INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - NSC PAST PAPERS AND MEMOS MAY/JUNE 2019
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY PAPER 2
GRADE 12
NATIONAL SENIOR CERTIFICATE EXAMINATIONS
MEMORANDUM
MAY/JUNE 2019
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 D ✓ (1)
1.1.2 B ✓ (1)
1.1.3 C v (1)
1.1.4 C ✓✓ (2)
1.1.5 B✓✓ (2)
1.2
1.2.1 Social engineering/ Social manipulation/ Phishing/ Pharming/ Spoofing ✓ (1)
1.2.2 Podcast/ Vodcast/ MP3/ MP4✓ (1)
1.2.3 Hacking/ Cracking / Back door accessing (1)
1.2.4 Audit trail ✓ (1)
1.2.5 BitTorrent/ torrent ✓ (1)
1.2.6 Web 2.0 ✓ (1)
1.2.7 System clock / clock ✓ (1)
1.2.8 Piggybacking ✓ (1)
TOTAL SECTION A: 15
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1 Any TWO functions of a motherboard: ✓✓
- Provides connectors to allow other circuits (CPU, RAM etc.) to connect to it/houses components.
- Ensures that all components of the computer can communicate with one another
- Distributes power to the parts that connect to it (2)
2.2 A point-to-point connection is dedicated. ✓✓ This means that the wires or paths used to transfer data are not shared between multiple components.
The wires or paths in a bus are shared between components. (2)
2.3
2.3.1 Any ONE of: ✓
- Video cards
- Network cards
- Modems
- Sound cards
- RAID card (1)
2.3.2 USB✓ (1)
2.4
2.4.1 CMOS memory ✓ (1)
2.4.2 The battery ✓ on the motherboard keeps the CMOS from losing its data. (1)
2.5
2.5.1 Multiprocessing ✓ (1)
2.5.2 Multitasking ✓ (1)
2.5.3 Multithreading ✓ (1)
2.6
2.6.1 Cache uses a limited amount of faster media✓ to speed up access to data and instructions stored on a slower media✓
OR
Cache temporarily stores recently/frequently accessed data and instructions on a faster medium
OR
A limited amount of fast memory used to speed up access to data and instructions stored on a slower medium
OR
Predicts the instructions to be loaded next.
Concepts:
- Faster access/high speed memory
- temporary storage of data and instructions frequently used (2)
2.6.2 A hardware interrupt is a means/method/signal whereby a device can indicate that it needs attention from the CPU. ✓ (1)
2.7 Any ONE ✓✓
They add extra features to browser to be able to view multimedia – e.g. in a web browser they are needed to allow the user to view 'special' effects.
OR
This has become necessary as more and more multimedia (a combination of text, pictures, sound and video) is added to the web which might not be supported by the browser.
Concepts:
- website contains specific types of multimedia
- browser needs plug-in to view/play media (2)
2.8
2.8.1 Point of sale ✓ (1)
2.8.2 Any TWO benefits of using barcodes in POS systems:✓✓
- Faster and more efficient for capturing prices.
- More accurate/prevents errors in the capture of prices that occur when people type in the prices.
- Business does not need to do individual pricing.
- Reference to updating stock
- Prevents tampering of prices on items (2)
2.9 The ability to increase and decrease resources (size and power) quickly and efficiently based on the changing requirements.
Concepts:
- Increase/decrease
- Changing needs (2)
2.10
2.10.1 Any TWO of: ✓✓
- Fix known bugs in programs
- Fix security loopholes
- Add new functions and features
- Improved performance
- Reference to malware (2)
2.10.2 Any TWO of: ✓✓
- The company does not have to check for and install updates/ updates are done automatically
- All users get the updates at the same time
- Do not use local resources. (2)
TOTAL SECTION B: 25
SECTION C:
COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 The switch connects computers to one another ✓and determines the destination of each network signal it receives, and forwards this signal to that destination.✓
Concepts:
- Connecting computers
- Directing signals (2)
3.2
3.2.1 Wi-Fi – connect to a LAN/HAN/ PAN
Reference to a small network✓ (1)
3.2.2 Bluetooth – file transfer✓/send files between laptop and cell phone
OR
to connect compatible devices over short distances
OR
A suitable example to illustrate Bluetooth (1)
3.2.3 Any one ✓
3G – use of cellular or mobile data/ use a 3G modem to access an ISP for Internet and e-mail activities when physically away from a wired network or Wi-Fi hotspot. (1)
3.3
3.3.1 Any TWO types of cable ✓✓
- UTP/STP/Twisted Pair
- Coaxial
- Fibre optic cables (2)
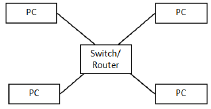
3.3.2
Criteria for diagram:
- All computers✓
- a switch ✓
- showing the connections to the switch ✓ (3)
3.4 Any TWO disadvantages of peer-to-peer: ✓✓
- Less security than a client-server
- Harder to manage than client-server
- Not suitable for a large number of node (2)
3.5
3.5.1 The data/text is transformed/ changed into a new unreadable/format ✓ using a specified set of rules/keys. ✓ (2)
3.5.2 Any ONE reason:✓
- Ensure privacy of users
- To prevent third parties from eavesdropping on the conversation (1)
3.5.3 Digital Rights Management (DRM) ✓ (1)
3.6
3.6.1 The decision engine refers to the program accepting data from the user ✓ looks it up in the knowledge base✓ and then deduces new facts or follows rules to generate a decision output. ✓
Concepts:
- Input from user
- Looks it up in the knowledge base
- Generates decision (3)
3.6.2 Fuzzy logic refers to reasoning/decision making that works with probabilities ✓ (1)
3.7 Distributed computing is a system whereby the resources of different computers ✓ are shared and used at the same time to solve a single problem✓ (2)
3.8 Java Script is used for automating elements ✓ on web pages.✓
OR
Java script commands help transform webpages from static to dynamic and interactive. (2)
TOTAL SECTION C: 24
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1
4.1.1 The relationship between the quality of data entered ✓ and the quality of information that can be extracted. ✓
OR
If the data entered is incorrect, the output produced will also be incorrect.
