INFORMATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - AMENDED SENIOR CERTIFICATE EXAMS PAST PAPERS AND MEMOS MAY/JUNE 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupINFORMATION TECHNOLOGY
PAPER 2
GRADE 12
AMENDED SENIOR CERTIFICATE EXAMS
PAST PAPERS AND MEMOS
MAY/JUNE 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of SIX sections:
SECTION A: Short Questions (16)
SECTION B: Systems Technologies (24)
SECTION C: Communication and Network Technologies (22)
SECTION D: Data and Information Management (23)
SECTION E: Solution Development (25)
SECTION F: Integrated Scenario (40) - Answer ALL the questions.
- Read ALL the questions carefully.
- The mark allocation generally gives an indication of the number of facts/reasons required.
- Number the answers correctly according to the numbering system used in this question paper.
- Write neatly and legibly.
QUESTIONS
SECTION A: SHORT QUESTIONS
QUESTION 1
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A to D) next to the question numbers (1.1.1 to 1.1.3 and 1.2.1 to 1.2.2) in the ANSWER BOOK, e.g. 1.1.4 D.
1.1 1.1.1 The most common protocol used to send e-mail is known as …
- POP3
- FTP
- SMTP
- VoIP (1)
1.1.2 Which ONE of the following refers to an encryption process used to authenticate the identity of the sender of an e-mail message?
- Digital certificate
- Digital fingerprint
- Digital handshake
- Digital signature (1)
1.1.3 Which ONE of the following refers to a data structure that is non-volatile?
- String
- One-dimensional array
- Two-dimensional array
- Text file (1)
1.2
1.2.1 The following declaration statements are provided:
var
K : integer;
R : real;
The assignment statements below have been coded:
- K := 25 div 4;
- K := R + 2;
- K := R div 5;
- R := 15 mod 4;
Which of the above assignment statements will cause a compilation/ syntax error?
- (i) and (iii)
- (i) and (iv)
- (ii) and (iii)
- (ii) and (iv) (2)
1.2.2 Determine the value of sAnswer after the execution of the statements below.
sLine := 'Information Technology is great';
sAnswer := copy(sLine, pos('n',sLine)-1, 4);
Insert('T',sAnswer, 2);
- nfo T
- ITnfo
- nfoT
- nTfo (2)
1.3 Give ONE word/term for each of the following descriptions. Write only the word/term next to the question numbers (1.2.1 to 1.2.10) in the ANSWER BOOK.
1.3.1 Web applications designed to deliver the functions and features of a traditional desktop application online. The interface is generated locally by your web browser. (1)
1.3.2 An type of information system that gathers, analyses and presents information for the management, operations and planning levels of an organisation. This helps to make decisions about problems that may be rapidly changing. (1)
1.3.3 Downloaded software that bombards the user with advertisements (1)
1.3.4 A remotely controlled network of zombie computers (1)
1.3.5 A type of memory that stores the BIOS settings (1)
1.3.6 Testing the accuracy of captured data by checking it against the source of the data (1)
1.3.7 Someone who gains unauthorised access to data in order to steal data or someone who makes unauthorised changes to data (1)
1.3.8 Specialised hardware and software designed to be used at till points (1)
1.3.9 E-mail sent to people that advertise products that were not requested (1)
TOTAL SECTION A: 16
SECTION B: SYSTEMS TECHNOLOGIES
QUESTION 2
2.1 Computers have modular designed motherboards.
2.1.1 Give ONE advantage of a modular designed motherboard. (1)
2.1.2 Name ONE component/device that could be plugged into any of the ports in the rear of a standard desktop computer. (1)
2.1.3 What is the purpose of RAM? (1)
2.1.4 Explain what CPU cache memory is and how it impacts the processing speed of a computer. (3)
2.1.5 Explain the concept of multiprocessing. (2)
2.2 The younger generation of computer users often prefer to use mobile devices rather than desktop computers.
2.2.1 Except for mobility, give TWO other reasons why mobile devices may be preferred to desktop computers. (2)
2.2.2 State TWO factors that limit the use of mobile devices. (2)
2.2.3 Give TWO reasons for using an SSD instead of a conventional hard drive in a mobile device. (2)
2.3 The use of cloud applications, such as Google Docs, as well as other types of Software as a Service (SaaS) is popular practice nowadays.
