INFORMATION TECHNOLOGY PAPER 2 GRADE 12 MEMORANDUM - NSC EXAMS PAST PAPERS AND MEMOS NOVEMBER 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
NSC EXAMS
PAST PAPERS AND MEMOS NOVEMBER 2018
MEMORANDUM
SECTION A: SHORT QUESTIONS
QUESTION 1
1.1
1.1.1 D ✔ (1)
1.1.2 B ✔ (1)
1.1.3 D ✔ (1)
1.1.4 A ✔✔ (2)
1.1.5 Faulty question – no possible answer
1.2
1.2.1 CMOS ✔ (Also accept: BIOS, Firmware) (1)
1.2.2 Biometrics/Bio authentication/Any specific correct example such as Voice recognition, Face/Iris/Fingerprint-scanning ✔
Do not accept: Digital fingerprint, only fingerprint/face/iris (1)
1.2.3 Digital signature ✔ (1)
1.2.4 Utility ✔ software (1)
1.2.5 Constructor ✔ (1)
1.2.6 Normalisation ✔ (1)
1.2.7 Trace table ✔
Also accept: watch facility of the built-in debugger, debugger (1)
1.2.8 Lossy ✔ compression (1) TOTAL SECTION A: 13
SECTION B: SYSTEM TECHNOLOGIES
QUESTION 2
2.1 Any TWO ✔✔
- Portable/could walk around to the tables and take orders
- Small in size/easy to fit into hand
- No cabling/Wireless/Can link to system using Wi-Fi
- Touch screens make selecting options quick/easy to use
- Saves time/quicker order taking/billing
There must be a reference to a feature of a tablet relating to placing orders
Do not accept: any reference to cost/cheaper
Do not accept: general answer applicable to any device
Do not accept: answers related to the software/GUI (2)
2.2
2.2.1 Any TWO hardware components ✔✔
- CPU/Processor
- Hard drive/storage
- Memory/RAM
- Motherboard (2)
2.2.2 Any TWO actions for disk cleanup ✔✔
- Deletes the temporary internet files
- Empties the recycle bin
- Deletes any other temporary files
- Deletes downloaded files
- Debug dump files
- Delete setup log files
- Delete system error memory dump files
- Delete unused/unnecessary/unwanted files (2)
2.3
2.3.1 Any TWO comparisons between cache and RAM+ ✔✔
- Cache is faster than RAM
- Cache has smaller capacity than RAM
- Cache stores recently used instructions/has a pre-fetch unit while RAM stores the whole program
- Cache found on CPU and RAM on motherboard
- Cache is more expensive per MB than RAM
- Cache is SRAM/static and RAM is DRAM/dynamic
- It is easier to upgrade RAM (2)
2.3.2
- The device driver facilitates communication ✔ between the computer and the printer/hardware ✔
OR - The device driver allows the operating system/computer to communicate/control/manage the hardware/printer
OR - The device driver converts the basic instructions of the operating system/computer to messages that can be interpreted by the hardware component.
Concepts:
- Communication/converting instructions
- Hardware/printer (2)
2.3.3
- To license the use of the software/prevent illegal copies of software from being used ✔
OR - Make all/licensed features of the software available (1)
2.3.4 (a) Any ONE advantage of installing updates: ✔
- Always have latest functions/features
- Bugs and problems are resolved
- Security loopholes are fixed
- Increase performance/work faster (1)
2.3.4 (b) Any ONE disadvantage of installing updates automatically: ✔
- Unexpected/unplanned use of data
- A hastily released update may cause more problems than it fixes/lose existing/familiar/pre-set features
- Unwanted features/preferences
- Slows system down (due to background processes)
- Unwanted restart/inconvenient timing of update (1)
2.3.5 (a) When RAM fills up/is full✔ (1)
2.3.5 (b) The operating system makes use of hard drive space ✔ as extra RAM ✔
OR
- Uses (dedicated) area on HDD/storage
- Moves unused data to HDD/virtual memory where it will easily be accessible again (2)
2.4
2.4.1 Any ONE: ✔
- Physical damage
- Power surge
Also accept examples of physical damage such as dropping a PC can cause a hard drive head crash while transporting/Spilling water on motherboard or HDD with PC case open
Do not accept: Any example or mention of data being damaged (1)
2.4.2 UPS/Invertor ✔ (1)
2.4.3 Backup:
- A duplicate copy ✔ of a file is created on another device/for use when the original copy is damaged or lost ✔
- Archiving: ✔
- Less frequently used/outdated/older files (can be compressed) and stored where they can be retrieved when necessary (3)
2.4.4 Monitors communication with computer/system and the internet/other networks✔ and blocks unauthorised communication✔ by software/malware (2)
TOTAL SECTION B: 23
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
3.1 Any TWO advantages of networks ✔✔
- Fast and efficient communication
- Centralisation of data/data always up to date
- Transfer of files between devices
- Leisure/LAN computing games/Watching movies
- Increased control and security (2)
3.2
3.2.1 An NIC is used to encode or 'convert' the data so that the data can be transmitted over a specific medium and it decodes the data that is received.