NOTE: No marks for only expanding the abbreviation. (2)
4.1.2 Any TWO:✓✓
- Format check/ Input mask
- Range check/ Validation rules
- Data type check
- Presence check (2)
4.1.3 Any ONE:✓
The correctness of data/free of errors
OR
Data which makes sense in a particular context. (1)
4.2 4.2.1 A code injection technique used to attack data-driven applications in which SQL statements ✓ are inserted into an entry/text field ✓ for execution
Concepts: Reference to using an SQL statement/command Action example Inserting, deleting, commanding the database (2)
4.2.2 When a record is open for either editing or inserting, the record is flagged to be in use. ✓ That means that no other user can make changes to that specific record. ✓
Concepts:
- Record in use
- Only 1 person can makes changes to the specific record (2)
4.3
4.3.1 A distributed database is a system where parts of a database ✓ are spread (distributed) across servers in separate locations. ✓ (2)
4.3.2 When the number of connected users becomes too large for a single server to cope with ✓
When a business is spread over a large geographical area✓ (2)
4.4
4.4.1 Number – Any numeric value entered by the user ✓
AutoNumber – A numeric value created by the program in sequence ✓ (2)
4.4.2 Field – ContactNumber ✓
Data type – Text ✓
Motivation – The leading 0 will not be retained ✓ (3)
4.4.3 Any ONE ✓
- To save memory space
- To avoid unnecessary /extra information being entered
- To help ensure that only valid data is captured (1)
4.5
4.5.1 Any TWO ✓✓
- Separate tables
- Relationships using correct primary and foreign keys
- Reduces redundancy
- Limit anomalies (2)
4.5.2 One to many ✓ (1)
4.5.3(a) Parent records in a table cannot be deleted if there is a child record in a related table✓✓ (2)
4.5.3(b) All records with the respective client number must first be deleted from the tblBookings table ✓ (1)
4.5.4 Composite ✓ key
Also accept
Concatenated
Compound (1)
TOTAL SECTION D: 26
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Testing ✓ (1)
5.1.2 Any ONE✓
- TOE (Task, Objects, Events) charts
- IPO
- UML/ Class diagram
- ERD
- Use case diagram/ UCD
- Flowchart (1)
5.1.3
- Repeat...Until ✓(1)
- While…do ✓ (1)
5.1.4
- Runtime ✓ (1)
- Logical ✓ (1)
5.2
5.2.1 Any TWO component's positions ✓✓
- Submit button should be placed at the bottom of the form
- The label indicating all information is necessary should be at the top of the form
- The label for the title-label must be to the left of the edit box (similar to the other labels)
- The vertical alignment of the labels relative to the edits differ – Full name-label is bottom aligned; Gender-label is top aligned and the Occupation-label is centre aligned
- The gender edit field does not require as many characters as a name/some edit fields are too wide/could be confusing (2)
5.2.2 Any ONE (Field ✓)(Component✓)
- Title - combo box/list box/radio group
- Gender - combo box/list box/radio group
- Occupation - edit box/list box (2)
5.3
5.3.1 Mutator/ set method ✓
Auxiliary ✓ (2)
5.3.2 Constructor✓ (1)
5.3.3 toString ✓ (1)
5.3.4
- The other class will not have direct access✓ to the attributes (1)
- Encapsulation ✓ (1)
5.4
5.4.1
| Line Number | Biggest | Smallest | Counter | Multiple | Remainder of Biggest / Counter = 0? | Output |
| 1,2,3 | 4 | 3 | 0 | |||
| 5 | 1 | |||||
| 6 | 3✓ | |||||
| 7 | No✓ | |||||
| 5 | 2✓ | |||||
| 6 | 6✓ | |||||
| 7 | No✓ | |||||
| 5 | 3✓ | |||||
| 6 | 9✓ | |||||
| 7 | No✓ | |||||
| 5 | 4✓ | |||||
| 6 | 12✓ | |||||
| 7 | Yes✓ | |||||
| 8 | 12✓ |
(12/2=6)
5.4.2(a) Start the counter at the value of 1 ✓ (1)
5.4.2(b) It is not necessary to test 1 as it would not be an LCM ✓/The LCM has to be 2 or more (1)
TOTAL SECTION E: 24
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 The measurement and identification ✓ of unique physical characteristics ✓ (2)
6.1.2 Any TWO ✓✓
- Finger print
- Iris scan
- Face scan
- Palm scan (2)
6.2
6.2.1 Any ONE ✓
- Security/vulnerability
- Speed of connection when lots of users are connected
- Often limited to small coverage area (1)
6.2.2 Any TWO of: ✓✓
- Interface is easier to navigate and therefore faster to use
- Have a dedicated purpose/no distraction and loss of focus.