2.3.1 What is a cloud application? (1)
2.3.2 Give TWO reasons for using SaaS instead of standard desktop software. (2)
2.3.3 State ONE disadvantage associated with the use of cloud computing. (1)
2.3.4 Cloud computing relies on virtualisation technologies. State TWO ways in which virtualisation techniques are used by companies that offer cloud services. (2)
2.4 The library at a school uses an online digital media repository.
2.4.1 What is an online digital media repository? (1)
2.4.2 Give TWO reasons for using a media repository. (2)
2.5 The library at the school wants to implement a backup policy to backup their data. Give ONE reason why an online backup service is recommended. (1)
TOTAL SECTION B: 24
SECTION C: COMMUNICATION AND NETWORK TECHNOLOGIES
QUESTION 3
The diagram below illustrates the network of a small business. 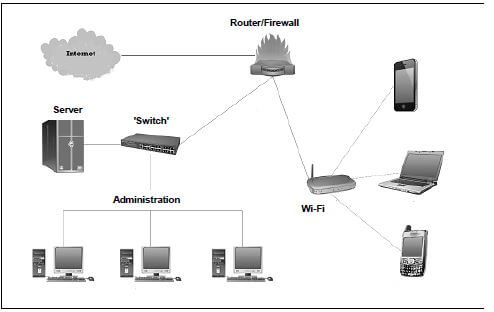
3.1 The computers in the cabled network are used by all staff members and the WLAN is used by clients.
3.1.1 Give ONE reason why a wireless network is more suitable for the clients. (1)
3.1.2 Give ONE reason why all devices must have a unique IP address. (1)
3.1.3 Give TWO possible reasons why clients using the WLAN could experience slow connection speeds sometimes. (2)
3.2 The LAN in the administration office uses a client-server model and provides internet access.
3.2.1 Name TWO services that can be provided by an ISP besides the connection to the internet. (2)
3.2.2 State TWO benefits of using an ADSL connection. (2)
3.2.3 Explain the function of the switch as part of the LAN. (2)
3.2.4 The LAN to be used by the administration staff uses fibre-optic cables.
- What medium is used by fibre-optic cables to transmit signals? (1)
- Give TWO reasons why fibre-optic cables will be more suitable for use in a LAN than UTP cables. (2)
3.3 It is a requirement that all computers in the LAN are thin clients and that a UPS be installed for the server.
3.3.1 Explain what a thin client is. (1)
3.3.2 Give TWO reasons why the use of thin clients is often preferred. (2)
3.3.3 What is the purpose of a UPS? (1)
3.4 Some staff members have access to the virtual private network (VPN) of the business.
3.4.1 Give ONE practical example of how the staff can benefit from using the VPN. (1)
3.4.2 Name the technique that is used to maintain the privacy of information during transmission on a VPN. (1)
3.4.3 Give TWO possible reasons why a staff member may encounter problems trying to connect to the VPN. (2)
3.5 The size of an e-service can range from very small to very large. What is the term used to describe the capability of a system to handle a reduction or a growth of its workload, or its potential to be reduced or enlarged to accommodate a possible reduction or growth of its workload? (1)
TOTAL SECTION C: 22
SECTION D: DATA AND INFORMATION MANAGEMENT
QUESTION 4
4.1 A library uses a relational database to have a record of books that have been borrowed.
4.1.1 Explain what a relational database is. (2)
4.1.2 Explain why record locking is necessary when different staff members are working on the same table in the database. (2)
4.1.3 Besides planning and creating a database, name TWO other tasks that a database administrator has to perform as part of his/her duties. (2)
4.2 The database of the library has two tables: tblStudents and tblBooksBorrowed. The table tblStudents keeps record of the students who use the services of the library. The table tblBooksBorrowed keeps record of the books borrowed by a student.
