COMPUTER APPLICATION TECHNOLOGY PAPER 2 GRADE 12 QUESTIONS - AMENDED SENIOR CERTIFICATE EXAMS PAST PAPERS AND MEMOS MAY/JUNE 2018
Share via Whatsapp Join our WhatsApp Group Join our Telegram GroupCOMPUTER APPLICATION TECHNOLOGY
PAPER 2
GRADE 12
AMENDED SCE PAST PAPERS AND MEMOS
MAY/JUNE 2018
INSTRUCTIONS AND INFORMATION
- This question paper consists of:
SECTION A: 75 marks
SECTION B: 50 marks
SECTION C: 25 marks - Answer ALL the questions.
- Number the answers correctly according to the numbering system used in this question paper.
- Start EACH question on a NEW page.
- Do NOT write in the right-hand margin of the ANSWER BOOK.
- Leave a line after EACH subquestion.
- In general, a mark is allocated per fact. A 2-mark question would therefore require TWO facts, etc.
- Write neatly and legibly.
QUESTIONS
SECTION A
QUESTION 1: MULTIPLE-CHOICE QUESTIONS
Various options are provided as possible answers to the following questions. Choose the answer and write only the letter (A–D) next to the question number (1.1–1.10) in the ANSWER BOOK, for example 1.11 D.
1.1 An HDD is used in a ...
- phablet.
- desktop computer.
- mobile phone.
- tablet. (1)
1.2 A spreadsheet error where the function is spelt incorrectly is called a ...
- value error (#VALUE!).
- reference error (#REF!).
- division by zero error (#DIV/0!).
- name error (#NAME?). (1)
1.3 Which ONE of the following terms does NOT logically belong with the other terms?
- Spyware
- Shareware
- Worm
- Trojan (1)
1.4 The relational operator <> is used to ... a value.
- exclude
- include
- decrease
- increase (1)
1.5 A wireless keyboard can NOT be connected to a computer using a/an ...
- infrared adapter.
- Bluetooth adapter.
- 3G adapter.
- Wi-Fi adapter. (1)
1.6 Message rules in e-mails are used to ...
- group related messages.
- respond to messages.
- create folders for messages.
- save attachments in a folder. (1)
1.7 'Read-only' and 'Hidden' are examples of file ...
- extensions.
- sizes.
- attributes.
- names. (1)
1.8 A comment in HTML code will appear … when the web page is displayed in the browser.
- as a title
- in brackets
- after all the tags
- nowhere (1)
1.9 The letters a/b/g/n refer to data transmission over a/an ... connection.
- ADSL
- Wi-Fi
- 3G
- Fibre (1)
1.10 What would the result be if the formula =ROUNDDOWN(B2-A2,0) was used in cell C2 below? 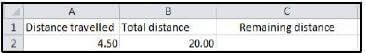
- 15.5
- 16
- 15
- 14.5 (1) [10]
QUESTION 2: MATCHING ITEMS
Choose a term/concept from COLUMN B that matches the description in COLUMN A. Write only the letter (A–T) next to the question number (2.1–2.10) in the ANSWER BOOK, for example 2.11 U.
COLUMN A | COLUMN B |
2.1 An aspect of web design that refers to moving between pages in a website |
|
QUESTION 3: TRUE/FALSE ITEMS
Indicate whether the following statements are TRUE or FALSE. Choose the answer and write 'true' or 'false' next to the question number (3.1–3.5) in the ANSWER BOOK. Correct the statement if it is FALSE. Change the underlined word(s) to make the statement TRUE. (Do NOT simply use the word 'NOT' to change the statement. NO mark will be awarded if only FALSE is written down.)
EXAMPLES:
QUESTION | ANSWER |
Google is the world's most popular search engine. | True |
An NIC has slots for hardware components, such as the CPU. | False – motherboard |
3.1 Patches are unintended flaws in software. (1)
3.2 OCR enables a user to unlock a protected smartphone without having to type in a password. (1)
3.3 =VLOOKUP(E10,A1:B10,2,FALSE)
The FALSE parameter will cause the VLOOKUP function above to return an exact match. (1)
3.4 A computer that has been taken over by a hacker is called a pirate. (1)
3.5 Cell formatting will display the result as a rounded number AFTER changing the value. (1) [5]
TOTAL SECTION A: 25
SECTION B
QUESTION 4: SYSTEMS TECHNOLOGIES
4.1 Name ONE computer application that can be used to edit text files. (1)
4.2 Give TWO GUI elements on an electronic form that can be used to present a list of options to a user. (2)
4.3 Suggest TWO methods that could be used to repair a flash drive that has been infected with a virus. (2)
4.4 Assume that you have downloaded software from the internet, but you cannot run it because there is not enough space on the hard drive. Suggest TWO ways in which you can run the software. (2)
4.5 Why would one have to use the System Restore utility? (2)
4.6 Give TWO advantages of using an interactive whiteboard. (2)
4.7 A folder contains documents that were created over a number of years. State TWO ways in which to display ONLY the documents that were created LAST WEEK. (2)
4.8 State TWO ways in which to improve the following password: Y5Y5Y (2)
4.9 Explain TWO ways in which RAM differs from SSD storage. (2)
4.10 Briefly explain the function of a client and a server in a network. (2)
4.11 The vertical and horizontal scrolling feature of a touchpad has stopped working. Suggest a reason why this could have happened.
