COMPUTER APPLICATIONS TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - 2018 SEPTEMBER PREPARATORY EXAM PAPERS AND MEMOS
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATIONS TECHNOLOGY PAPER 2
GRADE 12
NATIONAL SENIOR CERTIFICATE
SEPTEMBER 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25 marks)
SECTION B (75 marks)
SECTION C (50 marks) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin.
- Leave a line after EACH subquestion.
- In general, one mark is allocated per fact. A 2-mark question would therefore require TWO facts, et cetera.
- Write neatly and legibly.
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1–1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 Which ONE of the following is a component of the CPU?
- NIC
- GNU
- ALU
- SCSI (1)
1.2 Which ONE of the following interfaces is used to power a peripheral device?
- SCSI
- USB
- Parallel
- Infra-red (1)
1.3 With what is the icon shown here associated?
- OCR
- RSS
- XTML
- OSS (1)
1.4 Which ONE of the following is a protocol which provides a measure of protection to users of websites where banking is done?
- HTML
- HSDPA
- HTTP
- HTTPS (1)
1.5 Which ONE of the following terms refers to a method of publishing audio files to the Internet, allowing users to receive these files automatically, usually at no cost?
- HDTV
- Blogging
- Webcasting
- Podcasting (1)
1.6 Which ONE of the following icons represents a network drive?
1.7 A small picture that provides a preview of a file without opening the file.
- Thumbnail
- Spyware
- Wizard
- Microwave (1)
1.8 Firmware is ...
- software that has been debugged and is stable.
- oftware that is embedded and cannot be updated.
- software programmed by a large multi-national firm.
- software that is embedded and can be updated. (1)
1.9 Which ONE of the following represents access speed in descending order?
- Magnetic tape, hard disk, RAM, cache
- RAM, cache, magnetic tape, hard disk
- Cache, RAM, hard disk, magnetic tape
- RAM, cache, hard disk, magnetic tape (1)
1.10 Multi-processing is when …
- the computer has more than one processor present.
- many programs are running on one processor.
- a program is broken into different parts to be executed separately.
- the processor switches rapidly between applications. (1)
[10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–P) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 Q.
| COLUMN A | COLUMN B |
2.1 A hardware device used to protect a computer against power surges and spikes |
|
(10 x 1)
[10]
QUESTION 3: TRUE/FALSE
Indicate whether the following statements are TRUE or FALSE. Write ‘true’ or ‘false’ next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (You may not simply use the word ‘NOT’ to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
| QUESTION | ANSWER |
| Google is the world’s most popular search engine. | True |
| A NIC has slots for hardware components such as the CPU. | False – motherboard |
3.1 Companies often release shareware versions of their software for testing purposes, before the software is released for sale. (1)
3.2 Broadband refers to the total amount of data transferred over an Internet connection in a given period of time. (1)
3.3 The term DDR is associated with the RAM of a computer. (1)
3.4 The OLE object data type can be used to add an image to a record in an Access table. (1)
3.5 The image below is an example of a PIN code: 
(1)
[5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEM TECHNOLOGIES
4.1 Computers are made up of many parts.
4.1.1 What is the term used to describe computers in which the box and the screen come as a single unit? (1)
4.1.2 State TWO reasons why it is easier for computers to be made up of many parts, rather than being one functioning unit. (2)
4.2 The CPU does almost all the work in a computer.
4.2.1 There are TWO factors of the CPU that can influence the performance of a computer. Name these TWO factors and describe each briefly. (4)
4.2.2 Briefly explain why the CPU needs cache memory. (2)
4.3 Study the image of an SSD below, which was part of an advertisement, and answer the questions that follow.  (2)
(2)
4.3.1 What does the abbreviation SSD stand for? (1)
4.3.2 Explain why the following will be features of an SSD:
- Silent operation (1)
- Faster performance (1)
4.4 Every now and then your computer displays the following message: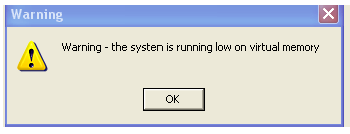
4.4.1 Explain what virtual memory is. (1)
4.4.2 When will the operating system use virtual memory? (1)
4.5 There are many economic considerations when using computers in a travel agency. (1)
4.5.1 Besides switching off all computers at night, state TWO other ways in which the electricity usage of computing devices can be decreased. (2)
4.5.2 Explain TWO ways in which the use of computers will be financially beneficial for the travel agency. (2)
4.6 An incorrect statement was made that the use of an effective backup maintenance program will prevent the hard drive from becoming fragmented.
4.6.1 Describe TWO aspects of an effective backup maintenance program. (2)
4.6.2 What kind of storage device would be used when backing up files from a server? (1)
4.6.3 Define the term disk fragmentation. (1)
4.7 Give THREE reasons why it is necessary to have an operating system installed on a computer by referring to the functions of an operating system. (3)
[25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES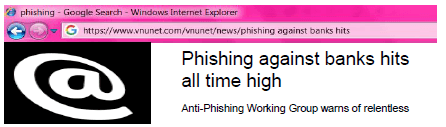
5.1 More and more criminals are making use of the Internet and phishing is becoming a worrying problem.
5.1.1 Write down the URL in the example above. (1)
5.1.2 Explain, by giving an example, how phishing is used to commit a crime. (2)
5.2 Today most computer devices are connected to some type of network, from a Personal Area Network (PAN) to Wide Area Network (WAN).