The relationship between the tables is given below. 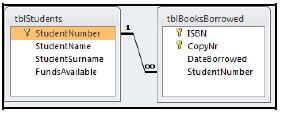
4.2.1 The student number in the tblStudents table is the primary key. Explain what a primary key is in this context. (1)
4.2.2 What is the StudentNumber field in the tblBooksBorrowed table called in terms of the relationship between the tables? (1)
4.2.3 A composite primary key is used in the tblBooksBorrowed table. What is meant by a composite primary key? (1)
4.2.4 Identify and motivate the specific relationship that exists between the tblStudents and the tblBooksBorrowed tables. (2)
4.2.5 Referential integrity was enforced when the relationship between the tables was created. Why was this done? (2)
4.2.6 The extract of data below shows some of the records in the two tables. 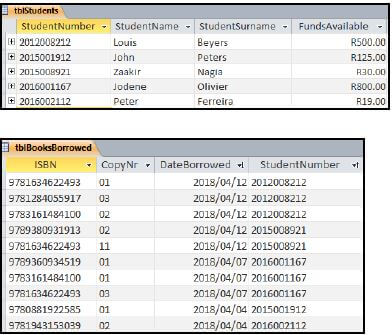
- Write an SQL statement to display the name, surname and funds available of all the students with R30 or less in their account. (3)
- Write an SQL statement to display the student number and number of books borrowed of all the students who have more than two books on loan. The number of books borrowed must be shown in a field called NumberBorrowed. (7)
TOTAL SECTION D: 23
SECTION E: SOLUTION DEVELOPMENT
QUESTION 5
5.1 Give a reason for the use of EACH of the following structures in a Delphi program:
5.1.1 FormCreate event (1)
5.1.2 A WHILE loop instead of a FOR loop (1)
5.1.3 Ord function (1)
5.2 Students can log in on the university's website or portal to access resources.
5.2.1 Below is an incomplete class diagram for an object class that was created to record access to a website.
StudentEntry |
Attributes |
-fStudentCode(String) |
-fStudentName(String) |
-fDateOfEntry |
-fTimeOfEntry |
-fLoginNumber(integer) |
Methods |
+Constructor Create |
+toString:String |
- An object's attributes should be encapsulated. Define the term encapsulation. (2)
- Suggest a suitable data type for the fDateOfEntry attribute. (1)
- Define a method that can be added to the class diagram to return the student code of the object. (1)
- Define a method that can be added to the class diagram that receives a parameter and changes the login number. (1)
- What type of method is the toString method? (1)
5.2.2 The student numbers of at least 1 000 IT students are stored in an array called arrStudNumbers. The final results for the Mathematics module are stored in a parallel array called arrMathResults.
Example of the first five student numbers and results in the respective arrays: 
The following code was used to enter a student number and update the student's result: 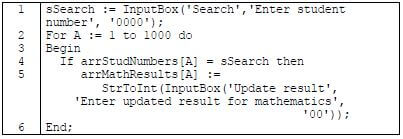
- Name the type of search technique used in the code above. (1)
- Criticise the program code provided in terms of good and effective programming techniques. (1)
- Write pseudo code that uses a more effective search technique that will terminate the search process when the update has been done. (8)
5.3 The following segment of programming code was used to generate a student code: 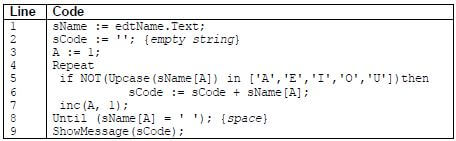
Copy and complete the trace table below to determine the output of this program segment if the name entered into the edit box edtName is 'Mark Simon'.
sName | NOT (Upcase (sName[A]) in ['A','E','I','O','U']) | sCode | A | Is sName[A] = ' '? | Display |
Mark Simon | '' | 1 | |||
True | |||||
M | |||||
2 | |||||
False | |||||
(6)
TOTAL SECTION E: 25
SECTION F: INTEGRATED SCENARIO
QUESTION 6
The local university is upgrading their library and the ICT infrastructure. The university's website can be used to check timetables and make reservations for access to the research section of the library. |
6.1 An AUP document has been compiled for the library. One of the points listed in the document states that, where possible, electronic documents should be used instead of printed documents.