Concepts:
- Decode/Encode ✔
- Making communication between devices possible ✔ over a network (2)
3.2.2 Radio waves ✔ (1)
3.3
3.3.1 Fibre Optic cables ✔ (1)
3.3.2 A reason and explanation for addressing poor signal strength: ✔✔ A device/technique with a valid explanation
Also accept : Any TWO of the following-
- Provide sufficient/multiple access points
- Interference by structures should be limited by strategically placing access points/line of sight
- Use a repeater/booster/amplifier/device/router to increase signal strength/WiMax
- Limit the noise by making use of different frequencies (2)
3.3.3 Any TWO reasons for using WiMax: ✔✔
- Greater range
- Faster/faster communication
- Provides higher bandwidth/data transfer
- Better security (2)
3.4
3.4.1 The Semantic Web refers to a web where the content has been optimised for computers and devices to filter content intelligently to be able to navigate without human intervention or involvement.
Concepts: Any TWO for Semantic web ✔✔
- Content optimised
- Filter content intelligently
- Without human involvement (2)
3.4.2 Any ONE reason for using metadata: ✔
- To supply additional data on which specific searches are done.
- Searching is optimised
- Improved results
Accept any explanation that metadata is used to improve results on specific searches. (1)
3.5
3.5.1 POP3 ✔ (1)
3.5.2
- Notification – The user is notified ✔ by a sound or message that a new e-mail has arrived
- Push Technology – The user receives the e-mail ✔/is notified and the e-mail is automatically downloaded to the device (2)
3.5.3 A link/folder ✔ is shared ✔ with another user.
Concepts for making large files available:
- Folder/Link provided
- Storage shared (2)
3.5.4 (a) Phishing is a technique to obtain personal/sensitive information ✔ from a user that appears to be from a legitimate institution in order to trick the user into providing information. ✔
Concepts of phishing:
- provide information about self
- Appears to be legitimate/tricking you (2)
3.5.4 (b) Any ONE example of phishing: ✔
- Request to confirm bank details
- Request to provide pin number for bank cards
- Request to confirm user name and provide password
- Request personal information (1)
TOTAL SECTION C: 21
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1 Any ONE example of the role of a database in a POS ✔
- When a transaction takes place, the database is updated to increase or reduce the stock items/items available/Relevant data obtained at POS is stored for the restaurant
- Customers details are updated as they pay for meals
- Accounting information is updated as customers pay
- Obtain the (latest) item information/prices from the database
- Can do calculations/generate statistics
OR
Any other valid example to do with data in a sales environment (1)
4.2
4.2.1(a) Any ONE ✔
- String
- Text (1)
4.2.1(b) Any ONE ✔
- Boolean
- YesNo
- True/False (1)
4.2.2 The table will be sorted according to initial and not surname. ✔ OR The waiter's initial and surname are captured in one field/Initials captured as the first section of the initial and surname field. (1)
4.2.3
tblJobCard | ||
PK | JobCardNr | ✔(a) |
NormalHoursWorked | ||
WeekStartDate | ✔(b) | |
HoursOvertime | ✔(b) | |
FK | WaiterID | ✔(b) |
(b) ✔ TotalHours is NOT included
(c) ✔ FK correctly identified
NOTE:
- The field names may differ from those in the above table (6)
4.2.4 One Waiter has many Job cards 
Mark allocation
- ✔ Correct ER diagram format
- ✔ One (Waiter) to many (Job_Card) relationship
- ✔ Placing entities in correct relationship/order (3)
4.3
4.3.1 Any ONE issue that threatens physical integrity ✔
- Power failure
- Natural disasters
- Mechanical failure of hardware
- Theft of devices (1)
4.3.2 Any TWO aspects to ensure logical integrity: ✔✔
- Data validation/validation rules
- Each record has a unique primary key
- Normalisation rules applied
- Ensuring referential integrity/Foreign key must refer to an existing record in the other table
- Verification of data (2)
4.4 Any THREE responsibilities of a database administrator: ✔✔✔
- Design the database
- Security of the database/access rights
- Backup and restoration plans and policies/updating software
- Monitoring the performance of the database
- Manage/maintain the database. (3)
4.5 TWO benefits of having a server DBMS:
Managing simultaneous multiple connections to the database to execute the transactions/It will allow a large number of users to connect simultaneously to a database
Concepts:
- Multiple connections/users✔
- Simultaneous access✔ (2)