NOTE: Assume that the hardware is working properly. (1)
4.12 State TWO advantages of 3D printing. (2)
4.13 Explain the concept of VR (virtual reality). (2) [24]
QUESTION 5: INTERNET AND NETWORK TECHNOLOGIES
5.1 Voice calling is used in many IM apps.
What network communications protocol makes this feature possible? (1)
5.2 NFC is a communication medium available on many mobile devices.
5.2.1 How would one transfer files using NFC between two devices that have the NFC setting switched on? (1)
5.2.2 State TWO uses of NFC. (2)
5.3 Give TWO possible reasons why an e-mail is not delivered to some recipients on a distribution list. (2)
5.4 With reference to online shopping, what is the purpose of a shopping cart? (2)
5.5 A smartphone can be used as a Wi-Fi hotspot. State TWO disadvantages of using a smartphone as a Wi-Fi hotspot. (2)
5.6 How can you make your own website available to the public on the internet? (1)
5.7 Wi-Fi hotspots are used by shops and businesses to attract customers. Give TWO reasons why a shop would ask customers to log on using a password. (2)
5.8 Give TWO reasons why it is necessary to limit the access rights of users on a LAN. (2) [15]
QUESTION 6: INFORMATION MANAGEMENT
6.1 Give TWO tips for setting high quality questions to be used in a survey. (2)
6.2 How would one transfer data collected electronically to another application without re-typing the data? (2)
6.3 Assume that you have one spreadsheet that uses data from another spreadsheet.
Give ONE reason why it would be better to insert a cell reference instead of using the copy and paste method to return the required data. (1)
6.4 Study the graph below and answer the questions that follow. 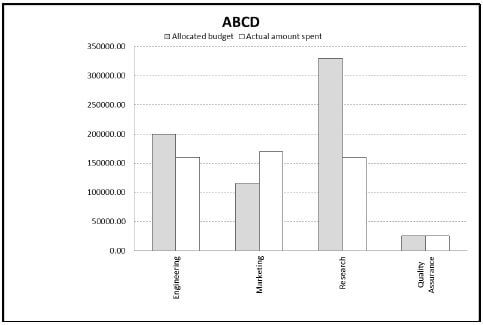
6.4.1 How many categories (series of data) are shown in this graph/chart? (1)
6.4.2 Explain the problem that exists in the Marketing department according to the graph/chart. (1)
6.4.3 Which department underspent by the largest percentage on their allocated budget? (1)
6.4.4 Suggest THREE improvements that could be made to this graph/chart to make it easier to interpret. (3) [11]
QUESTION 7: SOCIAL IMPLICATIONS
7.1 State TWO uses of AR (augmented reality). (2)
7.2 Give TWO examples of how social engineering is done. (2)
7.3 Discuss TWO benefits of using Bitcoin. (2)
7.4 A virtual private network (VPN) allows a user to remain anonymous while on the internet. Give TWO reasons why some governments are blocking VPN access for their citizens. (2)
7.5 Give TWO tips for the responsible use of social media in order to prevent offending other people. (2) [10]
QUESTION 8: SOLUTION DEVELOPMENT
8.1 What does the key symbol to the left of the database field show in the screenshot below?  (1)
(1)
8.2 After the Show/Hide feature was activated, the following is displayed in a word processing document: 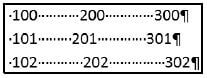
8.2.1 How did the user try to align the numbers in the screenshot above? (1)
8.2.2 Give TWO other word processing features that can be used to align the data above. (2)
8.3 Explain the purpose of a hyperlink in a document or web page. (1)
8.4 The numbers in the spreadsheet below need to be arranged from the smallest to the largest. ![]()
Describe how this can be done without re-typing each number. (2)
8.5 Consider the screenshot below.
Name the combination of spreadsheet functions that were used in the cells in column B to extract the first word from the data in the cells in column A.