5.2.1 Explain what a Personal Area Network (PAN) is by referring to its characteristics. (2)
5.2.2 Briefly explain what a Virtual Private Network (VPN) is. (2)
5.2.3 Wi-Fi networks are targets for hackers. Suggest ONE effective way of protecting a Wi-Fi network. (1)
5.3 Web browsers use a technology called web caching.
5.3.1 State TWO possible advantages of using web caching. (2)
5.3.2 Describe TWO ways in which available bandwidth plays a role when watching videos online from services like YouTube. (2)
5.3.3 Define the term protocol in a network. (1)
5.3.4 What protocol will be used to send files between remote computers that have an Internet connection? (1)
5.4 What type of network would use a 3G modem? (1)
[15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 The school has to gather information about why so many learners want to change their subjects in Grade 11.
Study the questionnaire below and answer the questions that follow.
Questionnaire: Why learners change their subjects in Grade 11
|
6.1.1 Identify any ONE closed question in the questionnaire.
Simply write down the question number as your answer. (1)
6.1.2 Why might the answers given for Question 2 on the questionnaire be difficult to analyse in a spreadsheet? (1)
6.1.3 Explain why Question 4 on the questionnaire is not a good survey question. (1)
6.1.4 The questionnaire does not have an introduction.
Give ONE element that should be included in the introduction of a survey. (1)
6.2 Give ONE disadvantage of conducting a survey online; that is by using a website for people to post their responses. (1)
6.3 What is metadata? Also give a suitable example of metadata in your answer. (2)
6.4 Quality data is needed for useful information to be extracted from a database.
List THREE characteristics of quality data. (3)
[10]
QUESTION 7: SOCIAL IMPLICATONS
7.1 Sea Shepherd Conservation Society (SSCS) is considering creating a website to help market the safeguarding of ocean ecosystems.
Give ONE potential advantage and ONE potential disadvantage of using a website for marketing. (2)
7.2 The website created for safeguarding ocean ecosystems has a Privacy Policy. Below is an extract from it.
Kids and Privacy For children, who visit our site, special rules apply. We do not request |
Discuss the dangers for children if their ʽprivacy’ is not guaranteed (2)
7.3 The Sea Shepherd Conservation Society (SSCS) purchased an antivirus program. Can they install it on all the computers, seeing that the computers all belong to the same business?
Motivate your answer briefly. (2)
7.4 State TWO negative implications of 3D printers, which are becoming more common. (2)
7.5 Many cameras have the capability to ‘geotag’ photographs. (1)
7.5.1 Explain the term geotagging. (1)
7.5.2 Why do the SSCS discourage children from placing geotagged photographs of whales on social media? (1)
[10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 The electronic form below was designed to be used for online registration of exhibitors.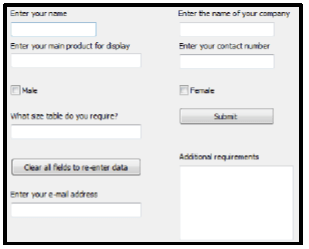
8.1.1 Critically comment on the layout of the components of the form, by indicating TWO ways in which the layout can be improved. (2)
8.1.2 Critically evaluate the components on the form that are used to obtain data from the user. Identify ONE poorly chosen component and suggest a more suitable component. (2)
8.2 Study the spreadsheet below and answer the questions that follow.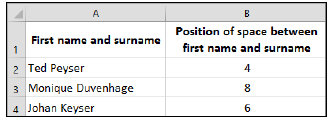
8.2.1 Give only the name of the function that was used in column B to obtain the position of the space between the first name and the surname. (1)
8.2.2 Give the most likely reason for obtaining the position of the space between the first name and the surname. (1)
8.3 The function below was used in a spreadsheet to count the number of cells in the range B3:B10 that contain amounts less than R100.00.
=COUNTA(B3:B10,>R100)
Give TWO reasons why this function will NOT work correctly, and give the correction in each case. (2)
8.4 Study the screenshot extract of a database table below and answer the questions that follow.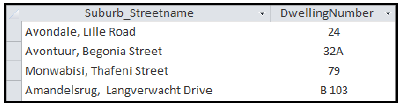
8.4.1 Which criterion would you enter in a query to extract suburbs starting with ‘A’? (2)
8.4.2 State which data type was used for the field DwellingNumber. (1)
8.4.3 Which criterion would you enter in a query to find those records that do not have a value entered in the DwellingNumber field? (1)
8.5 A learner created a web page using hypertext markup language (HTML). When he double-clicked the file in Windows Explorer to view the page in a browser, the file opened in Notepad.
