INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC EXAMS PAST PAPERS AND MEMOS NOVEMBER 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC EXAMS
PAST PAPERS AND MEMOS NOVEMBER 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (15)
SECTION B: System Technologies (23)
SECTION C: Communication and Network Technologies (21)
SECTION D: Data and Information Management (25)
SECTION E: Solution Development (29)
SECTION F: Integrated Scenario (37) - Read ALL the questions carefully.
- Answer ALL the questions.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1 Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1.1 to 1.1.5) in the ANSWER BOOK, e.g. 1.1.6 D.
1.1.1 A type of malware that is disguised as a useful program is known as a …
- virus.
- rootkit.
- worm.
- trojan horse. (1)
1.1.2 Software that may be used for free but with a time and functionality limit:
- EULA
- Shareware
- Proprietary software
- Freeware (1)
1.1.3 Which ONE is NOT a duty of a system analyst?
- Analyses the software requirements of the client
- Collaborates with the client and the programmer to develop a system
- Creates a list of specifications for the software developer
- Writes code for the software solution (1)
1.1.4 What will be the value of iAnswer when the following statement is executed?
iAnswer := 2 + 5 * 7 div 2 – sqr(4);
- 3
- 8
- 1
- 0 (2)
1.1.5 Which formula is represented in the segment of code below?
for k := 2 to p do
begin
n:= n * n;
end;
- n * p
- np
- pn
- pp (2)
1.2 Give ONE word/term for EACH of the following descriptions. Write only the word/term next to the question numbers (1.2.1 to 1.2.8) in the ANSWER BOOK.
1.2.1 Part of the ROM where information with regard to the setup of the computer can be saved (1)
1.2.2 Security based on the measurement and identification of unique physical characteristics of a person, e.g. fingerprints (1)
1.2.3 Digital code, attached to an e-mail, used to identify and validate the sender of an electronic message (1)
1.2.4 Software that allows the user to perform maintenance tasks on a computer (1)
1.2.5 The method that is used in object-oriented programming to instantiate an object (1)
1.2.6 The steps followed to prevent anomalies from occurring in a database (1)
1.2.7 A tool used to identify logical errors by working through the program manually step by step and recording the result of each step in a table (1)
1.2.8 Compressing data by losing some insignificant portions of the data (1)
TOTAL SECTION A: 15
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
| A chain of fast-food restaurants is opening a new branch in the local shopping mall. The IT infrastructure of the mall is modern. |
2.1 Tablet computers will be used to place orders directly on the system in the new restaurant. Give TWO reasons why the use of tablet computers is appropriate for this purpose. (2)
2.2 The mall server will store all the records.
2.2.1 Name TWO hardware components for which the specifications will be of a higher level in the server, as opposed to those for a standard PC. (2)
2.2.2 State TWO types of actions that will be performed by a disk clean-up when clearing space on the server's hard disk drive. (2)
2.3 Many restaurants owners are considering an upgrade of their computer systems.
2.3.1 State TWO important differences between standard RAM and cache memory in a computer system. (2)
2.3.2 What is the function of the device driver that is installed when adding a new printer? (2)
2.3.3 What is the purpose of the product key or activation code that is often required when installing new software? (1)
2.3.4 The operating system indicated that updates were available.
- State ONE advantage of ensuring that the operating system is updated regularly. (1)
- State ONE disadvantage of allowing the operating system to update automatically. (1)
2.3.5 Virtual memory can enhance the performance of the computer.
- When will virtual memory be used by the operating system? (1)
- Explain the basic concepts of how virtual memory works. (2)
2.4 Safeguarding of the data is vital.
2.4.1 Give ONE reason why a hard disk drive could fail. (1)
2.4.2 Suggest ONE device that could protect data from being corrupted during a power failure. (1)
2.4.3 Explain the difference between making a backup and archiving data. (3)
2.4.4 Explain the role of a firewall as a means of data protection. (2)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Sharing resources is an important benefit of using networks. State TWO other benefits of having a computer network in a company. (2)