NOTE: The formula in cell B1 was copied down to the rest of the cells in column B.  (2)
(2)
8.6 Draw the table represented by the HTML code below.
<table border=10>
<tr>
<td> A </td>
<td> B </td>
</tr>
<tr>
<td colspan=2> C </td>
</tr>
</table> (6) [15]
TOTAL SECTION B: 75
SECTION C: INTEGRATED SCENARIO
QUESTION 9
You are a computer specialist. The local traffic department has requested you to assist with the online administration of traffic offences.
9.1 The traffic officers have to record traffic offences at the roadside and communicate them to the traffic department.
9.1.1 What communications technology is most likely to be used to connect to the internet in this case? Motivate your answer. (2)
9.1.2 Barcodes are used on car licence disks. State TWO advantages of scanning barcodes as opposed to manually writing information down. (2)
9.1.3 Suggest a device that can be used to scan barcodes, other than barcode scanners. (1)
9.1.4 Give the term used to describe data that can be collected from offenders to uniquely identify them based on their physical features. (1)
9.2 The traffic officers would like to prevent traffic offenders from sharing information about speed traps and road blocks on social media.
9.2.1 State TWO ways in which traffic offenders can determine and share the location of a mobile speed camera after passing it. (2)
9.2.2 State TWO ways in which people try to hide social media posts from the authorities. (2)
9.2.3 While driving, your friend uses his smartphone to photograph people committing traffic offences with the aim of assisting the authorities. Why could his good intentions get him into trouble? (1)
9.3 The traffic department wants to implement an electronic filing system to establish a paperless office. There will be no need for a dedicated flatbed scanner to scan documents.
9.3.1 Explain the term dedicated device. (1)
9.3.2 Why is it possible to use certain printers for scanning? (1)
9.3.3 State TWO benefits of a paperless office. (2)
9.3.4 Suggest TWO ways in which the traffic department can make off-site backups of their data. (2)
9.3.5 The information from the documents will be captured in a database. State TWO advantages of storing data in a database. (2)
9.4 The traffic department would like to send letters to remind traffic offenders to pay their traffic fines.
9.4.1 What word processing feature can be used to create multiple personalised letters to all traffic offenders? (1)
9.4.2 State TWO ways to send electronic payment reminders using ICTs, other than using social media. (2)
9.5 Special cameras are used to monitor all traffic.
9.5.1 Name TWO types of internal storage media that can be used in the camera to store pictures and videos. (2)
9.5.2 Which camera setting affects the quality of the pictures and videos? (1) [25]
QUESTION 10
You decide to set up an employment centre to assist the unemployed people in your area to find jobs.
10.1 You want to promote the employment centre using a YouTube video.
10.1.1 Why is it not a good idea for a user to repeatedly stream a YouTube video? (1)
10.1.2 How could a user watch the video without streaming it? (1)
10.1.3 People who upload videos to YouTube always track the number of views of the videos. Give TWO reasons why one would track the number of views, other than finding out whether the video is popular or not. (2)
10.1.4 YouTube has different video resolution options to select from. Give TWO reasons for using a low resolution option when watching videos on YouTube. (2)
10.1.5 Which device would enable you to take a smartphone video of yourself without holding the smartphone in your hand? (1)
10.1.6 A computer used to edit videos has 16 GB RAM, which is the maximum amount of RAM that this computer can have. The computer is extremely slow.
Give TWO reasons with regard to hardware why this could happen. (2)
10.2 The employment centre wishes to invite companies to advertise vacancies on their website.
10.2.1 Give TWO e-mail netiquette guidelines when communicating with these companies. (2)
10.2.2 Give TWO reasons why some jobseekers cannot view certain content on the employment website. (2)
10.2.3 How can jobseekers get regular updates about vacancies without having to visit the website? (1)
10.2.4 State TWO ways in which the employment centre can stop unwanted advertisements from appearing while browsing. (2)
10.2.5 Suggest TWO ways in which jobseekers can refer to vacancies at a later stage without having to go online again. (2)
10.2.6 When viewing a website on a small screen, even maximising the browser window does not allow a user to see the full web page.
Suggest TWO ways in which this problem could be addressed. (2)
10.3 An image such as the one below will be generated for every vacancy on the website. 
10.3.1 What is this image called? (1)
10.3.2 State the function of this image. (1)
10.3.3 You have used your smartphone to download a brochure with this type of image. State how you could wirelessly connect your smartphone to a printer in order to print the brochure. (1)
10.4 Name TWO input or output devices that could make computers accessible to visually impaired users at the centre. (2) [25]
TOTAL SECTION C: 50
GRAND TOTAL: 150