COMPUTER APPLICATIONS TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - NSC EXAMS PAST PAPERS AND MEMOS NOVEMBER 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATIONS TECHNOLOGY
PAPER 2
GRADE 12
NSC EXAMS
PAST PAPERS AND MEMOS
NOVEMBER 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A (25)
SECTION B (75)
SECTION C (50) - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- Generally, one mark is allocated per fact. A 2-mark question would therefore require TWO facts, etc.
- All answers MUST be related to Computer Applications Technology.
- Answers such as 'cheaper', 'slower'/'faster', 'easier', etc. will ONLY be accepted if it is used together with a reason or an explanation.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are given as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question numbers (1.1 to 1.10) in the ANSWER BOOK, e.g. 1.11 D.
1.1 Which ONE of the following is both an input device AND an output device?
- Stylus
- Touch screen
- Laser printer
- Fingerprint scanner (1)
1.2 The digital divide refers to the gap between people who …
- have access to ICTs and people without access to ICTs.
- live in rural areas and people who live in cities.
- receive education and people who do not receive education.
- use mobile devices and people who use desktop computers. (1)
1.3 Which list of wireless technologies below is sorted from the longest range to the shortest range?
- NFC, WiMAX, Bluetooth
- WiMAX, NFC, Bluetooth
- Bluetooth, NFC, WiMAX
- WiMAX, Bluetooth, NFC (1)
1.4 Plug-and-play technology …
- allows only hand-held gaming consoles to connect to a computer.
- enables new devices to connect to computers without USB ports.
- installs the driver automatically when a new device is connected.
- allows only one storage device at a time to be connected to a computer. (1)
1.5 Which ONE of the following is NOT a benefit of grid computing?
- It allows processing of high volumes of data.
- It saves on electricity costs and data usage costs.
- The number of computers used in a grid can differ.
- It combines the processing power of many computers. (1)
1.6 A … is the most secure way to protect a smartphone against unauthorised access.
- USB connection
- screen lock pattern
- password
- fingerprint (1)
1.7 Which ONE of the following is a wild card character that can be used when you search for a file?
- *
- @
- #
- & (1)
1.8 An audio file that can be downloaded from the internet to a device is called a ...
- blog.
- podcast.
- vlog.
- vodcast. (1)
1.9 An e-mail could remain in a sender's Outbox because the …
- sender did not specify the recipient's e-mail address.
- recipient's e-mail address was spelled incorrectly.
- sender was not connected to the internet at the time.
- recipient's mailbox is full and cannot receive more e-mail. (1)
1.10 A database query displays the following records when it runs:
Name | Surname | Amount |
Lego | Komane | R 8 000.00 |
Joseph | Sithole | R 21 000.00 |
Zaheed | Kamir | R 15 870.00 |
Carel | Fourie | R 7 800.00 |
Which ONE of the following criteria was used in the Amount field to select the records that are displayed?
- >=7 800 And <21 000
- >7 800 And <=21 000
- >=7 800 And <=21 000
- <=7 800 And >=21 000 (1) [10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches a description in COLUMN A. Write only the letter (A–T) next to the question numbers (2.1 to 2.10) in the ANSWER BOOK, e.g. 2.11 U.
COLUMN A | COLUMN B |
2.1 Using ICTs to enable you to work away from your office |
(10 x 1) [10] |
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write 'true' or 'false' next to the question numbers (3.1 to 3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (Do NOT simply use the word 'NOT' to change the statement. NO mark will be awarded if only FALSE is written.)
EXAMPLES:
QUESTION | ANSWER |
Computer program instructions are executed by the CPU. | True |
An NIC has slots for hardware components. | False – motherboard |
3.1 Application software manages all the activities on a device. (1)
3.2 A UPS allows the computer to run for a limited time so that documents can be saved and applications closed when a power outage occurs. (1)
3.3 Phishing is a type of malware that demands a payment to restore the files it illegally encrypted. (1)
3.4 Social engineering is a legal way of obtaining financial support for a project by raising contributions online from a number of people. (1)
3.5 A calculation that includes all the records in a database report should be done in the report footer. (1) [5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 What is the purpose of a driver program? (2)
4.2 An accounting clerk uses a keyboard that does not have a numeric keypad. Explain why a keyboard with a numeric keypad would be a better option. (2)
