Unsolicited ✔ junk/adverts/email sent to many recipients ✔at once with the intention of trying to convince the receiver to purchase a product or visit a website. (2)
6.3.2 Any TWO ✔✔
- Do not give out personal information on web sites
- Check that the web site is secure
- Do not answer bogus e-mails
or any other valid example (2) 6.3.3 Encryption ✔ (1)
6.3.4 A digital certificate is used to authenticate the website/ person/organisation. ✔ (1)
6.3.5 Any TWO ✔✔
- Check whether the author is reputable.
- Check whether the site is reputable
- Compare information on the topic on different web sites.
- Check the creation date – should not be out dated information. (2)
6.3.6 Devices that connect to the Internet ✔ and interact with each other often without human interaction/remotely accessible ✔ (2)
6.3.7 Any TWO ✔✔
- Change the display setting to dim.
- Switch off GPS
- Switch off Bluetooth/Wi-Fi
- Do not play videos on the device
- Close unnecessary apps that are running in the background
Any other correct answer (2)
6.3.8 Collection of programs designed to gain administrator rights ✔ to take control of the computer at the most basic level✔ (2)
6.4
6.4.1 Peer-to-peer protocol/Internet ✔ (1)
6.4.2 Any ONE ✔
- IP address is open to other users/security of your computer is compromised
- Downloaded content may be pirated/illegal
- Up-bandwidth can be used up/Make Internet connection very slow due to use of bandwidth (1)
6.5
6.5.1 Any TWO ✔✔
- Attachments/files can sometimes be too large to e-mail
Also accept any advantage of file-sharing such as: - Collaboration
- Simultaneous editing of documents is possible
- Files are always the latest version
- Accessibility from anywhere (2)
- Attachments/files can sometimes be too large to e-mail
6.5.2 File syncing service:
- All changes to the files are copied to the cloud service automatically ✔
- Have access to all files even if offline ✔
- Have access anywhere, anytime to latest version ✔ (3)
6.6 Any THREE ✔ ✔
- Easy to navigate interface/smaller screen
- Managing Internet data use
- Less memory
- Less storage
- Less processing capability
- Dedicated purpose/specifically designed for an organisation
- Can make use of additional sensors (3)
TOTAL SECTION E: 37
GRAND TOTAL: 150