3.2 In laptop computers NICs are used to provide both Wi-Fi connection and an Ethernet port.
3.2.1 Explain the function of an NIC when providing network connectivity. (2)
3.2.2 What medium is used to send and receive data in a Wi-Fi network? (1)
3.3 Communication performance in cabled and wireless networks is often compared.
3.3.1 Name a type of network cable that has a very low level of attenuation of signal. (1)
3.3.2 Explain how poor signal strength can be addressed when setting up wireless communication networks. (2)
3.3.3 Give TWO reasons why companies providing wireless internet access prefer to use WiMAX instead of Wi-Fi. (2)
3.4 Web 3.0 is often referred to as the 'Semantic Web'.
3.4.1 Explain what is meant by the term Semantic Web. (2)
3.4.2 What is the purpose of metadata in the Semantic Web? (1)
3.5 E-mail remains a popular means of communication.
3.5.1 Which protocol is used to download e-mail? (1)
3.5.2 Differentiate between notifications and push technology in terms of the way e-mail is handled on a mobile device. (2)
3.5.3 Explain how a cloud-based service can be used to make large files available to an e-mail recipient, without attaching the files to the e-mail. (2)
3.5.4 Phishing is a technique often used by cyber criminals.
- Explain the term phishing. (2)
- Give ONE example of phishing. (1)
TOTAL SECTION C: 21
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
Some restaurants use a database and an efficient database management system for their administration, orders and point of sale (POS). |
4.1 Name ONE possible role of a database in the POS system of a restaurant. (1)
4.2 The job card below contains information about a waiter in a restaurant for a specific week.
Weekly Job Card for Waiters | Job Card No.: JC10012 | ||
Initial and Surname | K Nel | Waiter ID | W001 |
Permanent Appointment |
| ||
Start of Week: | 1 October 2018 | ||
Hours worked: | |||
Normal hours worked: | 27.5 hours | ||
Overtime hours worked: | 6 hours | ||
Total hours worked: | 33.5 hours | ||
4.2.1 A database with the following tblWaiter table has been designed:
tblWaiter | ||
Field Name | Data Type | |
PK | WaiterID | 4.2.1(a) |
Initial and Surname | Text | |
Permanent Appointment | 4.2.1(b) | |
Use the information provided on the job card to suggest a suitable data type for EACH of the following fields:
- WaiterID (1)
- Permanent Appointment (1)
4.2.2 A report with an alphabetical list of waiters, sorted according to their surnames, is required.
Evaluate the structure of the tblWaiter table and state the problem that will arise when attempting to generate the report. (1)
4.2.3 A second table, tblJobCard, needs to be created to save the remaining information on the job card.
The table below represents a tblJobCard table for the waiters. Redraw this table in your ANSWER BOOK.
tblJobCard | |
Field Name | |
PK | |
NormalHoursWorked | |
: : | : : |
Use the information on the weekly job card (on the previous page) and complete the tblJobCard table in your ANSWER BOOK as follows:
- Identify and add the field name of a suitable primary key (PK).
- List other field names that must appear in the tblJobCard table in addition to the NormalHoursWorked field.
- Identify and add an applicable foreign key (FK). Use the abbreviation FK in the first column.
NOTE:
- Each job card record must relate to a waiter.
- Follow the rules for normalisation. (6)
4.2.4 Draw a simple entity-relationship diagram (ERD) to show the relationship between the tblWaiter table and tblJobCard table. (3)
4.3 The physical integrity of data is just as important as the logical integrity.
4.3.1 Identify ONE issue that could threaten the physical integrity of data in general. (1)
4.3.2 State TWO database design aspects that will ensure logical integrity. (2)
4.4 An advertisement for a database administrator for a restaurant must be placed in the local newspaper. State THREE primary responsibilities of a database administrator. (3)
4.5 State TWO benefits of having a DBMS installed on a server. (2)
4.6 A restaurant group uses a distributed database system.
4.6.1 Suggest ONE reason why a distributed database system would require sophisticated security when compared to a database system stored on a single computer. (1)
4.6.2 What is the benefit of working on a distributed database rather than on a single-server database, from a user's perspective? (1)
4.6.3 Briefly explain how data synchronisation is done when using a partitioning model in a distributed database. (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
The manager of a restaurant approached a novice programmer to improve an outdated program used for reservations. |
5.1 Answer the questions below on general aspects and concepts related to programming.
5.1.1 State TWO guidelines for writing clear and readable source code. (2)
5.1.2 Define the concept of an algorithm in programming. (2)
5.1.3 Debugging is an integral part of programming.
- Explain what is meant by debugging a program. (2)
-
- What is a runtime error? (1)
- Give an example of a type of error that will lead to a runtime error. (1)
5.1.4 Looping is a common programming structure. Compare the structure and execution of a WHILE…DO loop and a REPEAT…UNTIL loop. (2)
5.1.5 Identify the data types for variables X and Y when executing the following two instructions:
- X := 5 mod 2;
AND
Y := 5 mod 2 = 0; (2)
5.2 Bookings are saved in a text file called Bookings.txt. 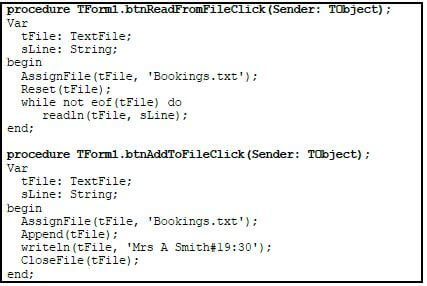
5.2.1 Explain the purpose of the following line of code: AssignFile(tFile,'Bookings.txt'); (2)
5.2.2 State the effect of replacing Append(tFile) with Rewrite(tFile) in the procedure above. (2)
5.2.3 The user needs to save data to a text file. When a button was clicked to write the data to the text file, an Input/Output file error occurred.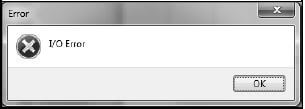
Give a possible reason why the I/O error occurred. (1)