Briefly explain what mistake was made in saving the file, and how to fix the mistake so that the web page may be viewed in a browser. (2)
8.6 Examine the screenshot below of a table on a web page that was created
using HTML and answer the question that follows.
| Worm | A computer malware that is able to distribute itself over a network, normally via email, without a person having to run an uninfected program |
Only the word ‘malware’ (in the second column) should be in italics. However, all the text after this word is italicised as well.
What is the most likely cause of this error? (1)
[15]
TOTAL SECTION B: 75
SECTION C
QUESTION 9: INTEGRATED SCENARIO
The school will host a website and be a part of a social network to allow for players to register and to play games online.
9.1 For the current gaming event gamers were informed that they can configure the settings on their computers to optimise game play.
Explain what can be done to save bandwidth while streaming. (1)
9.2 The CAT learners will make gamers aware of the NFC (near field communication) feature that is available on their tablets and other hand-held devices.
9.2.1 Give TWO examples of what NFC (near field communication) can be used for. (2)
9.2.2 NFC originated from a communication standard that uses radio waves. What is this communication standard called? (1)
9.3 Separate versions of some of the gaming software applications have been developed to provide for different operating systems, such as Android and IOS.
9.3.1 Motivate why the same application needs to be programmed differently for different operating systems. (2)
9.3.2 An important feature of an operating system is backward compatibility.
Use an example to explain the concept of backward compatibility. (2)
9.3.3 To customise the mouse icon for the gamers, where would you go to change the icon to a horse? 
(1)
9.4 One of the gamers will use the headset in the illustration below.
9.4.1 The headset supports plug-ins. Explain what a plug-in is. (1)
9.4.2 How does the fact that the headset supports plug-ins benefit the gamer? (1)
9.5 These types of devices normally contain sensors.
Name TWO possible types of sensors found on gaming devices. (2)
9.6 Gamers will be required to locate at least one Pokémon at some stage during the gaming event. To take part in the Pokémon GO location-based augmented reality (AR) game, a mobile device with GPS technology is required.
9.6.1 What does the abbreviation GPS stand for? (1)
9.6.2 Name TWO disadvantages of Augmented Reality (AR). (2)
9.7 Some gamers are unable to use their hands. Alternative measures have been investigated. Motivate TWO alternative input devices, for gamers who are physically handicapped, to make use of the games. (2)
9.8 Some of the gamers are not comfortable with using computers or do not have computers at home, while the other are very comfortable and have been working on computers from a very young age. What is this ‘gap’ called? (1)
9.9 The Internet of Things (IoT) is one solution for information overloading.
9.9.1 Briefly explain the term Internet of Things. (2)
9.9.2 Name TWO advantages of the Internet of Things. (2)
9.9.3 What is meant by information overloading and what is the effect on the user? (2)
[25]
QUESTION 10
The school hosts an exhibition that will showcase a variety of topics and new technologies. A separate help desk will be available to assist with any queries.
10.1 Each exhibitor will be issued with a wrist band containing an RFID tag to allow the exhibitor access to the canteen for lunch. Motivate the use of RFID tags instead of tickets with bar codes. (2)
10.2 One of the exhibitors will do a presentation on the capabilities of intelligent self-driven vehicles.
10.2.1 State ONE essential intelligent task that the software designed for a self-driven vehicle should be able to perform. (1)
10.2.2 Self-driven vehicles use GPS devices.
Name TWO other hardware devices that this type of vehicle should have in order to perform the intelligent tasks required. (2)
10.2.3 It has been stated that there will be fewer accidents with self-driven vehicles as human error will be eliminated.
State ONE disadvantage of self-driven vehicles. (1)
10.3 A cybercrime expert will compile a poster about computer crimes committed by means of ICT as a tool.
10.3.1 Discuss TWO ways in which cybercrime can have a negative influence on a business. (2)
10.3.2 Explain what a denial-of-service attack is. (2)
10.4 An environmental agency requested a stand to promote the responsible use of computers in the environment.
Suggest TWO ways in which the negative effects of computers on the environment can be minimised. (2)
10.5 There are several free Wi-Fi hotspots with limited data per day that the exhibitors can use.
10.5.1 What is a public Wi-Fi hotspot? (2)
10.5.2 Motivate the reason for limiting the data per day for the exhibitors of these Wi-Fi hotspots. (1)
10.6 The school has hired security consultants to advise on many security aspects to help protect exhibitors from computer theft.
10.6.1 Name THREE items of personal information that should NOT be posted on a social networking site. (3)
10.6.2 Name TWO types of computer criminals. (2)
10.7 All registration information for the exhibitors has been captured in a database table. Which field properties of the data types need be changed to:
10.7.1 Limit the First Name field to 15 characters. (1)
10.7.2 Set the status as “Finished” for all exhibitors. (1)
10.7.3 Restrict input in the Gender field to “male” and “female” only. (1)
10.7.4 Allow only two letters and two numbers to be used as the registration number. (1)
10.7.5 Ensure that the ExhibitorsID field cannot be left blank. (1)
[25]
TOTAL SECTION C: 50
GRAND TOTAL: 150