6.1.1 What does the acronym AUP stand for? (1)
6.1.2 Briefly explain the purpose of having an AUP. (2)
6.2 Some of the electronic documents are stored in an online storage facility to facilitate file syncing. Explain the concept of file syncing. (2)
6.3 The university employed a web designer to redesign the website.
6.3.1 Name TWO skills that a web designer would need when creating a website. (2)
6.3.2 Students can access the website from their mobile devices. State TWO factors that a web designer must take into consideration when designing websites to be accessible from mobile devices. (2)
6.4 Some students watch videos on their electronic devices as part of research projects. The videos are saved with metadata on an SSD.
6.4.1 What is metadata? (1)
6.4.2 Suggest a suitable format for the compression of videos. (1)
6.5 Schedules for short-course lectures and webinars are displayed on the website.
6.5.1 What is a webinar? (1)
6.5.2 How can the students remain informed of changes in the schedules without visiting the website? (1)
6.6 Some students use open-source operating systems, such as Linux, while others use proprietary systems, such as Microsoft Windows 10.
6.6.1 State THREE functions of an operating system. (3)
6.6.2 Give ONE reason for using a proprietary operating system rather than an open-source operating system. (1)
6.7 The library can use RFID tags embedded in books and RFID scanners at library exits and return points. Stock takes (audits) in a library can be facilitated by the use of mobile RFID rack readers, enabling an inventory to be done on an entire shelf within seconds, without a book being taken off the shelf.
6.7.1 Write out the abbreviation RFID. (1)
6.7.2 Explain the difference between a passive RFID tag and an active RFID tag. (3)
6.7.3 The use of RFID student cards eliminates the need to type in a student number. The card is scanned using an RFID reader. Give TWO reasons why manual data input (e.g. a person at a keyboard entering data) is one of the least popular data capture methods used today. (2)
6.8 Although e-mail is one of the most popular uses of the internet, users are often frustrated by the lack of netiquette. What is netiquette? Give an example as part of your answer. (2)
6.9 ICT has revolutionised the way in which people use social media to communicate. State ONE way in which social networking can impact negatively on cultures around the world. (1)
6.10 University staff want to be sure that information sent over the network will be safe and secure.
6.10.1 Public key encryption will be used to secure the data.
- Explain what the term encryption means. (2)
- Explain how public key encryption works. (3)
6.10.2 A yellow lock is displayed on the URL bar when the user opens the university's website. ![]()
- What other visual indication is displayed that indicates that the website is secure, besides the yellow lock? (1)
- When a user clicks on the yellow lock, the following dialogue box is displayed:
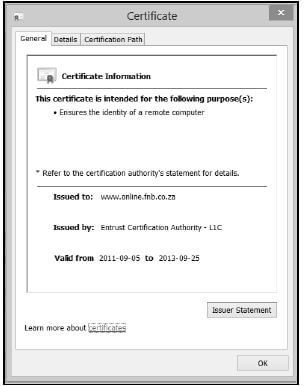
Which TWO pieces of information on the certificate can be used to verify that the website is legitimate? (2)
6.10.3 Staff members are often warned against social engineering.
- Explain what social engineering is. (2)
- What is a consequence of falling victim to social engineering? (1)
6.11 Green computing has become a focal point in the ICT field.
6.11.1 Define the term green computing. (1)
6.11.2 Suggest any TWO initiatives for the library to implement green computing. (2)
TOTAL SECTION F: 40
GRAND TOTAL: 150