- Don't have to remember URLs/use menus/bookmarks.
- Less data transfer needed – interface already installed/saves money and increases speed.
- Can be set to fetch data in the background/Data on your device can be continually synchronised with online storage in the 'cloud'.
- Make use of the additional sensors in your mobile device /offers a more integrated experience than a web page (2)
6.2.3 Any TWO ✓✓
- Cell phones can be used interactively by in class to do a quick quiz after a concept was discussed
- Teacher can provide the link to a YouTube video that explains a specific concept that learners need to apply is class e.g. How to declare an array in Delphi.
- Teacher can set up a discussion group for the duration of the class to encourage learners to investigate and discuss specific topics. Participation is evaluated afterwards and teacher can identify learners who are not participation for remedial action.
- Any other suitable answer (2)
6.2.4
- Can start listening immediately ✓/Do not have to wait for download to finish
- Does not take up storage space on device ✓/Music is not locally stored (2)
6.2.5 Safe online ✓ storage area/site for media files ✓ (2)
6.3
6.3.1 Radio Frequency Identification ✓ (1)
6.3.2 Any TWO ✓✓
- Easy to stock take
- Items fitted with RFID tags cannot easily be removed from the centre/Security
- Scanner can read items from a distance
- Scanner can read more than 1 item at a time (2)
6.4
6.4.1 Websites where an individual/company/organisation can write about their experiences ✓regarding a specific topic which are updated ✓often with events in chronological order.
Concepts
- Online diary/ refer to experiences
- Regular updates (2)
6.4.2 Any ONE: ✓
- Interaction with users of site
- The user can receive feedback from others about what the team is doing
- The blog gives the team an opportunity to make the work known to others
Also accept any other valid answer. (1)
6.5
6.5.1 Two marks allocated as follows:
- if single argument (bank or teacher) with single justification: one mark
- if arguments both ways with justification: two marks
Examples:
The bank should have:
- Adequate firewall protection
- Secure procedures (for example, not accepting telephonic instructions to change personal details for a person's bank account) (2)
Teacher should have:
- An updated anti-virus(required by the banks)
- Check that the computer's firewall protection is adequate
- Not done banking while at an Internet café/public free Wi-Fi connection
- Changed logon codes on a regular basis
- Kept the PIN number secret
6.5.2 Accept any well substantiated answer ✓
Yes,
- learners spend too much work time on social websites
- the use of school's data is high/learners use up the school's data cap
No
- If the learner needs to download material from their personal account for a school project (1)
6.6
- Transactions that are dependent on one another and are grouped together✓
- The DBMS will only complete the operation if all the individual transactions are successful✓
- If only some of the transactions are completed but errors occur the DBMS rolls back/reverses all transactions in the group. ✓ (3)
6.7 Any TWO ✓✓
- Provides limited free storage
- Synchronising of files between devices
- Able to share files with others/collaboration is possible
- Access files anywhere on any device
- Can serve as a backup (2)
6.8 Any ONE ✓
- Manage/access any computer remotely across a network.
- Can make changes to the data/files directly on the server via the network.
- Changes can be made on any PC from any location on the network.
- Can take control of a learners PC. (1)
6.9
6.9.1 Any ONE for PC technician ✓
- Assemble computers/Upgrade the computers
- Repair hardware/software
- Lay cables
- Install new trunking for cabling
- Install new switches/routers/wireless access points
- Install/ upgrade software (1)
6.9.2 Any ONE for Network administrator ✓
- Creates and manages accounts/Access control to hardware/ software
- Implements backup policy
- Installs and updates software
- Responsible for network security. (1)
6.10 Any ONE ✓
- Sensors
- Camera (1)
6.11
6.11.1(a) Mediated search: ✓
- Uses humans rather than reliance on algorithms.
- Search engine returns fewer more relevant results (1)
611.1(b) Semantic search: ✓
- Search engine software has the ability to interpret metadata on the web pages
- Search engine allows navigation without human intervention applying search criteria
- Automated searches for information (1)
6.11.2 A paid sponsored link is an advert which is often displayed on the results page ✓ and do not take one to a relevant website or web page. (1)
6.11.3 Click farms are companies that pay workers to repeatedly click on website elements ✓ to artificially 'increase' or 'boost' the status of a product or web page.✓ (2)
TOTAL SECTION F:36
GRAND TOTAL:150