4.6
4.6.1 Any ONE reason for security: ✔
- Data is transmitted across networks
- Multiple servers are used/Many systems are used
- Create security exposure on multiple fronts/many users (1)
4.6.2 Any ONE benefit of working with a distributed database: ✔
- Faster performance /less congestion
- Less downtime
- If connection is interrupted, database is not damaged/corrupted (1)
4.6.3 Partitioning:
Each site manages its own part of the database ✔ and uploads data to a central database in a scheduled batch process. ✔
Concepts:
- Local data
- Uploaded to central database (2)
TOTAL SECTION D: 25
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1
5.1.1 Any TWO guidelines for readable code: ✔✔
- Commenting of code
- Descriptive variable names
- Modularity
- Indentation
- Open lines between sections
- Collapsible regions (2)
5.1.2 An algorithm is a possible solution to a problem ✔ which contains a set of steps/instructions ✔
Concepts:
- Set of steps/instructions
- To perform a task/solve problem (2)
5.1.3
- Debugging is the technique/process of finding ✔ and resolving ✔ defects/problems/errors/bugs. (2)
- A runtime error is an error that causes termination or break in the running of a program. ✔
Do not accept: Prevents from running (1) - Any ONE example of runtime error: ✔
- Division by 0
- Data type mismatch/typing in a word instead of a number
- Reference to an index in an array that is not part of the declaration
- Attempting to access a resource/file that is not available. Also accept other valid examples. (1)
5.1.4 (2)
WHILE…DO | REPEAT…UNTIL | |
Executed while condition is true | Executed until condition is true | ✔ |
The statements may not be executed at all depending on the condition | Executed at least once irrespective of condition | ✔ |
5.1.5
- Statement 1: variable X := 5 mod 2; Integer/Real/Any number type ✔
- Statement 2: variable Y := 5 mod 2 = 0; Boolean ✔ (2)
5.2
5.2.1 Creates a link between the external/physical/textfile file ✔and file variable/logical file ✔ in the program (2)
5.2.2 Any ONE reason for replacing append with rewrite ✔✔
- The file will be emptied/ the contents will be removed
OR - Rewrite statement will replace/overwrite the current contents of the text file with Mrs Smith.
Do not accept: create a new file (2)
5.2.3 Any ONE reason for I/O Error: ✔
- The file was not closed in during a previous procedure/The file buffer was not cleared/The file is corrupt
- The file was not correctly assigned
- Append or rewrite was not used to open the file/Reset was used to open the file
- Writeln-statement does not refer to the text file (example: writeln(sline))
- The executable file is not in the same directory/folder as the text file
- The file was closed (1)
5.3
5.3.1 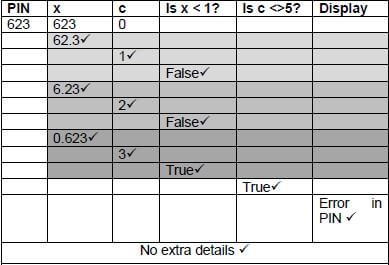
(12/2 = 6)
5.3.2 Any ONE of: ✔
- c = 5
- The user must enter a pin number which contains 5 digits. (1)
5.4 Marking Concepts:
- 1 mark – Inner loop
- 1 mark – Loop to correct counter
- 1 mark – Formulate a display
- 1 mark – Display in correct position
- 1 mark – Reset display variable/ move to next line
Line | Algorithm_Display_Pattern |
1 | Input number |
2 | Loop counter ? 1 to number |
3 | output ? '' ✔ |
4 | Loop counter2 ✔ ? 1 to counter ✔ |
5 | output ? output + counter2 ✔ |
6 | EndLoop counter2 |
7 | Display output✔ |
8 | EndLoop counter |
Concepts:
- 1 mark – Clear output variable in correct position
- 1 mark – Inner loop correct position
- 1 mark – Inner loop (counter2) from 1 to outer loop counter
- 1 mark – Add inner loop counter to output string
- 1 mark – Display output string outside inner loop, inside outer loop
ALTERNATE SOLUTION
Line | Algorithm_Display_Pattern |
1 | Input number |
2 | Loop counter ? 1 to number |
3 | Loop counter2 ? 1 to counter |
4 | Display counter2 (one character) |
5 | EndLoop counter2 |
6 | Move to next line |
7 | EndLoop counter |
Accept any other valid algorithm (5)
TOTAL SECTION E: 29
SECTION F: INTEGRATED SCENARIO
QUESTION 6
6.1
6.1.1 An area where wireless/Wi-Fi/ Internet✔access is available/connected/shared ✔ (2)
6.1.2
- Un-encrypted data/files that are sent can be intercepted ✔
OR - Any other acceptable example of personal information being exposed/hacking/threat of malware/viruses (1)
6.1.3
- A peer-to-peer protocol/network ✔for downloading files from the internet
OR
A file sharing software (1)
6.1.3(b) Any TWO reasons to block BitTorrent ✔✔
- Security issues
- To prevent piracy of software
- Data use/Data cap
- Congestion/Slow down performance of network (2)