5.3 The algorithm below is used to test the validity of a pin code.
Line | Algorithm_Validate_Pin |
1 | Input PIN |
2 | c ? 0 |
3 | x ? PIN |
4 | Repeat |
5 | x ? x / 10 |
6 | c ? c + 1 |
7 | Until x < 1 |
8 | If c <> 5 then |
9 | Display 'Error in PIN' |
10 | Else |
11 | Display 'PIN Accepted' |
5.3.1 Copy the trace table below into your ANSWER BOOK and complete it to determine the output value if 623 is entered as the pin value. (6)
Pin | x | c | Is x < 1? | Is c <> 5? | Display |
623 | 623 | 0 | |||
5.3.2 Analyse the completed trace table and state what the requirement is for the pin to be valid. (1)
5.4 An algorithm is required to display a pattern, based on the number that was entered indicating the number of lines to be displayed.
Example: If the value 6 is entered, the pattern below must be displayed: 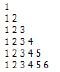
Complete the algorithm from line 3 below to display the pattern based on any input value. (5)
Line | Algorithm_Display_Pattern |
1 | Input number |
2 | Loop counter ? 1 to number |
3 | … |
TOTAL SECTION E: 29
SECTION F: INTEGRATED SCENARIO
QUESTION 6
| The days when restaurants could rely exclusively on good food, an enjoyable ambience and word-of-mouth advertising are quickly coming to an end. More and more restaurants realise that they must use consumer-facing connected technologies, such as websites, social networks and mobile apps, to stay competitive. The manager at a local restaurant decided to implement these technologies. |
6.1 The restaurant created an unsecured hotspot for their guests.
6.1.1 What is a hotspot? (2)
6.1.2 Name the threat for a guest when using an unsecure hotspot. (1)
6.1.3 The use of BitTorrent has been blocked on the network by the firewall.
- What is BitTorrent? (1)
- Give TWO reasons why the restaurant owner insists that BitTorrent be blocked. (2)
6.2 The hotspot in the restaurant is used by business people to connect to their company's VPN.
6.2.1 Write out the abbreviation VPN. (1)
6.2.2 Briefly explain what a VPN is. (2)
6.3 The restaurant upgraded their website.
6.3.1 The URL for a page on the website for this restaurant is given below.
http://www.mydinnersite.com/product.asp?id=12345
- Is this a static or dynamic web page? Motivate your answer. (2)
- How would the URL change to indicate that it is a mobile site? (2)
6.3.2 A paragraph on the home page of the website encourages users to use less power.
- Give TWO hints for saving power when using computing devices. (2)
- Suggest ONE environmentally friendly way in which the restaurant could dispose of its old electronic equipment. (1)
6.3.3 Name the technique that is used to ensure that the restaurant's website is placed as high as possible on a list of search results. (1)
6.4 Cybercrimes, such as DDoS, are common phenomena in cyberspace today.
6.4.1 Briefly explain what a DDoS attack on the restaurant's website might entail.
NOTE: NO marks will be allocated for writing out the acronym. (2)
6.4.2 Suggest TWO measures that the restaurant could implement to prevent cybercrime. (2)
6.5 The restaurant encourages their guests to download the Foursquare app to their mobile devices. 
6.5.1 Explain what a connected app is. (2)
6.5.2 Give TWO reasons why an app is more popular than conventional web pages when using certain websites. (2)
6.5.3
- What type of technology makes location-based services, such as Foursquare, possible? (1)
- State TWO benefits of a check-in service, such as Foursquare, from a restaurant's perspective. (2)
6.6 The process of data mining of data in a data warehouse produced the graph below of the monthly income of the restaurant. 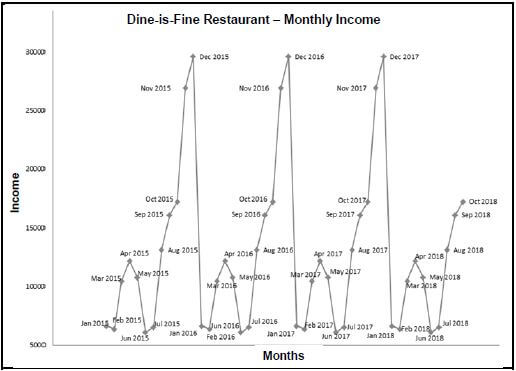
6.6.1 Explain the purpose of a data warehouse. (2)
6.6.2 State TWO roles that people play in the data-mining process. (2)
6.6.3 What is the purpose of data mining in this context? (2)
6.7 An application program for a specific task is required. Both a desktop package and an online application have the functions needed. Both packages involve additional cost.
6.7.1 State TWO advantages of using the online application. (2)
6.7.2 Give ONE reason why the desktop package could be regarded as the preferred choice. (1)
TOTAL SECTION F: 37
GRAND TOTAL: 150