4.3 A list of files stored on a computer is shown below. 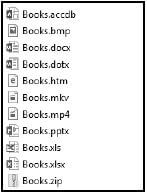
4.3.1 What type of content will be found in a file with a .mp4 extension? (1)
4.3.2 Give the full name of the spreadsheet in the list of files above that has a newer file format. (1)
4.3.3 Books.dotx is a template file. What is a template file? (1)
4.3.4 Give ONE reason for creating a compressed file, such as Books.zip. (1)
4.4 State TWO advantages for notebook computers going into sleep mode. (2)
4.5 Explain the term backward compatibility. (2)
4.6 Different types of memory/storage are often used on one device.
4.6.1 Give an example of memory that loses its contents if the computer is switched off. (1)
4.6.2 Give TWO reasons why modern mobile devices are more likely to have built-in solid state drives instead of hard disk drives. (2)
4.6.3 Why is Blu-Ray storage popular with computer gamers? (1)
4.6.4 State TWO ways in which data, stored on an SD card in a camera, can be transferred to a personal computer. (2)
4.7 Give THREE examples of accessibility software features that are part of the operating system. (3)
4.8 State TWO ways to access a website without typing in the URL or the IP address in a web browser. (2)
4.9 One of the functions of the operating system is to provide a user interface. Give TWO additional basic functions of the operating system. (2) [25]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 State TWO factors that should be carefully considered when choosing an ISP (internet service provider), other than cost. (2)
5.2 Give TWO limitations of using an ADSL connection. (2)
5.3 Name TWO technologies/protocols that use encryption to secure communication over a wide-area network. (2)
5.4 What are the advantages of a wireless LAN over a wired LAN? (2)
5.5 Explain why large videos stream slowly during office hours, but the same videos will stream faster late at night, even though you use the same computer and the same internet connection. E-mail and file downloads, however, are equally fast during the day or night. (3)
5.6 You use your smartphone only for instant messaging and cellphone calls. The monthly data cap of 5 GB on your smartphone has been used up before the end of the month. Give TWO possible reasons why the data cap did not last the whole month. (2)
5.7 State TWO netiquette rules for a group chat on social media. (2) [15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 The example below shows three questions that were part of a questionnaire for learners taking Mathematics as a subject at primary school.
QUESTIONNAIRE |
Answer the following questions based on the questionnaire above.
6.1.1 Identify ONE open-ended question from the questions above. (1)
6.1.2 Which question (Question 1, Question 2 or Question 3) in the questionnaire is more likely to give usable data if primary school learners completed the questionnaire? (1)
6.2 State TWO ways in which a teacher can check if a learner plagiarised from the internet. (2)
6.3 Give TWO tips that learners can use to check the quality of information when researching a topic on the internet. (2)
6.4 Name TWO broad categories of spreadsheet features/options that can be used to interpret data from a questionnaire. (2)
6.5 Why do you need a citation in the body of a research report and a bibliography at the end of a research report? (2) [10]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 A user sometimes shares his/her personal details when using social media, e.g. a cellphone number or an e-mail address.
Why should a user think carefully before sharing this information on social media websites? (1)
7.2 State TWO ways in which a system administrator can protect a network from hackers. (2)
7.3 Why would a research company benefit from using 'big data'? (2)
7.4 Explain why you want your friend to use a private browsing mode, such as incognito mode, when he uses your computer to log onto his web-based e-mail service. (2)
7.5 A school wants to promote e-learning by using the BYOD concept on a Wi-Fi network.
7.5.1 Explain the BYOD concept. (Do NOT only write out the acronym.) (1)
7.5.2 State TWO problems that this school could experience when implementing a BYOD policy. (2) [10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 Give ONE reason why words such as 'color' and 'favor' (instead of the expected 'colour' and 'favour') are NOT identified as spelling errors when you do a spell check on a word processing document. (1)
8.2 Give TWO possible reasons why a main mail merge document fails to load the data source when you are trying to open it. (2)
8.3 The database table below was created to capture learners' test marks. Copy the table below into your ANSWER BOOK and complete it by adding a suitable data type for EACH of the THREE remaining fields (8.3.1 to 8.3.3). (3)
Field Name | Data Type |
Name | Text |
ID Number | 8.3.1 |
Date of Test | 8.3.2 |
Mark | 8.3.3 |
8.4 How would you ensure that another user can NOT enter data into certain cells in a spreadsheet? (1)
8.5 The following error message is displayed in a spreadsheet cell: #VALUE! Explain how you would correct the error that causes the message above to appear. (2)
8.6 The two underlined arguments in the function below prevent the function from working correctly when copied down:
=VLOOKUP("A1", L1:M5, 2, FALSE)
Suggest ONE correction for EACH of the TWO underlined arguments. (Do NOT refer to the spaces in the function in your answer.) (2)
8.7 Suggest ONE function that can be used to replace the whole formula in EACH of the following cases:
8.7.1 =A1&A2&A3 (1) 8.7.2 =(A1+A2+A3+A4+A5)/5 (1) 8.8 Explain the purpose of EACH of the following HTML tags:
8.8.1 <a name="NAME"> (1)
8.8.2 <a href="#NAME"> (1) [15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
Learners use digital technologies that could have a positive and a negative impact on their lives. You are required to answer some questions about digital technologies.
9.1 Most learners use mobile devices to browse the Web.
9.1.1 Some learners confuse the terms internet and World Wide Web. Explain the terms internet and World Wide Web. (2)
9.1.2 What term is used to describe the concept where a learner is able to use more than one app on the same device at the same time? (1)
9.1.3 Give ONE reason why a web page does not open in the browser on a mobile device. (1)
9.1.4 State ONE argument against accessing the internet using a public Wi-Fi hotspot. (1)
9.2 Internet connectivity at the school makes it possible for learners to access social media websites using the school's computers.