6.2
6.2.1 Virtual Private Network ✔ (1)
6.2.2 Allows users to log into a network via the internet with the same security of a LAN.
Concepts: Any TWO ✔✔
- Log in via Internet
- Remotely
- Secured network/connection (2)
6.3
6.3.1 (a) Dynamic page ✔
Any ONE motivation: ✔
- Additional parameters are included that provide information to the software on the server in order to generate a dynamic page.
- ASP (Active Server Pages) are dynamic in nature. (2)
6.3.1 (b) Any ONE for a mobi website ✔✔
- Ends with .mobi
OR - M prefix (2)
6.3.2 (a) Any TWO hints to use less power ✔✔
- Turn off devices when not in use
- Change screen settings to dim
- Use automatic app that puts apps to sleep
- Close unnecessary apps
- Turn off Wi-Fi when not in use
- Turn off Bluetooth/GPS when not in use (2)
6.3.2 (b) Any ONE way to reduce impact on environment ✔
- Send old equipment to e-cycler/for recycling
- Donate useful equipment to others
- Re-use parts, that is still usable, in other computers (1)
6.3.3 SEO/Search (engine) optimisation ✔ (1)
6.4
6.4.1 DDoS:
- Many bot computers are used to bombard the servers hosting the restaurants website with a large number of requests ✔ , the servers are over loaded and cannot respond so the website becomes unavailable ✔
Concepts:
- High number of requests/overloaded with requests
- Website becomes unavailable (2)
6.4.2 Any TWO measures to prevent cybercrime ✔✔
- Install and update anti-virus software
- Use a firewall
- Use a strong password
- Make sure software is updated regularly
- Be aware of trends in cybercrime/Training of staff to be vigilant
- Not answering to phishing mail
- Make use of encryption
- Human verification/Captcha (2)
6.5
6.5.1 The app is connected to the Internet. ✔
The front end of the app is installed on the device, and the data is accessible/stored in the cloud/web server. ✔ (2)
6.5.2 Any TWO reasons for the popularity of apps: ✔✔
- Interface is easier to navigate
- Has a dedicated purpose
- Apps knows where to find data/do not have to enter URL's
- All the interface data already installed on your device/ speeds up responsiveness/use less data
- Can fetch data in the background
- Give notifications
- Can work with syncing device/online storage
- Can use additional sensors like GPS (2)
6.5.3(a) GPS ✔ (1)
6.5.3(b) Any TWO benefits of a check-in service: ✔✔
- Users will know if friends visit restaurant and can join them
- Profiling of customers
- Advertising specific deals/Marketing strategy
- When some-one is near restaurant invite them
- Easily reached for online orders
- Invisible data capture
- Feedback from customers (2)
6.6
6.6.1 The purpose of a data warehouse is to provide storage for large amounts of data ✔ and tools to access the data ✔ for data mining purposes.
Concepts:
- Large amount of data stored
- Using the data (2)
6.6.2 Any TWO roles played by people in data-mining process ✔✔
- Select/gather/prepare data sets
- Interpret/reporting
- Verify data mining results
- Develop data mining software/algorithms
Also accept: specific examples (2)
6.6.3 To identify hidden trends that can be used to make management decisions for example purchasing more stock for the months with high customer volumes.
Concepts:
- Identifying trends/patterns ✔
- Using information in a practical way in the restaurant context ✔
Also accept: Valid examples and explanation of the use of the data in the restaurant context (2)
6.7
6.7.1 Any TWO advantages for using an online application ✔✔
- Don’t need local powerful resources/processing done elsewhere
- Is not installed on system/saves hard disk space
- Always the latest version available/automatically updated
- Run in the browser
- Can be used on any device
- Can be used from anywhere where there is Internet access
- Automatic online backup of data
- Do not accept: Functionality or Cost. (2)
6.7.2 Do not need internet access ✔ to use the software. (1)
TOTAL SECTION F: 37
GRAND TOTAL: 150