9.2.1 Recommend TWO rules that should be included in a school's social media policy. (2)
9.2.2 Learners may be click-jacked when browsing a social media website. Explain the term click-jacking. (2)
9.2.3 Learners regularly share photos on social media. Name TWO features of a smartphone that determine how many photos can be saved on it. (2)
9.2.4 When you click on a Facebook page, the browser shows a message offering to install a plug-in. Explain what a plug-in is. (2)
9.3 Learners often use the school's mobile devices for long periods of time each day to enrich their learning experience in the classroom.
9.3.1 State TWO ways in which learners can prevent eyestrain when spending a lot of time on these mobile devices. (2)
9.3.2 State TWO possible mental health issues that the continuous use of technology can cause. (2)
9.3.3 State TWO positive effects that technology has on education. (2)
9.3.4 Suggest TWO ways in which teachers can prevent learners from being distracted when using the school's mobile devices in the classroom. (2)
9.4 A word processing app was used to create the image below to compare the popularity of social networks, that is Twitter 28%, Facebook 67% and Instagram 9%.
Suggest a combination of TWO word processing techniques to correct the display of the image below so that all the text in the objects is clearly visible.
NOTE: Do NOT refer to 'cut and paste', 'retyping' or 'recreating' in your answer. 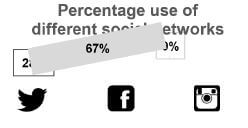 (2)
(2)
9.5 A Grade 12 CAT learner included the image below as part of his/her PAT report to show his/her research results.
Discuss TWO reasons why the information in the image is difficult to interpret.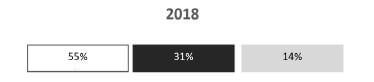 (2)
(2)
[25]
QUESTION 10: INTEGRATED SCENARIO
AcademyOne is a large academic library that sends books to smaller libraries across the country. You are required to assist the staff with ICT-related issues. Employee data and financial data must be protected.
10.1 Most of the existing computers in the libraries are entry-level computers.
10.1.1 You need to check the minimum system requirements of the computers to determine if they can run specific software. Define minimum system requirements. (2)
10.1.2 Name TWO hardware components, other than a motherboard, that would probably need to be upgraded to make it possible to process large amounts of data and run the data analysis software. (2) 10.1.3 Give TWO reasons why computers may slow down over time. (2)
10.2 The computers in the AcademyOne library must be connected to a network so that resources can be shared.
10.2.1 Which component, if not already part of the motherboard, must be installed in each computer to enable the computers to connect to the network? (1)
10.2.2 The library uses a large number of computers. Why would a peer-to-peer network NOT be suitable for this library? (2)
10.2.3 Suggest wired media that would be suitable to connect the library computers in a network. (1)
10.2.4 What device would be needed to connect the library's LAN to the internet? (1)
10.3 Data should be backed up regularly. The internet provides various online storage facilities.
10.3.1 Give TWO reasons why the library would use cloud storage to store files and to make backups. (2)
10.3.2 Give TWO reasons for restoring data from a backup. (2)
10.4 You need to complete a website using HTML.
10.4.1 Which tag would be used to create a bulleted list in HTML? (1)
10.4.2 Which tag would be used to create an open line in a paragraph in HTML? (1)
10.4.3 When the HTML code below is run in a browser, it should create a table with three rows and two columns. The code does not display the table correctly.
Study the code and answer the question that follows.
<table border=1> |
Suggest TWO changes to the code so that the table displays correctly.
NOTE: Do NOT rewrite the code. (2)
10.5 The screenshot below shows a few records from a larger data set used to display the salaries of part-time employees at smaller libraries across the country. The amounts earned (column E) are based on the number of days worked. 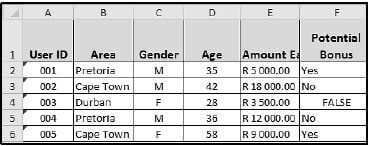
10.5.1 Which spreadsheet feature can be used to fully display the contents of cell E1 without adjusting the column width? (1)
10.5.2 What formatting has been applied to the cell values in the range A2:A6? (1)
10.5.3 The options below can be used to determine the total amount earned by the part-time employees from Cape Town.
Option 1: | =SUMIF(B2:B37492,"Cape Town",E2:E37492) |
Option 2: | =E3+E6+E11+E17+ … +E37492 |
Which ONE of the two options above would be most appropriate for the task? Motivate your answer. (2)
10.5.4 If an employee is older than 30 and earned more than R10 000 in the year, the text 'Yes' must be displayed in column F, otherwise 'No' must be displayed.
The IF statement in cell F2 (shown below) was copied down to the rest of the cells in the column:
=IF(D2>30,IF(E2>10000,"No","Yes"))
Give TWO reasons why the IF statement does NOT work correctly. (2) [25]
TOTAL SECTION C: 50
GRAND TOTAL: 150